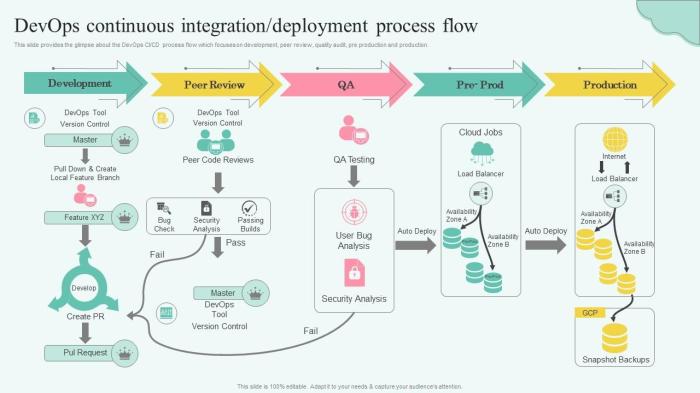
In the dynamic realm of software development, the concept of a CI/CD pipeline has emerged as a cornerstone of modern DevOps practices. This methodology revolutionizes the way software is built, tested, and deployed, enabling teams to deliver high-quality products faster and more reliably. It’s a fundamental shift from traditional, often cumbersome, development processes to an automated, streamlined approach that fosters collaboration and efficiency.
This exploration delves into the core principles of CI/CD, dissecting its components, benefits, and the tools that make it a reality. We will uncover how continuous integration, continuous delivery, and continuous deployment work together to create a robust and efficient software development lifecycle. From understanding the key stages of a pipeline to implementing best practices, this guide will provide a comprehensive understanding of how CI/CD can transform your development workflows.
Definition of a CI/CD Pipeline
A CI/CD pipeline is a series of automated steps that enable software development teams to deliver code changes more frequently and reliably. It streamlines the process of building, testing, and deploying software, allowing for faster feedback loops and quicker time to market. This automation reduces manual errors, improves code quality, and increases overall development efficiency.
Core Concept of a CI/CD Pipeline
The fundamental idea behind a CI/CD pipeline is to automate the software release process. This automation covers everything from code integration to deployment, minimizing human intervention and ensuring consistency. The pipeline typically involves several stages, each designed to perform a specific task, such as building the code, running tests, and deploying the application to a staging or production environment. Each stage is triggered automatically when the preceding stage is completed successfully, creating a smooth flow of code changes from development to the end-user.
This process is often visualized as a pipeline, representing the flow of code through various stages.
Continuous Integration (CI)
Continuous Integration (CI) is a development practice where developers frequently merge their code changes into a central repository. Each merge triggers an automated build and test process. The primary goal of CI is to identify and address integration issues early and often. This is achieved through automated tests that verify the code’s functionality and ensure that new changes do not break existing features.
- Developers integrate code changes frequently, ideally multiple times a day.
- Automated builds are performed to compile the code and create an executable.
- Automated tests, including unit tests, integration tests, and potentially others, are executed to ensure the code functions correctly.
- Feedback is provided to developers immediately, highlighting any build or test failures.
- This iterative process of integration, building, and testing helps catch bugs early, making them easier and cheaper to fix.
Continuous Delivery (CD)
Continuous Delivery (CD) builds upon Continuous Integration by automating the release process. With CD, code changes are automatically built, tested, and prepared for release to production. The deployment to production, however, is typically a manual step, often requiring approval from stakeholders. This ensures that the software is always in a deployable state.
- The code is automatically built and tested, as in CI.
- The application is packaged and prepared for deployment.
- The application is deployed to a staging environment for further testing and validation.
- Deployment to production is a manual step, triggered after successful staging tests and approvals.
- CD ensures that new features and bug fixes are always ready to be released.
Continuous Delivery vs. Continuous Deployment
Continuous Delivery and Continuous Deployment are often confused, but they represent distinct stages in the CI/CD process. The key difference lies in the automation of the deployment stage.
Continuous Delivery
- Code changes are automatically built, tested, and prepared for release.
- Deployment to production is a manual process, often requiring human approval.
- The focus is on ensuring the software is always in a releasable state.
Continuous Deployment
- Code changes are automatically built, tested, and deployed to production without manual intervention.
- The entire process, from code commit to production release, is fully automated.
- This approach enables faster release cycles and quicker feedback.
The Benefits of Implementing a CI/CD Pipeline
Implementing a CI/CD pipeline offers significant advantages for software development teams. By automating various stages of the software release lifecycle, organizations can achieve greater efficiency, improved software quality, and faster time-to-market. This section will delve into the specific benefits that CI/CD brings to the table.
Automating the Software Release Process
Automation is at the heart of CI/CD. It streamlines the entire software release process, minimizing manual intervention and human error.The benefits of automating the software release process include:
- Reduced Manual Effort: Automating tasks like code compilation, testing, and deployment frees up developers and operations teams from repetitive manual work. This allows them to focus on more strategic and creative activities.
- Increased Efficiency: Automated processes run faster and more consistently than manual processes. This leads to shorter release cycles and quicker feedback loops.
- Improved Consistency: Automation ensures that the same processes are followed every time, reducing the likelihood of inconsistencies and errors that can arise from manual procedures.
- Faster Deployment Frequency: By automating the release process, teams can deploy software more frequently. This allows for more rapid iteration, quicker response to user feedback, and faster delivery of new features.
Improving Software Quality and Reducing Errors
CI/CD pipelines incorporate automated testing at various stages, leading to higher software quality and fewer errors. This proactive approach helps catch bugs early in the development cycle.The role of CI/CD in improving software quality is multifaceted:
- Early Bug Detection: Automated testing, including unit tests, integration tests, and end-to-end tests, runs frequently, identifying bugs and defects early in the development process.
- Reduced Risk of Production Issues: Thorough testing before deployment minimizes the risk of deploying code with critical errors that could impact users.
- Faster Feedback Loops: Automated testing provides immediate feedback to developers, allowing them to quickly identify and fix issues. This leads to more rapid iteration and improved code quality.
- Consistent Code Quality: CI/CD pipelines often incorporate code analysis tools that enforce coding standards and identify potential code quality issues.
Accelerating Time-to-Market
A significant advantage of CI/CD is its ability to significantly reduce the time it takes to get software updates and new features into the hands of users.The impact of CI/CD on time-to-market is evident in several ways:
- Faster Release Cycles: Automated processes, including testing and deployment, shorten the time required to release new software versions.
- Reduced Lead Time: CI/CD pipelines reduce the lead time from code commit to production deployment.
- Rapid Feature Delivery: With faster release cycles, teams can deliver new features and updates to users more quickly.
