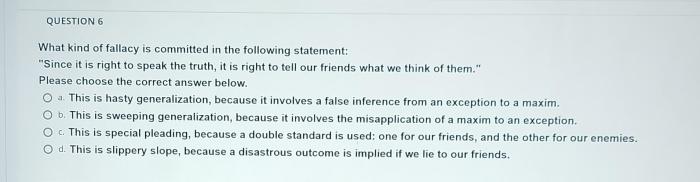
Database sharding is a crucial technique for managing massive datasets in modern applications. It involves strategically dividing a large database into smaller, manageable units called shards, each hosted on a separate server. This approach enhances scalability, performance, and availability, making it vital for handling the growing volume of data in today’s digital landscape.
This guide delves into the intricacies of database sharding, exploring various strategies, key considerations, and implementation details. From understanding different types of sharding to optimizing query performance and ensuring data consistency, this resource provides a comprehensive overview of this critical database architecture technique.
Introduction to Database Sharding
Database sharding is a technique employed to overcome the limitations of a single, large database in a high-growth environment. It involves splitting a large database into smaller, manageable partitions, called shards. These shards are typically distributed across multiple servers, enhancing scalability and performance.Sharding significantly improves database performance by distributing the workload across multiple servers. This approach ensures that queries against the database are processed more efficiently, preventing bottlenecks and delays, especially crucial for large-scale applications with high traffic volumes.
It also increases the overall availability of the database system.
Benefits of Sharding
Sharding offers several advantages for large-scale applications. These include improved scalability, enhanced performance, and increased availability. By distributing data across multiple servers, the database system can handle a larger volume of data and transactions without performance degradation. Furthermore, the failure of one shard does not necessarily compromise the entire system.
Challenges of Sharding
Implementing sharding presents certain challenges. These include data management complexity, ensuring data consistency across shards, and potential performance issues during query processing across multiple shards. Managing data distribution across shards, while maintaining data integrity, requires careful planning and implementation.
Situations Where Sharding is Suitable
Sharding is a suitable solution for applications experiencing rapid growth in data volume and user traffic. This is particularly true for e-commerce platforms, social media sites, and online gaming platforms that face massive amounts of concurrent requests. For instance, a rapidly expanding e-commerce platform with millions of product listings and customer records might benefit greatly from sharding. Similarly, a social media platform with billions of user interactions and posts could leverage sharding to ensure fast response times and handle the sheer volume of data.
Key Concepts of Sharding
The following table Artikels key concepts associated with sharding:
| Concept | Definition | Example |
|---|---|---|
| Sharding | The process of dividing a large database into smaller, independent parts (shards) distributed across multiple servers. | Dividing a user database into shards based on user location (e.g., US shard, EU shard). |
| Shard Key | A field or set of fields used to determine which shard a piece of data belongs to. | User ID could be a shard key, routing data to a specific shard. |
| Shard Router | A component that directs queries to the appropriate shard based on the shard key. | A middleware layer routing requests to the correct shard based on user location. |
| Data Replication | Duplicating data across multiple shards to ensure data availability and fault tolerance. | Replicating customer data in multiple shards for redundancy and quick access from any region. |
Types of Sharding Strategies
Sharding, a crucial technique in database architecture, involves partitioning a large database into smaller, more manageable units. This division enhances performance, scalability, and manageability. Different sharding strategies cater to diverse database needs, impacting the way data is distributed and accessed. Understanding these strategies is vital for selecting the optimal approach for a given application.
Horizontal Sharding
Horizontal sharding, also known asdatabase sharding*, involves partitioning data across multiple databases. Each shard contains a subset of the entire dataset, distributed based on a defined criteria. This method is often employed when dealing with massive datasets that exceed the capacity of a single database instance. The key benefit lies in the ability to scale horizontally, adding more servers to accommodate increasing data volumes and user traffic.
- Advantages: Horizontal sharding excels at handling massive data growth and high user loads. It allows for independent scaling of individual shards, enabling quick response times. This is particularly beneficial when dealing with specific data types or user segments, enabling dedicated resources for particular workloads.
