Event-driven architecture (EDA) is revolutionizing how applications communicate and react to events. Webhooks play a crucial role in this paradigm, enabling seamless asynchronous communication between different systems. This guide provides a comprehensive understanding of how to effectively utilize webhooks within an EDA framework, from fundamental concepts to advanced implementation strategies and security best practices. We will delve into various use cases, troubleshooting common issues, and exploring the potential for scalability.
This document will walk you through the entire process of leveraging webhooks for your event-driven applications. From the initial design and implementation to the critical aspects of data handling, security, and scalability, we will address every step in detail. We will provide practical examples and actionable insights to empower you to successfully integrate webhooks into your EDA systems.
Introduction to Event-Driven Architecture
Event-driven architecture (EDA) is a software design pattern where systems respond to events rather than relying on traditional request-response interactions. This approach fosters flexibility, scalability, and resilience, enabling applications to react dynamically to various stimuli and data changes. This paradigm shift is particularly beneficial in modern, complex applications, allowing for asynchronous communication and decoupling of components.Event-driven architecture (EDA) is characterized by its asynchronous communication and loose coupling between components.
This approach promotes scalability and fault tolerance, making systems more resilient to failures and easier to maintain. Crucially, EDA relies on events as the primary mechanism for communication, enabling dynamic responses to data changes and external stimuli.
Key Characteristics of EDA
EDA systems are built around events, which represent significant occurrences or data changes. These events are not directly tied to specific requests but rather trigger responses and actions across the system. This asynchronous communication fosters a decoupled architecture, enabling independent components to operate without direct knowledge of each other’s internal workings. This approach increases the flexibility and scalability of the system.
- Asynchronous Communication: Components communicate through event propagation, not through direct requests. This eliminates the need for immediate responses, allowing components to operate independently and at different speeds.
- Loose Coupling: Components are not tightly connected; they interact only through events. Changes in one component do not necessarily impact others, promoting system stability and modularity.
- Scalability and Flexibility: The decoupled nature of EDA allows for easier scaling of individual components. New components can be added or existing ones modified without disrupting the overall system. This adaptability is crucial in dynamic environments.
- Resilience and Fault Tolerance: Since components don’t depend on each other’s immediate availability, failures in one component don’t necessarily bring down the entire system. This is vital in distributed systems.
The Role of Events in EDA
Events are the fundamental building blocks of EDA. They represent significant occurrences or data changes within or outside the system. Events trigger responses and actions in various components, enabling dynamic and adaptable behavior. Events facilitate the communication between independent components.
- Data Representation: Events encapsulate data representing changes or occurrences.
- Triggering Actions: Events act as signals to trigger actions in different parts of the system.
- Decoupling Mechanism: Events decouple components by enabling communication without direct knowledge of each other.
- Asynchronous Communication: Events facilitate asynchronous communication between components, which increases the system’s scalability and resilience.
How Webhooks Fit into EDA
Webhooks are a mechanism for delivering events to external systems. They provide a way for one application to send notifications to another application when specific events occur. This integration enables EDA systems to interact with external services or applications without the need for continuous polling. In an EDA environment, webhooks act as a bridge between systems.
Relationship Between Events and Webhooks
Webhooks are a practical implementation of event delivery in EDA. They facilitate the asynchronous communication of events between different systems. A webhook essentially represents an event listener, allowing a specific application to be notified of a relevant event. This communication is triggered by the event itself, making the interaction highly responsive. This mechanism enhances the overall efficiency and adaptability of the event-driven system.
- Event Trigger: An event occurs within a system, triggering the need to notify another application.
- Webhook as Listener: The webhook acts as a listener for specific events, waiting to receive a notification.
- Notification Delivery: When the event occurs, the system sends a notification through the webhook to the external application.
- External System Action: The external application, notified by the webhook, performs the appropriate action based on the event data.
Understanding Webhooks
Webhooks represent a powerful mechanism in event-driven architectures, enabling applications to react dynamically to specific events occurring in other systems. They automate communication between different software components, removing the need for continuous polling and significantly improving efficiency. This approach fosters a more responsive and streamlined workflow, crucial for modern applications.Webhooks are essentially a way for applications to receive real-time notifications of events happening in other applications.
This method differs significantly from traditional request-response models, offering a more reactive and efficient approach to communication. Instead of an application actively querying another for updates, the target application proactively sends a notification when something significant happens.
