In today’s unpredictable business landscape, safeguarding your organization against disruptions is paramount. Integrating Business Continuity Planning (BCP) with Disaster Recovery (DR) is no longer a luxury, but a necessity. This guide provides a comprehensive roadmap to seamlessly merge these two critical strategies, ensuring your business can withstand unforeseen events and maintain operational resilience.
We’ll explore the core components of BCP and DR, delve into identifying critical functions and assets, and dissect the crucial processes of risk assessment and business impact analysis. From developing robust strategies to ensuring legal compliance and managing budgets, this guide offers actionable insights to build a resilient business ready to face any challenge. We’ll examine how to craft plans, conduct tests, and incorporate the latest technologies to protect your operations.
Understanding Business Continuity Planning (BCP) and Disaster Recovery (DR)
Business Continuity Planning (BCP) and Disaster Recovery (DR) are crucial for ensuring an organization’s resilience in the face of disruptions. While often used together, they address distinct aspects of operational continuity. Understanding their core components, objectives, and how they complement each other is essential for creating a robust business resilience strategy.
Core Components of BCP and DR: Differentiating Strategies
BCP and DR have distinct focuses and components. BCP is a broader, more holistic approach, while DR is more narrowly focused on IT infrastructure recovery.BCP typically includes:
- Business Impact Analysis (BIA): This process identifies critical business functions and their dependencies, estimating the potential impact of disruptions. It determines the maximum tolerable downtime (MTD) and the recovery time objective (RTO) for each function. For example, a BIA might reveal that order processing is critical, with an MTD of 4 hours, meaning the business can only tolerate a four-hour outage before significant financial losses occur.
- Recovery Strategies: This involves developing plans to ensure critical business functions can continue operating during a disruption. These strategies include procedures for data backup and recovery, alternate work locations, and communication plans. For instance, a company might establish a hot site for critical systems, enabling immediate failover in case of a primary site outage.
- Plan Development and Documentation: This phase involves creating detailed plans outlining the steps to be taken during a disruption, including roles and responsibilities, contact information, and procedures. This includes the documentation of all recovery procedures, from IT to communications.
- Testing and Exercises: Regularly testing and exercising the BCP to ensure its effectiveness and identify any weaknesses. This can involve tabletop exercises, simulations, and full-scale drills. A company might conduct a simulated power outage to test its backup generators and recovery procedures.
DR primarily focuses on:
- IT Infrastructure Recovery: This involves the procedures and resources required to restore IT systems, data, and applications after a disaster. This includes data backups, failover mechanisms, and recovery sites.
- Data Backup and Recovery: Implementing robust data backup and recovery solutions to ensure data integrity and availability. This includes regular backups, offsite storage, and recovery procedures. For example, a company might use a combination of on-site and off-site backups, with regular testing to ensure data can be restored quickly.
- Recovery Site Strategies: Selecting and maintaining recovery sites, such as hot sites, cold sites, or warm sites, to ensure IT infrastructure can be quickly restored. A hot site provides a fully functional environment ready for immediate failover, while a cold site requires more time to set up.
- Testing and Maintenance: Regularly testing and maintaining DR plans to ensure they are up-to-date and effective. This includes testing failover procedures, verifying backup integrity, and updating documentation.
Examples of Common Business Disruptions and Their Impact
Various disruptions can impact businesses, each with varying degrees of severity. Understanding these potential threats is critical for effective BCP and DR.
- Natural Disasters: Events like hurricanes, floods, earthquakes, and wildfires can cause significant damage to infrastructure, disrupt operations, and lead to data loss. The 2017 Hurricane Harvey, for example, caused billions of dollars in damage and disrupted operations for numerous businesses in the Houston area.
- Cyberattacks: Ransomware, malware, and other cyberattacks can disrupt IT systems, compromise data, and lead to financial losses. The 2021 Colonial Pipeline ransomware attack demonstrated the devastating impact of cyberattacks on critical infrastructure, causing fuel shortages and economic disruption.
- Power Outages: Prolonged power outages can shut down operations, damage equipment, and disrupt communication systems. The 2003 Northeast Blackout affected millions and caused significant economic losses for businesses across multiple states.