- Disadvantages: Implementing horizontal sharding introduces complexity in data management and query processing. Ensuring data consistency across shards demands meticulous design and careful consideration of potential conflicts. Developing and maintaining complex sharding algorithms can be a substantial effort.
Vertical Sharding
Vertical sharding, also known asapplication sharding*, involves partitioning a single database into multiple smaller databases based on application logic. Data related to specific functions or aspects of the application are housed in separate databases. This technique is frequently used to separate read-heavy workloads from write-heavy workloads, improving overall performance.
- Advantages: Vertical sharding allows for optimization of specific data sets. By separating different data types, it improves performance and reduces contention for resources. It often simplifies the database design, making it more maintainable.
- Disadvantages: Vertical sharding may not be the most scalable solution for exceptionally large datasets. Querying data across multiple databases requires careful planning and might result in increased latency. Data consistency across multiple databases can pose challenges, necessitating stringent data synchronization mechanisms.
Comparison of Horizontal and Vertical Sharding
| Strategy | Description | Use Cases | Performance |
|---|---|---|---|
| Horizontal Sharding | Dividing data across multiple databases. | High-volume, high-traffic applications with large datasets. | Excellent scalability, high throughput, but complex query handling. |
| Vertical Sharding | Dividing a single database into smaller databases based on application logic. | Applications with different data access patterns (e.g., read-heavy and write-heavy). | Improved performance for specific data types but limited scalability. |
Choosing the appropriate sharding strategy hinges on specific application needs. Factors such as data volume, access patterns, and anticipated growth should be carefully considered. Horizontal sharding is often preferred for applications experiencing rapid data growth and high user loads, whereas vertical sharding suits applications with distinct data access requirements. A thorough analysis of the application’s characteristics will lead to a more effective and scalable database architecture.
Key Considerations for Sharding
Sharding, while offering significant scalability benefits, introduces complexities that demand careful consideration. Effective sharding strategies necessitate a deep understanding of data distribution, consistency mechanisms, and failure recovery procedures. These considerations ensure the stability, performance, and integrity of the sharded database.Data partitioning, a core aspect of sharding, requires a meticulous approach to maintaining data integrity and performance across shards.
A well-defined sharding strategy will optimize query performance and data access. Subsequent sections will explore these vital aspects in greater detail.
Data Distribution and Query Performance
Data distribution across shards significantly impacts query performance. Optimal distribution minimizes the need to scan across multiple shards, reducing latency and improving query response times. An uneven distribution, where some shards hold disproportionately more data than others, can lead to performance bottlenecks. Strategies like consistent hashing or range-based partitioning can effectively distribute data, ensuring a more balanced workload across shards.
Sharding Keys and Data Partitioning
Choosing the appropriate sharding key is crucial for effective data partitioning. The sharding key determines how data is distributed across shards. An ideal sharding key should be evenly distributed, stable over time, and relevant to the queries frequently run against the data. Poorly chosen sharding keys can lead to uneven data distribution, impacting query performance and requiring manual intervention for rebalancing.
A well-chosen sharding key significantly contributes to the overall efficiency of the sharded database.
Data Consistency and Integrity
Maintaining data consistency and integrity in a sharded environment presents unique challenges. Transactions that span multiple shards demand careful coordination to ensure atomicity and isolation. Techniques like two-phase commit protocols or distributed transactions are employed to guarantee data consistency across shards. Data integrity rules must be enforced across all shards to prevent inconsistencies. Replication and redundancy are crucial in ensuring data consistency, ensuring the availability and integrity of data even in the event of a failure.
Load Balancing Mechanisms
Load balancing is critical for maintaining optimal performance in a sharded database. This involves distributing incoming requests across multiple shards to prevent overload on any single shard. Load balancers can employ various strategies, including round-robin distribution, weighted distribution based on shard capacity, and intelligent routing based on query characteristics. Proper load balancing ensures that all shards contribute to the overall database capacity and responsiveness.
Database Failures and Data Recovery
Sharded databases are susceptible to individual shard failures. Robust failure recovery mechanisms are essential. Techniques like replication and backup strategies across shards are crucial for maintaining data availability and recovering from failures. Implementing automatic failover mechanisms for shards that fail and employing recovery procedures for failed shards are essential aspects of database stability. Redundancy across shards and a well-defined recovery plan are critical for minimizing downtime and data loss.
