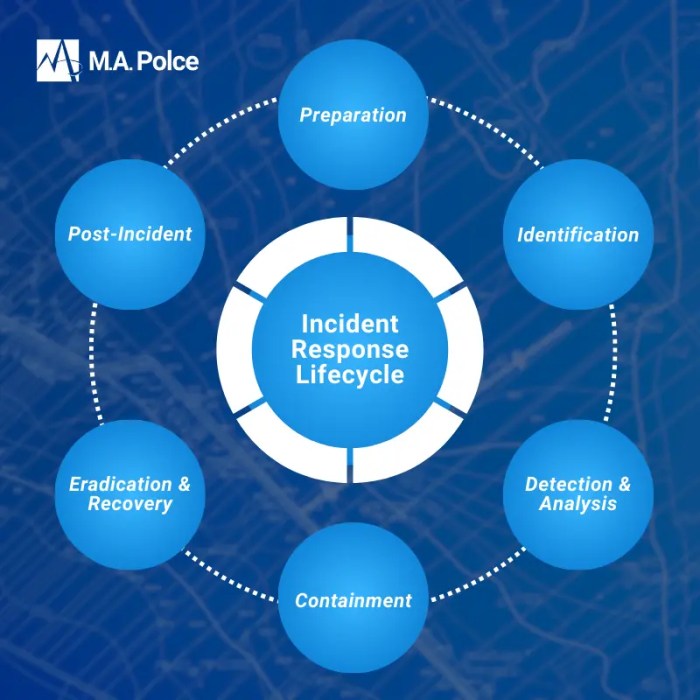
Embark on a journey into the realm of data security with a focus on Key Management Services (KMS). In today’s digital landscape, safeguarding sensitive information is paramount. This exploration delves into the essential role KMS plays in protecting your valuable data, ensuring its confidentiality, integrity, and availability.
A Key Management Service (KMS) is a centralized system designed to manage cryptographic keys. It provides a secure and efficient way to generate, store, rotate, and control access to these keys, which are crucial for encrypting and decrypting data. KMS is essential in various scenarios, such as securing financial transactions, protecting sensitive customer data, and ensuring compliance with industry regulations.
From safeguarding cloud storage to encrypting databases, a KMS acts as the gatekeeper, ensuring only authorized users can access protected information.
Introduction to Key Management Service (KMS)
In today’s digital world, protecting sensitive information is paramount. From personal data to financial records and intellectual property, the need for robust security measures is constantly growing. A Key Management Service (KMS) plays a crucial role in this effort, providing a secure and centralized way to manage the cryptographic keys that protect our data.A Key Management Service (KMS) is a system that provides centralized control over cryptographic keys.
It allows organizations to generate, store, rotate, and manage these keys securely. The primary function of a KMS is to protect the confidentiality and integrity of sensitive data by controlling the lifecycle of cryptographic keys. This includes tasks like key creation, storage, rotation, revocation, and auditing.
Essential Data Security Scenarios
Data security is critical across various industries and applications. A KMS is particularly essential in scenarios where data confidentiality and integrity are of utmost importance. Here are some real-world examples:
- Database Encryption: Organizations often encrypt sensitive data stored in databases, such as customer information or financial transactions. A KMS is used to manage the encryption keys, ensuring that only authorized users can access the data. This protects against data breaches and unauthorized access. For instance, a financial institution uses a KMS to encrypt customer account details stored in its database.
If the database is compromised, the encrypted data remains unreadable without the decryption keys managed by the KMS.
- Cloud Storage Security: Many businesses store data in the cloud. A KMS helps secure data stored in cloud environments by managing the encryption keys used to protect the data at rest and in transit. This is especially crucial for companies handling sensitive data like medical records or legal documents. For example, a healthcare provider utilizes a KMS to encrypt patient medical records stored in a cloud-based storage service.
The KMS ensures that the data is encrypted with keys controlled by the provider, meeting HIPAA compliance requirements.
- Payment Processing: E-commerce platforms and payment gateways rely heavily on secure key management to protect credit card information and other financial data. A KMS is used to generate, store, and manage the encryption keys used to encrypt sensitive payment details. This protects against fraud and ensures compliance with payment card industry (PCI) standards. A payment processor uses a KMS to protect credit card numbers during transactions.
The KMS securely manages the keys used to encrypt the cardholder data, reducing the risk of data breaches and fraud.
- Application Encryption: Software developers often integrate encryption into their applications to protect sensitive data. A KMS provides a secure way to manage the encryption keys used by these applications. This can include encrypting data stored within the application or securing communications between the application and other systems. For example, a software company uses a KMS to manage encryption keys for securing the data stored in its enterprise resource planning (ERP) system.
This ensures the confidentiality of sensitive business information.
Core Components of a KMS
A Key Management Service (KMS) is comprised of several critical components that work together to ensure the secure generation, storage, use, and management of cryptographic keys. Understanding these core components is crucial to appreciating the overall functionality and security of a KMS. This section details these essential elements.
Key Components of a KMS Architecture
The architecture of a KMS typically includes several interconnected components. These components work together to provide a comprehensive key management solution.
- Key Generation: This component is responsible for creating cryptographic keys. These keys can be symmetric or asymmetric, depending on the application. Key generation often involves the use of a Hardware Security Module (HSM) to ensure the keys are generated and protected in a secure environment.
- Key Storage: This component securely stores cryptographic keys. It is essential to protect these keys from unauthorized access. This storage can take various forms, including HSMs, dedicated key vaults, or encrypted databases.
- Key Usage: This component handles the use of keys for cryptographic operations, such as encryption, decryption, signing, and verification. It provides an interface for applications to access and utilize the keys in a secure manner.
- Key Rotation: This component automates the process of replacing cryptographic keys on a regular basis. Key rotation is a critical security practice that minimizes the impact of a compromised key.
- Access Control and Authorization: This component manages access to keys and cryptographic operations. It enforces policies to ensure that only authorized users and applications can access and use keys. This often involves role-based access control (RBAC) and other security mechanisms.
- Auditing and Logging: This component logs all key-related activities, including key generation, access, and rotation. This information is crucial for security auditing, compliance, and incident response.
- Administration Interface: This component provides a user interface for managing keys, policies, and other KMS configurations. It allows administrators to perform tasks such as creating and deleting keys, defining access control policies, and monitoring key usage.
