Navigating the cloud while adhering to the Health Insurance Portability and Accountability Act (HIPAA) can seem daunting. This guide serves as your compass, illuminating the path toward secure and compliant cloud adoption for healthcare organizations. We’ll explore the core principles of HIPAA, delving into the critical aspects of data protection, access controls, and risk management within a cloud environment. From understanding your responsibilities to selecting the right cloud service provider, we’ll equip you with the knowledge needed to confidently embrace the cloud while safeguarding protected health information (PHI).
This detailed exploration will cover essential topics, including data encryption, Business Associate Agreements (BAAs), disaster recovery, and audit trails. We’ll also address the crucial steps of risk assessment, data breach response, and ongoing compliance. By understanding these key areas, you can transform your cloud strategy into a powerful tool for enhancing data security and operational efficiency while meeting your HIPAA obligations.
Understanding HIPAA and Cloud Computing
Adopting cloud computing presents significant opportunities for healthcare organizations, but it also introduces complexities regarding compliance with the Health Insurance Portability and Accountability Act (HIPAA). This section provides a foundational understanding of HIPAA, its core principles, and how they translate into the cloud environment. It also highlights the shifting security responsibilities and the specific HIPAA Security Rule sections most affected by cloud adoption.
Core Principles of HIPAA in a Cloud Environment
HIPAA, enacted in 1996, establishes national standards to protect individuals’ medical records and other protected health information (PHI). These standards are critical, especially in cloud environments, where PHI is stored, processed, and transmitted. The core principles remain constant regardless of where the data resides.The key principles of HIPAA include:
- Privacy Rule: This rule sets national standards for the protection of individually identifiable health information. It regulates the use and disclosure of PHI by covered entities (healthcare providers, health plans, and healthcare clearinghouses) and their business associates. This rule emphasizes patient rights regarding their PHI, including the right to access, amend, and receive an accounting of disclosures. In the cloud, this necessitates robust access controls and audit trails.
- Security Rule: This rule establishes a set of national standards for protecting the confidentiality, integrity, and availability of electronic protected health information (ePHI). It Artikels administrative, physical, and technical safeguards that covered entities and business associates must implement. These safeguards are crucial in the cloud, where ePHI is often stored on shared infrastructure.
- Breach Notification Rule: This rule requires covered entities and business associates to notify individuals, the Department of Health and Human Services (HHS), and, in some cases, the media, of breaches of unsecured PHI. Cloud providers and their clients must collaborate to ensure timely breach detection and notification.
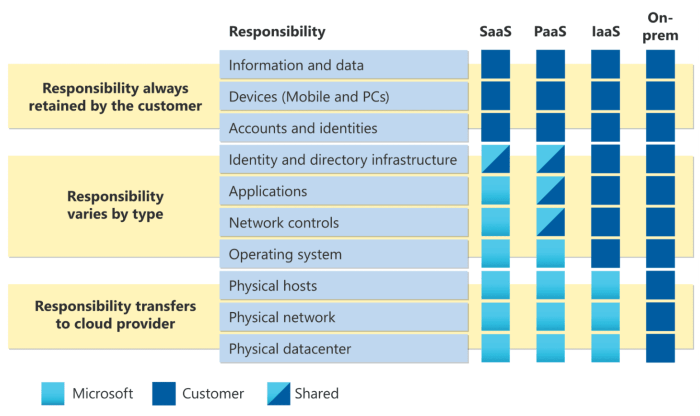
On-Premise vs. Cloud Security Responsibilities Under HIPAA
The responsibility for HIPAA compliance shifts when moving from an on-premise environment to a cloud environment. Understanding these differences is crucial for ensuring adequate protection of PHI.The following table illustrates the division of responsibilities:
| Security Area | On-Premise Responsibility | Cloud Responsibility (Shared Model) |
|---|---|---|
| Data Security | Covered Entity is fully responsible for data security, including encryption, access controls, and data loss prevention. | Shared responsibility. The cloud provider manages the underlying infrastructure security (e.g., physical security, network security), while the covered entity is responsible for securing data within the cloud environment (e.g., data encryption at rest and in transit, access controls, and data loss prevention policies). |
| Physical Security | Covered Entity is responsible for physical security of servers and data centers. | Cloud Provider is responsible for physical security of the data centers where the data resides. The covered entity should ensure the provider has appropriate certifications (e.g., SOC 2, ISO 27001). |
| Access Control | Covered Entity manages access controls to its systems and data. | Shared responsibility. The covered entity manages access controls to its data and applications within the cloud environment. The cloud provider provides the tools and infrastructure for access control. |
| Business Associate Agreements (BAAs) | Covered Entity directly enters into BAAs with all business associates. | The covered entity must ensure that the cloud provider is a business associate and has a signed BAA in place. The BAA Artikels the provider’s responsibilities for protecting PHI. |
| Compliance Auditing | Covered Entity is responsible for conducting its own HIPAA compliance audits. | Shared responsibility. The covered entity is responsible for auditing its own use of the cloud environment. The cloud provider may provide tools and documentation to assist with compliance. |
Cloud providers, such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP), offer services and tools that can help covered entities meet their HIPAA obligations. However, the ultimate responsibility for compliance always rests with the covered entity.
Impacted Sections of the HIPAA Security Rule in Cloud Adoption
Several sections of the HIPAA Security Rule are particularly relevant when adopting cloud services. These sections require careful consideration and implementation of appropriate safeguards.The following sections are significantly impacted:
- Administrative Safeguards: These safeguards involve the policies and procedures a covered entity puts in place to manage the security of ePHI. Cloud adoption requires updates to these safeguards, including:
- Risk Analysis and Management: Regularly assessing risks to the confidentiality, integrity, and availability of ePHI stored in the cloud.