- Competitive Advantage: Companies that can release software faster than their competitors gain a significant competitive advantage in the market.
Enhancing Team Collaboration and Efficiency
CI/CD pipelines promote better collaboration and communication between development and operations teams. This collaboration leads to increased efficiency and a more streamlined workflow.The ways CI/CD enhances team collaboration and efficiency are:
- Improved Communication: CI/CD encourages collaboration between developers and operations teams. This leads to better communication and a shared understanding of the software release process.
- Increased Transparency: CI/CD pipelines provide greater visibility into the software release process. This transparency allows teams to track progress, identify bottlenecks, and resolve issues more effectively.
- Reduced Conflicts: Automated processes and standardized workflows minimize conflicts between development and operations teams.
- Shared Responsibility: CI/CD promotes a culture of shared responsibility for the software release process. This shared responsibility leads to greater team alignment and improved outcomes.
Key Stages of a CI/CD Pipeline
A CI/CD pipeline automates the software release process, enabling faster and more reliable deployments. This involves a series of stages, each designed to perform specific tasks, ensuring code quality and facilitating continuous delivery. Understanding these stages is crucial for effectively implementing and managing a CI/CD pipeline.
Build Stage
The build stage transforms source code into an executable application. This stage typically involves several steps that prepare the code for testing and deployment.
- Code Compilation: The source code is compiled into machine-readable instructions. For instance, Java code is compiled into bytecode that can be executed by the Java Virtual Machine (JVM). This process checks for syntax errors and transforms the human-readable code into an intermediate or executable format.
- Dependency Management: Dependencies, which are libraries and frameworks required by the application, are resolved and integrated. Tools like Maven for Java or npm for JavaScript manage these dependencies, ensuring that all necessary components are available.
- Unit Testing: Small, isolated tests are executed to verify individual components or functions of the code. These tests help to identify bugs early in the development cycle. For example, a unit test might verify that a specific function correctly calculates the sum of two numbers.
- Code Analysis (Static Analysis): Tools are used to analyze the code for potential issues such as coding style violations, security vulnerabilities, and code quality problems. This process helps maintain code consistency and identify potential issues before runtime. Tools like SonarQube are commonly used for this purpose.
- Artifact Creation: The compiled code, along with its dependencies, is packaged into an artifact, such as a JAR file, a WAR file, or a container image (e.g., Docker image). This artifact is then used in subsequent stages.
Test Stage
The test stage validates the functionality, performance, and security of the built application. Various testing types are employed to ensure the software meets the required quality standards.
- Unit Testing: These tests, performed in the build stage, are revisited here to ensure that all individual units of code function correctly. The focus is on isolated components.
- Integration Testing: This involves testing the interaction between different components or modules of the application. For example, testing the communication between a database and the application’s user interface. This helps to identify issues that arise when different parts of the system work together.
- System Testing: The entire application is tested as a whole, simulating real-world scenarios. This stage verifies that all components work together correctly and that the application meets the specified requirements.
- User Acceptance Testing (UAT): End-users or stakeholders test the application to ensure it meets their needs and expectations. This stage provides valuable feedback on the usability and functionality of the software.
- Performance Testing: This evaluates the application’s performance under various load conditions. This includes load testing (simulating a high number of users), stress testing (testing the application’s limits), and endurance testing (testing the application’s performance over an extended period).
- Security Testing: This identifies vulnerabilities in the application’s security. This includes penetration testing, vulnerability scanning, and code review to identify and address potential security threats.
Deployment Stage
The deployment stage involves releasing the application to a production or staging environment. Different deployment strategies are used to minimize downtime and risk.
- Environment Preparation: The target environment (e.g., production, staging) is prepared for the deployment. This includes configuring servers, databases, and other necessary infrastructure.
- Artifact Deployment: The built artifact is deployed to the target environment. This might involve copying files, configuring servers, or deploying container images.
- Configuration: Application-specific configurations are applied to the deployed application. This includes setting environment variables, configuring databases, and other environment-specific settings.
- Testing (Post-Deployment): After deployment, post-deployment tests are performed to verify the application is functioning correctly in the new environment. These tests can include smoke tests and functional tests.
- Deployment Strategies: Various deployment strategies are used to minimize downtime and risk:
- Rolling Deployment: The application is updated incrementally across a set of servers or instances. This approach allows for gradual updates, minimizing downtime.
- Blue-Green Deployment: Two identical environments (blue and green) are maintained. The green environment receives the new deployment, and traffic is switched from the blue to the green environment after testing. This allows for a quick rollback if issues arise.
- Canary Deployment: A small subset of users are directed to the new version (canary) while the rest of the users continue to use the existing version. This allows for monitoring the performance of the new version before rolling it out to all users.
Tools and Technologies Used in CI/CD
The effectiveness of a CI/CD pipeline hinges on the tools and technologies employed at each stage. These components automate processes, ensure consistency, and facilitate rapid deployment. Selecting the right combination of tools depends on project requirements, team expertise, and infrastructure. A well-chosen toolset optimizes the CI/CD pipeline, leading to faster release cycles and improved software quality.
Here’s a look at the essential tools and technologies that power CI/CD pipelines.
CI Tools
Continuous Integration (CI) tools automate the build, testing, and integration phases of the software development lifecycle. These tools trigger builds automatically upon code changes, run unit and integration tests, and provide feedback to developers. Several CI tools are popular choices within the DevOps community. Some of the most widely adopted CI tools include:
- Jenkins: An open-source automation server widely used for CI/CD. Jenkins supports a vast ecosystem of plugins, enabling integration with various tools and technologies. It is highly customizable and can handle complex workflows.
- GitLab CI: Integrated directly within the GitLab platform, GitLab CI offers a seamless CI/CD experience for projects hosted on GitLab. It leverages the .gitlab-ci.yml file for defining pipelines and supports parallel execution.
- CircleCI: A cloud-based CI/CD platform known for its ease of use and speed. CircleCI integrates well with popular version control systems and offers robust support for containerization.
- Travis CI: Another cloud-based CI service, popular for open-source projects. It provides a straightforward configuration process and supports multiple programming languages.
- TeamCity: A CI/CD server from JetBrains, known for its rich feature set and user-friendly interface. It integrates well with JetBrains IDEs and supports a wide range of technologies.
CD Tools
Continuous Delivery (CD) tools automate the deployment and release of software. They often work in conjunction with CI tools to move built artifacts through various environments (e.g., staging, production). The CD tools ensure a consistent and reliable deployment process. Some of the commonly used CD tools include:
- Ansible: An open-source automation engine used for configuration management, application deployment, and task automation. Ansible uses a simple, human-readable YAML format for defining configurations.