Role of Cryptographic Keys within a KMS
Cryptographic keys are the fundamental building blocks of any KMS. Their primary function is to protect sensitive data by enabling encryption and decryption, signing and verification, and other cryptographic operations. The security of the entire system depends on the secure management of these keys.
The role of cryptographic keys can be summarized as:
- Data Encryption and Decryption: Keys are used to encrypt sensitive data, making it unreadable to unauthorized parties. They are also used to decrypt the data, allowing authorized users to access it.
- Digital Signatures: Keys are used to create digital signatures, which verify the authenticity and integrity of data. This ensures that the data has not been tampered with and that it originates from a trusted source.
- Authentication: Keys can be used for authentication purposes, such as verifying the identity of users or devices.
- Access Control: Keys can be used to control access to resources and data. For example, only users with the appropriate keys can access encrypted data.
Functions of Key Storage, Key Generation, and Key Rotation within a KMS
These three functions – key storage, key generation, and key rotation – are fundamental to the operation and security of a KMS. They each play a critical role in protecting cryptographic keys and the data they protect.
- Key Storage: The secure storage of cryptographic keys is paramount. Keys must be protected from unauthorized access, use, and modification. Key storage mechanisms often involve:
- Hardware Security Modules (HSMs): These are dedicated hardware devices that provide a secure environment for key generation, storage, and cryptographic operations. HSMs are designed to be tamper-resistant and provide strong protection against physical and logical attacks.
- Key Vaults: These are centralized repositories for storing and managing cryptographic keys. They provide features such as access control, key rotation, and auditing.
- Encrypted Databases: Keys can be stored in encrypted databases, with access to the database and the encryption keys tightly controlled.
- Key Generation: The process of generating cryptographic keys must be performed securely. The following considerations are crucial:
- Randomness: Keys must be generated using a strong random number generator (RNG) to ensure their unpredictability.
- Entropy: The RNG should have access to sufficient entropy (randomness) to generate keys that are cryptographically secure.
- Key Types and Lengths: The choice of key type (e.g., symmetric or asymmetric) and key length (e.g., 128-bit, 256-bit) should be appropriate for the intended use case and the level of security required.
- Key Rotation: Regularly rotating cryptographic keys is a crucial security practice. Key rotation involves replacing existing keys with new ones. This practice helps to:
- Minimize the Impact of Compromise: If a key is compromised, rotating it limits the amount of data that can be decrypted or accessed using the compromised key.
- Adhere to Compliance Requirements: Many regulatory standards and compliance frameworks require regular key rotation.
- Reduce the Risk of Key Exposure: Rotating keys reduces the time a key is in use and therefore the potential for it to be exposed.
Key rotation can be automated by the KMS, or it can be performed manually. Automated key rotation typically involves a pre-defined schedule and automated key lifecycle management.
Benefits of Using a KMS

Employing a Key Management Service (KMS) offers significant advantages in data protection, key lifecycle management, and overall security posture. A well-implemented KMS provides a centralized and secure method for managing cryptographic keys, leading to improved efficiency and reduced risk. This section explores the specific benefits of using a KMS, contrasting it with alternative key management approaches and highlighting its simplification of key lifecycle processes.
Enhanced Data Protection with a KMS
A KMS strengthens data protection by centralizing key management and enforcing robust security policies. This approach minimizes the attack surface and reduces the likelihood of unauthorized key access or compromise.
- Centralized Key Storage: A KMS securely stores cryptographic keys in a protected environment, often using hardware security modules (HSMs) or other security-hardened systems. This centralized approach simplifies key management and provides a single point of control.
- Access Control and Authorization: KMS solutions provide granular access control, allowing administrators to define who can access and use specific keys. This prevents unauthorized key usage and ensures that only authorized personnel can perform cryptographic operations.
- Auditing and Monitoring: KMS solutions offer comprehensive auditing capabilities, tracking key usage, access attempts, and changes to key policies. This provides valuable insights into key activities and helps identify potential security breaches or policy violations.
- Compliance: A KMS helps organizations meet regulatory compliance requirements, such as those related to data encryption and key management. It provides the necessary tools and controls to demonstrate compliance with standards like PCI DSS, HIPAA, and GDPR.
Comparison of KMS with Other Key Management Approaches
Compared to alternative key management approaches, a KMS offers superior security and efficiency, particularly in complex environments. Other approaches, such as manual key management or using application-specific key stores, often present significant security and operational challenges.
- Manual Key Management: Managing keys manually, such as storing them in configuration files or spreadsheets, is highly susceptible to human error and security breaches. This approach lacks proper access controls, auditing capabilities, and secure storage, making it unsuitable for protecting sensitive data.
- Application-Specific Key Stores: Embedding keys directly within applications or using application-specific key stores can lead to key sprawl and inconsistent key management practices. This approach complicates key rotation, access control, and auditing, increasing the risk of key compromise.
- KMS Advantages: A KMS offers a centralized, secure, and automated approach to key management. It provides robust security features, such as hardware security modules (HSMs), access controls, and auditing, to protect cryptographic keys. KMS also simplifies key lifecycle management, including key generation, rotation, and revocation.
Simplification of Key Lifecycle Management with a KMS
A KMS streamlines the key lifecycle, making it easier to manage keys from creation to destruction. This automation reduces manual effort, minimizes the risk of errors, and ensures that keys are properly protected throughout their lifespan.
- Key Generation: A KMS can generate cryptographic keys securely and randomly, using industry-standard algorithms and best practices. This eliminates the need for manual key generation, which can be error-prone and less secure.
- Key Rotation: Key rotation is a critical security practice that involves regularly changing cryptographic keys to minimize the impact of key compromise. A KMS automates key rotation, making it easy to schedule and execute key rotations on a regular basis. For instance, many organizations rotate their encryption keys quarterly or annually, and a KMS simplifies this process significantly.
- Key Revocation: If a key is compromised or suspected of being compromised, it must be revoked to prevent further unauthorized access. A KMS provides a mechanism for revoking keys quickly and efficiently, ensuring that the compromised key can no longer be used to decrypt data or perform cryptographic operations.
- Key Archival and Destruction: A KMS enables the secure archival and destruction of cryptographic keys when they are no longer needed. This ensures that keys are properly disposed of, preventing them from being recovered and misused. Secure key destruction often involves overwriting the key material or physically destroying the HSM where the key is stored.
