Embark on a journey to understand what is a threat modeling process like STRIDE, a crucial practice in securing software applications. Threat modeling, at its core, is a proactive approach to identify, assess, and mitigate potential security vulnerabilities before they can be exploited. This process involves systematically analyzing a system or application to understand the threats it faces and devise strategies to counter them.
The STRIDE model, an acronym for Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege, provides a structured framework for categorizing and addressing these threats. This methodology allows developers and security professionals to proactively identify potential weaknesses in their systems, leading to more secure and robust software development practices. By understanding STRIDE, you gain a powerful tool to build secure and resilient applications.
Introduction to Threat Modeling with STRIDE
Threat modeling is a crucial proactive approach in software development that systematically identifies and mitigates potential security vulnerabilities. It’s essentially a structured process for understanding the threats a system might face, prioritizing them based on their potential impact, and designing countermeasures to reduce the risk. This process is integral to building secure software from the ground up, rather than trying to bolt security onto an existing, potentially flawed, design.
Core Concept and Significance
The fundamental goal of threat modeling is to improve the security posture of a system by identifying potential weaknesses before they can be exploited. This proactive approach allows developers to make informed decisions about security controls and prioritize resources effectively. By analyzing a system’s design, architecture, and intended functionality, threat modeling helps to uncover vulnerabilities that might otherwise be missed during traditional testing phases.
The significance lies in its ability to shift security left in the development lifecycle, reducing the cost and effort associated with fixing security flaws later on. It’s a risk management exercise, providing a structured way to assess and manage the threats to a system.
Brief History of Threat Modeling Methodologies
The evolution of threat modeling methodologies reflects the changing landscape of cyber threats and the increasing complexity of software systems. Early approaches were often informal, relying on ad-hoc reviews and checklists. Over time, more structured methodologies emerged, driven by the need for more consistent and repeatable processes.
- Early Stages: In the early days of software development, security was often an afterthought. Threat modeling, if it existed at all, was usually a manual process, often limited to expert reviews of code and design documents.
- STRIDE and Beyond: Microsoft developed STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege) as a framework for identifying threats. This model provided a structured approach to threat identification, and has become a widely adopted framework. Other models like PASTA (Process for Attack Simulation and Threat Analysis) and OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation) also appeared, offering alternative approaches with varying degrees of complexity and focus.
- Modern Approaches: Today, threat modeling continues to evolve, incorporating automation, integration with DevOps pipelines, and a focus on agile methodologies. The emphasis is on making threat modeling a more accessible and efficient process, enabling developers to integrate security considerations seamlessly into their workflows.
Benefits of Implementing a Threat Modeling Process
Adopting a threat modeling process offers several key advantages for software development teams and organizations as a whole. The benefits extend beyond just improved security, contributing to better software quality, reduced costs, and enhanced stakeholder confidence.
- Proactive Security: Threat modeling allows teams to identify and address security vulnerabilities early in the development lifecycle, before they can be exploited by attackers. This proactive approach significantly reduces the risk of costly security breaches.
- Reduced Development Costs: Finding and fixing security vulnerabilities during the design phase is far less expensive than addressing them after the software has been deployed. Threat modeling helps to identify and eliminate security flaws early on, minimizing the cost of remediation.
- Improved Software Quality: By considering security aspects during the design phase, threat modeling contributes to the overall quality of the software. It forces developers to think critically about potential attack vectors and design systems that are more resilient to threats.
- Enhanced Compliance: Many industry regulations and standards require organizations to implement security controls and conduct regular security assessments. Threat modeling helps to meet these compliance requirements by providing a structured framework for identifying and mitigating risks.
- Better Communication and Collaboration: Threat modeling fosters communication and collaboration among developers, security professionals, and other stakeholders. It provides a common language and framework for discussing security risks and developing effective mitigation strategies.
- Increased Stakeholder Confidence: Demonstrating a commitment to security through threat modeling can build trust with customers, partners, and other stakeholders. It shows that the organization takes security seriously and is actively working to protect sensitive data and systems.
Overview of the STRIDE Model
The STRIDE model is a threat modeling methodology developed by Microsoft to help identify and categorize potential threats to a system. It provides a structured approach to analyzing applications and systems, enabling developers and security professionals to proactively address vulnerabilities during the design and development phases. By understanding the different types of threats and their impact, organizations can prioritize their security efforts and mitigate risks effectively.
Understanding the STRIDE Acronym
The acronym STRIDE represents six categories of threats, each of which targets a specific aspect of security. Each letter corresponds to a particular type of threat:
- Spoofing: This involves impersonating another user or system. It’s about gaining access by pretending to be someone or something you are not. For example, an attacker might use a stolen password to log in as a legitimate user.
- Tampering: This refers to unauthorized modification of data or code. Attackers might alter data in transit or stored on a server to achieve malicious goals. For example, an attacker could modify the price of an item in an e-commerce application.
- Repudiation: This involves denying that an action was performed. It focuses on the ability of a user to deny having performed an action. For instance, a user might deny having made a financial transaction.
- Information Disclosure: This refers to the unauthorized exposure of sensitive information. This can involve leaking confidential data or exposing internal system details. For example, an attacker might gain access to a database containing customer credit card numbers.
- Denial of Service (DoS): This aims to make a system or resource unavailable to legitimate users. Attackers might flood a server with traffic, preventing users from accessing the service. For example, a Distributed Denial of Service (DDoS) attack could render a website unavailable.
- Elevation of Privilege: This involves gaining unauthorized access to privileged functions or data. An attacker might exploit a vulnerability to gain administrative rights on a system. For example, an attacker could exploit a buffer overflow to gain root access.
STRIDE Categories and Security Goals
STRIDE categories are intrinsically linked to the security goals they violate. By understanding these connections, threat modelers can better assess the impact of potential threats and prioritize mitigation strategies. Each threat category is designed to address a specific security goal, ensuring a comprehensive approach to security.
Here’s a table illustrating the STRIDE categories, their corresponding security goals, and an example threat:
| STRIDE Category | Security Goal | Example Threat |
|---|---|---|
| Spoofing | Authentication | An attacker uses stolen credentials to access a system. |
| Tampering | Integrity | An attacker modifies data stored in a database. |
| Repudiation | Non-repudiation | A user denies having performed a transaction. |
| Information Disclosure | Confidentiality | An attacker gains unauthorized access to sensitive data. |
| Denial of Service | Availability | An attacker floods a server with traffic, making it unavailable. |
| Elevation of Privilege | Authorization | An attacker exploits a vulnerability to gain administrative rights. |
The Threat Modeling Process Steps
The threat modeling process, regardless of the specific methodology employed, provides a structured approach to identifying, understanding, and mitigating potential security threats. This process is iterative and typically involves several key steps, designed to proactively address vulnerabilities within a system or application. Each step builds upon the previous one, creating a comprehensive security assessment.