- Security Management Process: Implementing policies and procedures to prevent, detect, contain, and correct security violations.
- Workforce Training and Management: Ensuring that all workforce members receive appropriate training on HIPAA and cloud security best practices.
- Business Associate Agreements: Establishing and maintaining BAAs with cloud providers.
- Technical Safeguards: These are the technological measures used to protect ePHI. Cloud adoption requires the implementation of these safeguards:
- Access Control: Implementing strong authentication and authorization mechanisms to control access to ePHI. This includes multi-factor authentication and role-based access control.
- Encryption: Encrypting ePHI at rest and in transit.
- Audit Controls: Implementing audit trails to track access and modifications to ePHI.
- Integrity Controls: Implementing measures to ensure that ePHI is not improperly altered or destroyed.
- Physical Safeguards: These safeguards address the physical security of the systems and facilities where ePHI is stored. In the cloud, the cloud provider is primarily responsible for these safeguards, but the covered entity must ensure the provider has adequate measures in place:
- Facility Access Controls: Implementing measures to restrict physical access to the data centers.
- Workstation Security: Ensuring that workstations used to access ePHI are secure.
- Media Controls: Implementing procedures for the secure disposal of electronic media.
Adhering to these sections is critical to maintaining HIPAA compliance in the cloud and protecting sensitive patient data.
Data Encryption and Access Controls
To maintain HIPAA compliance in the cloud, robust data encryption and access controls are paramount. These measures safeguard Protected Health Information (PHI) from unauthorized access, use, or disclosure. They are crucial components of a comprehensive security strategy designed to protect patient confidentiality and meet the stringent requirements of the HIPAA Security Rule. This section details the importance of data encryption and access controls, along with best practices for their implementation.
Data Encryption
Data encryption is a fundamental security measure for protecting PHI in the cloud. It involves converting data into an unreadable format, rendering it unintelligible to unauthorized parties. This ensures that even if data is intercepted or accessed without authorization, it remains protected. Encryption is essential both when data is stored (at rest) and when it is being transmitted (in transit).Data encryption encompasses two primary categories:
- Encryption at Rest: This protects data stored on servers, in databases, and in other storage locations. It ensures that even if a storage device is lost or stolen, the data remains unreadable. This is often implemented using technologies like:
- Full-disk encryption, which encrypts the entire hard drive or storage volume.
- Database encryption, which encrypts specific database fields or entire databases.
- Object-level encryption, which encrypts individual data objects.
- Encryption in Transit: This protects data as it is being transmitted over networks, such as the internet. It prevents eavesdropping and ensures that data remains confidential during transfer. Common methods include:
- Transport Layer Security (TLS)/Secure Sockets Layer (SSL) for encrypting web traffic.
- Virtual Private Networks (VPNs) for creating secure connections.
- Secure File Transfer Protocol (SFTP) for secure file transfers.
For example, a healthcare provider using a cloud-based Electronic Health Record (EHR) system must encrypt all PHI stored in the cloud. This includes patient records, medical history, and billing information. The provider must also encrypt all data transmitted between its facilities and the cloud service provider.
Access Controls
Implementing strong access controls is critical for limiting access to PHI to only authorized individuals and systems. This helps to prevent accidental or intentional data breaches. Access controls should be implemented using a layered approach, incorporating various methods to verify and authorize users.Key access control methods include:
- Role-Based Access Control (RBAC): This approach assigns access privileges based on a user’s role or job function within the organization. For instance, a physician might have access to a patient’s medical records, while a billing clerk only has access to billing information. RBAC simplifies access management by allowing administrators to define roles and assign permissions to those roles, rather than managing individual user accounts.
- Multi-Factor Authentication (MFA): MFA requires users to provide multiple forms of verification before granting access. This typically involves something the user knows (e.g., a password), something the user has (e.g., a mobile device), and/or something the user is (e.g., biometric data). MFA significantly reduces the risk of unauthorized access, even if a password is compromised.
- Principle of Least Privilege: This principle dictates that users should only be granted the minimum level of access necessary to perform their job duties. This limits the potential damage caused by a compromised account.
- Regular Auditing and Monitoring: Continuous monitoring of access logs and user activity helps identify and address potential security threats. This includes reviewing who is accessing PHI, when they are accessing it, and what actions they are performing.
A hospital, for example, should implement RBAC to control access to its cloud-based patient portals. Physicians, nurses, and other healthcare professionals should have access to the patient portal based on their specific roles, with access rights tailored to their responsibilities. MFA should be enabled for all users accessing the portal to enhance security.
Encryption Key Management
Secure management of encryption keys is essential for maintaining the confidentiality and integrity of encrypted data. Encryption keys must be protected from unauthorized access, and a well-defined key management process is crucial.A robust key management process should include the following elements:
- Key Generation: Use strong, randomly generated encryption keys. Avoid using weak or easily guessable keys.
- Key Storage: Store encryption keys securely, using hardware security modules (HSMs) or other secure key management systems. Avoid storing keys in the same location as the encrypted data.
- Key Rotation: Regularly rotate encryption keys to minimize the impact of a potential key compromise. Establish a schedule for key rotation based on industry best practices and risk assessments.
- Key Access Control: Implement strict access controls to limit who can access and manage encryption keys. Use RBAC to assign permissions based on job roles.