Key Lifecycle Management with KMS
Key lifecycle management is a crucial aspect of any robust KMS implementation. It encompasses the entire journey of a cryptographic key, from its inception to its eventual decommissioning. Effective management ensures the confidentiality, integrity, and availability of sensitive data by controlling the key’s usage, storage, and access throughout its lifespan. This section will delve into the phases of a key lifecycle, key rotation strategies, and best practices for secure key disposal within a KMS environment.
Design of a Key Lifecycle
The key lifecycle defines the stages a cryptographic key goes through. A well-defined lifecycle is essential for maintaining key security and compliance with regulatory requirements.The key lifecycle typically consists of the following phases:* Generation: This is the initial phase where the key is created. The KMS utilizes a secure random number generator (RNG) to produce the key material.
The generation process often includes specifying the key type (e.g., symmetric or asymmetric), the algorithm (e.g., AES, RSA), and the key length.* Registration/Activation: Once generated, the key is registered within the KMS. This involves associating the key with metadata, such as a unique identifier, a description, and access control policies. Activation makes the key available for use in cryptographic operations.* Storage: The key is securely stored within the KMS’s protected environment.
This typically involves hardware security modules (HSMs) or other secure storage mechanisms to prevent unauthorized access. Access to the key is strictly controlled and audited.* Usage: This is the operational phase where the key is used for cryptographic operations, such as encryption, decryption, digital signing, and verification. The KMS controls the key’s usage based on defined policies and access controls.* Rotation: Periodic key rotation is a security best practice.
It involves generating a new key and transitioning the workload from the old key to the new one. This limits the impact of a potential key compromise. The old key may be retained for a specific period to decrypt old data if necessary.* Revocation: In the event of a suspected key compromise or policy violation, the key can be revoked.
Revocation prevents the key from being used for further cryptographic operations.* Deactivation: The key is deactivated when it is no longer needed for active use. This might involve disabling the key’s access to data or services. The deactivated key may still be available for decryption of old data, but it can no longer be used for new encryption.* Destruction: This is the final phase where the key material is permanently destroyed.
This process ensures that the key cannot be recovered and prevents any potential future misuse. Secure destruction methods are employed, such as overwriting the key material with random data or physically destroying the HSM.
Key Rotation within a KMS Environment
Key rotation is a critical security practice that involves regularly changing cryptographic keys to reduce the risk associated with key compromise. Implementing key rotation within a KMS environment involves several steps.Here are the steps involved in key rotation:
1. Key Generation
A new key is generated within the KMS. This key is created with the appropriate key type, algorithm, and length.
2. Key Activation
The new key is activated and registered within the KMS, allowing it to be used for cryptographic operations.
3. Data Re-encryption (if applicable)
Existing data encrypted with the old key may need to be re-encrypted with the new key. This ensures that the data remains protected by the latest key. The KMS facilitates this process, often through automated re-encryption capabilities.
4. Application Configuration
Applications that use the key must be configured to use the new key for encryption and decryption operations. This configuration change should be carefully planned and tested to minimize disruption.
5. Key Transition
A gradual transition period allows for a smooth switch from the old key to the new key. During this period, both keys may be used, allowing for flexibility and ensuring that all data is eventually encrypted with the new key.
6. Old Key Deactivation
Once the transition is complete, the old key is deactivated within the KMS. This prevents any new data from being encrypted with the old key. The old key may be retained for a specific period to decrypt archived data if necessary.
7. Key Archival (if applicable)
The old key may be archived, potentially with the associated metadata, for audit and recovery purposes.
8. Key Destruction
After a predetermined period, the old key is securely destroyed, ensuring that it cannot be recovered.
Best Practices for Secure Key Disposal
Secure key disposal is as important as the key’s generation and storage. Proper disposal ensures that the key material cannot be recovered, preventing unauthorized access to sensitive data.Here are some best practices for secure key disposal:* Secure Erase: Implement secure erase mechanisms to overwrite the key material with random data multiple times. This process ensures that the key data is unrecoverable.* Physical Destruction: For keys stored in hardware, such as HSMs, physical destruction is a reliable method.
This involves physically destroying the hardware containing the key material.* Key Shredding: In some cases, key material may be stored in documents or other physical media. Shredding or other forms of destruction should be used to render the key data unreadable.* Compliance with Regulations: Ensure that key disposal practices comply with relevant industry regulations and standards, such as NIST guidelines or PCI DSS requirements.* Audit Trails: Maintain comprehensive audit trails of key disposal activities.
This includes recording the date, time, method, and personnel involved in the disposal process.* Verification: Verify the key destruction process to confirm that the key material has been securely erased or destroyed. This may involve using tools or techniques to validate the destruction.* Documentation: Document all key disposal procedures and processes to ensure consistency and repeatability.* Regular Review: Regularly review and update key disposal practices to adapt to evolving security threats and technological advancements.
KMS Deployment Models

Choosing the right deployment model for a Key Management Service (KMS) is a critical decision that significantly impacts an organization’s security posture, operational efficiency, and compliance with industry regulations. The selection depends on factors such as the organization’s existing infrastructure, security requirements, budget constraints, and the level of control desired over cryptographic keys. Different deployment models offer varying trade-offs, making it essential to understand their characteristics and implications.
On-Premise KMS
An on-premise KMS involves deploying and managing the KMS software and hardware within the organization’s own data center. This model offers the highest level of control over the key management infrastructure, as the organization is responsible for all aspects of its operation, including physical security, access controls, and software updates.The advantages of an on-premise KMS include:
- Enhanced Control: The organization has complete control over the key management environment, ensuring that keys and related data remain within its direct control.
- Customization: It allows for extensive customization to meet specific security requirements and integration needs.
- Compliance: It can be easier to meet strict compliance requirements, particularly for industries with stringent data residency or regulatory obligations.
- Reduced Latency: For applications within the same data center, on-premise KMS can offer lower latency compared to cloud-based solutions.
The disadvantages of an on-premise KMS include:
- High Initial Investment: Requires significant upfront investment in hardware, software, and infrastructure.
- Ongoing Management: Demands dedicated IT staff and resources for maintenance, updates, and security management.
- Scalability Challenges: Scaling the KMS infrastructure can be complex and time-consuming, requiring careful planning and potentially costly upgrades.
- Physical Security: The organization is responsible for the physical security of the KMS hardware, including access control, environmental controls, and disaster recovery.