The Threat Modeling Workflow
The threat modeling workflow is a cyclical process that helps to visualize and manage the steps involved in identifying and mitigating threats. It typically starts with defining the scope of the system being analyzed and culminates in documenting the findings and actions taken. The workflow is not necessarily linear; it often involves revisiting previous steps as new information emerges or the system evolves.A simplified threat modeling workflow can be represented as follows:* Define Scope and Objectives: This initial phase involves understanding the system’s purpose, functionality, and boundaries.
It’s crucial to define what is being protected and why.* Gather Information: Collect detailed information about the system’s architecture, data flows, and components. This might include diagrams, code, and documentation.* Decompose the Application: Break down the system into its constituent parts, such as processes, data stores, and communication channels. This decomposition helps to identify potential attack surfaces.* Identify Threats (STRIDE): Apply the STRIDE model (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege) or another threat modeling framework to identify potential threats to the system.* Identify Vulnerabilities: Analyze the identified threats to pinpoint specific vulnerabilities within the system that could be exploited.* Prioritize Threats and Vulnerabilities: Assess the likelihood and impact of each threat to prioritize mitigation efforts.* Develop Mitigation Strategies: Design and implement countermeasures to address the identified vulnerabilities and reduce the risk of exploitation.* Document Findings and Recommendations: Record all the identified threats, vulnerabilities, mitigation strategies, and any remaining risks.* Review and Iterate: Regularly review and update the threat model as the system evolves or new threats emerge.
This is a continuous process.
Identifying Assets, Data Flows, and Trust Boundaries
Identifying assets, data flows, and trust boundaries is a critical step in the threat modeling process, as it lays the foundation for understanding the system’s attack surface and potential vulnerabilities. These elements are interconnected and provide context for applying the STRIDE model.* Assets: Assets represent the valuable resources that the system protects. These can include data, hardware, software, and even reputation.
Identifying assets is the first step in determining what needs to be secured. For example, in an e-commerce application, assets might include:
Customer personal information (names, addresses, credit card details).
Product inventory data.
Order history.
The application’s code and infrastructure.
Data Flows
Data flows describe how information moves through the system. Understanding data flows helps to identify potential points of vulnerability where data could be intercepted, modified, or lost. Data flow diagrams (DFDs) are commonly used to visualize data flows. For example, consider the data flow for a user logging into an e-commerce site: 1.
The user enters their username and password into a web browser. 2. The web browser sends this information to the web server. 3. The web server validates the credentials against a database.
4. If the credentials are valid, the web server grants the user access. 5. The user’s session information is stored on the server.
Trust Boundaries
Trust boundaries define the areas where different levels of trust are established. These boundaries represent points where data or control passes from one entity to another, and where security controls must be implemented. Common trust boundaries include:
User Interface
The point where the user interacts with the system.
Network Connection
The point where the system communicates with external networks.
Application Server
The component that processes user requests and interacts with data stores.
Database Server
The component that stores and manages data. For example, in the e-commerce application, trust boundaries might exist between:
The user’s web browser and the web server (e.g., using HTTPS to secure the connection).
The web server and the database server (e.g., using strong authentication and authorization).
The e-commerce platform and a third-party payment gateway (e.g., through API calls secured with encryption and authentication).
By carefully identifying these elements, the threat modeler can create a detailed picture of the system’s security posture and effectively apply the STRIDE model to identify and mitigate potential threats.
Identifying Threats Using STRIDE
Applying the STRIDE model is a systematic process for uncovering potential security vulnerabilities within a system or application. By methodically analyzing each category of STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege), security professionals can identify potential threats and prioritize mitigation efforts. This structured approach ensures a comprehensive assessment of security risks.
Applying STRIDE to Identify Threats
The process of identifying threats using STRIDE involves analyzing the system’s components and data flows, asking specific questions related to each STRIDE category. This often involves a team-based approach, with developers, security experts, and other stakeholders contributing their expertise. The goal is to proactively identify vulnerabilities before they can be exploited.
Common Threats Within Each STRIDE Category
Each category within STRIDE represents a different type of threat. Understanding these categories and their associated vulnerabilities is crucial for effective threat modeling.
- Spoofing: This involves an attacker impersonating a legitimate user or system. Common examples include:
- Credential Theft: An attacker steals user credentials (usernames, passwords, tokens) through phishing, keylogging, or brute-force attacks to gain unauthorized access.
- IP Address Spoofing: An attacker modifies their IP address to appear as a trusted source, bypassing access controls.
- Man-in-the-Middle (MitM) Attacks: An attacker intercepts communication between two parties, impersonating one or both of them.
- Tampering: This refers to the unauthorized modification of data or system components. Examples include:
- Data Corruption: An attacker alters data stored in a database or transmitted over a network, potentially leading to incorrect decisions or system failures.
- Code Injection: An attacker inserts malicious code into a system, such as SQL injection or cross-site scripting (XSS) attacks.
- File Tampering: An attacker modifies configuration files, application binaries, or other critical files to compromise system behavior.
- Repudiation: This is the ability of a user to deny having performed an action. Examples include:
- Lack of Audit Trails: Insufficient logging prevents tracing user actions, making it difficult to prove who performed a specific action.
- Compromised Accounts: If an account is compromised, the attacker can perform actions that appear to be legitimate, making it difficult to identify the actual perpetrator.
- Insufficient Non-Repudiation Mechanisms: The system lacks mechanisms to ensure that actions can be definitively attributed to a specific user, such as digital signatures.
- Information Disclosure: This involves revealing sensitive information to unauthorized parties. Examples include:
- Unencrypted Data Transmission: Sensitive data transmitted over an unencrypted network can be intercepted and read by attackers.
- Vulnerable Error Messages: Error messages that reveal internal system details, such as database names or file paths, can assist attackers in reconnaissance.
- Data Breaches: Data stored in databases or other repositories is exposed due to vulnerabilities.
- Denial of Service (DoS): This involves making a system or resource unavailable to legitimate users. Examples include:
- Distributed Denial of Service (DDoS) Attacks: An attacker uses multiple compromised systems to flood a target system with traffic, overwhelming its resources.
