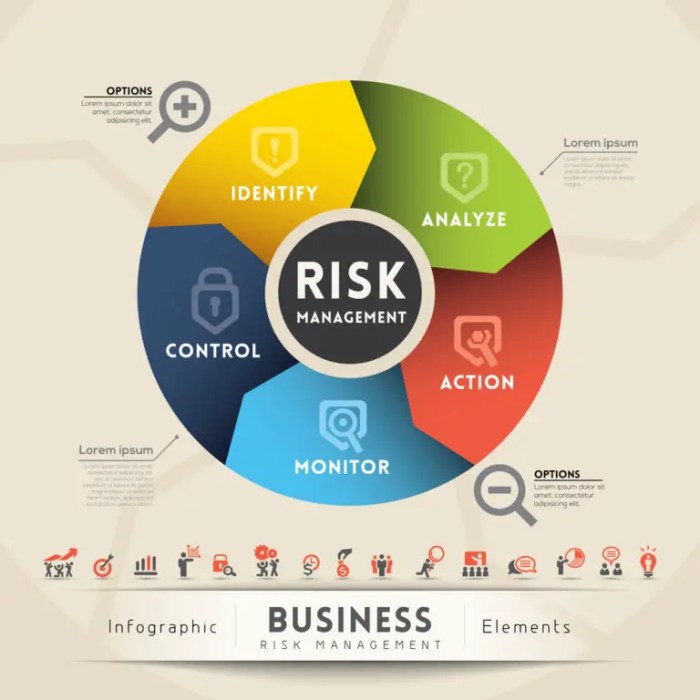
In today’s cloud-centric world, organizations increasingly rely on Software-as-a-Service (SaaS) applications and cloud storage for their operations. This shift, while offering significant advantages in terms of flexibility and scalability, also introduces new security challenges. Enter the Cloud Access Security Broker (CASB), a critical component in safeguarding your data and ensuring compliance within these dynamic cloud environments.
A CASB acts as a gatekeeper, sitting between your organization’s users and cloud service providers. It provides visibility into cloud app usage, enforces security policies, and protects sensitive data. By understanding what a CASB is and how it functions, businesses can significantly reduce their risk of data breaches and maintain control over their cloud resources, ensuring a secure and compliant cloud journey.
Introduction to Cloud Access Security Brokers (CASBs)
Cloud Access Security Brokers (CASBs) have become indispensable tools for organizations embracing cloud services. They act as intermediaries between cloud service users and cloud service providers, offering a comprehensive suite of security features. These solutions provide visibility, control, and data security, addressing the unique challenges of cloud adoption.
Core Function of a CASB
At its core, a CASB functions as a gatekeeper, ensuring that cloud services are used securely and in compliance with organizational policies. It acts as a central point of enforcement, monitoring and managing all cloud-based activities.
Definition of a CASB
A Cloud Access Security Broker (CASB) is a security policy enforcement point, placed between cloud service users and cloud service providers. It combines and integrates multiple security functions. Key features and benefits include:
- Visibility: CASBs provide detailed insights into cloud application usage, identifying which applications are being used, by whom, and how. This visibility helps organizations understand their cloud footprint and potential security risks.
- Compliance: CASBs help organizations meet regulatory requirements and internal policies by monitoring and enforcing compliance standards. This includes data loss prevention (DLP), data encryption, and access control.
- Data Security: CASBs protect sensitive data stored in the cloud through various methods, including data loss prevention, encryption, and tokenization. They help prevent data breaches and ensure data confidentiality.
- Threat Protection: CASBs detect and prevent threats, such as malware, insider threats, and compromised accounts, by monitoring user behavior and identifying suspicious activities. They provide real-time threat intelligence and incident response capabilities.
Problems a CASB Solves
Organizations face numerous challenges when using cloud services. A CASB directly addresses these problems, enhancing security posture and enabling secure cloud adoption.
- Shadow IT: The unauthorized use of cloud applications (Shadow IT) poses significant security risks. CASBs discover and manage shadow IT, providing visibility and control over unsanctioned cloud services.
- Data Loss Prevention (DLP): Protecting sensitive data in the cloud is crucial. CASBs implement DLP policies to prevent data breaches and ensure that sensitive information does not leave the organization’s control. For example, a CASB can be configured to prevent the upload of credit card numbers to a cloud storage service.
- Compliance Violations: Cloud services must comply with various regulations. CASBs help organizations meet compliance requirements, such as GDPR, HIPAA, and PCI DSS, by monitoring and enforcing security policies.
- Threat Protection: Cloud environments are vulnerable to various threats. CASBs provide threat detection and prevention capabilities, including malware detection, anomaly detection, and user behavior analytics, to protect against cyberattacks. For instance, a CASB can identify and block a user account compromised by a phishing attack.
- Account Takeover: CASBs can detect and prevent account takeover attempts by monitoring user login behavior and identifying suspicious activity. This helps prevent unauthorized access to cloud resources.
CASB Architecture and Deployment Models
Cloud Access Security Brokers (CASBs) are versatile security solutions, and their effectiveness hinges significantly on their architecture and how they’re deployed within an organization’s cloud environment. The choice of deployment model impacts how a CASB monitors, controls, and secures cloud application usage. Several deployment models exist, each with its own set of advantages and disadvantages, influencing its suitability for different organizational needs and cloud environments.
Understanding these models is crucial for selecting the right CASB solution.