- Kubernetes: A container orchestration platform that automates the deployment, scaling, and management of containerized applications. Kubernetes is widely used for deploying and managing applications in production environments.
- Docker: A platform for building, shipping, and running applications in containers. Docker enables consistent application execution across different environments and simplifies the deployment process.
- Terraform: An infrastructure-as-code tool that allows for defining and provisioning infrastructure resources. Terraform supports multiple cloud providers and enables automated infrastructure management.
- Spinnaker: An open-source continuous delivery platform designed for multi-cloud deployments. Spinnaker provides features for managing complex deployments and rollback strategies.
Technologies that Support CI/CD
Several core technologies underpin and facilitate the CI/CD process, enabling automation, version control, and efficient workflows. These technologies are essential for creating a robust and effective CI/CD pipeline.
- Version Control Systems: These systems track changes to code over time, enabling collaboration, versioning, and rollback capabilities. Git is the most popular version control system, providing a distributed and flexible platform for managing code.
- Containerization: Containerization technologies, such as Docker, package applications and their dependencies into isolated units called containers. This ensures consistency across different environments and simplifies deployment.
- Infrastructure as Code (IaC): IaC tools, such as Terraform and Ansible, allow infrastructure to be defined and managed as code. This approach enables automated infrastructure provisioning and configuration, ensuring consistency and repeatability.
- Configuration Management: Configuration management tools automate the configuration and management of servers and applications. Ansible, Chef, and Puppet are examples of configuration management tools.
- Monitoring and Logging: Monitoring and logging tools are critical for observing the performance and health of applications and infrastructure. These tools provide insights into the behavior of the system and enable proactive issue detection. Examples include Prometheus, Grafana, and the ELK stack (Elasticsearch, Logstash, Kibana).
Comparison of CI/CD Tools
Choosing the right CI/CD tool can significantly impact the efficiency and effectiveness of your software development process. The following table compares three popular CI/CD tools, highlighting their key features, advantages, and disadvantages:
| Feature | Jenkins | GitLab CI | CircleCI |
|---|---|---|---|
| Type | Open-Source | Integrated with GitLab | Cloud-Based |
| Ease of Use | Moderate (requires setup and configuration) | Easy (integrated within GitLab) | Easy (user-friendly interface) |
| Customization | Highly customizable (extensive plugin ecosystem) | Customizable (YAML-based configuration) | Customizable (YAML-based configuration) |
| Integration | Wide range of integrations via plugins | Seamless integration with GitLab | Excellent integrations with version control systems and cloud providers |
| Scalability | Scalable (can be scaled with appropriate infrastructure) | Scalable (can handle large projects) | Scalable (cloud-based infrastructure) |
| Pros | Highly flexible, extensive plugin ecosystem, open-source, large community support. | Tight integration with GitLab, easy setup, built-in features, good for GitLab users. | Easy to use, fast build times, excellent integration with various platforms and services, cloud-based. |
| Cons | Can be complex to set up and manage, requires dedicated infrastructure, security can be a concern if not configured properly. | Limited to GitLab projects, less flexibility than Jenkins. | Can be expensive for large projects, limited customization compared to Jenkins. |
Continuous Integration Practices
Continuous Integration (CI) is a cornerstone of modern software development, aiming to integrate code changes frequently and automatically, enabling faster feedback and reduced integration issues. It emphasizes the importance of collaboration and automated processes to streamline the development lifecycle. This section will delve into the key practices that define a successful CI implementation.
Frequent Code Integration
Frequent code integration is the core principle of CI. Developers integrate their code changes into a shared repository multiple times a day. This contrasts with traditional development models where code integration occurred less frequently, often at the end of a development cycle.* This practice minimizes the time developers spend working in isolation.
- It allows for early detection of integration issues.
- It promotes collaboration and communication within the development team.
- It enables faster feedback cycles, allowing for quick identification and resolution of bugs.
For example, a team might set a goal to integrate code at least once per day, or even multiple times per day, depending on the project’s size and complexity. Each integration triggers an automated build and test process, ensuring that the integrated code functions correctly.
Role of Automated Testing in CI
Automated testing is integral to CI, providing rapid feedback on the quality of code changes. Automated tests are executed automatically as part of the CI pipeline, allowing developers to identify and fix issues early in the development process.* Automated testing reduces the reliance on manual testing.
- It ensures consistent testing across all code changes.
- It helps identify bugs and defects quickly.
- It improves code quality and reduces the risk of releasing buggy software.
Various types of automated tests are employed in CI, including unit tests, integration tests, and end-to-end tests. Unit tests verify individual components, integration tests check the interaction between components, and end-to-end tests simulate user scenarios. A comprehensive test suite covering different aspects of the application is crucial for ensuring the reliability of the CI process.
Managing and Resolving Merge Conflicts
Merge conflicts are inevitable when multiple developers work on the same codebase simultaneously. CI processes should include strategies for managing and resolving these conflicts efficiently.* Merge conflicts arise when changes made by different developers affect the same lines of code.
- CI tools and version control systems, such as Git, provide mechanisms for identifying and resolving conflicts.
- Developers must communicate effectively to understand the changes and resolve conflicts.
- Regular code pulls and frequent integration can reduce the likelihood and complexity of merge conflicts.
When a merge conflict occurs, the developer must manually review the conflicting code and decide how to merge the changes. This may involve choosing one version of the code, combining parts of both versions, or rewriting the code to accommodate both changes. Effective conflict resolution requires a good understanding of the code and the changes being made.
Importance of Code Reviews in the CI Process
Code reviews are a critical part of the CI process, where developers review each other’s code changes before they are merged into the main codebase. Code reviews improve code quality, promote knowledge sharing, and help identify potential issues early.* Code reviews help to identify potential bugs, security vulnerabilities, and code style violations.
- Reviewers provide feedback and suggestions to improve the code.
- Code reviews promote knowledge sharing within the development team.
- They ensure that code adheres to established standards and best practices.
The code review process typically involves the following steps:
- A developer submits their code changes for review.
- Another developer (the reviewer) examines the code.
- The reviewer provides feedback, suggestions, and comments.
- The developer addresses the reviewer’s comments and makes necessary changes.
- The code is approved and merged into the main codebase.
Effective code reviews require a collaborative environment where developers feel comfortable providing and receiving feedback. Code reviews should be conducted promptly to ensure that changes are integrated quickly.