Fundamental Concept
Webhooks act as a notification service, allowing applications to subscribe to specific events. When an event of interest occurs within a source application, the source application automatically sends a notification to the subscribed application using a predefined HTTP endpoint. This approach dramatically reduces the need for constant polling, enhancing responsiveness and reducing server load.
Technical Aspects
Webhooks utilize HTTP POST requests to deliver data. The data transmitted typically includes details about the event that triggered the notification. A critical aspect is the use of a predefined URL, known as a webhook endpoint, where the notification is delivered. This URL is registered by the application wishing to receive notifications. This endpoint acts as a crucial communication channel.
Crucially, the structure of the data payload is standardized, ensuring that the receiving application can interpret the notification accurately.
How Webhooks Work
The process involves a three-part interaction:
- Subscription: The receiving application registers a webhook endpoint with the source application. This endpoint is a unique URL that the source application will use to deliver notifications.
- Event Trigger: When a specific event occurs within the source application, the source application sends an HTTP POST request to the registered webhook endpoint.
- Notification Delivery: The receiving application processes the data received in the POST request, handling the event accordingly. This often involves updating internal data or triggering further actions based on the event details.
Types of Webhooks
While the fundamental mechanism is HTTP POST, webhooks can leverage various HTTP methods for specific functionalities.
- HTTP POST: The most common method, used to transmit data about the event that occurred.
- HTTP GET: Less common, typically used for retrieving information about the event, although the data is not updated in real-time, unlike the POST method.
- Other HTTP Methods: Specific applications may employ other HTTP methods (e.g., PUT, DELETE) for more complex event-handling scenarios, but POST is overwhelmingly the prevalent method in most applications.
Security Considerations
Security is paramount when implementing webhooks. Unauthorized access to endpoints can lead to significant vulnerabilities. To mitigate risks, implementing robust security measures is essential.
- Authentication: Implementing authentication mechanisms (e.g., API keys, tokens) is crucial to verify the sender’s identity. This helps prevent malicious actors from sending unauthorized notifications.
- HTTPS: Using HTTPS to encrypt communication is essential to protect sensitive data exchanged between applications.
- Data Validation: Verifying the integrity of the data received from the source application is vital. This helps ensure the data is accurate and not tampered with.
- Rate Limiting: Implementing rate limiting can help protect against denial-of-service attacks by controlling the frequency of requests.
Using Webhooks to Send Data
Webhooks are used to send data by sending HTTP POST requests to a predefined URL (the webhook endpoint). The data in the request body describes the event that triggered the notification. For instance, a commerce platform might send a webhook to a payment gateway when a purchase is made, including details like the transaction ID and amount. This automated process allows for rapid updates and responsiveness in various applications.
Webhooks in EDA
Webhooks represent a crucial mechanism for enabling communication between applications in an event-driven architecture (EDA). They facilitate asynchronous data exchange, allowing applications to react to events without the need for constant polling. This dynamic approach dramatically improves efficiency and scalability in EDA systems.The key benefit of webhooks in EDA lies in their ability to streamline the flow of information.
Instead of applications continuously checking for updates, webhooks push relevant data to interested parties as events occur. This significantly reduces resource consumption and improves the overall responsiveness of the system.
How Webhooks Enable Communication in EDA
Webhooks act as a bridge between applications, enabling asynchronous communication. When an event of interest occurs within one application, the system sends a notification (the webhook) to another application subscribed to that event type. This notification contains information about the event, allowing the receiving application to respond appropriately. This mechanism eliminates the need for the receiving application to continuously query the sending application for updates.
It ensures efficiency and reduces unnecessary processing load.
Use Cases of Webhooks in EDA
Webhooks are versatile tools with a wide range of applications in event-driven architectures. They are particularly useful in scenarios where real-time updates are required, such as:
- Order Processing: When an order is placed in an e-commerce system, a webhook can be triggered to update inventory levels in the warehouse management system, or to notify a payment gateway about the transaction. This allows for immediate updates and ensures that downstream systems are aware of changes in real-time.
- Content Management: In a blog or news platform, a webhook can notify subscribers about new posts or articles. This ensures that readers receive updates promptly and without manual intervention.
- Social Media Integration: When a user posts on a social media platform, webhooks can be used to automatically update related systems, like a news aggregator or a marketing campaign dashboard.
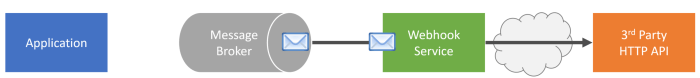
Webhook Functioning in an Event-Driven System
The following diagram illustrates how webhooks function in an event-driven system. A sending application (e.g., an order processing system) generates an event (e.g., a new order). This event triggers a webhook notification, which is delivered to a receiving application (e.g., a warehouse management system) via a secure HTTP POST request. The receiving application processes the notification and updates its internal state accordingly.