- Resource Exhaustion: An attacker consumes system resources, such as CPU, memory, or disk space, to prevent legitimate users from accessing the system.
- Application-Layer Attacks: An attacker exploits vulnerabilities in an application to consume excessive resources, such as sending a large number of requests to exhaust a server’s connection pool.
- Elevation of Privilege: This involves an attacker gaining unauthorized access to higher-level privileges. Examples include:
- Buffer Overflows: An attacker exploits a buffer overflow vulnerability to execute arbitrary code with elevated privileges.
- Privilege Escalation: An attacker exploits a vulnerability in the operating system or application to gain administrative or root access.
- Weak Access Controls: Poorly configured access controls allow users to perform actions they are not authorized to perform.
Using Data Flow Diagrams to Visualize Potential Attack Vectors
Data flow diagrams (DFDs) are a valuable tool for visualizing the flow of data through a system. By using DFDs, security professionals can easily identify potential attack vectors and vulnerabilities. The DFD provides a visual representation of how data moves between different components, allowing analysts to pinpoint where threats might occur.
Example: A Simple E-commerce System
Consider a simplified e-commerce system with the following components:
- Customer (Source): The customer initiates transactions.
- Web Server (Process): Handles customer requests, presents the user interface, and processes payment information.
- Database Server (Process): Stores customer data, product information, and transaction details.
- Payment Gateway (Process): Processes payment transactions.
A basic DFD would illustrate the flow of data, such as customer information, product selections, and payment details, between these components. For example, a line with an arrow would show customer information flowing from the customer to the web server. Another line with an arrow would show the customer’s credit card information flowing from the web server to the payment gateway.
By analyzing this DFD, security professionals can identify potential attack vectors. For instance:
- Tampering: An attacker might target the data flow between the web server and the database server, attempting to modify order details or customer information.
- Information Disclosure: The unencrypted transmission of credit card data from the web server to the payment gateway is a potential risk.
- Denial of Service: An attacker could target the web server to overload the system.
The DFD, therefore, provides a visual representation of the system’s data flows, facilitating the identification of potential vulnerabilities and the development of appropriate security controls.
Threat Prioritization and Risk Assessment
Prioritizing identified threats and assessing the associated risks is a crucial step in the STRIDE threat modeling process. This phase allows security professionals to focus their resources on the most critical vulnerabilities, ensuring the most effective mitigation strategies are implemented. A well-defined prioritization and risk assessment process significantly improves the overall security posture of a system or application.
Methods for Prioritizing Identified Threats
Several methods can be employed to prioritize the identified threats based on their potential impact and likelihood of occurrence. These methods help in ranking threats, enabling informed decision-making regarding resource allocation and mitigation efforts.
- Impact Assessment: This involves evaluating the potential consequences of a threat being realized. This includes considering factors such as data loss, financial damage, reputational harm, and operational disruption. A higher impact typically translates to a higher priority.
- Likelihood Assessment: Assessing the probability of a threat being exploited is another crucial aspect. This considers factors like the attacker’s capabilities, the accessibility of the vulnerability, and the existing security controls. Threats with a higher likelihood of exploitation should be prioritized.
- Threat Modeling Tools: Many threat modeling tools, such as Microsoft Threat Modeling Tool, provide built-in functionalities to assist in prioritizing threats based on various parameters. These tools often incorporate risk scoring frameworks to automate the prioritization process.
- Expert Judgment: Leveraging the expertise of security professionals and subject matter experts is invaluable. Their experience and knowledge can provide insights into the criticality of threats and the effectiveness of potential mitigation strategies.
- Asset Valuation: This method focuses on the value of the assets that the threat could impact. Assets are categorized based on their importance (e.g., critical, important, and non-critical). Threats that can compromise critical assets should receive the highest priority.
Examples of Risk Assessment Frameworks
Risk assessment frameworks provide structured methodologies for evaluating and quantifying risks. They typically involve assigning scores based on factors such as impact, likelihood, and exploitability. Here are examples of commonly used frameworks:
- DREAD: DREAD is an acronym for Damage, Reproducibility, Exploitability, Affected users, and Discoverability. Each of these factors is assigned a score (typically from 1 to 10), and the overall risk score is calculated based on these individual scores. The DREAD framework is used to categorize and prioritize the threats.
- CVSS (Common Vulnerability Scoring System): While not a threat modeling framework in itself, CVSS is a widely used open framework for assessing the severity of software vulnerabilities. It provides a numerical score reflecting the characteristics of a vulnerability, allowing for prioritization based on the potential impact.
- Custom Risk Matrices: Organizations can create their own risk matrices tailored to their specific needs and environment. These matrices typically involve assigning scores based on impact and likelihood, resulting in a risk score that helps in prioritizing threats.
Risk Scoring and Mitigation Strategies Table
The following table illustrates how threats can be scored and mitigation strategies implemented. This example uses a simplified scoring system and mitigation strategies. The actual scoring and strategies will vary based on the specific threat and environment.
| Threat | Risk Score | Mitigation Strategy | Status |
|---|---|---|---|
| Spoofing – Weak Authentication on Login | High (Impact: 8, Likelihood: 7) | Implement Multi-Factor Authentication (MFA), strengthen password policies, and regularly audit authentication logs. | In Progress |
| Tampering – Unvalidated Input in Database Queries (SQL Injection) | Critical (Impact: 9, Likelihood: 8) | Implement input validation and sanitization, use parameterized queries, and regularly scan for SQL injection vulnerabilities. | Completed |
| Repudiation – Lack of Audit Trails for Sensitive Transactions | Medium (Impact: 6, Likelihood: 5) | Implement comprehensive logging and auditing for all critical transactions, including timestamps, user IDs, and data changes. | Planned |
| Information Disclosure – Exposure of Sensitive Data in Error Messages | Medium (Impact: 7, Likelihood: 4) | Review and sanitize error messages to avoid revealing sensitive information, implement proper exception handling, and configure detailed logging for debugging purposes. | Completed |
| Denial of Service – Insufficient Resource Allocation | High (Impact: 8, Likelihood: 6) | Implement rate limiting, resource quotas, and capacity planning. Regularly monitor system performance and implement auto-scaling mechanisms. | In Progress |
| Elevation of Privilege – Weak Access Control | Critical (Impact: 9, Likelihood: 7) | Implement the principle of least privilege, regularly review and update access control lists, and conduct penetration testing to identify and fix access control vulnerabilities. | Planned |
Developing Mitigation Strategies
Following the identification and prioritization of threats using STRIDE, the next crucial step is to develop and implement mitigation strategies. These strategies aim to reduce the likelihood and impact of identified threats, safeguarding the system from potential attacks. This phase involves selecting and applying appropriate security controls based on the threat analysis.