Cloud-Based KMS
A cloud-based KMS is hosted and managed by a third-party cloud provider, such as Amazon Web Services (AWS), Microsoft Azure, or Google Cloud Platform (GCP). Organizations access the KMS through an API or web interface, offloading the operational burden of key management to the provider.The advantages of a cloud-based KMS include:
- Reduced Costs: Eliminates the need for upfront hardware and software investments, as well as reduces ongoing operational costs.
- Simplified Management: The cloud provider handles the infrastructure management, software updates, and security patching.
- Scalability and Flexibility: Cloud KMS solutions are designed to scale elastically, allowing organizations to easily adjust their key management capacity as needed.
- High Availability and Reliability: Cloud providers typically offer robust infrastructure with high availability and disaster recovery capabilities.
The disadvantages of a cloud-based KMS include:
- Limited Control: Organizations have less control over the underlying infrastructure and security configurations.
- Vendor Lock-in: Migrating to a different KMS provider can be complex and time-consuming.
- Dependency on Internet Connectivity: Requires a reliable internet connection to access the KMS.
- Security Concerns: Requires careful consideration of the cloud provider’s security practices and compliance certifications.
Hybrid KMS
A hybrid KMS combines elements of both on-premise and cloud-based models. This approach allows organizations to leverage the benefits of both models while mitigating their respective drawbacks. For example, an organization might use a cloud-based KMS for general-purpose key management while maintaining an on-premise KMS for highly sensitive keys or applications.The advantages of a hybrid KMS include:
- Flexibility: Provides the flexibility to choose the best deployment model for different key management needs.
- Enhanced Security: Allows organizations to isolate highly sensitive keys in an on-premise environment while leveraging the scalability and cost-effectiveness of the cloud for other keys.
- Gradual Migration: Enables organizations to gradually migrate their key management infrastructure to the cloud without disrupting existing operations.
- Compliance: Facilitates compliance with regulations that require specific data residency or control requirements.
The disadvantages of a hybrid KMS include:
- Increased Complexity: Requires managing and integrating both on-premise and cloud-based KMS solutions, which can increase complexity.
- Integration Challenges: Integrating different KMS solutions can be challenging and may require specialized expertise.
- Increased Costs: May involve the costs of maintaining both on-premise and cloud-based infrastructure.
- Security Management: Requires careful coordination of security policies and procedures across both environments.
Popular KMS Providers and Deployment Options
Several leading KMS providers offer various deployment options to meet the diverse needs of organizations.
Here are some examples:
| Provider | Deployment Options |
|---|---|
| AWS KMS | Cloud-based (integrated with AWS services) |
| Azure Key Vault | Cloud-based (integrated with Azure services) |
| Google Cloud KMS | Cloud-based (integrated with Google Cloud services) |
| Thales (CipherTrust) | On-premise, cloud-based, hybrid |
| Fortanix | Cloud-based, on-premise, hybrid |
These providers often offer multiple options, including dedicated hardware security modules (HSMs) for enhanced security and compliance. The choice of a KMS provider and its deployment model should be based on a thorough assessment of the organization’s specific requirements, security posture, and budget. For instance, a financial institution might opt for an on-premise KMS or a hybrid approach to meet stringent regulatory requirements.
A software-as-a-service (SaaS) company might choose a cloud-based KMS for its scalability and ease of management.
Security Considerations for KMS

A robust Key Management Service (KMS) is fundamentally built upon strong security principles. Protecting cryptographic keys is paramount, as their compromise can lead to severe data breaches and compromise the confidentiality, integrity, and availability of sensitive information. Implementing comprehensive security measures, including access controls, auditing, and robust key lifecycle management, is essential to mitigate these risks effectively.
Security Measures for Key Protection
KMS utilizes a multi-layered approach to safeguard cryptographic keys from unauthorized access. These measures are not implemented in isolation but work together to create a strong security posture.
- Hardware Security Modules (HSMs): HSMs are specialized, tamper-resistant hardware devices that store and protect cryptographic keys. They provide a secure environment for key generation, storage, and cryptographic operations. HSMs offer physical security, including tamper detection and response mechanisms, making them highly resistant to physical attacks. A KMS often relies on HSMs to store its master keys, which are the foundation of the entire key hierarchy.
- Encryption at Rest and in Transit: All keys stored within the KMS, and any communication between the KMS and other systems, are encrypted. Encryption at rest protects keys when they are not actively in use, while encryption in transit protects them during network communication. Strong encryption algorithms, such as AES-256, are commonly used to ensure the confidentiality of the keys.
- Access Control Policies: Role-Based Access Control (RBAC) and other access control mechanisms are implemented to restrict access to keys based on user roles and permissions. This ensures that only authorized personnel can perform specific key management operations, such as key generation, rotation, or deletion. For example, an administrator might have full access to manage keys, while a developer might only have access to use specific keys for encryption/decryption operations within an application.
- Key Vaulting and Backup: KMS solutions include mechanisms for backing up keys securely. These backups are often encrypted and stored in a separate, secure location to ensure that keys can be recovered in the event of a disaster or system failure. The backup and restore processes are themselves subject to strict access controls and auditing.
- Regular Key Rotation: Keys are rotated periodically to limit the impact of a potential key compromise. Key rotation involves generating new keys and invalidating or retiring old ones. The frequency of key rotation depends on the sensitivity of the data being protected and the organization’s security policies. For example, financial institutions may rotate their encryption keys more frequently than other organizations.
Access Controls and Auditing in a KMS
Effective access controls and comprehensive auditing are crucial components of a secure KMS. These measures ensure that only authorized individuals can access and manage keys and that all key-related activities are tracked and monitored.
- Role-Based Access Control (RBAC): RBAC is a fundamental access control mechanism that defines user roles and permissions. Each role is associated with specific privileges, allowing users assigned to that role to perform only the authorized key management operations. This principle of least privilege minimizes the potential damage from insider threats or compromised accounts.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring users to provide multiple forms of authentication, such as a password and a one-time code generated by a mobile app or sent via SMS. MFA significantly reduces the risk of unauthorized access, even if an attacker obtains a user’s password.
- Detailed Auditing: KMS solutions provide detailed audit logs that record all key-related activities, including key creation, rotation, deletion, and access attempts. These logs capture information such as the user, the timestamp, the operation performed, and the key involved. Auditing enables security teams to monitor key usage, detect suspicious activity, and investigate potential security incidents.