The entire process is asynchronous, allowing applications to operate independently without constant polling.[Diagram: A simplified diagram showing a sending application, an event, a webhook notification, and a receiving application. The arrow from the sending application to the receiving application is labeled “Webhook Notification.” The diagram should clearly illustrate the asynchronous nature of the communication.]
Handling Asynchronous Communication
Webhooks excel at handling asynchronous communication. When an event occurs, the sending application immediately sends a webhook notification to the receiving application without waiting for a response. This asynchronous nature is crucial in EDA, allowing applications to operate independently and preventing bottlenecks caused by synchronous communication.
Event Types Handled by Webhooks
Webhooks can handle a wide variety of event types, tailored to the specific needs of the applications involved. Examples include:
- Order Placement: An order is placed in the e-commerce system.
- Payment Confirmation: A payment is successfully processed.
- File Upload: A file is uploaded to a server.
- User Registration: A new user registers on a platform.
These event types can be customized to fit the particular requirements of each application within the EDA. The specific event types are dependent on the applications and the events that are of interest to them.
Implementing Webhooks
Implementing webhooks involves meticulously designing and setting up the necessary infrastructure to receive and process incoming notifications from various sources. This process is crucial for ensuring seamless communication and data flow within an event-driven architecture. A well-implemented webhook setup guarantees that applications are alerted to relevant events, enabling timely responses and actions.
Designing a Simple Webhook Setup
A fundamental webhook setup typically involves two key components: a webhook endpoint and a notification payload. The endpoint is a URL that receives the notification, and the payload contains the data associated with the event. A simplified example might involve a user registration service notifying a marketing automation platform about new user sign-ups. The registration service sends a notification (payload) to the marketing platform’s webhook endpoint when a user signs up.
Creating a Webhook Endpoint
This process varies depending on the chosen programming language and web server environment. A common approach involves setting up a web server (e.g., Node.js, Python’s Flask or Django, or a dedicated service like AWS API Gateway) that listens for incoming HTTP requests at a specified URL. This URL serves as the webhook endpoint. The server then processes the request, extracts the data from the payload, and performs the necessary actions based on the event.
Programming Languages for Webhook Implementation
Numerous programming languages are suitable for implementing webhook endpoints. Popular choices include:
- Python: Frameworks like Flask and Django provide robust tools for creating web applications and handling HTTP requests, making Python an excellent choice for webhook development.
- Node.js: With its asynchronous nature and extensive ecosystem, Node.js excels in handling high volumes of webhook requests efficiently.
- Java: Java’s strength lies in its robust frameworks, allowing for scalable and reliable webhook implementations. Spring Boot is a popular framework for this purpose.
- PHP: PHP is widely used for web development, and frameworks like Laravel offer features for handling webhooks.
- Ruby on Rails: Ruby on Rails is another option for web development, and its structure makes webhook implementation relatively straightforward.
Each language possesses unique advantages and considerations for webhook development. The selection depends on factors such as existing infrastructure, developer expertise, and anticipated traffic volume.
Receiving Webhook Data
The process of receiving and handling webhook data is fundamentally about receiving and parsing the HTTP request. This involves handling various HTTP request headers (e.g., Content-Type) and the request body, which contains the payload. The payload itself can be in various formats, such as JSON or XML. The server must extract the relevant data from the payload and perform the necessary actions.“`// Example (Python with Flask)from flask import Flask, requestapp = Flask(__name__)@app.route(‘/webhook’, methods=[‘POST’])def webhook(): if request.method == ‘POST’: try: data = request.get_json() # Process the data from the webhook payload print(data) return ‘Webhook received successfully’ except: return ‘Invalid payload format’, 400 else: return ‘Invalid request method’, 405if __name__ == ‘__main__’: app.run(debug=True)“`This example demonstrates a basic Python Flask webhook endpoint that receives a JSON payload.
The code handles potential errors like invalid payloads and uses the appropriate HTTP status codes for feedback.
Testing a Webhook Implementation
Thorough testing is essential to ensure a webhook implementation functions as expected. A common approach involves using tools like Postman or curl to simulate webhook events. The test involves sending a sample payload to the webhook endpoint and verifying that the expected actions are performed. Monitoring the system’s responses and log files can help identify any issues.
Furthermore, simulating various scenarios, such as different data formats or error conditions, can enhance the reliability and robustness of the implementation.