Data Replication and Redundancy
Data replication and redundancy are vital for maintaining data availability and integrity in a sharded environment. Replication strategies, such as master-slave or multi-master configurations, ensure data consistency and availability. Redundant copies of data across different shards and locations enhance data protection against failures and facilitate faster recovery. Replication strategies should be chosen carefully to balance data consistency requirements with performance considerations.
Sharding in Different Database Systems
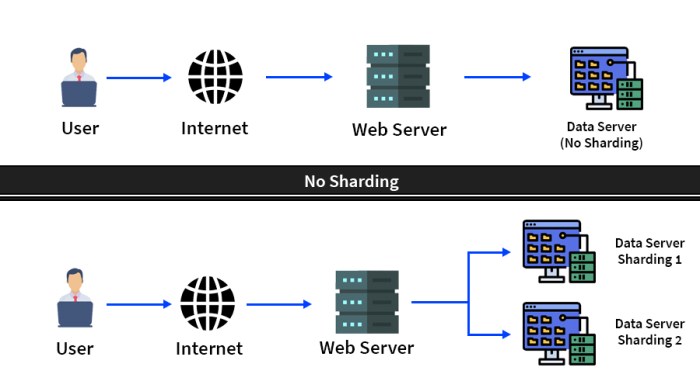
Sharding, a crucial technique for scaling databases, involves partitioning data across multiple servers. This approach allows for handling increased data volumes and query loads, ensuring system performance and availability. Different database systems employ varying strategies and tools to implement sharding, reflecting their underlying architectures and functionalities.
Relational Database Sharding
Relational databases like MySQL and PostgreSQL, typically structured with tables and relationships, require specific sharding strategies. Directly partitioning tables can be complex due to the integrity constraints imposed by relational models. Horizontal sharding is a common approach, distributing data across multiple instances of the database. This typically involves replicating the schema across shards and employing a sharding key to determine the shard responsible for a specific piece of data.
Implementing sharding in relational databases necessitates careful planning to maintain data consistency and avoid performance bottlenecks.
NoSQL Database Sharding
NoSQL databases, like MongoDB and Cassandra, often employ sharding as a core component of their architecture. Their flexible schema and distributed nature make sharding easier to implement. MongoDB, for example, leverages sharding through a dedicated configuration and a defined sharding key. Cassandra’s distributed nature facilitates sharding through its replication strategy, enabling data distribution across multiple nodes. The inherent characteristics of NoSQL databases lend themselves well to sharding, leading to scalability and high availability.
Specific Tools and Techniques for Sharding
Several tools and techniques aid in the sharding process. A common approach is using a dedicated sharding framework, which handles the complexities of distributing data and routing queries. Load balancing mechanisms are vital for distributing the load evenly across the shards. These tools often include functionalities for monitoring shard performance and rebalancing data as needed. Advanced sharding solutions may involve complex algorithms for query optimization and data replication.
Comparison of Database Systems’ Sharding Capabilities
Different database systems exhibit varying capabilities in supporting sharding. Relational databases often require more sophisticated sharding solutions to maintain data integrity, potentially leading to more complex implementation and maintenance. NoSQL databases, due to their design, typically provide more streamlined sharding capabilities, making scaling easier and faster. The choice of database system depends heavily on the specific requirements of the application, including the volume of data, query patterns, and data consistency needs.
Architectural Differences in Sharding Solutions
The architectural differences between sharding solutions for relational and NoSQL databases are significant. Relational databases require careful consideration of data consistency and transaction management across multiple shards. NoSQL databases often handle this through their inherent distributed architecture and replication strategies. The different underlying architectures directly influence the complexity and approach of sharding implementations.
Example: Sharding in MongoDB
MongoDB employs a concept of shard key. The shard key is a field (or a combination of fields) in the document. MongoDB automatically routes the read and write operations to the correct shard based on the shard key. This is done through a MongoDB configuration server, which maintains information about the shards and their locations.