Mitigation Techniques
A variety of mitigation techniques can be employed to address threats identified through STRIDE. The choice of technique depends on the specific threat, the system’s architecture, and the organization’s security policies.
- Code Reviews: This involves having developers or security specialists examine the source code for vulnerabilities. This manual process helps to identify flaws like buffer overflows, SQL injection vulnerabilities, and other coding errors that could be exploited. Code reviews should be a standard practice during the software development lifecycle (SDLC).
- Input Validation: This technique ensures that all user-supplied data is validated before being processed. It involves checking the type, format, and range of input to prevent malicious data from entering the system. Input validation can prevent many types of attacks, including cross-site scripting (XSS) and SQL injection.
- Access Controls: Implementing access controls restricts access to resources based on user identity and roles. This ensures that only authorized users can access sensitive data and functionalities. Access controls can include authentication, authorization, and privilege management.
- Authentication: Authentication verifies the identity of a user or system. Common authentication methods include passwords, multi-factor authentication (MFA), and biometrics. Strong authentication is essential for preventing unauthorized access.
- Authorization: Authorization determines what a user is allowed to do after they have been authenticated. It defines the permissions and privileges granted to a user or system. Authorization prevents users from performing actions they are not authorized to perform.
- Encryption: Encryption transforms data into an unreadable format, protecting its confidentiality. Encryption can be used to protect data at rest (stored data) and data in transit (data being transmitted over a network).
- Regular Security Updates: Regularly updating software and systems is crucial for patching known vulnerabilities. Vendors release security patches to address newly discovered vulnerabilities. Failing to apply security updates can leave systems vulnerable to attacks.
- Intrusion Detection and Prevention Systems (IDPS): IDPS monitor network traffic and system activity for malicious behavior. They can detect and, in some cases, prevent attacks. IDPS are an important part of a layered security approach.
- Web Application Firewalls (WAFs): WAFs are designed to protect web applications from various attacks, such as SQL injection and cross-site scripting. They filter malicious traffic before it reaches the web application.
Implementing Mitigation Strategies for Specific Threats
Let’s examine how to implement mitigation strategies for specific threats identified using STRIDE.
- Spoofing: To mitigate spoofing, implement strong authentication mechanisms, such as multi-factor authentication (MFA). Use digital signatures to verify the authenticity of messages and data. Network segmentation can limit the impact of a successful spoofing attack.
- Tampering: To mitigate tampering, use integrity checks, such as checksums or digital signatures, to detect unauthorized modifications to data or files. Implement access controls to restrict write access to critical resources. Regularly audit system logs to detect suspicious activity.
- Repudiation: To mitigate repudiation, implement non-repudiation mechanisms, such as digital signatures and audit trails. Digital signatures provide proof that a specific user performed an action. Audit trails record all actions performed within the system, making it difficult for users to deny their actions.
- Information Disclosure: To mitigate information disclosure, implement encryption to protect sensitive data. Enforce access controls to restrict access to sensitive information. Regularly review and update security policies to prevent the accidental disclosure of information.
- Denial of Service (DoS): To mitigate DoS, implement rate limiting to restrict the number of requests from a single source. Use a content delivery network (CDN) to distribute traffic and absorb attacks. Implement redundancy and failover mechanisms to ensure system availability.
- Elevation of Privilege: To mitigate elevation of privilege, implement the principle of least privilege, granting users only the minimum necessary permissions. Regularly review user accounts and permissions to identify and remove unnecessary privileges. Implement robust authentication and authorization mechanisms.
Code Snippet Example
Here is an example of a code snippet illustrating input validation to mitigate a potential SQL injection vulnerability. This example focuses on validating user input before it’s used in a database query.
// Example: PHP code for input validation before a database query <?php $username = $_POST['username']; $password = $_POST['password']; // Sanitize the input to prevent SQL injection $username = mysqli_real_escape_string($conn, $username); $password = mysqli_real_escape_string($conn, $password); // Construct the SQL query using the sanitized input $sql = "SELECT- FROM users WHERE username = '$username' AND password = '$password'"; // Execute the query $result = mysqli_query($conn, $sql); // ... (rest of the code) ?>
Documenting the Threat Model
Documenting the threat model is a critical step in the STRIDE process. It ensures that the analysis is repeatable, shareable, and serves as a valuable resource for future security efforts. A well-documented threat model provides a clear understanding of the system’s vulnerabilities, the identified threats, and the planned mitigations. This documentation aids in communication among stakeholders, facilitates security audits, and supports continuous improvement of the security posture.
Importance of Threat Model Documentation
The documentation serves multiple purposes. It provides a historical record of the threat modeling process, allowing for future analysis and comparison. It also acts as a communication tool, ensuring that all stakeholders understand the security risks and the proposed solutions. Furthermore, it aids in compliance efforts and provides a basis for security audits.
Guidelines for a Comprehensive Threat Model Document
Creating a comprehensive threat model document involves adhering to several guidelines to ensure its effectiveness and usefulness. This documentation should be clear, concise, and easily understandable by both technical and non-technical audiences.
- Clarity and Conciseness: The document should be written in clear and simple language, avoiding technical jargon whenever possible. The information should be presented in a logical and organized manner, making it easy to understand the threat landscape and the mitigation strategies.
- Completeness: The document should comprehensively cover all aspects of the threat modeling process, including the system description, data flow diagrams, threat identification, risk assessment, and mitigation strategies. Leaving out critical information can render the model incomplete and ineffective.
- Accuracy: The information presented in the document must be accurate and up-to-date. Any assumptions made during the threat modeling process should be clearly documented.
- Traceability: Each identified threat should be traceable back to its source, such as the data flow diagram or the STRIDE analysis. This helps in understanding the origin of the threat and the rationale behind the mitigation strategies.
- Maintainability: The document should be designed to be easily updated and maintained. As the system evolves, the threat model needs to be updated to reflect the changes.
- Audience Consideration: The document should be tailored to its intended audience. For example, a technical audience might require more detailed information than a non-technical audience.