- Key Backup and Recovery: Establish a process for backing up and recovering encryption keys in case of a system failure or disaster. Ensure that backup keys are stored securely.
- Key Destruction: Securely destroy encryption keys when they are no longer needed. This should include procedures for overwriting or physically destroying the keys.
For instance, a cloud service provider offering HIPAA-compliant services might use an HSM to generate, store, and manage encryption keys for its healthcare clients. The HSM would be a physically secured device that protects the keys from unauthorized access and tampering. This approach ensures that the encryption keys are protected at all times, even if the underlying cloud infrastructure is compromised.
Data Backup and Disaster Recovery
Maintaining the availability and integrity of Protected Health Information (PHI) is paramount under HIPAA. Data backup and disaster recovery (DR) plans are critical components of a comprehensive HIPAA compliance strategy. These plans ensure that PHI remains accessible and protected even in the event of unforeseen circumstances, such as natural disasters, cyberattacks, or system failures. Implementing robust backup and DR solutions is not just a best practice; it’s a regulatory requirement for covered entities and business associates.
Importance of Data Backup and Disaster Recovery for HIPAA Compliance
The HIPAA Security Rule mandates the implementation of policies and procedures to address data backup and disaster recovery. This means covered entities must have documented plans in place to protect PHI from loss, corruption, or unavailability. Failure to adequately protect PHI can result in significant financial penalties, reputational damage, and legal liabilities.Data backups serve as a safeguard against data loss, enabling the restoration of PHI in the event of data corruption, accidental deletion, or hardware failures.
Disaster recovery plans Artikel the steps to be taken to resume normal operations after a disruptive event, ensuring business continuity and minimizing downtime. Together, these measures help organizations meet the HIPAA requirement for maintaining the confidentiality, integrity, and availability of PHI.
Creating a HIPAA-Compliant Backup Strategy in the Cloud
A well-defined backup strategy is essential for safeguarding PHI in the cloud. The strategy should encompass several key elements:
- Data Identification and Prioritization: Identify all PHI stored in the cloud and prioritize it based on its criticality and sensitivity. This helps determine the frequency and type of backups needed.
- Backup Frequency and Retention: Establish a schedule for regular backups, considering the volume of data, the rate of change, and the recovery point objectives (RPO). Define a retention period for backup data, complying with HIPAA’s record retention requirements, which may vary depending on state and federal regulations.
- Backup Types: Utilize a combination of backup types, such as full, incremental, and differential backups, to optimize backup speed and storage space utilization.
- Backup Location: Store backups in a secure, off-site location, preferably in a different geographic region than the primary data center, to ensure data availability in the event of a regional disaster. Cloud providers offer various geographic regions to meet this requirement.
- Encryption: Encrypt all backup data, both in transit and at rest, to protect PHI from unauthorized access. Use strong encryption algorithms, such as AES-256, to ensure data confidentiality.
- Testing and Validation: Regularly test the backup and recovery process to verify its effectiveness. Conduct simulated disaster recovery exercises to ensure that the organization can successfully restore data and resume operations within an acceptable timeframe.
- Access Controls: Implement robust access controls to restrict access to backup data. Only authorized personnel should be able to access, modify, or delete backup data.
- Audit Trails: Maintain detailed audit trails of all backup and recovery activities, including who performed the actions, when they occurred, and what data was affected.
Cloud-Based Disaster Recovery Solutions
Cloud providers offer a range of disaster recovery solutions that can help organizations meet their HIPAA compliance obligations. These solutions vary in complexity and cost, providing flexibility to choose the option that best fits the organization’s needs and budget.The following table Artikels different cloud-based disaster recovery solutions, providing a brief description of each and their key features:
| Solution Type | Description | Key Features | Considerations |
|---|---|---|---|
| Backup as a Service (BaaS) | Automated data backup to the cloud, typically involving regular snapshots and versioning. |
|
|
| Disaster Recovery as a Service (DRaaS) | Replication of virtual machines or entire environments to the cloud, enabling rapid failover in the event of a disaster. |
|
|
| Warm Standby | A scaled-down, but functional, version of the production environment is always running in the cloud. This allows for a faster recovery than a cold standby. |
|
|
| Cold Standby | A replica of the production environment is maintained in the cloud, but it is not running until a disaster is declared. This solution is typically the least expensive but has the longest recovery time. |
|
|
Choosing the right disaster recovery solution depends on factors such as the organization’s RTO and RPO requirements, budget constraints, and the criticality of the data being protected. Regardless of the solution chosen, regular testing and validation are essential to ensure that the DR plan is effective and meets the organization’s HIPAA compliance obligations. For instance, a healthcare provider with a high volume of patient data and strict service level agreements (SLAs) might choose a DRaaS solution to minimize downtime, while a smaller clinic with less stringent requirements might opt for a BaaS solution.
Audit Trails and Activity Monitoring
Implementing robust audit trails and activity monitoring is critical for maintaining HIPAA compliance within a cloud environment. These mechanisms provide a comprehensive record of all activities related to Protected Health Information (PHI), allowing organizations to detect, analyze, and respond to potential security breaches and policy violations. Effective audit trails not only help in meeting regulatory requirements but also contribute significantly to improving overall security posture.
Role of Audit Trails and Activity Monitoring
Audit trails and activity monitoring serve as the foundation for demonstrating compliance with HIPAA’s Security Rule. They provide an immutable record of every action performed on systems and data containing PHI. This includes who accessed the data, what actions were performed, when these actions occurred, and from where the access originated.
- Detecting Security Breaches: Audit logs can identify unauthorized access attempts, data modifications, and other suspicious activities that may indicate a security breach.