Continuous Delivery and Deployment Strategies
Continuous Delivery (CD) and Deployment are critical components of a CI/CD pipeline, automating the release process and enabling faster, more reliable software releases. This section delves into various deployment strategies, the role of infrastructure as code, and the procedures for automating deployments.
Deployment Strategies
Deployment strategies define how new software versions are released to production. Choosing the right strategy depends on the application’s requirements, the desired level of risk tolerance, and the need for minimal downtime. Several strategies exist, each with its own advantages and disadvantages.
- Blue-Green Deployment: This strategy involves maintaining two identical environments: blue (current live version) and green (new version). When a new version is ready, it’s deployed to the green environment. Once testing is complete, traffic is switched from blue to green, typically using a load balancer. If issues arise, traffic can be quickly reverted to the blue environment.
For instance, a retail website could use blue-green deployment.
The blue environment is the live website, handling all customer traffic. The green environment contains the updated version of the website. After thorough testing on the green environment, the load balancer is configured to direct all traffic to the green environment. If any critical bugs or performance issues are detected after the switch, the load balancer can be quickly reconfigured to revert traffic to the blue environment, minimizing downtime and impact on customers.
- Canary Deployment: This strategy involves releasing a new version to a small subset of users (the “canary” group) while the majority continue using the existing version. This allows for real-world testing and monitoring of the new version’s performance before a full rollout. The canary group can be selected based on various criteria, such as location, device type, or user segment.
A streaming service, for example, could use canary deployments.
They might release a new video player version to 5% of their users. They then monitor the canary group for performance issues, such as buffering or playback errors, and gather feedback. If the new version performs well, the rollout is expanded to a larger percentage of users. If issues are detected, the rollout can be halted or rolled back to the previous version, minimizing the impact on the overall user experience.
- Rolling Deployment: In this strategy, the new version is rolled out incrementally to a subset of servers or instances, while the existing version continues to run on the remaining servers. This process continues until all servers are running the new version. This minimizes downtime, as only a portion of the users are affected during the update.
Consider a web application running on multiple servers.
A rolling deployment would update one server at a time. While one server is being updated, the other servers continue to serve requests. Once the update is complete on the first server, the next server is updated, and so on. This ensures that the application remains available throughout the deployment process.
- A/B Testing: This strategy involves deploying two different versions of an application or feature to different user groups simultaneously. The goal is to compare the performance of the two versions and determine which one is more effective based on metrics like conversion rates or user engagement.
An e-commerce website might use A/B testing to compare two different checkout processes.
Half of the users would see one checkout process, and the other half would see a different one. The website would then track metrics such as the completion rate of each checkout process. The checkout process that results in a higher completion rate would be deemed the more effective version.
The Role of Infrastructure as Code in CD
Infrastructure as Code (IaC) is the practice of managing and provisioning infrastructure through code rather than manual processes. IaC is crucial for automating CD because it enables the consistent and repeatable deployment of infrastructure components alongside application code. This ensures that the environment in which the application runs is always properly configured and consistent.
- Automation: IaC automates infrastructure provisioning, eliminating manual configuration steps. This reduces the risk of human error and accelerates the deployment process.
- Consistency: IaC ensures that infrastructure is consistently configured across all environments (development, testing, production). This reduces inconsistencies that can lead to deployment failures.
- Version Control: IaC code is stored in version control systems, allowing for tracking changes, collaboration, and rollbacks.
- Scalability: IaC enables the easy scaling of infrastructure to meet changing demands.
- Example: Using tools like Terraform or AWS CloudFormation, developers can define the infrastructure needed for their application (e.g., servers, databases, load balancers) in code. This code can then be executed as part of the CD pipeline to automatically provision and configure the infrastructure.
Procedures for Automating Deployments
Automating deployments involves a series of steps that are executed automatically as part of the CD pipeline. These steps typically include:
- Code Integration: Triggered by code commits, the pipeline starts by integrating the latest code changes.
- Build and Testing: The code is built, and automated tests (unit, integration, and end-to-end) are executed to ensure code quality.
- Artifact Creation: Upon successful testing, an artifact (e.g., a container image, a deployable package) is created.
- Environment Provisioning (with IaC): If necessary, the infrastructure for the target environment is provisioned using IaC.
- Deployment: The artifact is deployed to the target environment using the chosen deployment strategy.
- Verification and Monitoring: Automated tests and monitoring tools verify the successful deployment and monitor the application’s performance.
- Rollback (if necessary): If issues are detected, the pipeline automatically rolls back to the previous version.
Advantages and Disadvantages of Canary Deployments
Canary deployments offer several benefits but also come with some drawbacks.
- Advantages:
- Reduced Risk: Deployments are tested on a small subset of users, minimizing the impact of any issues.
- Early Detection: Issues are detected early in the deployment process, before they affect a large number of users.
- Faster Rollbacks: If issues arise, the rollback is quick and affects only a small percentage of users.
- Real-World Testing: Canary deployments allow for testing in a real-world environment with actual user traffic.
- Disadvantages:
- Complexity: Setting up and managing canary deployments can be more complex than other deployment strategies.
- Requires Monitoring: Careful monitoring is required to detect issues and make decisions about the rollout.
- Potential for Data Corruption: If the new version interacts with data in a way that causes problems, it could affect a subset of users.
- Can be time-consuming: Rolling out to all users can take time as you wait for the canary phase to finish.
Security Considerations in CI/CD
Integrating security into a CI/CD pipeline is crucial for protecting applications and infrastructure from vulnerabilities. Without proper security measures, the automation and speed of CI/CD can inadvertently introduce risks. Addressing security concerns proactively throughout the pipeline ensures a robust and resilient software delivery process.
Security Challenges in CI/CD Pipelines
CI/CD pipelines present unique security challenges that require careful consideration. The rapid pace of development, the use of automation, and the integration of various tools introduce new attack vectors that must be addressed.
- Secrets Management: Hardcoding secrets (API keys, passwords, etc.) directly into the code or configuration files poses a significant risk. If compromised, these secrets can provide attackers with unauthorized access to systems and data.
- Supply Chain Attacks: The CI/CD pipeline often relies on third-party libraries, dependencies, and tools. Vulnerabilities in these components can be exploited to compromise the entire software build and deployment process. This includes attacks on the build environment itself.
- Configuration Management: Misconfigured infrastructure and application settings can create security loopholes. Incorrectly configured cloud resources, databases, or web servers can expose sensitive information or provide attackers with entry points.
- Lack of Security Testing: Failing to integrate security testing into the pipeline can lead to vulnerabilities being deployed to production. Without regular scans and assessments, security flaws may remain undetected for extended periods.