Threat Model Report Template
A standard template ensures consistency and completeness across different threat models. The following sections are typically included in a threat model report:
- Introduction: Provides an overview of the system, the scope of the threat modeling exercise, and the goals of the document.
- System Overview: Describes the system’s architecture, components, and functionality. This section should include data flow diagrams (DFDs) to visualize the data flow and identify potential attack surfaces.
A data flow diagram (DFD) visually represents the flow of data through a system. It helps identify potential vulnerabilities by highlighting how data moves between different components and external entities. For example, a DFD for an e-commerce website would show how customer data flows from the web browser to the server, database, and payment gateway.
- Threat Identification (STRIDE Analysis): Details the STRIDE analysis, including the identified threats, their corresponding attack vectors, and the affected assets. The results of the STRIDE analysis are often presented in a table format.
The STRIDE model helps categorize threats based on six categories: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. Each threat category represents a different type of potential attack. For instance, a spoofing threat might involve an attacker impersonating a legitimate user to gain unauthorized access to the system.
- Risk Assessment: Describes the risk assessment process, including the criteria used to prioritize threats (e.g., likelihood and impact). The results are presented in a risk matrix or table, showing the severity of each threat.
Risk assessment involves evaluating the likelihood of a threat materializing and the potential impact if it does. The risk assessment matrix typically uses a scale (e.g., low, medium, high) to categorize the risk level of each threat. This helps prioritize mitigation efforts. For example, a high-impact, high-likelihood threat would require immediate attention, whereas a low-impact, low-likelihood threat might be accepted as a risk.
- Mitigation Strategies: Artikels the proposed mitigation strategies for each identified threat, including specific actions to be taken and the responsible parties. This section should also include the expected outcomes of the mitigations.
Mitigation strategies involve implementing security controls to reduce the risk of identified threats. Examples include using strong authentication mechanisms, encrypting sensitive data, and implementing access controls. The effectiveness of these strategies is evaluated through continuous monitoring and testing. For example, implementing multi-factor authentication (MFA) mitigates the threat of spoofing by requiring multiple forms of verification.
- Recommendations: Provides recommendations for improving the security posture of the system, including suggestions for future threat modeling exercises and ongoing security monitoring.
- Appendix: Includes supporting documentation, such as the data flow diagrams, the risk assessment matrix, and any other relevant information.
Tools and Techniques for Threat Modeling
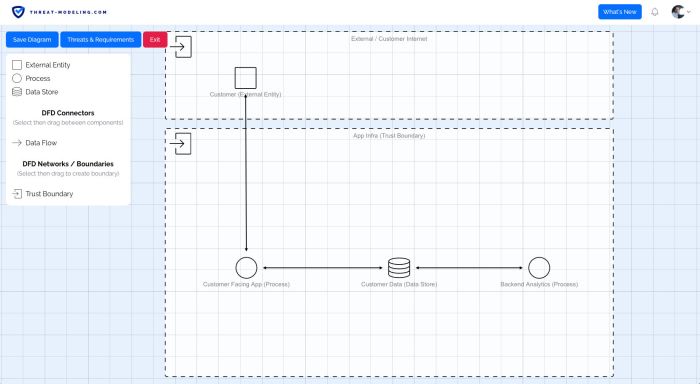
Threat modeling is significantly enhanced by the use of specialized tools and techniques. These resources streamline the process, automate certain tasks, and provide a structured approach to identifying and mitigating threats. The right tools can improve accuracy, efficiency, and the overall effectiveness of your threat modeling efforts.
Popular Threat Modeling Tools
Several tools are widely used for threat modeling, each with its strengths and weaknesses. Selecting the appropriate tool depends on factors such as project size, team expertise, and specific requirements.
- Microsoft Threat Modeling Tool: This tool, provided by Microsoft, is a popular choice, particularly for those working within the Microsoft ecosystem. It offers a user-friendly interface and is well-integrated with the STRIDE methodology.
- OWASP Threat Dragon: Developed by the Open Web Application Security Project (OWASP), Threat Dragon is an open-source threat modeling tool. It supports various threat modeling methodologies, including STRIDE, and is suitable for web applications and other software projects.
- Other Tools: Other tools available include commercial options like IriusRisk and cloud-based platforms that offer threat modeling capabilities as part of a larger security suite. Choosing the right tool depends on the project’s requirements.
Examples of Using Threat Modeling Tools
Using threat modeling tools involves several steps, including creating diagrams, identifying threats, and documenting mitigations. Here’s how some of the popular tools are used.
- Microsoft Threat Modeling Tool Example:
- Creating a Diagram: The user begins by creating a data flow diagram (DFD) that visually represents the application or system. The DFD illustrates how data flows between different components, such as processes, data stores, and external entities.
- Identifying Threats: Based on the DFD, the tool automatically suggests potential threats using the STRIDE model. The user reviews these suggestions and adds or modifies them as necessary. For instance, if a data store contains sensitive information, the tool might flag “Tampering” and “Information Disclosure” threats.
- Documenting Mitigations: For each identified threat, the user documents mitigation strategies. This might include implementing access controls, encrypting data, or validating user inputs. The tool allows the user to track the status of each mitigation and its implementation.
- OWASP Threat Dragon Example:
- Creating a Diagram: The user can create diagrams representing the system’s architecture. Threat Dragon supports various diagramming options.
- Identifying Threats: Using the diagram, the user identifies threats based on the chosen threat modeling methodology (e.g., STRIDE). The tool assists in generating threat suggestions.
- Documenting Mitigations: The user documents the proposed mitigations for each identified threat, detailing the actions and controls to be implemented. Threat Dragon allows for tracking the status of these mitigations.
Integrating Threat Modeling into the Development Lifecycle
Integrating threat modeling into the development lifecycle ensures that security is considered throughout the software development process. This proactive approach helps identify and address vulnerabilities early on, reducing the cost and effort of remediation.
- Requirement Phase: Threat modeling can start during the requirements phase. By analyzing requirements, potential security risks associated with the intended functionality can be identified early.
- Design Phase: During the design phase, developers can use threat modeling to create secure architectures and identify potential vulnerabilities in the system’s design.
- Implementation Phase: Threat modeling can be used to review code, identify vulnerabilities, and ensure that security controls are implemented correctly.
- Testing Phase: Security testing, including penetration testing and vulnerability scanning, can validate the effectiveness of implemented security controls.
- Deployment and Maintenance Phase: Threat modeling is an ongoing process. As the system evolves, threat models need to be updated to reflect new functionality, changes in the threat landscape, and emerging vulnerabilities.