- Regular Security Audits: Periodic security audits are performed to assess the effectiveness of access controls, auditing mechanisms, and other security measures. These audits may be conducted internally or by external security experts. The findings of the audits are used to identify and address any vulnerabilities or weaknesses in the KMS.
Mitigating Risks Associated with Key Compromise
A well-designed KMS incorporates several features and practices to minimize the impact of a key compromise if it were to occur. These measures are designed to contain the damage and prevent a complete loss of control over the organization’s data.
- Key Rotation: As previously mentioned, regular key rotation is a critical risk mitigation strategy. By rotating keys frequently, the attacker’s ability to decrypt data is limited to the period during which the compromised key was active. For example, if a key is rotated every 90 days, the attacker’s window of opportunity to decrypt data is limited to that 90-day period.
- Key Shredding/Destruction: KMS allows for the secure destruction of keys when they are no longer needed. This process typically involves overwriting the key material or securely erasing it from the storage location. This ensures that even if an attacker gains access to the system, the key is no longer usable.
- Revocation of Compromised Keys: In the event of a suspected key compromise, the KMS can be used to revoke the compromised key. This action renders the key invalid, preventing its further use for encryption or decryption. Any data encrypted with the compromised key will need to be re-encrypted using a new, secure key.
- Incident Response Plan: Organizations should have a comprehensive incident response plan that Artikels the steps to be taken in the event of a key compromise. This plan should include procedures for identifying and containing the breach, notifying stakeholders, and recovering from the incident. The plan should also specify the roles and responsibilities of the individuals involved in the response.
- Defense in Depth: A KMS should be implemented as part of a defense-in-depth strategy. This approach involves layering multiple security controls to protect the keys and the data they protect. This includes physical security of the KMS hardware, network segmentation, intrusion detection systems, and regular security assessments.
KMS and Compliance
Key Management Services (KMS) play a critical role in helping organizations achieve and maintain compliance with various data protection regulations. By providing a centralized and secure method for managing cryptographic keys, KMS solutions simplify the complex requirements of compliance, allowing organizations to demonstrate adherence to industry standards and legal mandates. This is particularly crucial in today’s data-driven landscape, where data breaches can result in significant financial penalties, reputational damage, and legal repercussions.A KMS helps organizations meet compliance requirements by enabling robust data encryption, key access controls, audit logging, and key rotation practices.
These features directly address the core principles of many data privacy regulations, such as confidentiality, integrity, and availability of sensitive information.
KMS Assisting with Regulatory Compliance
A KMS streamlines compliance efforts by offering a centralized and secure platform for managing cryptographic keys. This approach allows organizations to effectively address the complex requirements of various regulations, thereby minimizing the risk of non-compliance.
- Data Encryption: KMS facilitates the encryption of sensitive data at rest and in transit. This protects data from unauthorized access, a fundamental requirement of many regulations. Encryption ensures that even if data is compromised, it remains unreadable without the appropriate decryption keys.
- Access Controls: KMS allows for granular control over key access, limiting who can use specific keys and for what purposes. This principle of least privilege is crucial for preventing unauthorized access to sensitive data and demonstrating compliance with access control mandates.
- Audit Logging: KMS solutions provide detailed audit logs that track all key-related activities, including key creation, rotation, access, and deletion. These logs are essential for demonstrating compliance, providing evidence of key management practices, and aiding in incident investigations.
- Key Rotation: KMS simplifies the process of key rotation, a critical security practice that reduces the risk associated with compromised keys. Regular key rotation limits the impact of a potential breach by ensuring that even if a key is compromised, its lifespan is limited.
Examples of Compliance Standards Relying on KMS
Several compliance standards explicitly or implicitly require the use of strong cryptographic key management practices, often fulfilled by a KMS. These standards are designed to protect sensitive data, ensuring its confidentiality, integrity, and availability.
- General Data Protection Regulation (GDPR): GDPR mandates the protection of personal data of individuals within the European Union. While GDPR does not explicitly require a KMS, it emphasizes the importance of data encryption as a means of protecting personal data. A KMS facilitates encryption and key management, enabling organizations to demonstrate compliance with GDPR’s data security requirements. Non-compliance can result in significant fines.
- Health Insurance Portability and Accountability Act (HIPAA): HIPAA establishes standards for protecting sensitive patient health information (PHI) in the United States. HIPAA requires organizations to implement safeguards to protect the confidentiality, integrity, and availability of electronic PHI. A KMS supports HIPAA compliance by enabling encryption of PHI, controlling access to encryption keys, and providing audit trails.
- Payment Card Industry Data Security Standard (PCI DSS): PCI DSS is a set of security standards designed to protect cardholder data. PCI DSS mandates the use of encryption to protect cardholder data at rest and in transit. A KMS is essential for managing the encryption keys used to secure this data, ensuring compliance with PCI DSS requirements.
- California Consumer Privacy Act (CCPA): CCPA grants California consumers the right to control their personal information. While not explicitly mandating a KMS, CCPA emphasizes the importance of data security. Encryption, facilitated by a KMS, is a key component of data security, enabling organizations to protect consumer data and meet CCPA requirements.
KMS Requirements by Compliance Standard
The following table compares different compliance standards and their specific requirements related to KMS and key management. This comparison highlights how KMS solutions directly support organizations in meeting the security and data protection mandates of these regulations.
| Compliance Standard | Data Protected | KMS Requirement | Benefits of Using a KMS |
|---|---|---|---|
| GDPR | Personal data of EU residents | Encryption of personal data recommended. Key management practices must be secure. | Enables data encryption, facilitates access controls, provides audit trails for demonstrating compliance, simplifies key rotation. |
| HIPAA | Protected Health Information (PHI) | Encryption of ePHI recommended. Access controls and audit logging for key management are required. | Supports data encryption, provides granular access controls, generates audit logs for key usage, enables key rotation. |
| PCI DSS | Cardholder data | Encryption of cardholder data at rest and in transit is mandated. Key management practices must be secure. | Simplifies encryption key management, ensures secure key storage, facilitates key rotation, provides audit trails for compliance reporting. |
| CCPA | Personal information of California consumers | Data security measures, including encryption, are essential. Key management practices must be robust. | Facilitates data encryption, supports access controls, enables audit logging, simplifies key rotation to protect consumer data. |
KMS Integration with Applications
Integrating a Key Management Service (KMS) with various applications is crucial for securing sensitive data across an organization’s infrastructure. This integration allows applications to leverage the KMS’s capabilities for encryption, decryption, and key management, ensuring data confidentiality and integrity. Proper integration ensures that applications can securely access and utilize cryptographic keys without compromising their security.