CASB Deployment Models
CASBs offer several deployment models, each with unique characteristics affecting their implementation and operational capabilities. These models cater to different cloud environments and security requirements, enabling organizations to choose the best fit for their needs. Here are the primary deployment models:
- Reverse Proxy: This model places the CASB between the user and the cloud application. All traffic from the user to the cloud service is routed through the CASB, which inspects and enforces security policies.
- Forward Proxy: In this model, the CASB sits between the user and the internet. All outbound traffic from the user’s device or network passes through the CASB. This model is particularly useful for controlling and monitoring traffic from unmanaged devices or networks.
- API-based: This approach leverages the APIs of cloud applications to access data and enforce security policies. The CASB directly integrates with the cloud provider’s APIs to monitor user activity, data access, and security configurations.
Reverse Proxy Deployment Model
The reverse proxy model provides real-time monitoring and control over user access to cloud applications.
- Advantages:
- Real-time Control: Provides immediate enforcement of security policies.
- Granular Policy Enforcement: Allows for detailed control over user actions and data access.
- Data Loss Prevention (DLP): Enables the inspection of data in transit to prevent data leakage.
- Visibility: Offers comprehensive visibility into user activity within cloud applications.
- Disadvantages:
- Latency: Can introduce latency, potentially affecting user experience.
- Implementation Complexity: Requires careful configuration and can be complex to implement.
- Compatibility: May not be compatible with all cloud applications.
- User Experience: Could impact user experience, depending on the configuration and the performance of the CASB.
Forward Proxy Deployment Model
The forward proxy model secures outbound traffic from user devices or networks.
- Advantages:
- Control of Unmanaged Devices: Effectively manages and secures traffic from devices not directly managed by the organization.
- Centralized Policy Enforcement: Allows for consistent security policy enforcement across all users and devices.
- Web Filtering: Enables web filtering and content control.
- Simplified Deployment: Can be simpler to deploy compared to a reverse proxy, particularly in certain network configurations.
- Disadvantages:
- Requires Client Configuration: Users or devices need to be configured to use the proxy.
- Potential Performance Impact: Can introduce latency and affect network performance.
- Limited Visibility: May have limited visibility into cloud application usage compared to other models.
- Bypass Risk: Users can potentially bypass the proxy if not properly configured.
API-based Deployment Model
The API-based model integrates directly with cloud applications using their APIs.
- Advantages:
- No Impact on User Experience: Doesn’t affect user experience since traffic isn’t routed through the CASB.
- Comprehensive Visibility: Offers deep visibility into user activity, data access, and security configurations.
- No Client-Side Configuration: No configuration is required on user devices.
- Easy Deployment: Relatively easy to deploy and maintain.
- Disadvantages:
- Dependency on APIs: Relies on the availability and functionality of cloud application APIs.
- Limited Real-Time Control: May not offer real-time control over user actions.
- API Rate Limits: Can be subject to API rate limits, potentially affecting monitoring capabilities.
- Data Access Limitations: Limited access to data that is not exposed via the API.
Comparison of CASB Deployment Models
The following table provides a side-by-side comparison of the pros and cons of each CASB deployment model.
| Deployment Model | Advantages | Disadvantages | Use Cases |
|---|---|---|---|
| Reverse Proxy | Real-time control, granular policy enforcement, DLP, comprehensive visibility. | Latency, implementation complexity, compatibility issues, potential impact on user experience. | Securing access to sensitive cloud applications, enforcing DLP policies, and controlling user actions in real-time. |
| Forward Proxy | Control of unmanaged devices, centralized policy enforcement, web filtering, simplified deployment. | Requires client configuration, potential performance impact, limited visibility, bypass risk. | Securing traffic from unmanaged devices, enforcing web filtering policies, and controlling internet access. |
| API-based | No impact on user experience, comprehensive visibility, no client-side configuration, easy deployment. | Dependency on APIs, limited real-time control, API rate limits, data access limitations. | Monitoring user activity, detecting threats, and enforcing security policies within cloud applications without affecting user performance. |
Key Features and Capabilities of CASBs
Cloud Access Security Brokers (CASBs) are not just security tools; they are comprehensive platforms designed to provide visibility, control, and data protection across cloud environments. They offer a range of features and capabilities that address the unique security challenges posed by cloud adoption, ensuring that organizations can leverage the benefits of the cloud while maintaining a strong security posture. This section will delve into the key features and capabilities of CASBs, highlighting their role in securing cloud data and applications.
Main Security Features Offered by CASBs
CASBs provide a multifaceted approach to cloud security, incorporating several core features to address various security concerns. These features work in concert to offer a holistic security solution for cloud environments.
- Data Loss Prevention (DLP): DLP capabilities are central to CASB functionality, preventing sensitive data from leaving the organization’s control.
- Threat Protection: CASBs detect and mitigate threats, including malware, ransomware, and insider threats, by analyzing user behavior and cloud application activity.
- Access Control: Access control features enable organizations to manage and enforce user access to cloud applications based on identity, device, location, and other contextual factors.
- Compliance and Auditing: CASBs facilitate compliance with industry regulations and internal policies by providing audit trails, reporting, and automated policy enforcement.
- Visibility and Monitoring: CASBs offer comprehensive visibility into cloud application usage, user activity, and data flows, enabling organizations to identify and address security risks.
Enforcing Data Loss Prevention (DLP) Policies in the Cloud
Data Loss Prevention (DLP) is a critical capability of CASBs, designed to protect sensitive data from unauthorized access, use, or disclosure. CASBs achieve this through a combination of techniques, including data discovery, classification, and policy enforcement.