Handling Webhook Data
Webhooks, as a crucial component of event-driven architectures, facilitate the seamless exchange of data between applications. Effectively handling this data is critical for reliable communication and prevents errors or delays. This section delves into various aspects of managing webhook data, including formats, error handling, validation, and the role of message queues.Data integrity and reliability are paramount in webhook communication.
Proper handling ensures applications can efficiently process information, trigger appropriate actions, and maintain data consistency.
Data Formats
Webhooks primarily utilize JSON for data transmission. JSON’s structured nature allows for easy parsing and interpretation by receiving applications. However, other formats like XML are also possible, though JSON is significantly more prevalent due to its simplicity and widespread adoption. The choice of format should align with the application’s needs and existing infrastructure.
Error Handling Mechanisms
Robust error handling is vital for maintaining application stability and resilience. Common error handling mechanisms include returning HTTP status codes (e.g., 400 Bad Request, 500 Internal Server Error) to indicate the nature of the problem. Detailed error messages in the response body provide more context for troubleshooting. Error logging, both on the sender and receiver side, is also critical for monitoring and analysis.
Payload Validation
Validating webhook payloads is crucial for preventing malicious or incorrect data from entering the system. This involves verifying the data structure, checking for expected fields, and ensuring data types match the application’s schema. For instance, a webhook might send a user ID. The application needs to verify if the ID is a number and if it corresponds to an actual user in the database.
This validation helps maintain data integrity and prevent unexpected behavior.
Message Queues in Webhook Traffic
Message queues play a critical role in handling webhook traffic. They act as buffers, decoupling the sender and receiver, allowing for asynchronous communication and preventing the sender from being blocked by slow or unresponsive receivers. Message queues also enable scaling and load balancing, ensuring responsiveness under high traffic conditions. A queue can also provide important features such as message persistence and retries for failed deliveries.
Webhook Response Structure Example
A successful webhook response often includes a status code (e.g., 200 OK) and a response body. The response body may contain a confirmation message, data related to the event that triggered the webhook, or an error message if the processing failed. A typical example would be:“`HTTP/1.1 200 OKContent-Type: application/json “status”: “success”, “message”: “Webhook processed successfully”, “event_data”: “order_id”: “12345”, “user_id”: “ABC123”, “amount”: 100.00 “`This example demonstrates a successful response, indicating successful processing of the webhook and providing pertinent details about the event.
Security Best Practices for Webhooks
Webhooks, while enabling efficient event-driven architectures, introduce security vulnerabilities if not implemented correctly. Proper security measures are crucial to protect sensitive data and maintain the integrity of the system. This section Artikels key security best practices for securing webhook implementations.Effective webhook security hinges on understanding potential threats and implementing robust countermeasures. This involves careful consideration of authentication, authorization, data validation, and endpoint security.
Failing to address these aspects can expose systems to attacks, compromise data integrity, and lead to serious consequences.
Common Webhook Security Vulnerabilities
Various security vulnerabilities can arise from poorly secured webhooks. These include issues like insecure authentication, lack of data validation, and exposed endpoints. Understanding these vulnerabilities is paramount to implementing robust security measures.
- Insecure Authentication: Failing to implement proper authentication mechanisms allows unauthorized access to webhook endpoints, leading to data breaches and manipulation of events.
- Insufficient Data Validation: Lack of validation of incoming webhook data exposes systems to malicious payloads. This can lead to injection attacks, unauthorized actions, or system crashes.
- Exposed Endpoints: Publicly accessible webhook endpoints without proper security measures are vulnerable to attacks. These attacks can exploit the endpoint for malicious purposes, causing system disruption or data breaches.
- Tampered Webhook Data: If webhook data is not validated or signed, malicious actors can alter it, leading to incorrect actions or unintended consequences in the receiving system.
Security Protocols for Protecting Webhooks
Several security protocols can be employed to mitigate webhook vulnerabilities. These include HTTPS, message signing, and secure authentication methods.
- HTTPS: Employing HTTPS for all webhook communication is fundamental. It encrypts the communication channel, preventing eavesdropping and man-in-the-middle attacks. This ensures the confidentiality and integrity of the data transmitted between the sender and receiver.
- Message Signing: Implementing message signing, using cryptographic signatures, verifies the authenticity and integrity of webhook payloads. This ensures that the data hasn’t been tampered with during transit.
Implementing Secure Authentication Mechanisms
Secure authentication mechanisms are critical for controlling access to webhook endpoints. These mechanisms ensure that only authorized applications can interact with the webhook.