- Facilitating Incident Response: In the event of a security incident, audit logs provide crucial information for investigating the root cause, assessing the scope of the breach, and taking appropriate remediation steps.
- Supporting Compliance Audits: Audit trails are essential for demonstrating compliance with HIPAA regulations during audits conducted by regulatory bodies. They provide evidence of implemented security controls and adherence to policies.
- Improving Security Posture: By analyzing audit data, organizations can identify vulnerabilities, assess the effectiveness of security controls, and make informed decisions to enhance their security posture.
Implementing Audit Logging in the Cloud
Implementing effective audit logging in a cloud environment requires careful planning and configuration. The process involves selecting appropriate logging services, configuring logging policies, and establishing mechanisms for data storage and analysis.
- Selecting Logging Services: Choose cloud-native logging services or third-party solutions that integrate with your cloud environment. These services should provide features like centralized logging, log aggregation, and security event correlation.
- Configuring Logging Policies: Define specific logging policies to capture relevant events based on HIPAA requirements and your organization’s security policies. Consider logging events at different levels (e.g., system-level, application-level, and database-level).
- Defining Log Retention Policies: Establish clear retention policies for audit logs, ensuring that logs are stored for the required period as mandated by HIPAA regulations. Consider the volume of logs and the storage capacity needed.
- Securing Audit Logs: Protect audit logs from unauthorized access and tampering. Implement access controls, encryption, and integrity checks to ensure the confidentiality and integrity of log data.
- Monitoring and Analysis: Implement automated monitoring and alerting mechanisms to detect suspicious activities and potential security breaches. Regularly review and analyze audit logs to identify trends, anomalies, and potential risks.
Events to Log and Monitor for HIPAA Violations
A comprehensive audit logging strategy should capture a wide range of events related to PHI access and data modifications. The following are examples of events that should be logged and monitored:
- User Access and Authentication:
- Successful and failed login attempts, including timestamps, user IDs, and source IP addresses.
- Account lockouts and password resets.
- Changes to user account privileges and permissions.
- Data Access and Modification:
- Access to PHI, including the data accessed, the user who accessed it, and the timestamp.
- Data modifications, such as additions, deletions, and updates, along with the user who made the changes and the affected data.
- Data downloads and exports.
- System and Network Activity:
- System startup and shutdown events.
- Changes to system configurations, such as firewall rules and security settings.
- Network traffic patterns and anomalies.
- Security-Related Events:
- Detection of malware or malicious activities.
- Security alerts and warnings generated by security tools.
- Unusual or suspicious activities, such as multiple failed login attempts from a single IP address.
For example, consider a healthcare provider using a cloud-based Electronic Health Record (EHR) system. They implement audit logging to track every instance of a user accessing a patient’s medical record. The system logs the user’s ID, the time of access, the specific records accessed, and the IP address from which the access originated. If an unauthorized user attempts to access a patient’s record, the audit logs will capture the failed attempt, including the user’s credentials and the IP address, which can trigger an alert to the security team.
This allows for a quick response to prevent a potential data breach and maintain HIPAA compliance.
Risk Assessment and Management
Implementing HIPAA security in the cloud necessitates a robust risk assessment and management strategy. This involves identifying potential vulnerabilities and threats to protected health information (PHI), evaluating the likelihood and impact of those threats, and implementing safeguards to mitigate the risks. A proactive approach to risk management is not only a regulatory requirement but also crucial for maintaining patient trust and ensuring the confidentiality, integrity, and availability of sensitive data.
Conducting a Thorough Risk Assessment
A comprehensive risk assessment is the cornerstone of HIPAA compliance in the cloud. This process systematically identifies and analyzes potential security risks to PHI.The risk assessment process typically includes these key steps:
- Data Identification: Identify all locations where PHI is created, received, maintained, or transmitted within the cloud environment. This includes data at rest, in transit, and in use. Document all systems, applications, and devices that access or store PHI.
- Threat Identification: Identify potential threats that could compromise the confidentiality, integrity, or availability of PHI. These threats can be categorized as:
- Human Threats: These include accidental or intentional actions by employees, contractors, or other authorized users (e.g., data breaches, unauthorized access, or malicious insider attacks).
- Natural Threats: These include events such as floods, fires, earthquakes, or other natural disasters that could disrupt cloud services or damage physical infrastructure.
- Environmental Threats: These threats relate to power outages, HVAC failures, or other environmental factors that could impact cloud operations.
- Technical Threats: These encompass vulnerabilities in software, hardware, or network infrastructure (e.g., malware, ransomware, denial-of-service attacks, or misconfigurations).
- Vulnerability Identification: Identify vulnerabilities that could be exploited by the identified threats. Vulnerabilities are weaknesses in systems or processes that could be exploited by a threat. Examples include:
- Software vulnerabilities: Unpatched software, outdated operating systems, or insecure coding practices.
- Configuration vulnerabilities: Misconfigured firewalls, access controls, or encryption settings.
- Network vulnerabilities: Weak network segmentation, unencrypted network traffic, or open ports.
- Physical vulnerabilities: Lack of physical security controls at data centers.
- Risk Analysis: Analyze the likelihood of each threat exploiting a vulnerability and the potential impact on the confidentiality, integrity, and availability of PHI. This involves:
- Likelihood Assessment: Estimate the probability of a threat exploiting a vulnerability. Consider factors such as the frequency of attacks, the presence of existing controls, and the attacker’s motivation and capabilities.
- Impact Assessment: Determine the potential harm if a threat exploits a vulnerability. This includes financial costs (e.g., fines, legal fees, breach notification costs), reputational damage, and operational disruptions.