Example: Sharding in MySQL
MySQL, a relational database, can be sharded using third-party tools or techniques. These methods typically involve replicating data across multiple MySQL instances. A routing layer handles the distribution of queries to the appropriate shard, maintaining data consistency through mechanisms like transactions and replication.
Data Partitioning Techniques
Data partitioning is a crucial aspect of sharding, enabling efficient data management across multiple database shards. Effective partitioning strategies significantly impact query performance, scalability, and overall system efficiency. Different partitioning methods offer varying advantages and disadvantages, making careful selection essential for optimal database design.
Range-Based Partitioning
Range-based partitioning divides data based on a specific range of values within a column. For instance, if a table stores customer data organized by their geographic region, you might partition it into ranges based on zip codes (e.g., 00000-10000, 10001-20000, etc.). This method is particularly useful for queries that target specific data ranges.
- Advantages: Range-based partitioning simplifies queries focused on specific data ranges, as the database can directly access the relevant shard. It’s straightforward to implement and manage, especially when the data range is predictable.
- Disadvantages: If the data distribution within the ranges isn’t uniform, it can lead to uneven load distribution across shards. Adding or removing data ranges can become complex, potentially requiring restructuring.
- Use Cases: Ideal for applications where data is frequently queried based on specific ranges, such as date ranges, numerical values, or geographic locations. Examples include sales data analysis by year or customer records sorted by age groups.
Hash-Based Partitioning
Hash-based partitioning uses a hash function to distribute data across shards. The hash function maps data values to specific shard IDs. This method ensures a relatively even distribution of data across the shards, mitigating the uneven load problem common with range-based partitioning.
- Advantages: Hash-based partitioning excels at distributing data evenly, preventing hot spots on specific shards. Adding or removing shards is often simpler compared to range-based partitioning.
- Disadvantages: Queries that need to access data based on specific ranges might not be optimized. The performance of the hash function plays a crucial role; an inefficient hash function can lead to poor performance.
- Use Cases: Suitable for applications with unpredictable data distribution or when ensuring consistent load balancing across shards is paramount. User data, order data, or general transactional data where specific ranges aren’t a primary query criterion are excellent use cases.
List-Based Partitioning
List-based partitioning divides data based on a predefined list of values. For instance, a table storing order data might be partitioned based on a list of order statuses (e.g., ‘Pending’, ‘Shipped’, ‘Delivered’). This method is beneficial for queries that target specific values within the list.
- Advantages: List-based partitioning is excellent for queries focused on specific categories or values. The query execution can be optimized to directly access the relevant shard.
- Disadvantages: The predefined list of values can be rigid. Modifying the list requires significant restructuring. The distribution of data across the shards may be uneven if some values are used more frequently than others.
- Use Cases: Suitable for applications where data is frequently queried based on specific categories or values. Examples include order status tracking, product categorization, or user roles in an application.
Comparison of Partitioning Methods
| Method | Description | Advantages | Disadvantages | Use Cases |
|---|---|---|---|---|
| Range-Based | Partitions data based on ranges of values. | Simple for range-based queries, predictable load distribution | Potential for uneven distribution, complex range updates | Sales data by year, customer data by age groups |
| Hash-Based | Partitions data using a hash function. | Even data distribution, easier shard management | Inefficient for range-based queries, hash function performance critical | User data, transactional data |
| List-Based | Partitions data based on a predefined list of values. | Optimized for queries targeting specific values | Rigid list, complex updates, potential uneven distribution | Order status tracking, product categories |
Query Processing in Sharded Environments
Query processing in sharded databases presents unique challenges compared to non-sharded systems. The distributed nature of sharding necessitates sophisticated mechanisms for routing queries to the appropriate shards, retrieving data, and aggregating results. This requires careful consideration of query optimization strategies to maintain performance as the database scales.Efficient query processing is crucial for maintaining application responsiveness in a sharded environment.
The complexity arises from the distributed nature of the data, requiring mechanisms to identify the relevant shards and efficiently combine results. This section details these mechanisms and optimization strategies.