- API Keys: Using API keys provides a simple yet effective way to authenticate webhook requests. These keys can be tied to specific applications, enabling granular access control.
- OAuth 2.0: OAuth 2.0 is a widely adopted standard for authorization. It allows applications to access protected resources without needing to store sensitive credentials.
- JWT (JSON Web Tokens): JWTs are compact, self-contained security tokens that can be used to securely transmit information between parties. They provide authentication and authorization claims, allowing for secure and efficient communication.
Securing Webhook Endpoints
Protecting webhook endpoints involves securing the server receiving the webhook requests.
- Rate Limiting: Implementing rate limiting prevents abuse by malicious actors. This involves limiting the number of requests per unit of time, preventing a denial-of-service attack. This approach safeguards the receiving server from overload and potential exploitation.
- Input Validation: Validating incoming webhook data is essential to prevent injection attacks and ensure data integrity. Validating input helps prevent malicious payloads from disrupting the system.
- Error Handling: Robust error handling is crucial for managing unexpected situations and preventing vulnerabilities. Proper error handling helps in identifying and resolving issues promptly, maintaining system stability.
Validating Incoming Webhook Data
Validating incoming webhook data is critical to prevent malicious payloads from compromising the system. This validation process should include checks for expected data types, formats, and potentially, digital signatures.
- Data Type Validation: Verify that incoming data conforms to the expected data types, such as integers, strings, or dates. This validation prevents unexpected behavior and malicious payloads.
- Format Validation: Validate the format of incoming data to ensure it adheres to the defined schema or structure. This prevents inconsistencies and ensures data reliability.
- Signature Verification: Use cryptographic signatures to verify the authenticity and integrity of incoming webhook data. This step helps in preventing unauthorized modifications or tampering of the data.
Webhooks and Scalability
Webhooks, crucial components of event-driven architectures, are vital for enabling applications to react to events in real-time. Their effectiveness, however, hinges on their ability to handle increasing volumes of requests without compromising performance. This section explores strategies for scaling webhook implementations to ensure reliable and responsive systems.
Strategies for Handling High Volumes of Webhook Requests
Efficiently handling high volumes of webhook requests is paramount for maintaining system responsiveness and reliability. A crucial aspect of this involves understanding the inherent characteristics of webhook traffic. These requests, often triggered by significant events, can exhibit unpredictable spikes in demand. Therefore, proactive measures are necessary to absorb these fluctuations without compromising service quality.
- Load Balancing: Distributing webhook requests across multiple servers can significantly improve scalability. This ensures that no single server becomes overwhelmed during peak demand. Load balancers can intelligently route requests based on factors like server load and availability, optimizing resource utilization.
- Caching: Caching frequently accessed webhook data can dramatically reduce the number of requests that need to be processed. Caching strategies, such as Redis or Memcached, can store commonly requested data, returning it quickly to subsequent requests, thus minimizing database load.
- Asynchronous Processing: Instead of processing webhook requests synchronously, asynchronous processing can improve overall system responsiveness. By decoupling the webhook handling process from the main application flow, the system can continue to function even if a particular webhook request takes longer than anticipated. Message queues, such as RabbitMQ or Kafka, are commonly used for asynchronous processing.
Comparing and Contrasting Scaling Approaches
Several approaches exist for scaling webhook implementations, each with its own set of strengths and weaknesses. The optimal strategy often depends on specific application requirements and the nature of webhook traffic.
| Approach | Description | Advantages | Disadvantages |
|---|---|---|---|
| Load Balancing | Distributes incoming webhook requests across multiple servers. | Improved performance during peak demand, reduced server load, enhanced availability. | Requires additional infrastructure, potentially increased complexity in routing and management. |
| Caching | Stores frequently accessed webhook data for rapid retrieval. | Reduced database load, improved response times for repeated requests, reduced latency. | Requires careful consideration of cache invalidation strategies, potential for stale data if not managed properly. |
| Asynchronous Processing | Processes webhook requests in a non-blocking manner. | Improved system responsiveness, ability to handle large volumes of requests without affecting overall application performance. | Requires message queuing infrastructure, introduces complexity in message handling and error handling. |
Optimizing Webhook Performance
Optimizing webhook performance involves various strategies to minimize latency and ensure efficient processing. Efficient data serialization and deserialization can significantly impact the speed of handling webhook requests. Employing appropriate data structures and utilizing efficient programming techniques can lead to noticeable performance gains.