CASBs utilize several mechanisms to enforce DLP policies in the cloud:
- Data Discovery: CASBs scan cloud storage and applications to identify and classify sensitive data, such as personally identifiable information (PII), protected health information (PHI), and financial data.
- Data Classification: Once data is discovered, CASBs classify it based on predefined rules, regular expressions, and data patterns. This allows organizations to categorize data based on its sensitivity and risk level.
- Policy Enforcement: CASBs enforce DLP policies by monitoring user activity and data flows within cloud applications. When a policy violation is detected, the CASB can take actions such as blocking the action, quarantining the data, or alerting security teams.
- Content Inspection: CASBs inspect the content of files and data being uploaded, downloaded, or shared within cloud applications. This allows them to identify sensitive information and prevent data leaks.
- Context-Aware Policies: CASBs can create context-aware policies that take into account factors such as user identity, device, location, and time of day. This enables organizations to tailor their DLP policies to specific scenarios and users.
For example, a CASB might be configured to prevent users from uploading sensitive financial data to a personal cloud storage account. If a user attempts to do so, the CASB would detect the policy violation and block the upload. The CASB can also alert the security team, providing them with information about the incident and the user involved.
Integrating with Other Security Tools and Systems
CASBs are designed to integrate with existing security tools and systems to provide a cohesive and comprehensive security architecture. Integration enables CASBs to leverage the capabilities of other security solutions and share information to improve overall security posture.
CASBs integrate with various security tools and systems in several ways:
- SIEM Integration: CASBs can integrate with Security Information and Event Management (SIEM) systems to send security events, alerts, and logs. This allows organizations to centralize security monitoring and incident response.
- Identity and Access Management (IAM) Integration: CASBs integrate with IAM systems to enforce access control policies and manage user identities. This integration ensures that users have appropriate access to cloud applications based on their roles and permissions.
- Threat Intelligence Feeds: CASBs can integrate with threat intelligence feeds to identify and block malicious activities. This enables them to stay up-to-date on the latest threats and protect against them.
- Endpoint Detection and Response (EDR) Integration: CASBs can integrate with EDR solutions to provide visibility into endpoint activity and detect potential threats. This integration helps organizations to identify and respond to threats across both cloud and on-premises environments.
- API Integration: CASBs use APIs to integrate with cloud applications and other security tools. This allows them to collect data, enforce policies, and automate security tasks.
For instance, a CASB can integrate with a SIEM to forward security events, enabling security analysts to correlate cloud-based threats with on-premises activities. This integrated approach provides a more complete view of the organization’s security posture and facilitates faster and more effective incident response. Another example is integration with an IAM system. A CASB can leverage the user identity information provided by the IAM system to enforce access control policies within cloud applications, ensuring that users only have access to the resources they are authorized to use.
Data Loss Prevention (DLP) with CASBs
Data Loss Prevention (DLP) is a critical security function within Cloud Access Security Brokers (CASBs), designed to protect sensitive data from unauthorized access, misuse, or loss. CASBs implement DLP by inspecting data in transit and at rest within cloud applications, enforcing policies to prevent data leakage. This proactive approach is crucial for maintaining regulatory compliance and safeguarding an organization’s intellectual property and sensitive information.
Implementing DLP with CASBs
CASBs implement DLP by integrating with cloud applications and monitoring user activity. They analyze data flowing into and out of the cloud environment, applying predefined policies to identify and control sensitive information. When a policy violation is detected, the CASB can take various actions, such as blocking the activity, quarantining the data, alerting administrators, or redacting sensitive information. The effectiveness of DLP in CASBs relies on a combination of data classification, policy enforcement, and incident response capabilities.
Examples of DLP Policies Configured within a CASB
Organizations can configure a wide array of DLP policies within a CASB to address specific data security needs. These policies are typically tailored to the organization’s industry, regulatory requirements, and internal security standards.Here are some examples:
- Preventing the upload of sensitive documents: This policy could block users from uploading files containing credit card numbers, social security numbers, or protected health information (PHI) to unauthorized cloud storage services.
- Restricting the sharing of confidential data: This policy might prevent users from sharing documents marked as “confidential” with external recipients or sharing them publicly.
- Monitoring data movement between cloud applications: This policy can track and control the transfer of data between different cloud services, ensuring that sensitive information does not move to less secure platforms. For instance, preventing the download of a customer database from Salesforce to an unmanaged device.
- Detecting and preventing the exfiltration of data: This policy could identify attempts to download large volumes of data or send sensitive information outside the organization’s network via email or other channels.
- Enforcing data encryption: This policy could mandate the encryption of sensitive data stored in cloud applications or transmitted between cloud services.
Common Data Types Targeted by DLP Policies
DLP policies often target specific data types to ensure comprehensive data protection. The following data types are commonly addressed:
- Personally Identifiable Information (PII): This includes data such as names, addresses, phone numbers, email addresses, dates of birth, and government-issued identification numbers.
- Protected Health Information (PHI): This encompasses medical records, insurance information, and other health-related data, as defined by regulations such as HIPAA.
- Payment Card Information (PCI): This includes credit card numbers, cardholder names, expiration dates, and security codes, as governed by PCI DSS.
- Intellectual Property (IP): This covers confidential business plans, trade secrets, source code, and other proprietary information.
- Financial Data: This includes bank account details, financial statements, and investment information.