Query Routing Mechanisms
Query routing is the process of directing a query to the appropriate shard(s) containing the relevant data. Effective routing is essential for performance, as it minimizes the overhead of traversing multiple shards unnecessarily.Various strategies exist for query routing, each with its own trade-offs. A common approach is hash-based routing, where a hash function is used to determine the shard responsible for a particular data item.
This allows for consistent routing, ensuring that the same data always resides on the same shard. Another approach is range-based routing, where data is partitioned based on a specific range of values. This method is particularly suitable for data with inherent ordering. A more sophisticated approach is a hybrid strategy combining both hash and range partitioning for different parts of the query.
Optimizing Query Performance in Sharded Databases
Query optimization techniques in sharded environments differ significantly from those used in non-sharded databases. In a sharded system, optimization must account for the distribution of data across multiple shards.A crucial aspect of optimization involves minimizing the number of shards that need to be queried. This can be achieved by careful query design, including using appropriate filtering conditions to reduce the data volume retrieved from each shard.
Additionally, the use of indexes on sharded data is essential. Well-designed indexes allow queries to quickly locate the necessary data within each shard. A further consideration is query decomposition, breaking down complex queries into smaller, independent queries that can be processed in parallel across different shards. This can significantly improve the overall query processing time.
Handling Complex Queries Spanning Multiple Shards
Complex queries that span multiple shards necessitate specialized processing. These queries might involve joins across shards, aggregations over data from various shards, or complex filtering criteria.A critical aspect of handling such queries involves optimizing the join process. Using distributed join algorithms is crucial, which can handle joins across multiple shards. This allows for efficient merging of data from different shards.
A common strategy is to pre-aggregate data on each shard, reducing the amount of data that needs to be transferred and processed. Additionally, techniques for partitioning data across shards can be crucial for reducing the number of joins needed and improving overall query performance.
Differences in Query Optimization Techniques
Query optimization techniques differ significantly between sharded and non-sharded databases. In a non-sharded database, optimization focuses on the single database instance. Techniques like indexing and query rewriting are applied within the single database.In contrast, sharded environments necessitate distributed optimization strategies. These techniques account for data distribution across multiple shards, query routing, and efficient data retrieval from various shards.
The primary goal is to minimize the number of shards queried and the amount of data transferred. This often involves using specialized algorithms for distributed joins and aggregations.
Maintaining Data Consistency in Sharded Systems
Sharding a database distributes data across multiple servers, enhancing scalability and performance. However, this distribution introduces complexities in maintaining data consistency, a crucial aspect for reliable data management. Ensuring that all replicas of the data remain in sync across the various shards is a significant challenge that requires careful consideration.Maintaining data consistency in sharded environments is critical for ensuring data integrity and reliability.
Inconsistencies can lead to incorrect calculations, inaccurate reporting, and ultimately, a flawed understanding of the data. Therefore, various strategies and mechanisms are implemented to mitigate these risks and ensure data remains synchronized and accurate across all shards.
Challenges of Maintaining Data Consistency
Maintaining data consistency in sharded systems is challenging due to the distributed nature of the data. The independent operation of shards can lead to data discrepancies if not carefully managed. Transactions involving multiple shards need mechanisms to ensure all operations succeed or fail together. Network latency and intermittent connectivity problems further complicate the process of maintaining a consistent view of the data across the distributed shards.
Approaches for Achieving Data Consistency
Different approaches to data consistency address the challenges in sharded systems. A common approach is eventual consistency, where data eventually converges to a consistent state, though not immediately. This approach is often employed in applications that can tolerate short-term inconsistencies, such as social media feeds or online gaming. Strong consistency, on the other hand, ensures that all operations are immediately reflected across all shards.
This method requires stricter protocols and coordination between shards, leading to higher overhead but guaranteeing a consistent view of the data at all times.
Trade-offs Between Consistency and Performance
There is a fundamental trade-off between data consistency and performance in sharded systems. Strong consistency often requires more complex mechanisms, potentially impacting the speed of read and write operations. This is because these mechanisms involve more communication between shards. In contrast, eventual consistency often allows for faster operations but requires applications to account for potential transient inconsistencies.