- Risk Determination: Calculate the overall risk level for each threat-vulnerability pair. This is often done using a risk matrix, which combines the likelihood and impact assessments.
- Documentation: Document all steps of the risk assessment process, including the identified threats, vulnerabilities, risk levels, and existing security controls. This documentation is crucial for demonstrating compliance and for informing the development of a risk management plan.
- Regular Reviews: Conduct regular risk assessments (e.g., annually or more frequently) to account for changes in the cloud environment, new threats, and evolving regulations.
Methods for Mitigating Identified Risks
Once risks are identified, implementing appropriate safeguards is critical. These safeguards can be categorized into technical, administrative, and physical controls.
- Technical Safeguards: These are technological measures used to protect electronic PHI. Examples include:
- Encryption: Encrypt PHI at rest and in transit to protect it from unauthorized access. This can involve using strong encryption algorithms, such as AES-256.
- Access Controls: Implement strong access controls, including multi-factor authentication (MFA), to restrict access to PHI to authorized users only. Use the principle of least privilege.
- Firewalls and Intrusion Detection/Prevention Systems (IDS/IPS): Use firewalls to control network traffic and IDS/IPS to detect and prevent malicious activity.
- Data Loss Prevention (DLP): Implement DLP solutions to monitor and prevent sensitive data from leaving the cloud environment.
- Vulnerability Scanning and Patch Management: Regularly scan systems for vulnerabilities and promptly apply security patches.
- Administrative Safeguards: These are policies and procedures used to manage the selection, development, implementation, and maintenance of security measures to protect PHI. Examples include:
- Security Policies and Procedures: Develop and maintain comprehensive security policies and procedures that address all aspects of HIPAA compliance.
- Employee Training: Provide regular security awareness training to all employees, contractors, and other authorized users. Training should cover topics such as HIPAA regulations, data security best practices, and incident response procedures.
- Business Associate Agreements (BAAs): Ensure that BAAs are in place with all cloud service providers (CSPs) and other business associates that have access to PHI.
- Incident Response Plan: Develop and implement an incident response plan to address security incidents, including data breaches. The plan should Artikel procedures for detection, containment, eradication, recovery, and post-incident analysis.
- Risk Management Plan: Develop and maintain a risk management plan that addresses the identified risks and Artikels the steps to be taken to mitigate them.
- Physical Safeguards: These are physical measures to protect electronic PHI. Examples include:
- Data Center Security: Ensure that data centers used by the CSP have robust physical security controls, such as access control, surveillance, and environmental monitoring.
- Device Security: Implement security measures for devices that access PHI, such as laptops, tablets, and smartphones. This includes device encryption, remote wipe capabilities, and access controls.
- Media Disposal: Establish procedures for securely disposing of PHI, including hard drives, backup tapes, and other media.
Designing a Risk Management Plan
A well-defined risk management plan is essential for maintaining HIPAA compliance and protecting PHI. The plan should be tailored to the specific cloud environment and regularly updated to reflect changes in the environment and evolving threats.Key components of a risk management plan include:
- Risk Assessment Results: Include the results of the risk assessment, including the identified threats, vulnerabilities, risk levels, and existing security controls.
- Risk Mitigation Strategies: Artikel the specific steps to be taken to mitigate the identified risks, including the implementation of technical, administrative, and physical safeguards. For each risk, the plan should specify the controls to be implemented, the responsible parties, and the timelines for implementation.
- Implementation Schedule: Provide a detailed schedule for implementing the risk mitigation strategies. This should include milestones and deadlines for each task.
- Roles and Responsibilities: Clearly define the roles and responsibilities for each individual or team involved in implementing and maintaining the risk management plan.
- Monitoring and Evaluation: Establish procedures for monitoring the effectiveness of the implemented safeguards and evaluating the overall risk management program. This should include regular audits, vulnerability scans, and penetration testing.
- Plan Review and Updates: The risk management plan should be reviewed and updated regularly (e.g., annually or more frequently) to account for changes in the cloud environment, new threats, and evolving regulations. The plan should be updated whenever significant changes occur in the environment, such as the introduction of new systems or applications, or when new vulnerabilities are discovered.
- Incident Response: Integrate the incident response plan within the risk management plan. This will help ensure that security incidents are handled promptly and effectively.
A robust risk management plan is not a static document; it’s a living process that requires ongoing attention and adaptation.
Data Breach Notification and Response

Data breaches are an unfortunate reality in the digital age, and healthcare organizations storing protected health information (PHI) in the cloud are particularly vulnerable. A robust data breach notification and response plan is crucial for mitigating the damage caused by a breach, fulfilling legal obligations under HIPAA, and maintaining patient trust. This section Artikels the requirements for data breach notification and response, providing a practical checklist for organizations to follow.
HIPAA Data Breach Notification Requirements
The HIPAA Breach Notification Rule mandates specific actions that covered entities and business associates must take in the event of a data breach. Failure to comply with these requirements can result in significant penalties.
The key elements of the notification requirements include:
- Definition of a Breach: A “breach” is defined as the unauthorized acquisition, access, use, or disclosure of PHI which compromises the security or privacy of the PHI. Certain disclosures are exempt, such as unintentional disclosures to another workforce member.
- Notification to Individuals: Individuals whose PHI has been breached must be notified without unreasonable delay, and no later than 60 days following the discovery of the breach. The notification must be provided in plain language and include specific information about the breach, such as a description of the incident, the types of PHI involved, the steps the individual should take to protect themselves, and contact information for the covered entity.