- Social Security Numbers (SSNs): SSNs are a critical data type due to their use in identity verification and access to financial and personal information.
Threat Protection and CASBs
Cloud Access Security Brokers (CASBs) are crucial for safeguarding cloud environments from a variety of threats. They act as a security enforcement point, providing visibility and control over cloud application usage. CASBs employ various techniques to detect and mitigate malicious activities, ensuring data and system integrity. This section will delve into the threat protection capabilities of CASBs, exploring detection methods and response mechanisms.
Detecting and Mitigating Cloud-Based Threats
CASBs are designed to proactively detect and mitigate threats originating from or targeting cloud-based resources. They offer a multi-layered approach, combining real-time monitoring, behavioral analysis, and policy enforcement. This allows organizations to identify and respond to threats before they can cause significant damage.
Threat Detection Techniques Employed by CASBs
CASBs utilize a range of threat detection techniques to identify malicious activity. These techniques are often employed in combination to improve accuracy and reduce false positives.
- Anomaly Detection: CASBs establish baselines of normal user behavior. They then monitor for deviations from these baselines, such as unusual login times, access from unfamiliar locations, or excessive data downloads.
- Malware Scanning: CASBs integrate with malware scanning engines to identify malicious files uploaded to or downloaded from cloud applications. This helps prevent the spread of malware within the cloud environment.
- Behavioral Analysis: CASBs analyze user behavior patterns to identify potentially malicious activities. This includes identifying users who exhibit risky behaviors, such as accessing sensitive data from unmanaged devices or sharing credentials.
- Policy Enforcement: CASBs enforce security policies to prevent risky activities. This can include blocking access to certain applications, restricting data sharing, or enforcing multi-factor authentication.
- Threat Intelligence Integration: CASBs integrate with threat intelligence feeds to identify known threats and vulnerabilities. This allows them to proactively block malicious activity and protect against emerging threats.
CASB Response to Detected Threats
When a CASB detects a threat, it takes specific actions to mitigate the risk. The response actions are typically based on predefined policies and can vary depending on the severity of the threat. Here are some examples:
Quarantine: Isolates a compromised user account or device to prevent further damage.
Alerting: Notifies security teams about the detected threat, providing details about the incident.
Blocking: Prevents access to malicious files, applications, or resources.
Revoking Access: Revokes access to cloud resources for compromised users or devices.
Data Encryption: Encrypts sensitive data to protect it from unauthorized access.
Access Control and CASBs
Cloud Access Security Brokers (CASBs) play a crucial role in securing cloud environments by meticulously managing and enforcing access control policies. They act as intermediaries, ensuring that only authorized users and devices can access cloud applications and data, mitigating the risks associated with unauthorized access and data breaches. This is achieved through a combination of features and functionalities that allow organizations to define, implement, and monitor access control measures tailored to their specific security requirements.
Access Control Policies Management
CASBs manage and enforce access control policies for cloud applications by acting as a central point of enforcement. They sit between the user and the cloud application, intercepting access requests and evaluating them against predefined policies. These policies dictate who can access what resources, under what conditions, and how they can interact with the cloud environment. The primary goal is to ensure that access is granted based on established security principles, such as the principle of least privilege, and to prevent unauthorized access to sensitive data.Access control policies implemented by CASBs are often highly granular, allowing for the definition of rules based on a variety of factors, including user identity, device posture, location, time of day, and application context.
This level of control enables organizations to create sophisticated access control mechanisms that adapt to the evolving threat landscape.
Examples of Access Control Policies
CASBs support a wide range of access control policies, providing organizations with flexibility in securing their cloud environments.
- Multi-Factor Authentication (MFA): This policy requires users to provide multiple forms of authentication, typically something they know (password), something they have (a security token or mobile device), and/or something they are (biometric data). This significantly enhances security by making it more difficult for unauthorized users to gain access, even if they have compromised a user’s credentials. For example, a CASB can enforce MFA for all users accessing a sensitive cloud application, such as a financial management system, regardless of their location or device.
- Role-Based Access Control (RBAC): RBAC assigns access permissions based on a user’s role within the organization. This simplifies access management by grouping users with similar responsibilities and granting them the necessary permissions to perform their job functions. For instance, a CASB can configure RBAC to allow only finance department employees to access financial data, while restricting access for other departments.
- Device-Based Access Control: This policy restricts access based on the device used to access cloud applications. This can involve checking the device’s security posture, such as whether it has the latest security patches installed, is running up-to-date antivirus software, or is compliant with the organization’s mobile device management (MDM) policies. For example, a CASB can prevent access from non-compliant devices or allow access with limited functionality.
- Location-Based Access Control: This policy limits access based on the user’s geographic location. This can be used to restrict access from high-risk locations or to comply with data residency requirements. For example, a CASB can block access to sensitive data from outside a specific country or region.
- Context-Aware Access Control: This is a more sophisticated approach that considers various contextual factors, such as the time of day, the user’s activity, and the sensitivity of the data being accessed. For instance, a CASB could allow access to certain data only during business hours or automatically block access to sensitive files if unusual activity is detected.
Configuring a Basic Access Control Policy within a CASB: A Step-by-Step Procedure
Configuring an access control policy typically involves several steps, although the exact procedure may vary depending on the specific CASB solution. Here is a generalized procedure for configuring a basic access control policy:
- Define the Policy Objective: Clearly define the purpose of the access control policy. Determine which cloud applications and data the policy will apply to, and identify the specific security goals, such as protecting sensitive data or preventing unauthorized access.