APIs and Protocols for KMS Integration
Several APIs and protocols facilitate seamless integration between applications and a KMS. These standards enable applications to interact with the KMS to perform cryptographic operations securely.
- Cryptoki (PKCS#11): Cryptoki, also known as PKCS#11, is a standard API for accessing cryptographic tokens, such as hardware security modules (HSMs). It provides a platform-independent interface for applications to perform cryptographic operations, including key generation, encryption, decryption, and digital signatures. Many KMS solutions support PKCS#11 to allow applications to interact with the KMS via HSMs.
- KMIP (Key Management Interoperability Protocol): KMIP is a communication protocol designed for managing cryptographic keys. It defines a standardized way for key management systems and clients to communicate, allowing for key creation, deletion, rotation, and other management functions. KMIP simplifies the integration of KMS with various applications and devices, ensuring interoperability.
- REST APIs: Representational State Transfer (REST) APIs are widely used for KMS integration. They offer a flexible and standardized way for applications to interact with the KMS over HTTP/HTTPS. REST APIs typically support operations such as key creation, retrieval, encryption, decryption, and key rotation. They are often preferred for their ease of use and compatibility with various programming languages and platforms.
- gRPC: gRPC is a modern, high-performance remote procedure call (RPC) framework that can be used for KMS integration. It uses Protocol Buffers for defining service interfaces and allows for efficient communication between applications and the KMS. gRPC is particularly well-suited for microservices architectures and environments requiring low latency and high throughput.
Integrating a KMS with a Database
Integrating a KMS with a database involves encrypting sensitive data stored within the database. This protects the data from unauthorized access, even if the database is compromised. Several methods and tools can facilitate this integration.
- Transparent Data Encryption (TDE): Many database systems, such as Microsoft SQL Server, Oracle, and PostgreSQL, offer TDE. TDE automatically encrypts data at rest within the database files. The encryption keys are often managed by the database server or can be integrated with a KMS for enhanced security. The database server handles the encryption and decryption transparently to the application, simplifying the integration process.
- Column-Level Encryption: Column-level encryption involves encrypting specific columns within a database table. This approach allows for more granular control over data security, as only sensitive columns are encrypted. Applications need to use the KMS to encrypt and decrypt the data before storing or retrieving it from the database.
- Database-Specific Encryption Plugins: Some databases offer encryption plugins or extensions that integrate with a KMS. These plugins provide a streamlined way to encrypt and decrypt data using keys managed by the KMS. They often handle the cryptographic operations, simplifying the application’s interaction with the KMS.
- Example: PostgreSQL with pgcrypto and KMS integration: PostgreSQL can be integrated with a KMS by using the `pgcrypto` extension. This extension provides cryptographic functions, including encryption and decryption. Applications can use the `pgcrypto` functions, along with a KMS, to encrypt sensitive data before storing it in the database. The KMS manages the encryption keys, providing an extra layer of security. The application retrieves the data, decrypts it using the KMS, and presents it to the user.
Integrating a KMS with a Cloud Storage Service
Integrating a KMS with a cloud storage service secures data stored in the cloud. This integration ensures that data is encrypted before it is uploaded to the cloud and decrypted when retrieved, providing confidentiality and data integrity.
- Server-Side Encryption (SSE): Cloud storage providers often offer server-side encryption (SSE) options. With SSE, the cloud provider manages the encryption keys. Integrating with a KMS involves configuring the cloud storage service to use keys managed by the KMS for SSE. This allows organizations to retain control over their encryption keys.
- Client-Side Encryption: Client-side encryption involves encrypting data before uploading it to the cloud. Applications use the KMS to encrypt the data locally and then upload the encrypted data to the cloud storage service. This approach gives organizations complete control over the encryption process and the keys used.
- Key Management Integration with Cloud Provider Services: Cloud providers such as AWS, Azure, and Google Cloud offer native KMS services. These services allow applications to integrate with a KMS to manage encryption keys for cloud storage. The KMS manages the keys, and the cloud storage service uses these keys to encrypt and decrypt data.
- Example: AWS S3 with KMS Integration: AWS S3 supports KMS integration through SSE-KMS. When a user uploads an object to S3, they can specify that the object should be encrypted using a key managed by AWS KMS. S3 uses the KMS key to encrypt the object’s data. When the user retrieves the object, S3 decrypts the data using the KMS key before returning it to the user.
The KMS provides key rotation, audit logging, and other security features for the encryption keys.
Integrating a KMS with a Web Server
Integrating a KMS with a web server involves securing sensitive information transmitted and stored by the web server. This integration ensures the confidentiality and integrity of data, protecting against unauthorized access and data breaches.
- TLS/SSL Certificate Management: KMS can be integrated with a web server to manage TLS/SSL certificates. The KMS can store and protect the private keys associated with the certificates. The web server can retrieve the keys from the KMS when needed for TLS/SSL handshake and encryption. This centralizes key management and improves security.
- Encryption of Sensitive Data: Web servers often handle sensitive data such as user credentials, payment information, and personal data. KMS can be used to encrypt this data before it is stored in the web server’s database or other storage locations. Applications on the web server use the KMS to encrypt and decrypt the data.
- API Authentication and Authorization: KMS can be used to protect API keys and other credentials used for authentication and authorization. The web server can securely store these credentials and use the KMS to manage their lifecycle, rotation, and access control.
- Example: Apache Web Server with KMS Integration for TLS/SSL: A KMS can be integrated with an Apache web server to manage TLS/SSL certificates. The private keys associated with the certificates are stored and protected by the KMS. The Apache web server is configured to use the KMS to retrieve the private keys when establishing TLS/SSL connections. The KMS manages the key rotation, and access control, enhancing the security of the web server’s communication.
The Apache server uses the retrieved keys to encrypt communication.
Key Generation and Storage Techniques
Key generation and storage are fundamental aspects of a Key Management Service (KMS). The security of any KMS hinges on the strength of its key generation process and the security of its key storage mechanisms. Properly implemented, these techniques ensure that cryptographic keys are created securely and protected from unauthorized access or compromise.