- Human Error: Mistakes by employees, such as accidental data deletion or incorrect system configurations, can lead to disruptions and data loss.
- Supply Chain Disruptions: Events like pandemics, political instability, or transportation issues can disrupt supply chains, impacting the availability of goods and services. The COVID-19 pandemic caused widespread supply chain disruptions, leading to shortages and price increases for many products.
The impact of these disruptions can include:
- Financial Losses: Revenue loss due to downtime, recovery costs, and legal liabilities.
- Reputational Damage: Loss of customer trust and damage to brand image.
- Operational Disruptions: Inability to provide goods or services.
- Data Loss: Loss of critical data and information.
- Legal and Regulatory Consequences: Fines and penalties for non-compliance.
Objectives of BCP and DR: Complementary Roles
BCP and DR share the overarching goal of ensuring business resilience but achieve this through different means.The primary objectives of BCP are:
- Minimize Downtime: To reduce the duration of business disruptions.
- Protect Critical Business Functions: To ensure that essential operations continue to function, even during a disruption.
- Reduce Financial Losses: To mitigate the financial impact of disruptions.
- Protect Reputation: To maintain customer trust and protect brand image.
- Ensure Regulatory Compliance: To meet legal and regulatory requirements.
The primary objectives of DR are:
- Restore IT Systems and Data: To recover IT infrastructure, applications, and data quickly after a disaster.
- Minimize Data Loss: To protect data integrity and prevent significant data loss.
- Reduce Recovery Time: To minimize the time required to restore IT systems.
- Ensure Business Continuity: To support the overall business continuity goals.
Both BCP and DR are essential for achieving business resilience. BCP provides the framework for managing the overall response to a disruption, while DR focuses on the technical aspects of IT recovery.
The BCP Artikels what to do, and the DR plan provides the technical means to do it.
Importance of a Unified Approach to Business Resilience
A unified approach to business resilience integrates BCP and DR into a comprehensive strategy. This ensures that all aspects of the business are considered when preparing for and responding to disruptions.Benefits of a unified approach include:
- Improved Coordination: Seamless coordination between business and IT teams during a disruption.
- Enhanced Efficiency: Streamlined recovery processes and reduced recovery time.
- Reduced Costs: Optimized resource allocation and reduced recovery expenses.
- Increased Resilience: A more robust and resilient organization.
- Better Communication: Clear and consistent communication during a crisis.
This unified approach involves:
- Integrated Planning: Aligning BCP and DR plans to ensure they complement each other.
- Shared Resources: Utilizing shared resources, such as communication systems and recovery sites.
- Regular Testing: Conducting integrated testing and exercises to validate the effectiveness of the plans.
- Cross-Functional Training: Training employees from all departments on their roles and responsibilities during a disruption.
Identifying Critical Business Functions and Assets
Identifying critical business functions and assets is a foundational step in integrating Business Continuity Planning (BCP) with Disaster Recovery (DR). This process ensures that resources are allocated effectively to protect the most vital aspects of an organization, minimizing downtime and financial losses during a disruptive event. It involves a thorough assessment of all business processes and the resources required to support them.
Methods for Assessing Critical Business Functions
Assessing critical business functions requires a structured approach to identify those that are essential for the organization’s survival and ongoing operations. This involves a combination of qualitative and quantitative analyses.
- Business Impact Analysis (BIA): A BIA is a crucial process for identifying and evaluating the potential impacts of disruptions to business functions. It involves:
- Identifying Business Functions: Listing all key business processes, such as order processing, customer service, and payroll.
- Determining Maximum Tolerable Downtime (MTD): Estimating the maximum period a business function can be unavailable before causing irreparable damage.
- Assessing Impact: Evaluating the financial, operational, reputational, and legal impacts of downtime for each function. This includes estimating revenue loss, increased expenses, and damage to customer relationships.
- Identifying Dependencies: Determining the resources, systems, and third-party services that each function relies upon.
For example, a retail company might determine that its point-of-sale (POS) system has a very low MTD due to its direct impact on sales revenue. Conversely, internal training programs might have a higher MTD.
- Risk Assessment: Conducting a risk assessment helps to identify potential threats and vulnerabilities that could disrupt business functions. This involves:
- Identifying Threats: Listing potential threats such as natural disasters, cyberattacks, power outages, and human error.