- Identify Target Users or Groups: Determine which users or groups of users the policy will apply to. This may involve selecting specific users, user groups, or all users accessing a particular cloud application.
- Choose the Access Control Method: Select the appropriate access control method based on the policy objective. Options include MFA, RBAC, device-based control, location-based control, or context-aware access control.
- Configure the Policy Rules: Define the specific rules that will govern access. This involves specifying the conditions under which access will be granted or denied, such as user identity, device type, location, or time of day. For example, if implementing MFA, specify the MFA method (e.g., authenticator app, SMS) and the cloud applications that require MFA.
- Test the Policy: Before deploying the policy, test it thoroughly to ensure it functions as intended and does not inadvertently block legitimate access. This can involve simulating different user scenarios and verifying that the access control rules are correctly enforced.
- Deploy and Monitor the Policy: Once the policy has been tested, deploy it to the production environment. Continuously monitor the policy’s effectiveness, including user access logs and any security alerts. Regularly review and update the policy as needed to adapt to changes in the cloud environment and the evolving threat landscape.
Compliance and CASBs
Cloud Access Security Brokers (CASBs) are crucial tools for organizations navigating the complex landscape of regulatory compliance. They act as intermediaries between cloud service providers and end-users, enforcing security policies and ensuring data governance. This capability is particularly vital in industries with stringent compliance requirements, where breaches can result in significant financial penalties and reputational damage.
Meeting Regulatory Compliance Requirements
CASBs are instrumental in helping organizations achieve and maintain compliance with various regulatory frameworks. They offer a centralized platform for enforcing security policies, monitoring cloud usage, and generating reports that demonstrate adherence to specific regulations. This functionality simplifies the often-complex process of proving compliance to auditors and regulators.For example, CASBs assist with:
- GDPR (General Data Protection Regulation): CASBs help organizations comply with GDPR by providing features like data loss prevention (DLP) to prevent sensitive data leakage, data discovery to identify where personal data resides within cloud applications, and access control to restrict access based on user roles and location.
- HIPAA (Health Insurance Portability and Accountability Act): In healthcare, CASBs help maintain HIPAA compliance by enforcing security measures to protect protected health information (PHI) stored in cloud environments. This includes encryption, access controls, and audit logging.
- PCI DSS (Payment Card Industry Data Security Standard): CASBs aid in PCI DSS compliance by monitoring and controlling access to cardholder data, detecting and preventing malicious activities, and providing detailed audit trails for all cloud-based transactions.
- CCPA (California Consumer Privacy Act): CASBs can support CCPA compliance by enabling data discovery to identify consumer data, providing access controls to manage consumer requests for data access and deletion, and monitoring data usage to ensure compliance with consumer privacy rights.
Compliance Reports Generated by CASBs
CASBs provide a variety of compliance reports that organizations can use to demonstrate their adherence to regulatory requirements. These reports offer insights into cloud usage, security posture, and potential compliance violations.Examples of compliance reports include:
- Data Loss Prevention (DLP) Reports: These reports detail instances of data leakage or potential data breaches, highlighting the types of data involved, the users or applications involved, and the actions taken to remediate the issue. They can demonstrate the effectiveness of DLP policies in preventing sensitive data from leaving the organization.
- Access Control Reports: These reports provide an overview of user access privileges, including who has access to what data and when. They can demonstrate that access controls are properly configured and enforced to restrict access to sensitive data based on the principle of least privilege.
- Audit Logs: Detailed audit logs track user activity, including login attempts, data access, and application usage. These logs provide an audit trail that can be used to investigate security incidents, identify compliance violations, and demonstrate accountability.
- Configuration Compliance Reports: These reports assess the configuration of cloud services against security best practices and regulatory requirements. They can identify misconfigurations that could lead to vulnerabilities and provide recommendations for remediation.
- Usage Reports: These reports provide insights into cloud application usage, including which applications are being used, by whom, and how frequently. This information can be used to identify shadow IT, monitor data storage, and optimize cloud spending.
Auditing Cloud Usage and Identifying Compliance Violations
CASBs facilitate the auditing of cloud usage to identify and address potential compliance violations. They continuously monitor user activity, data access, and application behavior, providing real-time visibility into cloud environments. This proactive approach allows organizations to detect and respond to security incidents and compliance breaches quickly.Here’s how CASBs help with auditing:
- Real-time Monitoring: CASBs monitor cloud activity in real-time, providing immediate alerts when suspicious or non-compliant behavior is detected.
- User Behavior Analytics (UBA): CASBs use UBA to identify anomalous user behavior that may indicate a security threat or compliance violation. This includes detecting unusual login patterns, excessive data downloads, or unauthorized data access.
- Data Discovery and Classification: CASBs can scan cloud storage and applications to identify and classify sensitive data, such as personally identifiable information (PII) or protected health information (PHI). This helps organizations understand where their sensitive data resides and implement appropriate security controls.
- Policy Enforcement: CASBs enforce security policies that align with regulatory requirements. For example, a CASB can automatically block users from downloading sensitive data to unmanaged devices or restrict access to cloud applications from outside of approved geographic locations.
- Incident Response: When a compliance violation is detected, CASBs can trigger automated incident response actions, such as blocking user access, quarantining files, or notifying security teams.
User Behavior Analytics (UBA) with CASBs

Cloud Access Security Brokers (CASBs) are not just about enforcing policies; they also provide intelligent threat detection through User Behavior Analytics (UBA). UBA leverages machine learning and statistical analysis to establish a baseline of normal user activity and then identify deviations that might indicate a security breach or malicious insider activity. This proactive approach is crucial for mitigating risks in a cloud environment.