Impact on Transaction Management
Transaction management is significantly impacted by the choice of consistency model. Strong consistency requires transaction protocols to guarantee that operations on multiple shards are performed atomically. In contrast, eventual consistency transactions might involve a relaxation of atomicity, with the understanding that data will eventually converge to a consistent state. The specific transaction management strategy needs to align with the chosen consistency model.
Implementing Data Consistency Mechanisms
Several mechanisms can be implemented to manage data consistency in a sharded environment. One key technique is using distributed transactions. These transactions ensure that all operations in a transaction either succeed or fail across all participating shards. Optimistic locking, where updates are validated against the most recent data versions, can also be used to mitigate potential inconsistencies.
Additionally, data replication across shards can help to improve consistency by ensuring that each shard has a consistent copy of the data.
Data Replication Strategies
Data replication across shards plays a crucial role in maintaining consistency. Master-slave replication, where one shard acts as a master and others as slaves, ensures consistency by replicating changes from the master to the slaves. Other replication methods, such as multi-master or peer-to-peer replication, might be used depending on the specific needs and configuration of the sharded system.
Each approach has its trade-offs in terms of complexity, performance, and consistency guarantees.
Security Considerations for Sharded Databases
Sharding, while offering significant scalability benefits, introduces unique security challenges. Protecting data across multiple shards requires meticulous planning and implementation to prevent unauthorized access and maintain data integrity. Ensuring the security of a sharded database system demands a comprehensive approach that addresses the vulnerabilities inherent in distributed architectures.Protecting data integrity and confidentiality across multiple shards is crucial for maintaining trust and compliance.
This involves implementing robust security measures at each layer of the sharded system, from the individual shard level to the overall system. Careful consideration of authentication, authorization, and data handling is paramount.
Potential Security Vulnerabilities in Sharded Architectures
Sharded databases are susceptible to various security vulnerabilities that differ from traditional centralized systems. These include compromised shard servers, insecure communication channels between shards, and inadequate access controls. A security breach in one shard can potentially expose data from other shards, depending on the implementation details and communication protocols. Furthermore, the complexity of distributed systems can obscure potential attack vectors, making it harder to detect and prevent security incidents.
Securing Data Access Across Multiple Shards
Implementing secure data access across multiple shards requires a strategy that ensures data isolation and prevents unauthorized access. This often involves using a centralized authentication and authorization service that controls access to each shard. The authorization system needs to verify user identities and enforce access permissions on a per-shard or per-data-item basis.
Authentication and Authorization in Sharded Systems
Robust authentication and authorization mechanisms are essential to secure sharded databases. A centralized authentication service, often a separate application or component, can verify user identities and issue tokens. These tokens are then used to grant or deny access to specific shards and data within them. Fine-grained authorization, defining which users can access which shards and which data within those shards, is critical to controlling access permissions.
Handling Sensitive Data in a Sharded Database
Handling sensitive data in a sharded environment requires specific attention to data encryption. Data encryption should be applied at rest and in transit, and the encryption keys should be managed securely. Data masking techniques may be employed to obscure sensitive data during queries or reports. Regular audits and penetration testing should be conducted to identify and address any security vulnerabilities.
Security Measures for Sharded Databases
| Threat | Mitigation Strategy | Description |
|---|---|---|
| Unauthorized Access to Shard | Strong Authentication and Authorization | Implement a centralized authentication service and granular authorization policies to control access to each shard. Use multi-factor authentication for added security. |
| Compromised Shard Server | Redundancy and Failover Mechanisms | Maintain multiple copies of data and shard servers to ensure high availability. Implement failover mechanisms to quickly switch to backup servers in case of a failure. |
| Insecure Communication Channels | Secure Communication Protocols | Use encrypted communication protocols (e.g., TLS) to protect data transmitted between shards. Implement secure network configurations to limit access to communication channels. |
| Data Breaches Across Shards | Data Encryption | Encrypt data at rest and in transit to protect sensitive information in case of a breach. Use encryption algorithms with strong security properties. |
| Lack of Monitoring and Logging | Comprehensive Logging and Auditing | Implement comprehensive logging to track all database activity and access attempts. Establish an audit trail to monitor access patterns and identify unusual behavior. |
Scalability and Performance in Sharded Systems
Sharding, by its very nature, is a powerful technique for enhancing the scalability and performance of database systems. It allows for horizontal expansion, distributing the workload across multiple servers, thereby mitigating the performance bottlenecks associated with a single, large database. This approach is particularly crucial for applications with high transaction volumes and rapidly growing datasets.Sharding directly addresses the limitations of vertical scaling, which often reaches a point of diminishing returns.