- Notification to the Department of Health and Human Services (HHS): The HHS must be notified of breaches. Breaches affecting 500 or more individuals must be reported to the HHS Secretary without unreasonable delay, and no later than 60 days after discovery. Breaches affecting fewer than 500 individuals must be reported to the HHS annually.
- Notification to the Media: For breaches affecting 500 or more individuals, the media must also be notified within 60 days of discovery, often through a press release or public statement.
- Notification by Business Associates: Business associates are required to notify covered entities of any breaches they discover. The business associate agreement should specify the timeframe and content of this notification.
Steps for Responding to a Data Breach in the Cloud
Responding effectively to a data breach requires a systematic approach to contain the breach, assess the damage, and remediate vulnerabilities. The following steps are crucial:
The process involves the following key steps:
- Containment: Immediately take steps to contain the breach and prevent further unauthorized access to PHI. This may involve isolating affected systems, changing passwords, and blocking malicious IP addresses.
- Investigation and Assessment: Conduct a thorough investigation to determine the scope of the breach, including the date and time of the incident, the systems affected, the types of PH of compromised, and the number of individuals impacted. This should include a review of security logs and activity monitoring data.
- Notification: Implement the notification procedures as required by HIPAA. This includes notifying affected individuals, the HHS, and, if applicable, the media.
- Remediation: Implement corrective actions to prevent future breaches. This may include strengthening security controls, patching vulnerabilities, improving employee training, and updating policies and procedures.
- Documentation: Thoroughly document all aspects of the breach response, including the investigation, notification process, and remediation efforts. This documentation is crucial for regulatory compliance and potential legal proceedings.
Data Breach Response Checklist
A well-defined checklist helps ensure a consistent and effective response to a data breach. This checklist should be readily accessible to relevant personnel and regularly reviewed and updated.
The following elements should be included in a comprehensive data breach response checklist:
- Incident Identification and Verification:
- Verify the incident and confirm it is a data breach.
- Activate the incident response team.
- Containment:
- Isolate affected systems and networks.
- Change passwords for all potentially compromised accounts.
- Implement temporary security measures (e.g., increased monitoring).
- Assessment and Investigation:
- Determine the scope of the breach (affected systems, data types, individuals affected).
- Gather and analyze security logs, system logs, and other relevant data.
- Identify the root cause of the breach.
- Notification Procedures:
- Internal Notification:
- Notify key internal stakeholders (e.g., legal counsel, privacy officer, senior management).
- Assign roles and responsibilities for notification.
- External Notification:
- Prepare notification letters to individuals, including required information.
- Determine the appropriate notification method (e.g., mail, email, phone).
- Prepare notifications for the HHS and, if applicable, the media.
- Coordinate with legal counsel regarding notification requirements.
- Internal Notification:
- Remediation and Recovery:
- Implement corrective actions to address the root cause of the breach.
- Patch vulnerabilities.
- Strengthen security controls (e.g., access controls, encryption).
- Review and update policies and procedures.
- Restore affected systems and data from backups, ensuring data integrity.
- Post-Incident Review and Documentation:
- Conduct a post-incident review to identify lessons learned.
- Update the data breach response plan based on the findings.
- Document all actions taken, including investigation findings, notification details, and remediation efforts.
Cloud Service Provider (CSP) Selection
Choosing a Cloud Service Provider (CSP) is a critical decision for any organization handling Protected Health Information (PHI). The CSP you select directly impacts your ability to meet HIPAA Security Rule requirements and protect sensitive patient data. Thorough evaluation and due diligence are essential to ensure the CSP aligns with your compliance obligations and maintains the confidentiality, integrity, and availability of PHI.
Criteria for Evaluating a CSP’s HIPAA Compliance Posture
Evaluating a CSP’s HIPAA compliance posture requires a multi-faceted approach. It’s not enough to simply take a CSP’s word; you must verify their claims through documented evidence and independent assessments. This evaluation should consider various factors, including the CSP’s security practices, contractual commitments, and business associate agreements (BAAs).
- Business Associate Agreement (BAA): The BAA is the cornerstone of HIPAA compliance when using a CSP. It legally obligates the CSP to protect PHI and Artikels their responsibilities under HIPAA. A comprehensive BAA should clearly define the scope of services covered, the CSP’s security obligations, and procedures for data breach notification.
- Security Policies and Procedures: Examine the CSP’s security policies and procedures. These documents should detail how the CSP implements the HIPAA Security Rule requirements, including administrative, physical, and technical safeguards. Look for policies addressing access controls, data encryption, data backup and recovery, audit trails, and incident response.
- Data Encryption: Verify the CSP’s data encryption practices. Data encryption is crucial to protect PHI at rest and in transit. The CSP should use strong encryption algorithms, such as AES-256, and provide details on how they manage encryption keys.
- Access Controls: Review the CSP’s access control mechanisms. These controls should restrict access to PHI to authorized personnel only. The CSP should implement role-based access control (RBAC), multi-factor authentication (MFA), and regular access reviews.
- Data Backup and Disaster Recovery: Assess the CSP’s data backup and disaster recovery (DR) plans. These plans are essential to ensure the availability of PHI in the event of a data loss or system failure. The CSP should have documented backup procedures, offsite data storage, and a tested DR plan with a defined recovery time objective (RTO) and recovery point objective (RPO).
- Audit Trails and Activity Monitoring: Evaluate the CSP’s audit trail and activity monitoring capabilities. These features are essential to track user access, data modifications, and security events. The CSP should log all relevant activities and provide tools for reviewing and analyzing audit logs.