Identifying Unusual User Behavior
CASBs use UBA to identify unusual user behavior by monitoring a variety of activities and comparing them against established baselines. These activities include access patterns, data transfer volumes, login times, and geographic locations. Any significant deviation from the norm triggers an alert, enabling security teams to investigate potential threats promptly.
Examples of Suspicious User Activities
A CASB might flag several types of suspicious user activities. These activities, when detected, warrant immediate investigation by security teams.
- Unusual Login Patterns: Logging in from an unfamiliar location, at unusual times, or using an unfamiliar device. For example, a user accessing cloud resources from a country they’ve never visited.
- Excessive Data Downloads: Downloading significantly more data than usual, especially sensitive information. For instance, a user downloading a large number of financial records from a cloud storage service.
- Unsuccessful Login Attempts: A high number of failed login attempts from a single user account, which could indicate a brute-force attack.
- Privilege Escalation: Attempts to access resources or modify settings beyond the user’s authorized permissions.
- Data Exfiltration: Transferring large amounts of data to unauthorized locations or external services. This might involve uploading sensitive documents to a personal cloud storage account.
- Suspicious File Access: Accessing files or data that the user rarely interacts with, especially if those files contain sensitive information.
UBA-Driven Threat Detection Scenario
Consider a scenario where a marketing employee, Sarah, typically accesses marketing-related files from her office in New York.
- User’s Actions: Sarah begins downloading large volumes of sensitive customer data, including personally identifiable information (PII) and financial records, from her company’s cloud storage. Simultaneously, her login activity shows attempts to access these files from an IP address originating from a location in Eastern Europe, a region she has never traveled to.
- CASB’s Response: The CASB’s UBA engine detects these anomalies. The system notes the sudden increase in data downloads, the access of sensitive data, and the unusual login location. The CASB immediately flags these activities as suspicious and triggers an alert. The alert includes information about the user, the affected data, and the location of the potential threat. The CASB might also automatically take actions, such as blocking Sarah’s account, quarantining the downloaded files, and notifying the security team.
- Investigation and Remediation: The security team investigates the alert. They confirm that the login from Eastern Europe is indeed unusual and likely indicates a compromised account. They also find that the data downloads are excessive and not related to Sarah’s normal job duties. The team then takes steps to remediate the threat, which may include resetting Sarah’s password, isolating her device, and investigating the extent of the data breach.
CASB Integration with Cloud Service Providers (CSPs)
Integrating a Cloud Access Security Broker (CASB) with Cloud Service Providers (CSPs) is crucial for effectively securing cloud environments. This integration allows CASBs to leverage the CSP’s infrastructure and APIs, providing comprehensive visibility, control, and security across cloud resources. The seamless collaboration between CASBs and CSPs enhances security posture and streamlines cloud management.
Integration with Popular CSPs
CASBs offer robust integration capabilities with major CSPs like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP). This integration typically involves leveraging APIs provided by the CSPs to access and analyze cloud resource configurations, user activity, and data. The level of integration varies depending on the CASB vendor and the CSP, but generally includes:
- API-Based Integration: CASBs utilize APIs to connect to CSPs, gathering data on user activity, data storage, and application usage.
- Log Analysis: CASBs ingest and analyze logs generated by the CSPs to identify potential security threats and compliance violations.
- Real-time Monitoring: CASBs monitor cloud resources in real-time, enabling immediate detection and response to security incidents.
- Automated Remediation: CASBs can automatically trigger remediation actions based on pre-defined policies and security events, such as quarantining compromised accounts or restricting access to sensitive data.
Benefits of Integrating a CASB with a Specific CSP (AWS)
Integrating a CASB with AWS offers several benefits, enhancing security and simplifying cloud management. Specifically, integration provides:
- Enhanced Visibility: CASBs provide a centralized view of all AWS resources, user activity, and data stored within the environment. This enables organizations to gain a comprehensive understanding of their cloud security posture.
- Improved Data Loss Prevention (DLP): CASBs can scan data stored in AWS services like S3 and identify sensitive information. They then apply policies to prevent data breaches, such as blocking the upload of confidential documents.
- Threat Protection: CASBs detect and respond to threats within AWS by analyzing user behavior and identifying malicious activities. They can block compromised accounts or prevent the execution of malicious code.
- Compliance Management: CASBs assist organizations in meeting compliance requirements by monitoring AWS configurations and ensuring adherence to industry standards and regulations.
- Automated Security Enforcement: CASBs automate security enforcement by automatically enforcing security policies and remediating security incidents.
For example, consider a scenario where a company uses AWS S3 for storing sensitive customer data. Without a CASB, monitoring and securing this data can be complex. However, by integrating a CASB with AWS, the company gains several advantages:
- Data Discovery: The CASB can scan the S3 buckets and identify where sensitive data, such as Personally Identifiable Information (PII) or financial records, is stored.
- Data Classification: The CASB can classify the data based on its sensitivity level, allowing for tailored security policies.
- Policy Enforcement: The CASB can enforce policies such as preventing unauthorized access to the data, encrypting data at rest, and monitoring for suspicious activity.
- Incident Response: If a security incident occurs, such as a data breach, the CASB can alert security teams and trigger automated remediation actions, such as blocking access to the compromised data.