- Access Control and Permissions: Inadequate access controls within the CI/CD pipeline can lead to unauthorized modifications, deployments, and access to sensitive data. Weakly configured roles and permissions can be exploited by malicious actors.
Practices for Securing the CI/CD Process
Implementing robust security practices throughout the CI/CD pipeline is essential for mitigating risks. These practices should be integrated into every stage of the pipeline to ensure continuous protection.
- Secrets Management: Implement a dedicated secrets management solution (e.g., HashiCorp Vault, AWS Secrets Manager, Azure Key Vault) to securely store and manage sensitive information. Use environment variables to inject secrets into the build and deployment processes, avoiding hardcoding. Rotate secrets regularly to minimize the impact of a potential compromise.
- Dependency Management: Regularly scan dependencies for known vulnerabilities using tools like Snyk, OWASP Dependency-Check, or Trivy. Automate the process of updating dependencies to the latest secure versions. Use a software bill of materials (SBOM) to track all dependencies and their versions.
- Infrastructure as Code (IaC) Security: Implement security checks and validation as part of your IaC pipelines (e.g., Terraform, CloudFormation). Use tools like tfsec, Checkov, or Terrascan to identify misconfigurations and vulnerabilities in your infrastructure code before deployment.
- Container Security: Scan container images for vulnerabilities using tools like Clair, Anchore, or Trivy. Implement container runtime security monitoring to detect and prevent malicious activity within containers. Employ container image signing and verification to ensure the integrity of images.
- Access Control and Permissions: Enforce the principle of least privilege, granting users and services only the minimum necessary permissions. Implement robust authentication and authorization mechanisms within the CI/CD pipeline. Regularly review and audit access controls to identify and remediate any weaknesses.
Methods for Incorporating Security Testing into the Pipeline
Integrating security testing into the CI/CD pipeline is a critical step towards identifying and mitigating vulnerabilities early in the development lifecycle. Automating security tests ensures that security is not an afterthought but an integral part of the process.
- Static Application Security Testing (SAST): Integrate SAST tools (e.g., SonarQube, Veracode, Coverity) into the build process to analyze source code for vulnerabilities, coding errors, and security flaws. SAST should be performed on every code commit or pull request to catch issues early.
- Dynamic Application Security Testing (DAST): Implement DAST tools (e.g., OWASP ZAP, Burp Suite, Netsparker) to test running applications for vulnerabilities. DAST scans can be automated as part of the deployment process or on a scheduled basis.
- Software Composition Analysis (SCA): Employ SCA tools (e.g., Snyk, WhiteSource, Black Duck) to identify vulnerabilities in open-source libraries and dependencies. SCA helps to track and manage the risks associated with using third-party components.
- Interactive Application Security Testing (IAST): Use IAST tools (e.g., Contrast Security, HCL AppScan on Cloud) to combine the benefits of SAST and DAST. IAST instruments the application to provide real-time feedback on security vulnerabilities during testing.
- Penetration Testing: Conduct regular penetration tests, either manually or automated, to simulate real-world attacks and identify vulnerabilities that may not be detected by other testing methods. Penetration testing can be performed as part of the release process or on a periodic schedule.
Diagram: Security Checkpoints within a CI/CD Pipeline
The following diagram illustrates security checkpoints integrated into a typical CI/CD pipeline. The pipeline stages include Code Commit, Build, Test, and Deploy, with security checks integrated at various points.
Diagram Description:
The diagram illustrates a CI/CD pipeline with security checkpoints at different stages. The pipeline begins with the “Code Commit” stage, where developers commit code changes. Security checks begin here. The next stage is “Build,” where the code is compiled and packaged. In this stage, there are SAST and SCA checks.
The following stage is “Test,” where various tests are performed. DAST, IAST, and Penetration Testing are integrated here. The final stage is “Deploy,” where the application is deployed to production. Before deployment, security checks, like secrets validation, and infrastructure-as-code security checks are performed. At the end of the “Deploy” stage, there’s a monitoring and alerting system.
The diagram demonstrates a continuous loop, with feedback loops to the developers if security issues are detected. The diagram also shows the use of secrets management and container security throughout the pipeline.
Monitoring and Logging in CI/CD
Monitoring and logging are crucial components of a successful CI/CD pipeline. They provide valuable insights into the performance, health, and security of the pipeline and the applications it deploys. Without effective monitoring and logging, it becomes challenging to identify bottlenecks, troubleshoot issues, and ensure the overall reliability and efficiency of the CI/CD process.
Importance of Monitoring in a CI/CD Environment
Monitoring in a CI/CD environment is essential for several reasons. It allows for proactive issue detection, performance optimization, and continuous improvement. By tracking key metrics, teams can identify potential problems before they impact users, optimize resource allocation, and streamline the pipeline for faster and more reliable deployments. Effective monitoring also supports faster mean time to resolution (MTTR) and provides data for informed decision-making.
Tools for Monitoring CI/CD Pipelines
Several tools are available to monitor CI/CD pipelines, each offering different features and capabilities. These tools help visualize metrics, set alerts, and provide historical data for analysis.
- Prometheus: Prometheus is a popular open-source monitoring system. It collects metrics from various sources using a pull model, stores them as time series data, and provides a powerful query language (PromQL) for analysis. Prometheus is well-suited for monitoring containerized environments and is often integrated with Kubernetes. It allows you to monitor a wide range of metrics, from application performance to infrastructure health.
An example of its use would be tracking the number of builds triggered, the average build time, or the success/failure rate of deployments.
- Grafana: Grafana is a data visualization and dashboarding tool that works well with Prometheus. It allows users to create customizable dashboards to visualize metrics collected by Prometheus and other data sources. Grafana’s flexibility makes it easy to create dashboards that provide a comprehensive overview of the CI/CD pipeline’s performance. You can create dashboards showing build success rates, deployment times, and resource utilization.
- ELK Stack (Elasticsearch, Logstash, Kibana): The ELK Stack is a powerful combination for log management and analysis. Elasticsearch is a search and analytics engine, Logstash is a data processing pipeline, and Kibana is a visualization tool. This stack is used to collect, process, and visualize logs generated by the CI/CD pipeline and the applications it deploys. The ELK stack allows you to analyze log data to identify errors, track performance, and troubleshoot issues.
For example, you could use it to search for specific error messages in application logs, or to visualize the frequency of different types of events over time.
- Datadog: Datadog is a monitoring and analytics platform that provides comprehensive visibility into the entire technology stack, including CI/CD pipelines. It offers a wide range of integrations, including those for build servers, container orchestration platforms, and cloud providers. Datadog’s features include real-time dashboards, alerting, and anomaly detection. It can monitor metrics like build durations, deployment success rates, and resource utilization.