- Efficient Data Serialization/Deserialization: Utilizing lightweight and performant serialization formats, such as JSON, reduces processing overhead. Efficiently parsing and converting data between formats is critical for optimizing webhook handling.
- Minimizing Database Interactions: Reducing the number of database queries required to process webhook data can significantly improve performance. Employing appropriate database indexing and optimizing queries can minimize delays.
- Appropriate API Design: Designing APIs with efficient endpoints and request structures directly impacts webhook performance. Efficient routing, input validation, and appropriate response formats contribute to improved performance.
Webhook Deployment Checklist (Scalability Focused)
A comprehensive checklist for webhook deployment should prioritize scalability considerations. Thorough planning and consideration of potential scaling challenges are critical for future success.
- Capacity Planning: Anticipate future growth and potential spikes in webhook traffic to ensure adequate infrastructure.
- Load Testing: Conduct rigorous load testing to identify performance bottlenecks and evaluate system scalability under stress.
- Monitoring and Logging: Implement comprehensive monitoring and logging to track webhook request performance and identify potential issues proactively.
- Scalable Infrastructure: Select infrastructure that can adapt to increasing webhook traffic demands without significant performance degradation.
- Automated Scaling: Consider automated scaling solutions that can dynamically adjust resources based on real-time demand.
Common Use Cases of Webhooks in EDA
Webhooks provide a powerful mechanism for enabling real-time communication and event-driven workflows in event-driven architectures (EDA). They act as a crucial bridge between systems, allowing applications to react instantly to events occurring in other systems, fostering dynamic and responsive applications. This real-time interaction streamlines processes and enhances overall application efficiency.
Common Applications of Webhooks in EDA
Webhooks are not limited to a single domain; their utility extends across various applications within event-driven architectures. Their adaptability stems from their ability to react to diverse events, making them valuable for many use cases. The table below illustrates some common applications and their corresponding actions.table| Use Case | Description | Example | Implementation Notes ||—|—|—|—|| Order Processing | Triggering actions based on order events | New order placed, order shipped, order cancelled | Use JSON payload to send order details, including order ID, customer information, and shipping address.
This allows for immediate updates to inventory, payment systems, and shipping labels. || Payment Processing | Handling payment events | Payment successful, payment failed | Implement secure payment handling protocols. Ensure data integrity and confidentiality during payment processing using appropriate encryption and authentication methods. This includes verifying the webhook signature to prevent malicious tampering. || User Activity | Tracking user actions in real time | User login, profile update, purchase | Provide user context and activity details, such as the user ID, the specific action performed, and the timestamp.
This enables real-time analytics and personalized experiences. For example, updating user profiles or sending personalized notifications. || Inventory Management | Tracking inventory changes | Inventory low, inventory restocked | Implement real-time inventory updates. This allows for automated replenishment orders or alerts when stock falls below a threshold, maintaining optimal inventory levels. For example, triggering an order for more inventory when a particular item falls below a specified quantity.
|| Real-time Data Updates | Updating dashboards and applications | Data changes, data updates | Design for high-frequency data updates, allowing for immediate visualization and analysis of changing data. This enables dashboards to reflect real-time status, critical for applications requiring immediate feedback. |/tableThese examples demonstrate the versatility of webhooks in event-driven architectures. The key is to design webhooks with specific use cases in mind, ensuring a secure and efficient communication channel.
Troubleshooting Webhooks
Troubleshooting webhook integrations is crucial for maintaining the reliability and efficiency of event-driven architectures. Effective troubleshooting involves identifying the root cause of issues, which can range from simple configuration errors to complex network problems. Understanding the common causes and implementing appropriate diagnostic techniques are vital for resolving these problems swiftly and minimizing downtime.Properly configured webhooks are essential for successful event-driven communication.
If the webhook integration fails to function as expected, this can disrupt the flow of events and lead to data inconsistencies or missed actions. Troubleshooting these failures requires systematic investigation and a clear understanding of the communication channels involved.
Common Webhook Issues and Their Causes
A variety of issues can arise in webhook integrations. These problems can stem from errors in configuration, communication failures, or problems within the systems involved. Understanding the potential causes helps to identify and resolve issues efficiently.
- Incorrect Configuration: Incorrect webhook URLs, headers, or authentication credentials are frequent causes of failures. Mismatched settings between the event source and the receiving application can lead to the webhook request being rejected or ignored. For instance, a typo in the webhook URL, an incorrect authentication token, or an improperly formatted header will prevent the webhook from being processed correctly.