- Assessing Vulnerabilities: Identifying weaknesses in systems, infrastructure, and processes that could be exploited by threats.
- Analyzing Likelihood and Impact: Evaluating the probability of each threat occurring and the potential impact on business functions.
- Developing Mitigation Strategies: Implementing controls and safeguards to reduce the likelihood and impact of identified risks.
A manufacturing company might identify a power outage as a high-impact, medium-likelihood threat, prompting them to invest in backup power generators.
- Process Mapping: Process mapping visually represents the flow of business activities. This can help identify critical points where disruptions could have a significant impact.
- Creating Flowcharts: Using flowcharts to illustrate the steps involved in each business function.
- Identifying Bottlenecks: Pinpointing areas where delays or failures could occur.
- Analyzing Dependencies: Visualizing the relationships between different processes and resources.
For example, a process map of an online ordering system might reveal that the payment gateway is a critical bottleneck, highlighting the need for redundant payment processing solutions.
Procedure for Prioritizing Business Processes Based on Impact
Prioritizing business processes is essential for allocating resources effectively and ensuring that the most critical functions are protected first. This involves a structured approach using impact assessments.
- Categorize Business Processes: Group business processes based on their criticality, using a predefined classification system. Common categories include:
- Critical: Processes that must be recovered immediately to prevent significant financial loss, legal repercussions, or damage to reputation.
- Important: Processes that are essential for ongoing operations but have a lower priority than critical processes.
- Non-Critical: Processes that are not essential for immediate operations and can be recovered later.
For instance, a financial institution might classify its core banking system as “critical,” customer service as “important,” and internal training programs as “non-critical.”
- Assign Impact Scores: Assign numerical scores to each process based on the potential impact of downtime. This can include factors such as financial loss, reputational damage, legal and regulatory consequences, and operational disruption.
Example of impact factors and scoring (1-5, 5 being the highest impact):
- Financial Loss: 1 (minimal)
-5 (catastrophic) - Reputational Damage: 1 (minimal)
-5 (catastrophic) - Legal/Regulatory Consequences: 1 (minimal)
-5 (catastrophic) - Operational Disruption: 1 (minimal)
-5 (catastrophic)
- Financial Loss: 1 (minimal)
- Calculate Priority Levels: Use the impact scores to calculate a priority level for each process. This can be done by summing the scores or using a weighted scoring system.
For example, the weighted score formula could be: Priority = (Financial Loss
– 0.4) + (Reputational Damage
– 0.3) + (Legal Consequences
– 0.2) + (Operational Disruption
– 0.1) - Document Prioritization: Create a documented list of prioritized business processes, including their assigned priority levels, impact assessments, and recovery requirements.
This documentation serves as a reference for allocating resources and developing recovery strategies.
- Regular Review: Regularly review and update the prioritization of business processes to reflect changes in the business environment, regulatory requirements, and operational needs.
Changes in technology, business strategies, or market conditions can necessitate updates to process prioritization.
Process of Identifying and Classifying Vital Assets
Identifying and classifying vital assets is crucial for protecting the resources that support critical business functions. This involves categorizing and assessing assets based on their importance and sensitivity.
- Identify Assets: Create an inventory of all assets, including data, systems, infrastructure, and personnel. This includes:
- Data: Customer data, financial records, intellectual property, and operational data.
- Systems: Servers, applications, databases, and network infrastructure.
- Infrastructure: Buildings, power supplies, and communication systems.
- Personnel: Key employees and specialized teams.
For instance, a healthcare provider’s assets include patient medical records (data), electronic health record (EHR) systems (systems), and medical equipment (infrastructure).
- Classify Assets: Categorize assets based on their criticality, sensitivity, and legal/regulatory requirements. Common classification levels include:
- Critical: Assets essential for the operation of critical business functions.
- Important: Assets that support important business functions but are not critical.
- Sensitive: Assets containing confidential or protected information (e.g., Personally Identifiable Information – PII, financial data).
- Public: Assets containing information that can be publicly disclosed.
A financial institution might classify customer financial data as “critical” and “sensitive,” while marketing brochures would be classified as “public.”