Integrating Threat Modeling into SDLC
Integrating threat modeling into the Software Development Life Cycle (SDLC) is crucial for proactively identifying and mitigating security vulnerabilities throughout the development process. This integration ensures that security considerations are not an afterthought but are embedded from the initial planning stages through deployment and maintenance. This proactive approach helps to reduce the cost and effort associated with fixing security issues later in the SDLC, when they are often more complex and expensive to address.
Incorporating Threat Modeling into SDLC Stages
Threat modeling should be incorporated at various stages of the SDLC to ensure comprehensive security coverage. This allows for the identification of threats and the implementation of appropriate mitigation strategies at each stage.
- Requirements Phase: Threat modeling begins with understanding the system’s intended functionality and the potential threats it might face. This stage involves:
- Defining security requirements: Explicitly stating security goals and requirements, such as confidentiality, integrity, and availability.
- Identifying assets: Determining the valuable assets that need protection, including data, systems, and functionalities.
- Analyzing the threat landscape: Understanding the potential attackers, their motivations, and the threats they might pose.
- Design Phase: During the design phase, threat modeling informs architectural decisions and helps identify potential vulnerabilities in the system’s design. This includes:
- Creating data flow diagrams (DFDs): Visualizing the movement of data through the system to identify potential attack vectors.
- Applying STRIDE to design elements: Using STRIDE to analyze the design and identify potential threats like Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege.
- Designing security controls: Implementing security controls to mitigate identified threats, such as authentication, authorization, and encryption.
- Implementation Phase: Threat modeling guides secure coding practices and helps identify vulnerabilities introduced during the implementation phase. This includes:
- Secure coding guidelines: Adhering to secure coding standards and guidelines to prevent common vulnerabilities like SQL injection and cross-site scripting (XSS).
- Code reviews: Conducting code reviews to identify and address security flaws in the code.
- Static and dynamic analysis: Using static and dynamic analysis tools to identify potential vulnerabilities.
- Testing Phase: Threat modeling informs the development of security tests and helps to validate the effectiveness of security controls. This includes:
- Developing security test cases: Creating test cases to verify that the implemented security controls are effective.
- Penetration testing: Conducting penetration testing to simulate real-world attacks and identify vulnerabilities.
- Vulnerability scanning: Regularly scanning the system for known vulnerabilities.
- Deployment and Maintenance Phase: Threat modeling helps to ensure that the system remains secure after deployment and during its lifecycle. This includes:
- Configuration management: Properly configuring the system and its components to minimize vulnerabilities.
- Monitoring and logging: Implementing monitoring and logging to detect and respond to security incidents.
- Incident response: Establishing an incident response plan to address security breaches.
- Regular security assessments: Conducting regular security assessments to identify and address new vulnerabilities.
Integrating Threat Modeling into Agile and Waterfall Methodologies
Threat modeling can be effectively integrated into both Agile and Waterfall methodologies, although the approach may vary slightly.
- Waterfall Methodology: In the Waterfall model, threat modeling is typically performed at the requirements and design phases. This is because the Waterfall model is a sequential process, with each phase completed before the next one begins.
- Requirements Phase: Threat modeling is used to define security requirements and identify potential threats.
- Design Phase: Threat modeling is used to inform architectural decisions and identify vulnerabilities in the design.
- Implementation Phase: Secure coding practices are followed based on the threat model.
- Testing Phase: Security testing is performed to validate the effectiveness of the implemented security controls.
- Deployment and Maintenance Phase: Regular security assessments are conducted to identify and address new vulnerabilities.
- Agile Methodology: In Agile, threat modeling is integrated into sprints and is an iterative process. This allows for flexibility and adaptation as the project evolves.
- Sprint Planning: Threat modeling is used to identify and prioritize security tasks for each sprint.
- Sprint Execution: Threat modeling is used to guide secure coding practices and identify vulnerabilities.
- Sprint Review: Security testing is performed to validate the effectiveness of the implemented security controls.
- Retrospectives: Lessons learned from threat modeling and security testing are used to improve the process in future sprints.
Best Practices for Continuous Threat Modeling
Continuous threat modeling involves regularly assessing and updating the threat model throughout the SDLC to ensure that it remains relevant and effective.
- Automate Threat Modeling: Automate threat modeling tasks where possible. Use tools that can automatically generate data flow diagrams (DFDs) and identify potential threats. This can significantly reduce the time and effort required for threat modeling.
- Integrate with CI/CD Pipeline: Integrate threat modeling into the Continuous Integration/Continuous Deployment (CI/CD) pipeline. This ensures that threat modeling is performed automatically whenever code changes are made.
- Use Threat Modeling as a Service (TMaaS): TMaaS solutions provide automated threat modeling capabilities. These services can help to streamline the threat modeling process and make it more accessible to development teams.
- Regularly Update the Threat Model: Threat models should be updated regularly to reflect changes in the system, the threat landscape, and the security requirements. This includes reviewing and updating the threat model after each sprint in Agile methodologies or after significant changes in Waterfall methodologies.
- Train and Educate Teams: Provide training and education to development teams on threat modeling principles and best practices. This ensures that team members understand how to identify and mitigate threats.
- Establish Metrics and Measure Effectiveness: Establish metrics to measure the effectiveness of threat modeling efforts. Track the number of vulnerabilities identified and mitigated, the time spent on threat modeling, and the cost of fixing security issues.
- Foster Collaboration: Encourage collaboration between development, security, and operations teams. This ensures that everyone is aware of the threats and the mitigation strategies.
Advanced Threat Modeling Concepts

The realm of threat modeling extends beyond basic application security and requires adaptation for modern architectures. This section explores advanced threat modeling techniques, specifically focusing on cloud environments and microservices, to equip you with the knowledge to secure complex systems. Understanding these concepts is crucial for proactively identifying and mitigating potential risks in evolving technological landscapes.
Threat Modeling in Cloud Environments
Cloud environments introduce unique challenges to threat modeling due to their distributed nature, shared responsibility models, and reliance on third-party services. Effective threat modeling in the cloud requires a deep understanding of cloud-specific threats and the services provided by cloud providers.
- Shared Responsibility Model: Cloud providers and their customers share responsibility for security. The provider secures the underlying infrastructure, while the customer is responsible for securing the data, applications, and configurations they deploy. This shared model necessitates clearly defined boundaries and communication to ensure comprehensive security coverage. Threat modeling must explicitly address this division of responsibility, mapping threats to the relevant party.