- New Relic: New Relic is another popular observability platform that helps monitor and analyze the performance of applications and infrastructure. It offers features for application performance monitoring (APM), infrastructure monitoring, and log management. New Relic can be used to track the performance of CI/CD pipelines and the applications they deploy. It offers real-time dashboards and alerting capabilities to quickly identify and resolve issues.
Significance of Logging for Troubleshooting and Auditing
Logging is critical for troubleshooting and auditing CI/CD pipelines. Logs provide a detailed record of events, including build processes, deployment activities, and application behavior. This information is invaluable for identifying the root cause of issues, tracking down errors, and ensuring compliance with security and regulatory requirements. Comprehensive logging enables teams to understand what happened, when it happened, and why it happened.
Key Metrics to Monitor in a CI/CD Pipeline
Monitoring key metrics provides valuable insights into the performance and health of a CI/CD pipeline. The following are examples of key metrics that should be monitored:
- Build Time: Measures the time it takes to build the application from source code. Monitoring build time helps identify bottlenecks in the build process, such as slow compilation or dependency resolution. Significant increases in build time can indicate performance issues that need to be addressed.
- Deployment Frequency: Measures how often code is deployed to production. A higher deployment frequency generally indicates a more efficient and agile development process. Monitoring this metric helps assess the speed of the release cycle.
- Deployment Success Rate: Tracks the percentage of successful deployments. A low success rate indicates problems in the deployment process, such as configuration errors or application compatibility issues. Monitoring this metric is critical for ensuring the reliability of the deployed applications.
- Mean Time to Recovery (MTTR): Measures the average time it takes to recover from an incident or failure. A lower MTTR indicates a more efficient incident response process. This metric is a crucial indicator of the pipeline’s resilience.
- Failed Builds: The number of failed builds provides an indication of code quality and the stability of the build process. A high number of failed builds may indicate problems in the code, tests, or build environment.
- Test Coverage: Measures the percentage of code covered by automated tests. Higher test coverage helps ensure that more of the codebase is tested, reducing the risk of defects. Monitoring this metric helps assess the thoroughness of testing.
- Resource Utilization (CPU, Memory, Disk I/O): Monitoring resource utilization helps identify performance bottlenecks in the build and deployment environments. High resource utilization can slow down the pipeline and impact performance. This metric helps ensure that the infrastructure is adequately provisioned.
- Number of Tests Run and Test Pass Rate: Tracking the number of tests run and the pass rate provides insights into the effectiveness of the testing strategy. A decreasing pass rate can indicate issues in the codebase or tests.
- Security Scan Results: Monitoring the results of security scans (e.g., static code analysis, vulnerability scanning) is essential for identifying and addressing security vulnerabilities. This helps ensure the security of the application and infrastructure.
CI/CD Pipeline for Different Application Types
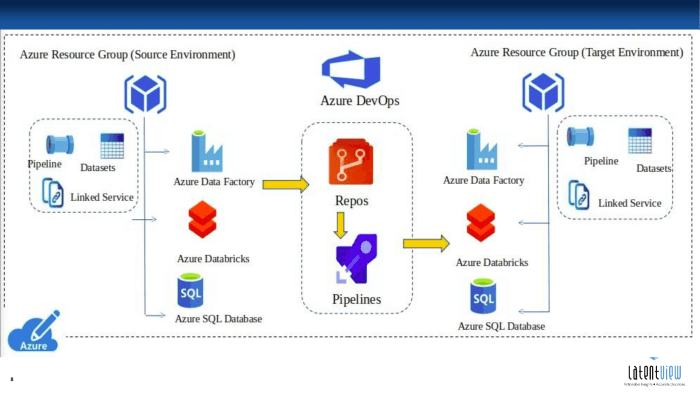
The versatility of CI/CD pipelines allows them to be adapted for a wide array of application types, each with its unique requirements and challenges. Tailoring a CI/CD pipeline to the specific characteristics of an application ensures efficient development, testing, and deployment processes, ultimately leading to faster release cycles and improved software quality. This section will delve into how CI/CD is implemented for various application types, providing practical examples and insights.
CI/CD for Web Applications
Web applications, being the backbone of many online services, benefit significantly from CI/CD pipelines. The rapid iteration and frequent updates common in web development are perfectly suited to the automated processes of CI/CD.Web application CI/CD pipelines typically encompass the following stages:
- Code Commit and Version Control: Developers commit code changes to a version control system like Git. This triggers the CI process.
- Build: The build stage compiles the code and prepares it for testing. This may involve transpiling code (e.g., from TypeScript to JavaScript), bundling assets, and generating deployment artifacts.
- Automated Testing: Comprehensive testing is crucial. This includes unit tests, integration tests, and end-to-end tests to ensure functionality and prevent regressions. Tools like Jest, Selenium, and Cypress are commonly used.
- Deployment: The application is deployed to a staging environment after successful testing. This allows for final checks and user acceptance testing.
- Production Deployment: Once the staging environment is validated, the application is deployed to the production environment. This might involve blue/green deployments, canary releases, or rolling updates to minimize downtime.
- Monitoring and Feedback: After deployment, the application is continuously monitored for performance, errors, and user behavior. Feedback is used to inform future development cycles.
CI/CD for Microservices
Microservices architectures, with their independent, deployable units, are ideally suited for CI/CD. The ability to deploy individual services without impacting the entire application allows for faster releases and increased agility.Key considerations for CI/CD in a microservices environment include:
- Independent Pipelines: Each microservice has its own dedicated CI/CD pipeline. This allows for independent development, testing, and deployment cycles.
- Containerization: Docker containers are frequently used to package microservices, ensuring consistent environments across development, testing, and production.
- Orchestration: Tools like Kubernetes manage the deployment, scaling, and networking of microservices.
- Service Discovery: Mechanisms like Consul or etcd enable microservices to find and communicate with each other.
- API Gateway: An API gateway handles routing, authentication, and other cross-cutting concerns, simplifying service interactions.
Microservices CI/CD pipelines often involve these steps:
- Code commit triggers a build process for the specific microservice.
- The microservice is built and packaged into a container image.
- Automated tests, including unit, integration, and contract tests (using tools like Pact), are executed.
- The container image is deployed to a staging environment for testing.
- Upon successful testing, the image is deployed to production, potentially using strategies like blue/green deployments to minimize downtime.
- Monitoring and logging are essential to observe service health and performance.