- Network Connectivity Problems: Network issues, such as firewalls blocking communication or temporary network outages, can disrupt webhook delivery. In such cases, the event source may successfully send the webhook request, but the receiving application might not receive it due to network problems. Timeouts or connection failures can also be indicators of network connectivity problems. For example, a firewall blocking port 443 can prevent webhook requests from reaching the intended destination.
- Application Errors: Errors in the receiving application, such as incorrect handling of the webhook payload or exceeding server capacity, can prevent the webhook from being processed successfully. The application may be unable to handle the incoming data due to limitations in its processing capabilities or internal errors. For example, a database failure within the application could cause a backlog or errors in processing the webhook.
- Authentication Issues: Authentication failures, such as invalid or missing authentication tokens, will lead to requests being rejected. Incorrect or expired authentication keys prevent the webhook from being validated, causing the integration to fail. This can arise from incorrect credentials or issues with the authentication mechanism.
Diagnosing and Resolving Webhook Problems
Effective diagnosis and resolution of webhook problems depend on a methodical approach. This involves checking configurations, examining logs, and testing communication.
- Verify Configuration Settings: Carefully review the webhook configuration on both the event source and the receiving application to ensure that all settings match and are correct. Double-checking the URLs, headers, and authentication credentials is crucial to identify any configuration errors.
- Inspect Logs: Examine the logs of both the event source and the receiving application to pinpoint errors. Log files provide valuable insights into the status of requests and responses, indicating where the communication breakdown might be occurring. For instance, error messages in the application’s logs can point to issues with the webhook data handling.
- Test Communication Channels: Test the communication channels involved in the webhook integration to confirm that the requests are being sent and received correctly. Use tools to test the network connectivity between the event source and the receiving application, ensuring that the data is being transmitted and received without problems. This helps identify if there’s a network blockage or if the request is being dropped along the way.
Troubleshooting Techniques for Webhook Communication Failures
Troubleshooting webhook communication failures often involves systematic checks and verifications.
- Check Network Connectivity: Verify that the network connection between the event source and the receiving application is stable and functional. Using network diagnostic tools can help identify potential network problems or bottlenecks.
- Inspect Webhook Request and Response: Carefully examine the webhook request and response to identify any errors or discrepancies. Pay attention to the HTTP status codes, headers, and payload to pinpoint the source of the issue.
- Simulate Webhook Requests: Simulate webhook requests to test the functionality of the integration under various conditions. Using tools to simulate webhook requests helps to isolate and reproduce the problem.
Potential Causes of Webhook Errors
Several factors can contribute to webhook errors, necessitating a comprehensive troubleshooting approach.
- Rate Limiting: Exceeding the rate limit imposed by the event source or the receiving application can cause errors. The frequency of webhook requests should be managed to avoid exceeding these limits.
- Data Format Issues: Incorrect or unexpected data formats in the webhook payload can lead to errors in processing. Ensure that the data format adheres to the specifications defined for the integration.
- Server Overload: Overloading the server receiving the webhook requests can result in errors. Implement appropriate scaling and error handling mechanisms to mitigate server overload.
Comprehensive Guide for Troubleshooting Webhook Integrations
A comprehensive guide for troubleshooting webhook integrations involves a structured approach, incorporating multiple techniques for effective diagnosis and resolution.
- Document the Integration: Thoroughly document the webhook integration process, including configuration details, communication protocols, and error handling mechanisms. This documentation aids in quickly identifying and addressing issues.
- Isolate the Problem: Identify the specific component causing the problem. Start by checking the simplest aspects of the integration, like configuration, and gradually move to more complex areas if necessary.
- Test and Retest: After implementing a solution, retest the webhook integration thoroughly to ensure that the issue is resolved and the integration functions correctly.
Advanced Webhook Topics
Webhooks, while a powerful tool for event-driven architectures, can become more complex as application needs evolve. This section delves into advanced concepts and strategies for leveraging webhooks effectively in sophisticated scenarios. From robust retry mechanisms to sophisticated delivery confirmations, we’ll explore techniques to ensure reliable and scalable communication between systems.Implementing webhooks in complex environments necessitates a nuanced understanding of different delivery strategies and the role of message queues.
Understanding these advanced topics will equip developers with the skills to design and maintain resilient webhook integrations that can handle high volumes of events and critical business logic.
Retry Mechanisms
Reliable communication between systems is crucial. Webhook delivery failures can occur due to transient network issues, service outages, or temporary application errors. Implementing robust retry mechanisms is essential for maintaining the integrity of event delivery. A retry mechanism attempts delivery again after a predetermined delay if the initial attempt fails. The retry strategy should incorporate exponential backoff, gradually increasing the delay between attempts.