- Cloud-Specific Threats: Several threats are unique to cloud environments, including:
- Data Breaches: Unauthorized access to sensitive data stored in the cloud. This can be caused by misconfigurations, weak access controls, or compromised credentials.
- Account Hijacking: Gaining unauthorized access to a cloud account, allowing attackers to control resources and steal data.
- Denial-of-Service (DoS) Attacks: Overwhelming cloud resources, making them unavailable to legitimate users.
- Insider Threats: Malicious or negligent actions by cloud provider employees or authorized users.
- API Vulnerabilities: Exploiting vulnerabilities in cloud provider APIs to gain unauthorized access or control.
- Threat Modeling Methodologies for Cloud: While STRIDE remains a useful framework, it can be adapted and augmented with cloud-specific considerations. Techniques like using cloud-specific threat libraries (e.g., those provided by cloud providers) and focusing on the specific services used (e.g., AWS S3, Azure Blob Storage, Google Cloud Storage) are essential.
- Automated Threat Modeling: Consider the use of automated tools and frameworks that are designed to analyze cloud configurations and identify potential vulnerabilities. These tools can help to streamline the threat modeling process and identify misconfigurations that could lead to security breaches.
Threat Modeling for Microservices
Microservices architectures, with their distributed nature and independent deployments, present a different set of challenges for threat modeling compared to monolithic applications. The focus shifts from a single application to a network of interconnected services.
- Distributed Nature: Microservices are deployed independently and communicate over a network, typically using APIs. This distributed nature increases the attack surface and complicates threat modeling.
- API Security: APIs are the primary interface for communication between microservices. Securing APIs is paramount.
- Authentication and Authorization: Ensuring that only authorized users and services can access specific APIs and resources.
- Input Validation: Validating all input to prevent injection attacks and other vulnerabilities.
- Rate Limiting: Preventing abuse and denial-of-service attacks by limiting the number of requests from a single source.
- API Gateway: Implementing an API gateway to manage and secure API traffic.
- Service Discovery and Communication Security: Ensuring secure communication between services is crucial.
- Service Discovery: Securely managing how services find and communicate with each other.
- Encryption: Encrypting all communication between services, using TLS or other encryption protocols.
- Service Mesh: Using a service mesh to manage and secure inter-service communication, including authentication, authorization, and traffic management.
- Data Consistency and Integrity: Maintaining data consistency and integrity across multiple microservices.
- Distributed Transactions: Implementing distributed transactions to ensure that data changes are consistent across multiple services.
- Eventual Consistency: Using eventual consistency patterns to handle data updates in a distributed environment.
- Data Validation: Validating data to ensure its integrity.
- Continuous Integration and Continuous Deployment (CI/CD): Integrate threat modeling into the CI/CD pipeline to identify and address vulnerabilities early in the development process.
Illustrative Diagram: Cloud-Based System with Threats and Mitigations
The following diagram illustrates a cloud-based e-commerce system and its associated threats and mitigations.
Diagram Description: The diagram depicts a cloud-based e-commerce system. At the center is a cloud symbol, representing the overall cloud infrastructure. Surrounding this are various components, each with labeled threats and mitigations. The components include:
- Web Application: Represented by a web browser icon. Threats: SQL Injection, Cross-Site Scripting (XSS). Mitigations: Input validation, output encoding.
- API Gateway: Depicted as a gateway symbol. Threats: API Abuse, DDoS attacks. Mitigations: Rate limiting, API authentication.
- Microservices (Order, Product, Payment): Represented by three separate service icons. Threats: Service compromise, data breaches. Mitigations: Encryption in transit, strong authentication, authorization.
- Database: Represented by a database icon. Threats: Data breaches, unauthorized access. Mitigations: Encryption at rest, access control lists (ACLs).
- CDN: Represented by a CDN icon. Threats: DDoS attacks, content poisoning. Mitigations: DDoS protection, content integrity checks.
- Cloud Provider’s Infrastructure: Encompassing all the above. Threats: Misconfigurations, insider threats. Mitigations: Regular security audits, access controls, and configuration management.
Each threat is linked to the component where it’s most likely to occur, and mitigations are shown as solutions implemented within or around those components. The connections between components illustrate data flow and potential attack vectors.
Table of Threats and Mitigations:
| Component | Threat | Mitigation |
|---|---|---|
| Web Application | SQL Injection | Input validation, parameterized queries |
| Web Application | Cross-Site Scripting (XSS) | Output encoding |
| API Gateway | API Abuse | Rate limiting, API authentication |
| API Gateway | DDoS Attacks | DDoS protection |
| Microservices (Order, Product, Payment) | Service Compromise | Encryption in transit, strong authentication |
| Microservices (Order, Product, Payment) | Data Breaches | Authorization, access controls |
| Database | Data Breaches | Encryption at rest |
| Database | Unauthorized Access | Access control lists (ACLs) |
| CDN | DDoS Attacks | DDoS protection |
| CDN | Content Poisoning | Content integrity checks |
| Cloud Provider’s Infrastructure | Misconfigurations | Regular security audits |
| Cloud Provider’s Infrastructure | Insider Threats | Access controls, configuration management |
Real-World Examples of STRIDE in Action
Applying STRIDE in real-world scenarios demonstrates its effectiveness in identifying and mitigating security vulnerabilities. These examples highlight how STRIDE has been used across various industries and applications to proactively address potential threats, ultimately safeguarding sensitive information and critical systems. The following case studies showcase practical applications, lessons learned, and the tangible benefits of employing STRIDE as a core component of a robust security strategy.
Case Study: E-commerce Platform Security Enhancement
An e-commerce platform, handling millions of transactions daily, adopted STRIDE to enhance its security posture. This initiative aimed to identify and address potential vulnerabilities before they could be exploited by malicious actors.
- Objective: To identify and mitigate potential threats to the e-commerce platform’s security, focusing on sensitive customer data and financial transactions.
- STRIDE Application: The development team conducted a threat modeling session using STRIDE. They analyzed the platform’s architecture, including web servers, databases, payment gateways, and customer-facing applications. Each component was assessed against the STRIDE categories: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege.
- Threat Identification: The analysis revealed several potential threats:
- Spoofing: The potential for attackers to impersonate legitimate users or the platform itself.
- Tampering: The risk of unauthorized modification of transaction data or website content.
- Repudiation: The possibility of users denying their transactions or actions.