By partitioning the data, sharding allows for independent scaling of individual shards, leading to significant improvements in both the system’s capacity to handle growing data and the speed with which queries are processed. This distributed architecture facilitates faster response times, reduced latency, and increased overall system availability.
Improving Database Scalability
Sharding effectively distributes the database workload across multiple servers. This horizontal scaling allows the system to accommodate increasing data volumes and user traffic without significant performance degradation. The system’s capacity grows proportionally with the number of shards added, addressing the inherent limitations of vertical scaling.
Impact on Performance Metrics
Sharding impacts various performance metrics. Query performance, measured by response time, often improves significantly due to the distributed nature of the system. Data retrieval becomes faster as the database can utilize multiple shards concurrently. However, sharding introduces complexities in query processing, which requires careful consideration of query routing and data distribution strategies. Read and write throughput are also affected, often increasing as the number of shards and available resources increase.
Load balancing is critical in ensuring consistent performance across all shards.
Monitoring and Optimizing Performance
Monitoring a sharded database environment is essential for identifying bottlenecks and ensuring optimal performance. Key metrics to monitor include query latency, resource utilization (CPU, memory, disk I/O) across each shard, and network traffic between the shards and the load balancer. Specialized monitoring tools designed for sharded environments are crucial in providing comprehensive insights into the system’s health and performance.
Regular analysis of these metrics allows for proactive identification and resolution of potential issues before they escalate. Database administrators can leverage this information to fine-tune query optimization techniques, adjust resource allocation, and proactively address performance degradation.
Scaling Sharded Databases
Scaling sharding involves adding more shards to the system as the data volume and user load increase. The specific scaling strategy depends on the chosen sharding technique. Techniques include adding new servers, distributing data across the newly added shards, and adjusting the load balancing strategy. A carefully planned scaling approach ensures a smooth transition, maintaining performance and availability throughout the process.
Automated scaling mechanisms are often implemented to streamline the process, enabling the system to adapt to changing demands dynamically.
Role of Load Balancers in Sharded Environments
Load balancers play a crucial role in sharded environments. They distribute incoming requests across the available shards, ensuring that no single shard is overloaded. This distribution is typically based on a predetermined routing strategy, such as hash-based routing or round-robin distribution. A robust load balancer monitors the health of each shard and dynamically adjusts the traffic distribution to maintain optimal performance.
A sophisticated load balancer can handle the complexity of routing queries to the appropriate shard, ensuring high availability and preventing bottlenecks. This also helps in preventing single points of failure within the sharded architecture.
Tools and Technologies for Sharding
Database sharding requires robust tools and technologies to effectively manage the distributed data. Proper selection of tools significantly impacts the success and maintainability of a sharded system. Choosing the right toolset involves careful consideration of factors like scalability needs, data model complexity, and the team’s expertise.The correct tools can simplify the management of sharded databases, enabling faster query processing and improved overall system performance.
Conversely, inappropriate tools can lead to complexities, maintenance challenges, and even data loss. This section explores common sharding tools, their advantages and disadvantages, and critical selection factors.
Common Sharding Tools
Various tools and technologies facilitate sharding, each with its own strengths and weaknesses. Selecting the appropriate tool requires careful evaluation based on specific database requirements and project constraints.
- Database Sharding Frameworks: Frameworks like the Apache ShardingSphere project offer a comprehensive solution for sharding, enabling various sharding strategies and query routing. These frameworks often provide automatic data distribution and query optimization. A key advantage is abstraction, allowing developers to work with a single logical database, simplifying development and reducing complexity. However, frameworks might introduce a performance overhead due to the added layer of abstraction.
The overhead can be mitigated with proper configuration and tuning. ShardingSphere, for instance, allows customization of various aspects like data sharding strategy, query routing, and transaction management.