- Assess Asset Value: Determine the value of each asset, considering its replacement cost, the cost of downtime, and the potential impact on the organization.
For example, the value of a database server would include its hardware and software costs, as well as the potential financial loss if the server were unavailable.
- Document Asset Information: Create a comprehensive asset register that includes:
- Asset name and description.
- Asset classification.
- Asset owner.
- Location.
- Value.
- Recovery requirements.
This register serves as a central repository for asset information and is essential for developing effective recovery strategies.
- Implement Security Controls: Implement appropriate security controls based on the asset classification and sensitivity. This may include:
- Data encryption: Protects sensitive data from unauthorized access.
- Access controls: Restricts access to assets based on user roles and permissions.
- Data backups: Ensures data can be restored in case of a loss.
For example, a healthcare provider would implement strong encryption and access controls to protect patient data stored on servers.
Determining the Recovery Time Objective (RTO) and Recovery Point Objective (RPO) for Each Critical Function
Defining RTO and RPO is critical for establishing the acceptable downtime and data loss for each critical business function. These objectives guide the development of recovery strategies and the allocation of resources.
- Recovery Time Objective (RTO): The RTO defines the maximum acceptable downtime for a business function after a disruptive event. It is the time within which a system or function must be restored to prevent unacceptable consequences.
The RTO is determined by considering the MTD and the impact of downtime on the business. The RTO should be less than or equal to the MTD.
RTO ≤ MTD
For example, if the BIA determines that a critical order processing system can only be down for 4 hours before causing significant financial loss, the RTO for that system should be set at 4 hours or less.
- Recovery Point Objective (RPO): The RPO defines the maximum acceptable data loss for a business function. It is the point in time to which data must be recovered to resume operations.
The RPO is determined by considering the frequency of data backups and the acceptable data loss window. A shorter RPO implies more frequent backups and a greater investment in data protection technologies.
For example, if a company can tolerate the loss of one day’s worth of sales data, the RPO for its sales database would be 24 hours.
- Determine RTO and RPO for Each Critical Function: For each critical business function, analyze the BIA results and assess the potential impact of downtime and data loss.
- Financial Impact: Consider the potential revenue loss, increased expenses, and other financial consequences of downtime and data loss.
- Operational Impact: Assess the impact on business operations, customer service, and employee productivity.
- Reputational Impact: Evaluate the potential damage to the organization’s reputation and brand.
- Legal and Regulatory Requirements: Identify any legal or regulatory requirements that dictate the RTO and RPO.
For instance, a financial institution’s core banking system might have an RTO of minutes and an RPO of seconds due to the critical nature of its operations and the need to comply with strict regulatory requirements.
- Document RTO and RPO: Document the RTO and RPO for each critical business function in the BCP and DR plans. This documentation provides clear objectives for recovery efforts.
This information should be easily accessible to the recovery teams.
- Test and Validate RTO and RPO: Regularly test and validate the RTO and RPO to ensure that recovery strategies are effective and that the organization can meet its recovery objectives.
This includes conducting regular DR exercises and simulations to test the recovery processes and identify areas for improvement.
Risk Assessment and Business Impact Analysis (BIA)
Integrating Business Continuity Planning (BCP) with Disaster Recovery (DR) requires a thorough understanding of potential risks and their impact on business operations. This involves a systematic approach to identify vulnerabilities and assess the consequences of disruptions. The Risk Assessment and Business Impact Analysis (BIA) are crucial components of this process, providing the foundation for effective DR strategies.
Designing a Risk Assessment Framework to Identify Potential Threats and Vulnerabilities
A robust risk assessment framework systematically identifies potential threats and vulnerabilities that could disrupt business operations. This framework serves as a proactive measure to understand the potential impact of various events, enabling the development of targeted mitigation strategies.The risk assessment framework should encompass several key steps:
- Identification of Assets: This involves identifying all critical business assets, including physical infrastructure (e.g., servers, data centers), digital assets (e.g., data, applications), and intangible assets (e.g., reputation, intellectual property). This step is foundational, as all subsequent steps will relate to these assets.
- Threat Identification: Identify a comprehensive list of potential threats. Threats can be categorized into several types:
- Natural Disasters: Examples include hurricanes, earthquakes, floods, and wildfires.