CI/CD Pipeline Examples for Mobile Applications
Mobile applications, whether native or cross-platform, also benefit from CI/CD. Automating the build, testing, and deployment processes streamlines the development lifecycle and ensures faster releases to app stores.CI/CD pipelines for mobile apps typically incorporate these elements:
- Build Automation: Tools like Xcode (for iOS) and Gradle (for Android) automate the build process, generating the necessary artifacts (e.g., .ipa or .apk files).
- Automated Testing: Unit tests, UI tests (using tools like Espresso for Android or XCUITest for iOS), and integration tests are crucial for ensuring application quality.
- Code Signing: Proper code signing is essential for deploying applications to app stores.
- App Store Integration: CI/CD pipelines often integrate with app store services (e.g., App Store Connect or Google Play Console) to automate the release process.
- Distribution: Automated distribution to beta testers and internal teams facilitates feedback gathering and pre-release testing.
A typical mobile app CI/CD workflow involves:
- A developer commits code changes to the repository.
- The CI server triggers a build process.
- The application is built, and unit tests are executed.
- If tests pass, the application is signed.
- UI tests are performed on emulators or real devices.
- The application is deployed to a staging environment for user acceptance testing.
- After successful testing, the app is released to the app store.
- Monitoring and feedback are collected to improve future iterations.
Example: CI/CD Process for a Specific Application Type
This example demonstrates a simplified CI/CD pipeline for a web application built using React and deployed on AWS.
Application Type: React Web Application
Version Control: Git (GitHub)
CI Tool: Jenkins
Build Tool: npm
Testing Framework: Jest, Cypress
Deployment Target: AWS S3 and CloudFront
Pipeline Stages:
- Code Commit: Developer commits changes to the GitHub repository.
- Build: Jenkins triggers a build job. npm install and npm run build are executed.
- Unit Tests: Jest tests are run to validate component logic.
- Integration Tests: Cypress tests are executed to simulate user interactions.
- Deployment to Staging: If all tests pass, the application is deployed to an AWS S3 bucket used for staging.
- Staging Review: Manual review of the staging environment.
- Deployment to Production: After successful staging review, the application is deployed to the production S3 bucket, and CloudFront is invalidated to serve the new content.
- Monitoring: AWS CloudWatch monitors application performance and errors.
Best Practices for CI/CD Implementation
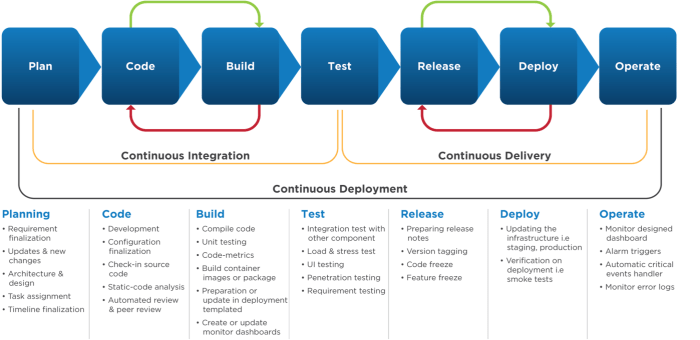
Implementing a CI/CD pipeline effectively requires careful planning, execution, and continuous refinement. Success depends on adopting best practices across various aspects, from version control to monitoring. This section Artikels key strategies for building and maintaining a robust and efficient CI/CD pipeline, ensuring faster releases, improved code quality, and enhanced collaboration.
Organizing Steps for Implementing a Successful CI/CD Pipeline
A well-defined implementation plan is crucial for a smooth transition to CI/CD. It helps teams avoid common pitfalls and ensures a systematic approach.
- Assess Current State: Begin by evaluating the existing development and deployment processes. Identify bottlenecks, manual steps, and areas for improvement. Understand the current infrastructure, tools, and team skills.
- Define Goals and Objectives: Clearly articulate the goals of implementing CI/CD. Determine specific metrics for success, such as reduced deployment frequency, faster time-to-market, and improved code quality. Set realistic expectations.
- Choose the Right Tools: Select CI/CD tools that align with the project’s needs and the team’s expertise. Consider factors like ease of use, integration capabilities, community support, and cost. Popular tools include Jenkins, GitLab CI, CircleCI, and Azure DevOps.
- Plan the Pipeline: Design the CI/CD pipeline stages, including source code management, build, testing (unit, integration, and end-to-end), and deployment. Define the triggers for each stage and the artifacts that will be produced.
- Implement Version Control: Establish a robust version control system (e.g., Git) to manage code changes and collaborate effectively. Implement a branching strategy to facilitate parallel development and feature releases.
- Automate Build and Testing: Automate the build process to compile code and create deployable artifacts. Implement automated testing to catch errors early in the development cycle. This includes unit tests, integration tests, and potentially performance tests.
- Automate Deployment: Automate the deployment process to various environments (development, staging, production). Use infrastructure-as-code tools (e.g., Terraform, Ansible) to manage infrastructure consistently.
- Monitor and Log: Implement comprehensive monitoring and logging to track the pipeline’s performance and identify issues. Set up alerts to notify the team of failures or performance degradation.
- Iterate and Improve: Continuously monitor the pipeline, gather feedback, and make improvements. Refine the pipeline based on performance data, team feedback, and evolving project requirements. This includes regularly reviewing and updating testing strategies.
- Train the Team: Provide adequate training to the team on the new tools, processes, and best practices. Ensure everyone understands their roles and responsibilities within the CI/CD pipeline.
Best Practices for Version Control and Branching Strategies
Version control is the cornerstone of a successful CI/CD pipeline. A well-defined branching strategy is essential for managing code changes, facilitating collaboration, and ensuring stability.
Version control provides a structured way to track changes, collaborate, and revert to previous versions of code. A good branching strategy enables parallel development, simplifies releases, and reduces the risk of conflicts.
- Choose a Version Control System: Select a version control system like Git, which is widely adopted and offers robust features for branching, merging, and collaboration. Git provides a distributed system, allowing each developer to have a local repository.
- Implement a Branching Strategy: Adopt a branching strategy like Gitflow or GitHub Flow to manage code changes effectively.
- Gitflow: Gitflow uses feature branches, develop branches, release branches, and hotfix branches. This is suitable for projects with scheduled releases.
- GitHub Flow: GitHub Flow uses a main branch (e.g., `main` or `master`) and feature branches. This is suitable for continuous deployment and frequent releases.
- Use Feature Branches: Create a dedicated branch for each new feature, bug fix, or enhancement. This isolates changes and allows for independent development.
- Write Clear Commit Messages: Write descriptive and concise commit messages that explain the changes made. This helps in understanding the code’s evolution and facilitates debugging.