Specific CASB Features Leveraging AWS Capabilities
CASBs leverage specific AWS capabilities to provide enhanced security features. Here are a few examples:
- AWS CloudTrail Integration: CASBs integrate with AWS CloudTrail, which logs all API calls made within an AWS account. By analyzing CloudTrail logs, CASBs can identify suspicious user behavior, unauthorized access attempts, and potential security threats. This helps organizations monitor user activity and detect malicious actions.
- AWS S3 Bucket Scanning: CASBs can scan data stored in AWS S3 buckets for sensitive information, such as credit card numbers, social security numbers, and other confidential data. This feature enables organizations to enforce data loss prevention (DLP) policies and prevent data breaches.
- AWS IAM Integration: CASBs integrate with AWS Identity and Access Management (IAM) to manage user access to AWS resources. This allows organizations to enforce access control policies, such as restricting access to sensitive data based on user roles and permissions. This ensures that only authorized users can access specific resources.
- AWS Lambda Integration: CASBs can leverage AWS Lambda functions to automate security tasks, such as quarantining compromised accounts or restricting access to malicious IP addresses. This allows organizations to respond quickly to security incidents and minimize the impact of security threats.
- AWS Security Hub Integration: CASBs can integrate with AWS Security Hub, a centralized security service that aggregates security findings from various AWS services. This integration allows organizations to gain a comprehensive view of their security posture and prioritize security efforts. This centralizes the security information for easier management.
For example, a CASB might use AWS CloudTrail logs to detect a user accessing an S3 bucket containing sensitive data from an unusual location. The CASB could then automatically block the user’s access to the bucket, preventing a potential data breach. This exemplifies how CASBs leverage AWS capabilities to provide real-time threat detection and response.
Selecting a CASB Solution
Choosing the right Cloud Access Security Broker (CASB) solution is a critical decision that can significantly impact an organization’s cloud security posture. With a multitude of vendors and features available, selecting the most appropriate CASB requires a careful evaluation process. This section provides guidance on the key factors to consider, compares different vendors, and offers a decision matrix to aid in the selection process.
Key Factors for CASB Selection
Several crucial factors must be considered when evaluating and selecting a CASB solution. These factors encompass functionality, deployment options, integration capabilities, and overall cost-effectiveness.
- Functionality and Features: The core features of a CASB should align with the organization’s security needs. Consider features such as data loss prevention (DLP), threat protection, access control, user behavior analytics (UBA), and compliance reporting. Ensure the CASB supports the specific cloud applications used by the organization.
- Deployment Options: CASBs offer various deployment models, including reverse proxy, forward proxy, API-based, and inline. The choice of deployment model depends on the organization’s existing infrastructure, security policies, and the level of control required. API-based CASBs offer greater visibility and ease of deployment, while proxy-based solutions provide more granular control over traffic.
- Integration Capabilities: A robust CASB should integrate seamlessly with existing security tools and cloud service providers (CSPs). Consider the CASB’s ability to integrate with SIEM systems, identity providers, and other security solutions to streamline incident response and threat management.
- Performance and Scalability: The CASB solution must handle the organization’s cloud traffic volume and scale as the organization’s cloud footprint grows. Performance degradation can negatively impact user experience and hinder security effectiveness.
- Pricing and Total Cost of Ownership (TCO): Evaluate the pricing models of different CASB vendors, considering factors such as per-user fees, data volume, and feature tiers. Calculate the TCO, including implementation costs, ongoing maintenance, and training expenses.
- Compliance and Regulatory Requirements: Ensure the CASB solution helps meet industry-specific compliance requirements, such as HIPAA, GDPR, and PCI DSS. The CASB should provide the necessary reporting and auditing capabilities.
- Vendor Reputation and Support: Research the vendor’s reputation, customer reviews, and industry recognition. Evaluate the vendor’s support options, including documentation, training, and technical assistance.
Comparing CASB Vendors
Different CASB vendors offer a range of features, pricing models, and deployment options. Comparing vendors requires evaluating their strengths and weaknesses based on the organization’s specific needs.
- Vendor A: This vendor is known for its strong DLP capabilities and comprehensive feature set. They offer a wide range of deployment options, including API-based and proxy-based solutions. Pricing is generally on the higher end, but it offers a robust set of features. Vendor A is particularly suitable for organizations with complex security requirements.
- Vendor B: Vendor B excels in threat protection and UBA. It provides advanced threat detection capabilities and integrates well with SIEM systems. They offer competitive pricing and a user-friendly interface. Vendor B is a good choice for organizations that prioritize threat detection and incident response.
- Vendor C: This vendor is known for its ease of deployment and integration with popular cloud applications. They offer a cost-effective solution, making them an attractive option for small and medium-sized businesses. Vendor C is a good option for organizations that want a quick and simple CASB deployment.
CASB Vendor Decision Matrix
A decision matrix helps evaluate and compare different CASB vendors based on key criteria. This allows for a structured approach to the selection process.
| Criteria | Vendor A | Vendor B | Vendor C |
|---|---|---|---|
| Key Features | DLP, Access Control, UBA, Threat Protection | Threat Protection, UBA, Access Control | Access Control, Basic DLP |
| Deployment Options | Reverse Proxy, Forward Proxy, API-based | API-based, Reverse Proxy | API-based |
| Pricing Model | Per-user, Tiered | Per-user | Per-user, Volume-based |
| Integration Capabilities | SIEM, Identity Providers, CSPs | SIEM, Identity Providers, CSPs | CSPs |
The Future of CASBs
The cloud access security broker (CASB) market is dynamic, constantly evolving to meet the ever-changing demands of cloud computing and the evolving threat landscape. As organizations increasingly adopt cloud services, CASBs are poised to play an even more critical role in securing sensitive data and ensuring compliance. This section explores the emerging trends, future developments, and adaptations that will shape the future of CASBs.