- Incident Response Plan: Review the CSP’s incident response plan. This plan should detail the steps the CSP will take in the event of a data breach or security incident. The plan should include procedures for identifying, containing, and remediating the incident, as well as for notifying affected parties and regulatory agencies.
- Physical Security: Assess the physical security of the CSP’s data centers. The CSP should have robust physical security measures in place to protect its infrastructure and prevent unauthorized access to PHI. This includes measures such as access control, surveillance, and environmental controls.
- Compliance Certifications: Determine the CSP’s relevant compliance certifications. Certifications, such as HITRUST, ISO 27001, and SOC 2, demonstrate that the CSP has undergone independent audits and meets specific security standards.
- Vendor Risk Management: Implement a vendor risk management program to continually monitor the CSP’s security posture. This program should include ongoing assessments, security audits, and contract reviews.
Questions to Ask a CSP to Ensure They Meet HIPAA Security Requirements
Asking the right questions is crucial to determine if a CSP can meet your HIPAA compliance needs. Prepare a detailed questionnaire covering all aspects of the HIPAA Security Rule. Be sure to document all responses.
- BAA Related Questions:
- Does the CSP offer a BAA that meets HIPAA requirements?
- Can the BAA be customized to address specific needs?
- What is the process for amending or terminating the BAA?
- Security Controls and Policies:
- Can you provide documentation of your security policies and procedures?
- How do you ensure the confidentiality, integrity, and availability of PHI?
- What security awareness training do you provide to your employees?
- What security standards or frameworks do you adhere to (e.g., NIST, ISO)?
- Data Encryption:
- How is data encrypted at rest and in transit?
- What encryption algorithms are used?
- How are encryption keys managed?
- Access Controls:
- What access control mechanisms are in place (e.g., RBAC, MFA)?
- How are user access rights managed and reviewed?
- How do you ensure that access is limited to authorized personnel?
- Data Backup and Disaster Recovery:
- What are your data backup and recovery procedures?
- Where is data stored, and what is the geographic location?
- What is your RTO and RPO?
- How often are backups tested?
- Audit Trails and Activity Monitoring:
- What audit logging and monitoring capabilities are in place?
- What types of activities are logged?
- How long are audit logs retained?
- What tools are available for reviewing and analyzing audit logs?
- Incident Response:
- What is your incident response plan?
- What is the process for reporting and responding to security incidents?
- How do you handle data breaches, including notification procedures?
- Who is the designated security contact for incident reporting?
- Compliance and Certifications:
- What HIPAA compliance certifications or attestations do you hold?
- Are you audited by a third party?
- Can you provide audit reports?
- Vendor Management:
- Do you use subcontractors, and if so, do they also have BAAs?
- How do you manage the security of your third-party vendors?
How to Verify a CSP’s Certifications and Attestations Related to Data Security
Verifying a CSP’s certifications and attestations provides objective evidence of their commitment to data security. Review the documentation and reports provided by the CSP to confirm the scope of the certification and the findings of any audits.
- Review Relevant Certifications: Look for certifications relevant to data security and HIPAA compliance. The most common and relevant certifications include:
- HITRUST CSF Certification: HITRUST is a widely recognized framework for healthcare organizations and their service providers. It provides a comprehensive set of security and compliance requirements. Obtaining HITRUST certification indicates a high level of security posture.
- ISO 27001 Certification: ISO 27001 is an international standard for information security management systems (ISMS). It provides a framework for establishing, implementing, maintaining, and continually improving an ISMS.
- SOC 2 Reports: SOC 2 reports are based on the AICPA’s Trust Services Criteria. They assess a service organization’s controls related to security, availability, processing integrity, confidentiality, and privacy. SOC 2 reports are a good indicator of a CSP’s security controls.
- Examine Audit Reports: Request and review the CSP’s audit reports. These reports provide detailed information about the CSP’s security controls and any identified weaknesses. Pay close attention to the scope of the audit, the findings, and any remediation efforts.
- Verify the Scope of the Certification: Ensure the certification covers the services you plan to use. Some certifications may only apply to certain aspects of the CSP’s operations.
- Confirm the Date of the Certification: Verify that the certification is current and up-to-date. Certifications typically have an expiration date and must be renewed periodically.
- Contact the Certifying Body: If you have any doubts about the validity of a certification, contact the certifying body directly to verify its authenticity. This can provide assurance regarding the CSP’s adherence to the standards.
- Review Attestation Reports: Some CSPs may provide attestation reports from independent auditors. These reports attest to the CSP’s compliance with specific security standards or regulations.
- Assess the CSP’s Remediation Efforts: If the audit reports identify any weaknesses, assess the CSP’s efforts to remediate those weaknesses. Request information on the steps taken to address the issues and the timeline for completion.
Ongoing Compliance and Training
Maintaining HIPAA compliance in the cloud is not a one-time task; it requires continuous vigilance and proactive measures. Regular monitoring, comprehensive reviews, and robust training programs are essential to ensure the ongoing protection of protected health information (PHI). This section Artikels the key elements of an effective ongoing compliance strategy.
Ongoing Monitoring and Compliance Reviews
Continuous monitoring and regular compliance reviews are crucial for identifying and addressing potential vulnerabilities in a timely manner. These practices help to maintain the integrity and security of PHI stored in the cloud.Regular compliance reviews typically involve:
- Systematic Monitoring: Implementing automated tools and processes to continuously monitor system activity, network traffic, and access logs for suspicious or unauthorized behavior. This includes real-time alerts for potential security incidents.