Key Generation Techniques
A KMS employs various techniques to generate cryptographic keys, each with its own strengths and suitable use cases. These techniques ensure the creation of strong, unpredictable keys that are crucial for the overall security of the cryptographic operations.The following methods are commonly utilized:
- Random Number Generation (RNG): This is the cornerstone of key generation. A robust RNG is essential for producing keys that are cryptographically secure. KMS uses hardware-based or software-based RNGs to generate random bits, which are then used to form the keys. Hardware RNGs (HRNGs) are preferred as they are typically more secure than software RNGs, as they draw randomness from physical phenomena.
- Pseudo-Random Number Generation (PRNG): PRNGs use a deterministic algorithm to generate a sequence of numbers that appear random. While faster than HRNGs, PRNGs require a strong seed value and are less secure on their own. They are often used in conjunction with HRNGs to improve performance.
- Key Derivation Functions (KDFs): KDFs are used to derive one or more keys from a secret value, such as a master key or a password. This is useful when the KMS needs to generate multiple keys from a single, securely stored key. The process involves applying a cryptographic function to the input secret, along with other parameters like salts and iteration counts, to produce the derived keys.
A common KDF is the HMAC-based Key Derivation Function (HKDF).
- Elliptic Curve Cryptography (ECC) Key Generation: ECC provides a method for generating public and private key pairs. ECC offers strong security with smaller key sizes compared to other cryptographic algorithms. KMS can leverage ECC for applications requiring efficient key management and high security, such as digital signatures and secure communications.
- RSA Key Generation: RSA is a widely used asymmetric encryption algorithm, and KMS supports the generation of RSA key pairs. This involves generating two large prime numbers and using them to create a public key and a private key. RSA is often used for digital signatures, encryption, and key exchange.
Key Storage Methods
Secure key storage is paramount in a KMS. The method used to store cryptographic keys directly impacts the overall security posture of the system. Several techniques are employed to protect keys from unauthorized access, loss, or compromise.One of the most secure methods for key storage is the use of Hardware Security Modules (HSMs).
Hardware Security Modules (HSMs)
HSMs are dedicated, tamper-resistant hardware devices designed specifically for secure cryptographic key management. They provide a high level of security by isolating cryptographic operations and key storage within a physically protected environment. HSMs are a critical component of many KMS implementations.HSMs offer the following security benefits:
- Tamper Resistance: HSMs are designed to detect and resist physical tampering. Any attempt to physically access or modify the device typically results in the erasure of sensitive keys.
- Secure Key Generation and Storage: HSMs generate keys within a secure environment and store them in an encrypted format. This ensures that keys are never exposed in plaintext.
- Cryptographic Operations: HSMs perform cryptographic operations, such as encryption, decryption, and digital signatures, within their secure boundaries. This protects keys from being exposed during these operations.
- Access Control: HSMs provide robust access control mechanisms to restrict access to keys. These controls typically involve authentication, authorization, and auditing.
- Key Backup and Recovery: HSMs often support secure key backup and recovery procedures to prevent data loss in case of hardware failure.
- Compliance and Certification: HSMs are often certified to industry standards such as FIPS 140-2 or FIPS 140-3, demonstrating their compliance with stringent security requirements.
- Key Rotation and Destruction: HSMs provide capabilities for key rotation and secure key destruction, following established security best practices.
Monitoring and Auditing in KMS
Robust monitoring and auditing are critical for maintaining the security, integrity, and compliance of a Key Management Service (KMS). These practices provide visibility into key usage, identify potential security threats, and support regulatory compliance requirements. Effective monitoring and auditing allow organizations to proactively detect and respond to security incidents, ensuring the confidentiality and availability of sensitive data protected by KMS.
Importance of Monitoring and Auditing
Monitoring and auditing are essential components of a secure KMS environment. They provide the necessary insights to ensure the system operates as intended and that security policies are being adhered to.
- Security Incident Detection and Response: Continuous monitoring helps in identifying unusual activities or potential security breaches, such as unauthorized key access or unusual key usage patterns. Auditing provides the detailed logs necessary to investigate incidents and determine the scope of compromise.
- Compliance and Regulatory Requirements: Many industry regulations and compliance standards (e.g., GDPR, HIPAA, PCI DSS) mandate the logging and auditing of key management activities. Monitoring ensures that these requirements are met.
- Operational Efficiency and Troubleshooting: Monitoring helps identify performance bottlenecks, configuration issues, and other operational problems within the KMS. Auditing provides valuable data for troubleshooting and optimizing the system’s performance.
- Key Usage Tracking and Control: Auditing enables tracking of who accessed which keys, when they were accessed, and for what purpose. This provides crucial information for access control and security audits.
Events to Log for Auditing
Comprehensive logging of key management activities is vital for effective auditing. The logs should capture a wide range of events to provide a complete picture of KMS operations.
- Key Creation and Deletion: Records of key creation and deletion events, including the user or service that initiated the action, the key’s attributes, and the time of the event.
- Key Access and Usage: Logs of all key access attempts, including successful and failed attempts. This should include the identity of the requester, the specific key accessed, the time of access, and the purpose of the access.
- Key Rotation: Records of key rotation events, including the old and new key versions, the time of rotation, and the user or service that initiated the rotation.
- Configuration Changes: Logs of all configuration changes within the KMS, such as changes to access control policies, security settings, and system parameters.
- Authentication and Authorization Events: Records of all user authentication attempts (successful and failed) and authorization decisions, including the identity of the user, the time of the event, and the outcome.
- System Events: Logs of system-level events, such as system startup and shutdown, error messages, and performance metrics.
- Key Import and Export: Records of key import and export operations, including the source and destination of the key, the time of the event, and the user or service that initiated the action. This is crucial for tracking key movement and ensuring secure key handling.
Setting Up Alerts for Suspicious Activity
Proactive alerting is a critical component of a robust KMS monitoring strategy. Alerts should be configured to trigger notifications for potentially malicious or unusual activities, enabling rapid response.
- Unauthorized Key Access Attempts: Configure alerts for repeated failed attempts to access a key or attempts to access keys by unauthorized users or from unexpected locations.