- Human-Caused Threats: These include cyberattacks (e.g., ransomware, malware), data breaches, sabotage, and insider threats.
- Technical Failures: Hardware failures, software bugs, network outages, and power failures.
- Operational Disruptions: Supply chain disruptions, labor strikes, and pandemics.
- Vulnerability Analysis: Evaluate the vulnerabilities of each asset to the identified threats. A vulnerability is a weakness that a threat can exploit. For example, a server without adequate security patches is vulnerable to a cyberattack.
- Risk Analysis: Determine the likelihood of each threat occurring and the potential impact on the business. This involves assessing the probability of the threat and the severity of the consequences. Risk is often expressed as a function of likelihood and impact.
- Risk Prioritization: Prioritize risks based on their likelihood and impact. This helps focus resources on the most critical risks. A risk matrix, discussed later, is a valuable tool for this.
- Risk Mitigation Strategies: Develop strategies to reduce the likelihood and/or impact of each risk. This could involve implementing security controls, developing contingency plans, or purchasing insurance.
Organizing a BIA to Determine the Financial and Operational Impact of Different Scenarios
The Business Impact Analysis (BIA) determines the potential consequences of disruptions to critical business functions. It’s a vital component of BCP and DR, providing crucial information for developing recovery strategies and setting recovery time objectives (RTOs) and recovery point objectives (RPOs).The BIA process typically involves these steps:
- Identify Critical Business Functions: Determine which business functions are essential for the organization to operate. Examples include order processing, customer service, payroll, and manufacturing.
- Determine Maximum Tolerable Downtime (MTD): Establish the maximum amount of time a business function can be unavailable before causing irreparable damage to the organization. MTD is a critical factor in determining RTO.
- Assess Recovery Time Objective (RTO): Define the time within which a business function must be restored after a disruption. The RTO should be equal to or less than the MTD.
- Determine Recovery Point Objective (RPO): Specify the maximum acceptable data loss in the event of a disruption. This determines how frequently data needs to be backed up.
- Quantify Impact: Measure the financial and operational impact of a disruption to each business function. This includes direct costs (e.g., lost revenue, repair costs), indirect costs (e.g., reputational damage, decreased productivity), and other factors.
- Document Findings: Create a detailed report that summarizes the BIA findings, including critical functions, MTDs, RTOs, RPOs, and impact assessments.
Creating a Matrix to Correlate Risks with Potential Impacts on Business Functions
A risk matrix is a valuable tool for visualizing and prioritizing risks. It correlates identified risks with their potential impacts on business functions, facilitating effective decision-making regarding mitigation strategies.A typical risk matrix uses two dimensions:
- Likelihood: The probability of the risk occurring (e.g., low, medium, high).
- Impact: The severity of the consequences if the risk occurs (e.g., negligible, moderate, severe, critical).
The matrix is then divided into quadrants or zones, representing different levels of risk:
- Low Risk: Risks with low likelihood and low impact. These risks may require minimal attention.
- Medium Risk: Risks with either a moderate likelihood or a moderate impact. These risks should be monitored and may require some mitigation efforts.
- High Risk: Risks with either a high likelihood or a high impact. These risks require immediate attention and significant mitigation efforts.
- Critical Risk: Risks with both high likelihood and high impact. These risks are the highest priority and require the most comprehensive mitigation strategies.
The risk matrix allows for a clear visual representation of the risks, enabling organizations to:
- Prioritize risks based on their severity.
- Allocate resources effectively to mitigate the most critical risks.
- Communicate risk information clearly to stakeholders.
- Track the effectiveness of mitigation strategies.
For example, a company might identify a potential cyberattack as a high-risk event. The likelihood might be assessed as “medium” based on the increasing frequency of cyberattacks, and the impact might be assessed as “critical” due to potential data loss, regulatory fines, and reputational damage. This would place the cyberattack in the “high risk” or “critical risk” zone of the matrix, prompting the company to invest in robust cybersecurity measures.