Integration with Zero Trust Architecture
The integration of CASBs with Zero Trust architectures is becoming increasingly important. This approach assumes no implicit trust, requiring continuous verification of every user and device accessing resources, regardless of their location.CASBs are adapting to support Zero Trust principles through several key features:
- Context-Aware Access Control: CASBs are enhancing their ability to assess access requests based on a variety of factors, including user identity, device posture, location, and behavior. This allows for more granular and dynamic access control policies that align with Zero Trust principles.
- Microsegmentation: CASBs are facilitating microsegmentation within cloud environments, enabling organizations to isolate sensitive data and applications. This limits the impact of potential breaches by restricting lateral movement within the cloud infrastructure.
- Continuous Monitoring and Verification: CASBs are incorporating continuous monitoring and verification mechanisms to detect and respond to anomalous behavior in real-time. This includes analyzing user activity, network traffic, and device security posture to identify potential threats and enforce access policies dynamically.
Advancements in Artificial Intelligence and Machine Learning
Artificial intelligence (AI) and machine learning (ML) are transforming the capabilities of CASBs, enabling more proactive and intelligent security measures.AI and ML are being applied in the following ways:
- Threat Detection and Response: AI-powered CASBs can analyze vast amounts of data to identify sophisticated threats, such as insider threats and advanced persistent threats (APTs), that might be missed by traditional security tools. They can also automate threat response actions, such as blocking malicious activity or quarantining compromised accounts.
- User and Entity Behavior Analytics (UEBA): ML algorithms are used to establish a baseline of normal user behavior and detect deviations that may indicate malicious activity or compromised accounts. This enables CASBs to identify and respond to threats more quickly and effectively.
- Data Loss Prevention (DLP) Enhancements: AI and ML are improving DLP capabilities by enabling CASBs to understand the context of data and identify sensitive information more accurately. This includes the ability to recognize data patterns, identify data exfiltration attempts, and enforce data protection policies more effectively.
Expanded Cloud Coverage and Integration
The proliferation of cloud services necessitates broader coverage and deeper integration capabilities for CASBs.The future of CASBs involves:
- Multi-Cloud Support: CASBs will need to provide comprehensive security across multiple cloud platforms, including AWS, Azure, and Google Cloud Platform (GCP), as well as hybrid cloud environments. This includes supporting consistent security policies, monitoring, and enforcement across all cloud environments.
- API-Driven Integration: CASBs will increasingly rely on API-driven integration to connect with a wider range of cloud services and security tools. This allows for seamless data sharing, automated threat response, and enhanced visibility into cloud environments.
- Support for Emerging Technologies: CASBs will need to adapt to new cloud technologies, such as serverless computing and containerization, to provide security for these rapidly evolving environments. This includes developing new features and capabilities to address the unique security challenges posed by these technologies.
Focus on Data Privacy and Compliance
With the increasing emphasis on data privacy and compliance regulations, CASBs will play a critical role in helping organizations meet these requirements.The evolution of CASBs in this area includes:
- Enhanced Data Governance: CASBs are evolving to provide more comprehensive data governance capabilities, including data discovery, classification, and labeling. This allows organizations to identify and protect sensitive data more effectively, ensuring compliance with regulations such as GDPR, CCPA, and HIPAA.
- Automated Compliance Reporting: CASBs are automating compliance reporting by providing pre-built reports and dashboards that demonstrate compliance with relevant regulations. This reduces the burden on security teams and simplifies the audit process.
- Data Residency Controls: CASBs are enabling organizations to enforce data residency controls, ensuring that sensitive data is stored and processed in specific geographic locations. This is essential for meeting data privacy regulations and complying with industry-specific requirements.
Ending Remarks

In summary, a Cloud Access Security Broker is an essential tool for organizations embracing cloud services. It provides a multi-faceted approach to cloud security, from data loss prevention and threat protection to access control and compliance. As cloud adoption continues to rise, the role of CASBs will become even more critical in safeguarding sensitive information and ensuring a secure and compliant cloud experience.
By implementing a robust CASB solution, businesses can confidently leverage the power of the cloud while mitigating potential risks.
Helpful Answers
What is the primary difference between a CASB and a firewall?
While firewalls primarily protect the network perimeter, CASBs focus on securing cloud applications and the data within them, offering more granular control and visibility into cloud usage.
Can a CASB protect against insider threats?
Yes, CASBs use User Behavior Analytics (UBA) to identify unusual activity that might indicate malicious intent from within the organization, such as compromised accounts or data exfiltration attempts.
How does a CASB help with compliance?
CASBs assist with compliance by enforcing policies related to data privacy, access control, and data retention, as well as generating reports that demonstrate adherence to regulations like GDPR and HIPAA.
Is a CASB difficult to implement?
Implementation varies depending on the deployment model and vendor. API-based CASBs are often easier to deploy, while proxy-based solutions may require more configuration. Most vendors offer comprehensive documentation and support to assist with the process.
What are the ongoing costs associated with using a CASB?
Ongoing costs typically include subscription fees based on the number of users, applications monitored, or data volume. There may also be costs for support and maintenance.