- Unusual Key Usage Patterns: Set up alerts for significant deviations from normal key usage patterns, such as a sudden spike in key access requests or access to a key outside of its scheduled time window. For instance, if a key is usually accessed once a day at 9:00 AM and suddenly sees hundreds of accesses in a short period, an alert should be triggered.
- Key Deletion or Modification: Generate alerts for the deletion or modification of critical keys, especially if initiated by an unexpected user or service.
- Configuration Changes: Alert on any changes to the KMS configuration, especially those related to security settings or access control policies.
- System Errors and Performance Issues: Configure alerts for system errors, performance degradation, or other operational issues that could indicate a security problem or a service disruption. For example, if the KMS experiences a high CPU utilization rate, an alert should be triggered to investigate the cause.
- Anomaly Detection: Utilize anomaly detection techniques to identify unusual activity based on historical data. This involves establishing a baseline of normal behavior and triggering alerts when deviations from this baseline occur.
Future Trends in KMS
The field of Key Management Services (KMS) is dynamic, constantly evolving to meet the demands of increasingly sophisticated cyber threats and the shift towards cloud-centric architectures. This section explores the emerging trends shaping the future of KMS, focusing on advancements in cryptography, cloud-native integration, and the proactive adaptation to evolving security challenges.
Quantum-Resistant Cryptography
The advent of quantum computing poses a significant threat to current cryptographic algorithms. Quantum computers, with their ability to perform complex calculations exponentially faster than classical computers, can potentially break many of the encryption methods currently in use. Therefore, a major trend in KMS is the adoption of quantum-resistant cryptography.Quantum-resistant cryptography refers to cryptographic algorithms that are believed to be secure against attacks from both classical and quantum computers.
This involves transitioning from algorithms like RSA and ECC, which are vulnerable to quantum attacks, to post-quantum cryptography (PQC) algorithms. PQC algorithms are mathematical problems that are computationally hard for both classical and quantum computers to solve.
- Algorithm Development: Researchers are actively developing and evaluating various PQC algorithms. These algorithms are based on different mathematical principles, such as lattice-based cryptography, multivariate cryptography, code-based cryptography, and hash-based signatures. The National Institute of Standards and Technology (NIST) is leading the effort to standardize PQC algorithms, having selected several algorithms for standardization.
- Implementation Challenges: Implementing PQC algorithms in KMS presents several challenges. These include performance overhead, key size differences (PQC keys are often larger than traditional keys), and the need to maintain compatibility with existing systems.
- Hybrid Approaches: A common approach is to use hybrid cryptography, combining classical algorithms with PQC algorithms. This allows organizations to benefit from the security of PQC while gradually transitioning their infrastructure.
- Key Management: KMS must be updated to support the generation, storage, and management of PQC keys. This includes securely storing and distributing these new key types, as well as ensuring that the KMS can interoperate with systems that use both classical and PQC algorithms.
Evolving Role of KMS in Cloud-Native Environments
Cloud-native environments, built on principles like microservices, containerization, and DevOps, require a different approach to security, including key management. The dynamic and distributed nature of these environments necessitates a KMS that can scale and adapt quickly.The evolution of KMS in cloud-native environments is driven by several key factors.
- Scalability and Automation: Cloud-native applications often experience rapid scaling. KMS must be able to automatically provision, rotate, and manage keys for a large number of microservices and containers. Automation is crucial to reduce operational overhead and ensure consistent security policies.
- Integration with Container Orchestration: KMS must seamlessly integrate with container orchestration platforms like Kubernetes. This allows for the automated injection of keys and secrets into containers at runtime, ensuring that sensitive data is not exposed.
- Microservices Security: In a microservices architecture, each service needs its own keys and secrets. KMS facilitates secure communication between services, enabling encryption and authentication.
- DevSecOps Integration: KMS should be integrated into the DevSecOps pipeline, allowing developers to manage keys as part of their code and infrastructure. This ensures that security is integrated throughout the development lifecycle.
- Policy-as-Code: Defining key management policies as code allows for consistent and repeatable security configurations across all environments. KMS can be integrated with policy-as-code frameworks to automate key lifecycle management based on defined rules.
Future Scenario: Adapting to Emerging Security Threats
The future of KMS will involve proactive adaptation to emerging security threats, including advanced persistent threats (APTs), ransomware, and sophisticated insider attacks. The following blockquote illustrates a potential future scenario.
Imagine a scenario where a large financial institution is targeted by a highly sophisticated APT. The attackers have successfully infiltrated the network and are attempting to steal sensitive data. The institution’s KMS, however, is designed to be highly resilient. The KMS automatically detects suspicious activity, such as unusual access patterns or data exfiltration attempts. Leveraging AI-powered threat intelligence, the KMS dynamically rotates keys, isolates compromised systems, and initiates incident response protocols. The KMS also integrates with a zero-trust architecture, requiring continuous verification of user identities and device security. Furthermore, the KMS is fully quantum-resistant, protecting against future attacks. Even if the attackers manage to compromise a part of the infrastructure, the KMS ensures that the impact is contained, and the data remains protected. The KMS continuously monitors for new vulnerabilities and automatically applies security patches, ensuring that the system is always up-to-date and secure. The KMS’s adaptability, combined with its proactive security measures, significantly reduces the risk of data breaches and minimizes the impact of successful attacks.
Final Summary
In conclusion, a Key Management Service is more than just a technical tool; it’s a fundamental pillar of modern data security. By understanding its core components, benefits, and deployment models, organizations can effectively protect their digital assets. As technology continues to evolve, KMS will remain at the forefront of data protection, adapting to new threats and ensuring the confidentiality and integrity of information.
Embracing KMS is not just a best practice; it’s a commitment to safeguarding the future of your data.
Questions Often Asked
What is the main purpose of a KMS?
The primary purpose of a KMS is to securely manage cryptographic keys throughout their lifecycle, from creation to destruction, ensuring data confidentiality and integrity.
How does a KMS differ from simply storing keys in a file?
Unlike storing keys in files, a KMS offers enhanced security through features like hardware security modules (HSMs), access controls, key rotation, and auditing, significantly reducing the risk of key compromise.
Is a KMS only for large organizations?
No, KMS is beneficial for organizations of all sizes. Cloud-based KMS solutions make it accessible and affordable for even small businesses to enhance their data security posture.
What are the key benefits of using a KMS?
Key benefits include improved security, simplified key lifecycle management, compliance with regulations, and reduced operational overhead associated with key management.