- Exponential Backoff: This strategy increases the delay between retry attempts exponentially. This approach prevents overwhelming the receiving service with requests, allowing for system recovery and preventing overload. For instance, a first retry might occur after 1 second, followed by 2 seconds, 4 seconds, and so on.
- Retry Limits: Defining a maximum number of retry attempts is crucial. This prevents indefinite retries that could consume resources or lead to system instability. A practical example would be limiting retries to five attempts before marking the event as failed and potentially routing it to a dedicated error handling queue.
- Error Handling: A retry mechanism should also include comprehensive error handling. Different error types (e.g., network timeout, server errors) should trigger specific actions, such as logging the error or escalating it to an administrator. This aids in understanding and resolving persistent issues.
Webhook Delivery Confirmation
Ensuring that the receiving application successfully processed the webhook payload is critical for accurate event tracking. Webhook delivery confirmation mechanisms provide a way for the sending application to know that the webhook was received and processed. This often involves using HTTP response codes and/or confirmation URLs.
- HTTP Response Codes: The receiving application should respond with a successful HTTP status code (e.g., 200 OK) upon successful processing. This informs the sending application that the event was received and acted upon.
- Confirmation URLs: The sending application can include a confirmation URL in the webhook request. The receiving application can post a confirmation to this URL upon successful processing, providing a clear signal of successful delivery. This is particularly useful in scenarios requiring acknowledgment.
Webhook Delivery Strategies
Various strategies for webhook delivery cater to different application needs. Understanding these strategies is vital for optimal webhook setup.
- Polling: The receiving application periodically queries the sending application for new events. This is suitable for low-volume scenarios where latency isn’t a major concern. Polling, however, can create overhead and isn’t ideal for high-volume event streams.
- Push: The sending application actively pushes events to the receiving application using webhooks. This is more efficient for high-volume events and provides real-time updates. This is the preferred method for most modern event-driven architectures.
- Batching: Events are grouped and sent in batches to reduce overhead, particularly useful in high-volume scenarios. The receiving application needs to handle these batches appropriately.
Message Queues in Advanced Webhook Setups
In complex scenarios, message queues play a vital role in handling webhook events. They act as a buffer, ensuring that events are delivered even if the receiving application is unavailable.
- Decoupling: Message queues decouple the sending and receiving applications. This improves resilience and allows the receiving application to process events asynchronously.
- Scalability: Queues enable scaling by allowing the receiving application to handle events at its own pace. This ensures responsiveness and stability, especially during periods of high event volume.
- Error Handling: Queues enable the implementation of retry mechanisms and dead-letter queues, which are crucial for handling failed deliveries and ensuring no events are lost.
Complex Use Cases
- Real-time order updates: A webhook can notify various systems (payment processors, inventory management, shipping providers) about order updates in real-time.
- Multi-step processes: A webhook can trigger further actions based on specific events, facilitating complex workflows. This is commonly seen in e-commerce or supply chain management.
- Automated reporting: Webhooks can trigger reports or alerts based on events, providing valuable insights and driving proactive responses. This is useful in monitoring and analytics systems.
Final Thoughts
In conclusion, mastering webhooks within an event-driven architecture empowers applications to react dynamically to events, enabling seamless communication and enhanced scalability. By understanding the fundamental principles, implementation strategies, and security considerations Artikeld in this guide, you can effectively leverage webhooks to build robust and efficient applications. This comprehensive approach equips you with the knowledge needed to navigate the complexities of webhook integration, fostering efficient and scalable event-driven systems.
Essential FAQs
What are the common data formats used for webhooks?
Webhooks commonly utilize JSON (JavaScript Object Notation) for data transmission. Other formats, such as XML, are also possible but less prevalent.
How do I handle high volumes of webhook requests?
To manage high volumes of webhook requests, consider employing message queues (e.g., RabbitMQ, Kafka) to decouple the sender and receiver. This approach allows for buffering and processing of requests without impacting the performance of your core application.
What are some common security vulnerabilities in webhooks?
Common vulnerabilities include insecure authentication, lack of data validation, and improper handling of sensitive data. Implementing robust authentication mechanisms, validating incoming payloads, and securing webhook endpoints are crucial steps in mitigating these risks.
What are the different types of webhook events?
Webhook events can be triggered by various actions, such as order placement, payment processing, user activity, and inventory changes. The specific event type depends on the application and its integration requirements.