- API Gateways: Tools like Kong or Apigee provide API gateways that act as intermediaries between clients and the sharded database. They can handle request routing to the appropriate shard, thus improving scalability and availability. An advantage is the separation of concerns, allowing for a clear distinction between the application logic and database interactions. A disadvantage is the added complexity of setting up and managing the gateway, requiring additional resources and expertise.
An API gateway can also introduce latency, which must be considered when dealing with high-performance applications.
- Cloud-based Database Services: Cloud providers like Amazon Web Services (AWS), Google Cloud Platform (GCP), and Microsoft Azure offer managed database services that often include sharding capabilities. This approach often simplifies deployment and management. A significant advantage is the ease of scalability and the cloud provider’s support. However, the reliance on a third-party provider may introduce limitations or cost considerations.
- Custom Solutions: In some cases, custom sharding solutions tailored to specific needs might be necessary. These solutions offer the most flexibility and control over the sharding process. An advantage is the potential for a highly customized and optimized solution. A significant disadvantage is the substantial development effort required, which necessitates a skilled team and can be costly. This option is usually preferred for complex scenarios requiring highly specialized solutions.
Factors to Consider When Selecting a Sharding Tool
Selecting the appropriate sharding tool hinges on a thorough evaluation of several key factors.
- Scalability Requirements: The tool must be capable of handling anticipated growth in data volume and user traffic. Consider how the tool scales horizontally to accommodate increasing data volume.
- Data Model Complexity: The complexity of the data model influences the choice of sharding strategy and the appropriate tool. Simple models might require simpler solutions, while complex models could benefit from more robust frameworks.
- Team Expertise: The technical skills of the development team are crucial. Choosing a tool that aligns with the team’s existing expertise simplifies implementation and reduces learning curves.
- Budget Constraints: Cost is a key factor. Evaluate the licensing fees, cloud charges, and maintenance costs associated with different tools.
- Integration with Existing Systems: The tool must seamlessly integrate with existing applications and infrastructure. Ensure compatibility with current systems.
System Architecture for a Sharded Database System (using Apache ShardingSphere)
A sharded database system using Apache ShardingSphere can be architected as follows:
| Component | Description |
|---|---|
| Application | The application interacts with the ShardingSphere proxy. |
| ShardingSphere Proxy | Acts as a gateway, routing requests to the appropriate shard. |
| Sharding Database Servers | Multiple database servers, each holding a portion of the data. |
Setting Up and Configuring a Sharded Database Environment
The setup involves configuring the ShardingSphere proxy and the underlying database shards.
- Installation: Install ShardingSphere proxy and configure it with the necessary properties to route queries.
- Data Partitioning: Determine the sharding strategy (e.g., hash-based) and partition the data across the shards.
- Configuration: Configure the data sources (the underlying database shards) and the sharding rules within the ShardingSphere configuration file.
- Testing: Thoroughly test the sharded environment to ensure proper data distribution and query processing.
Outcome Summary
In conclusion, sharding offers a powerful solution for scaling databases to accommodate large datasets and high traffic loads. Understanding the various sharding strategies, key considerations, and implementation details is essential for leveraging its benefits effectively. This guide has provided a framework for navigating the complexities of sharding, enabling informed decision-making and effective implementation within diverse database systems.
Commonly Asked Questions
What are the common challenges associated with sharding?
Challenges include data consistency across shards, query processing complexities, and maintaining data integrity. Choosing the right sharding strategy and carefully considering data distribution are essential for overcoming these issues.
How does sharding improve query performance?
By distributing data across multiple servers, sharding reduces the load on individual servers, leading to faster query response times and improved overall performance. Query routing mechanisms play a critical role in this optimization.
What are the different types of data partitioning techniques in sharding?
Common techniques include range-based partitioning, hash-based partitioning, and list-based partitioning. Each approach has unique advantages and disadvantages, and the optimal choice depends on the specific data characteristics and query patterns.
What are the security considerations when implementing sharding?
Security vulnerabilities exist across multiple shards, requiring robust authentication and authorization mechanisms. Ensuring secure data access across shards and handling sensitive data are crucial aspects of sharding security.