- Regular Vulnerability Scanning: Conducting periodic vulnerability scans of cloud infrastructure and applications to identify and remediate security weaknesses. This can be automated to run regularly and provide reports on discovered vulnerabilities.
- Performance Audits: Reviewing system performance to ensure that security controls are not negatively impacting system functionality or user experience. Performance audits are crucial to ensure systems remain efficient.
- Policy and Procedure Updates: Regularly reviewing and updating security policies and procedures to reflect changes in regulations, technology, and organizational practices. This includes documenting all changes and communicating them to relevant stakeholders.
- Risk Assessments: Conducting periodic risk assessments to identify and evaluate potential threats and vulnerabilities. These assessments inform the development of security controls and mitigation strategies.
- Incident Response Plan Testing: Regularly testing the incident response plan to ensure its effectiveness in handling security incidents. This can include simulated attacks and tabletop exercises.
- Documentation and Reporting: Maintaining comprehensive documentation of all compliance activities, including audit logs, vulnerability scan reports, and incident response reports. This documentation is essential for demonstrating compliance to regulatory bodies.
Regular Security Audits
Security audits are a critical component of an effective HIPAA compliance strategy. They provide an independent assessment of the effectiveness of security controls and help to identify areas for improvement.Regular security audits should be conducted according to these procedures:
- Scope Definition: Clearly define the scope of the audit, including the systems, applications, and data that will be reviewed. The scope should be tailored to the specific environment and the risks associated with it.
- Audit Planning: Develop a detailed audit plan that Artikels the objectives, scope, methodology, and schedule of the audit. The plan should be reviewed and approved by relevant stakeholders.
- Evidence Collection: Gather evidence to support the audit findings. This may include reviewing documentation, interviewing personnel, and examining system logs.
- Control Testing: Test the effectiveness of security controls to ensure they are implemented correctly and functioning as intended. This may involve performing penetration tests, vulnerability scans, and access control reviews.
- Findings and Reporting: Document the audit findings, including any identified vulnerabilities or weaknesses. Prepare a detailed report that summarizes the audit results and provides recommendations for remediation.
- Remediation and Follow-up: Implement the recommendations from the audit report to address any identified vulnerabilities or weaknesses. Conduct follow-up audits to verify that the remediation efforts were effective.
Implementing a Comprehensive HIPAA Training Program
A well-designed HIPAA training program is essential for ensuring that employees understand their responsibilities for protecting PHI. The program should be tailored to the roles and responsibilities of each employee and should be updated regularly to reflect changes in regulations and organizational practices.A comprehensive HIPAA training program includes:
- Initial Training: Providing all employees with initial HIPAA training upon hire. This training should cover the basics of HIPAA, including the Privacy Rule, Security Rule, and Breach Notification Rule.
- Role-Based Training: Tailoring training to the specific roles and responsibilities of each employee. For example, employees who have access to PHI should receive training on how to handle and protect this information.
- Annual Refresher Training: Conducting annual refresher training to reinforce key concepts and update employees on any changes to HIPAA regulations or organizational policies. This ensures ongoing awareness.
- Security Awareness Training: Educating employees on security best practices, such as password management, phishing awareness, and data protection. This training should be integrated into the overall HIPAA training program.
- Breach Response Training: Training employees on how to respond to a data breach, including reporting procedures and incident response protocols.
- Documentation and Record Keeping: Maintaining documentation of all training activities, including training materials, attendance records, and test results. This documentation is essential for demonstrating compliance.
- Regular Assessments: Evaluating the effectiveness of the training program through quizzes, assessments, and feedback from employees. This information should be used to improve the training program over time.
Final Summary
In conclusion, achieving HIPAA compliance in the cloud is not just possible, it’s a strategic imperative. By implementing robust security measures, establishing clear policies and procedures, and fostering a culture of vigilance, healthcare organizations can harness the benefits of cloud computing while safeguarding patient data. Remember, ongoing monitoring, regular audits, and continuous training are essential for maintaining compliance and adapting to the ever-evolving landscape of cloud security.
Embracing these practices will not only protect sensitive information but also build trust and confidence with patients and stakeholders.
Key Questions Answered
What is the difference between HIPAA Security Rule and Privacy Rule?
The HIPAA Privacy Rule establishes national standards to protect individuals’ medical records and other personal health information. The HIPAA Security Rule specifically addresses the security of electronic protected health information (ePHI), detailing administrative, physical, and technical safeguards to ensure its confidentiality, integrity, and availability.
Does HIPAA apply to all cloud providers?
HIPAA applies to cloud providers that create, receive, maintain, or transmit protected health information (PHI) on behalf of a covered entity or another business associate. These providers must enter into a Business Associate Agreement (BAA) and comply with the HIPAA Security Rule.
What happens if there is a data breach?
In the event of a data breach, covered entities and business associates are required to notify affected individuals, the Department of Health and Human Services (HHS), and potentially the media. They must also conduct a thorough investigation, implement corrective actions, and take steps to prevent future breaches. Penalties for non-compliance can be severe, including financial penalties and reputational damage.
How often should we review our HIPAA compliance?
HIPAA compliance should be reviewed regularly, at least annually, or more frequently if there are significant changes in the cloud environment, security threats, or regulations. These reviews should include risk assessments, security audits, and updates to policies and procedures to ensure ongoing compliance.
What are some common security risks in the cloud?
Common security risks in the cloud include unauthorized access, data breaches, malware attacks, data loss, and insider threats. Properly configured access controls, data encryption, and robust monitoring systems can mitigate these risks.