- Perform Code Reviews: Implement code reviews to ensure code quality, identify potential issues, and share knowledge within the team. This process involves having another developer review the code before it is merged.
- Merge Regularly: Merge feature branches into the main branch frequently to minimize merge conflicts and integrate changes smoothly. Frequent merges also help to identify and resolve integration issues early on.
- Use Pull Requests: Use pull requests (or merge requests) to facilitate code reviews and merge code changes. Pull requests provide a platform for discussing changes, suggesting improvements, and ensuring code quality.
- Automate Branch Management: Automate tasks like branch creation, deletion, and merging using scripts or CI/CD tools. This reduces manual effort and minimizes the risk of errors.
- Protect Main Branches: Protect the main branch from direct commits. Enforce code reviews and automated tests before allowing merges to the main branch.
Tips for Managing Dependencies Effectively
Dependencies are an integral part of modern software development. Effective dependency management is crucial for building, testing, and deploying applications reliably. Poor dependency management can lead to build failures, security vulnerabilities, and deployment issues.
Dependencies refer to the external libraries, frameworks, and other software components that a project relies on. Managing these dependencies efficiently is vital for maintaining a stable and secure CI/CD pipeline.
- Use a Package Manager: Utilize a package manager (e.g., npm for JavaScript, Maven for Java, pip for Python) to manage dependencies and their versions. Package managers automate the process of downloading, installing, and updating dependencies.
- Specify Dependencies Clearly: Define dependencies in a configuration file (e.g., `package.json`, `pom.xml`, `requirements.txt`) with specific versions or version ranges. This ensures that the correct versions of dependencies are used during builds and deployments.
- Lock Dependency Versions: Lock dependency versions to ensure consistent builds across different environments. This prevents unexpected behavior caused by updates to dependencies. Use lock files (e.g., `package-lock.json`, `pom.xml.lock`, `requirements.txt`) to record the exact versions of dependencies.
- Regularly Update Dependencies: Regularly update dependencies to benefit from bug fixes, security patches, and new features. Automate dependency updates using tools like Dependabot.
- Scan for Vulnerabilities: Scan dependencies for security vulnerabilities using tools like Snyk, OWASP Dependency-Check, or npm audit. Address any vulnerabilities promptly.
- Isolate Dependencies: Use virtual environments or containers (e.g., Docker) to isolate dependencies and prevent conflicts between projects. This ensures that each project has its own set of dependencies, without affecting other projects.
- Cache Dependencies: Cache dependencies to speed up build times. This avoids the need to download dependencies repeatedly. Many CI/CD tools provide built-in caching mechanisms.
- Test Dependencies: Test the application thoroughly after updating dependencies to ensure that the changes have not introduced any regressions. This includes unit tests, integration tests, and end-to-end tests.
- Document Dependencies: Document all dependencies and their versions in the project’s documentation. This helps in understanding the project’s dependencies and makes it easier for new team members to get started.
- Monitor Dependency Health: Monitor the health of dependencies and their updates, looking for signs of deprecation or potential conflicts. This can be integrated into your monitoring and alerting system.
Detailing the Importance of Feedback Loops and Continuous Improvement in CI/CD
Continuous integration and continuous delivery are iterative processes that thrive on feedback and continuous improvement. Establishing effective feedback loops is crucial for identifying and addressing issues promptly.
Feedback loops are mechanisms that provide insights into the performance of the CI/CD pipeline and the software being delivered. Continuous improvement involves making data-driven decisions to enhance the pipeline’s efficiency, reliability, and effectiveness.
- Implement Monitoring and Logging: Implement comprehensive monitoring and logging to track the performance of the CI/CD pipeline and the deployed applications. Collect metrics on build times, test results, deployment success rates, and application performance.
- Collect Feedback from Stakeholders: Gather feedback from developers, testers, operations teams, and end-users. Use surveys, interviews, and user feedback channels to understand their experiences and identify areas for improvement.
- Analyze Test Results: Analyze test results to identify code quality issues, performance bottlenecks, and areas for improvement in testing strategies. Pay close attention to failing tests and investigate the root causes.
- Review Deployment Performance: Review deployment performance metrics, such as deployment frequency, lead time, and change failure rate. Identify and address any deployment issues or inefficiencies.
- Use Automated Alerts: Set up automated alerts to notify the team of failures, performance degradation, or security vulnerabilities. Ensure that alerts are actionable and provide enough context to diagnose and resolve issues quickly.
- Conduct Post-Mortem Analysis: Conduct post-mortem analysis after significant incidents, such as production outages or major deployment failures. Identify the root causes, document lessons learned, and implement corrective actions.
- Regularly Review and Refine the Pipeline: Regularly review the CI/CD pipeline to identify areas for improvement. Refine the pipeline based on feedback, performance data, and evolving project requirements. This includes updating the tools, processes, and configurations.
- Automate Feedback Mechanisms: Automate feedback mechanisms, such as sending automated reports on build status, test results, and deployment performance. This provides timely and actionable information to the team.
- Foster a Culture of Continuous Improvement: Foster a culture of continuous improvement within the team. Encourage experimentation, learning, and sharing of best practices. Promote a blameless culture where failures are viewed as opportunities for learning and growth.
- Use Data-Driven Decision-Making: Use data to drive decisions about pipeline improvements. Base decisions on metrics, feedback, and analysis rather than assumptions or guesswork.
Last Point
In conclusion, the CI/CD pipeline represents a paradigm shift in software development, offering a pathway to accelerated delivery, improved quality, and enhanced collaboration. By embracing automation, continuous testing, and strategic deployment practices, organizations can significantly reduce time-to-market, minimize errors, and adapt swiftly to evolving market demands. The journey towards implementing a successful CI/CD pipeline is a continuous process of learning and improvement, ultimately leading to a more agile, efficient, and innovative development environment.
Popular Questions
What is the main difference between Continuous Delivery and Continuous Deployment?
Continuous Delivery ensures code changes are always ready for release and can be deployed at any time, while Continuous Deployment automates the release process, deploying changes directly to production after passing all tests.
What are the benefits of using a CI/CD pipeline?
CI/CD pipelines offer faster release cycles, reduced risk of errors, improved software quality, enhanced team collaboration, and increased efficiency in the software development lifecycle.
Which tools are commonly used for CI/CD?
Popular CI tools include Jenkins, GitLab CI, and CircleCI, while CD tools encompass Ansible, Kubernetes, and Docker. Version control systems like Git are also essential.
How does a CI/CD pipeline improve software quality?
CI/CD incorporates automated testing at various stages, including unit, integration, and end-to-end tests, which helps identify and fix bugs early in the development process, leading to higher-quality software.