- Information Disclosure: The risk of exposing sensitive customer data, such as credit card details or personal information.
- Denial of Service: The potential for attackers to disrupt the platform’s availability, rendering it inaccessible to users.
- Elevation of Privilege: The risk of attackers gaining unauthorized access to administrative functions or sensitive resources.
- Mitigation Strategies: Based on the identified threats, the team implemented various mitigation strategies:
- Spoofing: Implementing multi-factor authentication (MFA) for user logins and API authentication.
- Tampering: Employing cryptographic signatures to verify data integrity and using web application firewalls (WAFs) to protect against malicious attacks.
- Repudiation: Implementing detailed audit logs and transaction records to provide an irrefutable record of all actions.
- Information Disclosure: Encrypting sensitive data at rest and in transit, and implementing strict access controls.
- Denial of Service: Implementing rate limiting, content delivery networks (CDNs), and robust infrastructure to handle high traffic loads.
- Elevation of Privilege: Implementing least privilege access control, regular security audits, and penetration testing.
- Outcome: By proactively identifying and mitigating threats, the e-commerce platform significantly reduced its attack surface. The implemented security measures protected the platform from several attempted attacks, prevented data breaches, and maintained customer trust. The application of STRIDE led to a more secure and resilient platform.
Case Study: Mobile Application Security Assessment
A mobile application development company used STRIDE to assess the security of a new application designed for managing sensitive user data. This involved a thorough analysis of the application’s architecture, data flow, and potential vulnerabilities.
- Objective: To identify and address potential security vulnerabilities within the mobile application before its public release.
- STRIDE Application: The development team conducted a STRIDE-based threat modeling exercise. They mapped out the application’s components, including user interfaces, data storage, network communication, and backend services. They analyzed each component against the STRIDE threat categories.
- Threat Identification: The threat modeling process revealed several critical vulnerabilities:
- Spoofing: The potential for attackers to impersonate legitimate users or the application itself.
- Tampering: The risk of unauthorized modification of the application’s code or data.
- Repudiation: The possibility of users denying their actions within the application.
- Information Disclosure: The risk of exposing sensitive user data, such as personal information or financial details.
- Denial of Service: The potential for attackers to disrupt the application’s functionality, making it unavailable to users.
- Elevation of Privilege: The risk of attackers gaining unauthorized access to sensitive features or data.
- Mitigation Strategies: The development team implemented various mitigation strategies:
- Spoofing: Implementing robust authentication mechanisms, including multi-factor authentication and device verification.
- Tampering: Implementing code signing, integrity checks, and obfuscation techniques to protect the application’s code and data.
- Repudiation: Implementing detailed audit logs to track user actions and transactions.
- Information Disclosure: Encrypting sensitive data at rest and in transit, implementing secure data storage practices, and minimizing data exposure.
- Denial of Service: Implementing rate limiting, resource allocation controls, and load balancing to protect against denial-of-service attacks.
- Elevation of Privilege: Implementing strict access controls, regular security audits, and penetration testing.
- Outcome: The application was released with significantly improved security. The STRIDE-based threat modeling process helped identify and mitigate several critical vulnerabilities, reducing the risk of data breaches and ensuring user trust. The application’s security was significantly enhanced, leading to a more secure and reliable user experience.
Case Study: Cloud Infrastructure Security
A company migrating its infrastructure to the cloud used STRIDE to assess and improve the security of its cloud environment. This involved analyzing the cloud services, data flows, and potential attack vectors.
- Objective: To identify and mitigate security risks associated with the company’s cloud infrastructure.
- STRIDE Application: The security team conducted a threat modeling exercise using STRIDE. They mapped out the cloud architecture, including virtual machines, storage services, databases, and network configurations. Each component was analyzed against the STRIDE categories.
- Threat Identification: The analysis revealed several potential threats:
- Spoofing: The potential for attackers to impersonate legitimate users or cloud resources.
- Tampering: The risk of unauthorized modification of cloud resources or data.
- Repudiation: The possibility of users denying their actions within the cloud environment.
- Information Disclosure: The risk of exposing sensitive data stored in the cloud.
- Denial of Service: The potential for attackers to disrupt the availability of cloud services.
- Elevation of Privilege: The risk of attackers gaining unauthorized access to cloud resources or administrative functions.
- Mitigation Strategies: The team implemented several mitigation strategies:
- Spoofing: Implementing multi-factor authentication, strong identity and access management (IAM) policies, and network segmentation.
- Tampering: Implementing data encryption, version control, and infrastructure-as-code practices to protect against unauthorized modifications.
- Repudiation: Implementing comprehensive logging and auditing to track all actions within the cloud environment.
- Information Disclosure: Encrypting data at rest and in transit, implementing data loss prevention (DLP) measures, and securing storage buckets.
- Denial of Service: Implementing rate limiting, autoscaling, and DDoS protection services.
- Elevation of Privilege: Implementing the principle of least privilege, regular security audits, and vulnerability scanning.
- Outcome: By proactively addressing the identified threats, the company significantly improved the security of its cloud infrastructure. The implemented measures helped prevent data breaches, maintain the availability of cloud services, and ensure compliance with security best practices. The application of STRIDE resulted in a more secure and resilient cloud environment.
Conclusion
In conclusion, understanding what is a threat modeling process like STRIDE is paramount for any organization committed to robust cybersecurity. From identifying threats using the STRIDE framework to implementing effective mitigation strategies, the process equips developers with the knowledge and tools to build secure and reliable software. By integrating threat modeling into the Software Development Life Cycle, organizations can proactively protect their assets and minimize the risk of security breaches.
Embracing STRIDE empowers you to build more secure and resilient applications, safeguarding against potential threats and ensuring the integrity of your systems.
Essential FAQs
What is the primary goal of threat modeling?
The primary goal is to identify and mitigate potential security threats to a system or application before they can be exploited, leading to a more secure and robust design.
How does STRIDE help in threat modeling?
STRIDE provides a structured framework for categorizing threats based on the security goals they violate, making it easier to systematically identify potential vulnerabilities within a system.
What are some common tools used for threat modeling?
Popular tools include the Microsoft Threat Modeling Tool, OWASP Threat Dragon, and various open-source and commercial options that assist in visualizing and analyzing potential threats.
How can I integrate threat modeling into the SDLC?
Integrate threat modeling into various stages of the SDLC, such as requirements gathering, design, coding, testing, and deployment, to ensure security is considered throughout the development process.