Demonstrating How to Quantify the Impact of Disruptions (e.g., Financial Loss, Reputational Damage)
Quantifying the impact of disruptions is essential for making informed decisions about BCP and DR strategies. This involves estimating the financial, operational, and reputational consequences of various scenarios.Here’s how to quantify the impact of disruptions:
- Financial Loss: Calculate the financial impact of a disruption, including:
- Lost Revenue: Estimate the revenue lost during the downtime of critical business functions. This can be calculated by multiplying the average daily revenue by the duration of the downtime.
- Increased Costs: Identify and estimate any increased costs incurred due to the disruption, such as overtime pay, temporary staffing, and expedited shipping.
- Recovery Costs: Estimate the costs associated with restoring operations, including data recovery, equipment repair, and system upgrades.
- Fines and Penalties: Determine the potential fines and penalties for non-compliance with regulations, such as data privacy laws.
For example, if a company experiences a system outage that prevents it from processing orders for one day, and the average daily revenue is $100,000, the lost revenue would be $100,000. If recovery costs are estimated at $20,000, the total financial loss would be $120,000.
- Operational Impact: Assess the impact on operational efficiency and productivity. This can include:
- Decreased Productivity: Estimate the reduction in employee productivity due to the disruption.
- Supply Chain Disruptions: Analyze the impact on the supply chain, including delays in receiving raw materials or delivering finished products.
- Customer Service Disruptions: Assess the impact on customer service, such as delays in responding to inquiries or processing orders.
For instance, a manufacturing plant experiencing a power outage might see a 50% reduction in productivity for the duration of the outage.
- Reputational Damage: Evaluate the potential damage to the company’s reputation. This is often more difficult to quantify but can have significant long-term consequences. Consider:
- Loss of Customer Trust: Assess the potential for customers to lose trust in the company due to the disruption.
- Negative Media Coverage: Monitor media coverage and assess the potential for negative publicity.
- Damage to Brand Value: Estimate the potential impact on the company’s brand value.
Reputational damage can lead to a decrease in sales, a decline in stock value, and difficulty attracting new customers.
Quantifying the impact of disruptions is not an exact science, but it’s a crucial step in BCP and DR planning. By estimating the potential consequences of various scenarios, organizations can make informed decisions about the level of investment required to protect their critical assets and ensure business continuity.
Developing BCP Strategies
Developing robust Business Continuity Planning (BCP) strategies is crucial for ensuring business resilience in the face of disruptions. This involves formulating actionable plans to resume critical business functions and operations within a predefined timeframe. The effectiveness of these strategies directly impacts an organization’s ability to mitigate risks, minimize financial losses, and maintain its reputation. This section Artikels the key aspects of developing effective BCP strategies.
Strategies for Business Resumption
Strategies for business resumption focus on how an organization will recover and continue its critical operations after a disruption. These strategies are developed based on the business impact analysis (BIA) and risk assessment performed earlier. The goal is to provide a framework for quickly restoring essential functions, minimizing downtime, and ensuring business continuity.Here are some key considerations for developing effective business resumption strategies:
- Recovery Time Objective (RTO): Define the maximum acceptable downtime for each critical business function. This is a critical parameter for strategy selection. For example, if a function requires an RTO of 4 hours, the strategy must be capable of restoring that function within that timeframe.
- Recovery Point Objective (RPO): Determine the acceptable data loss for each critical business function. This informs the data backup and recovery strategy. An RPO of one hour means that the organization can afford to lose up to one hour’s worth of data.
- Resource Allocation: Identify and allocate the necessary resources, including personnel, equipment, infrastructure, and financial resources, to support the chosen strategies.
- Testing and Maintenance: Regularly test and maintain the strategies to ensure their effectiveness. This includes simulating disruptions and updating plans to reflect changes in the business environment.
Examples of BCP Strategies
Organizations can employ various BCP strategies, depending on their specific needs, risks, and resources. The selection of the most appropriate strategy depends on factors such as the criticality of the business function, the potential impact of the disruption, and the cost of implementing the strategy.Here are some common BCP strategies:
- Relocation: This strategy involves moving operations to an alternate location. This could be a pre-arranged backup site, a temporary facility, or even employees’ homes in the case of remote work. The effectiveness depends on the speed and efficiency of the relocation process. For example, a financial institution might have a dedicated backup office ready to be activated in case of a disaster at its primary location.
- Alternate Sites: This involves establishing agreements with other organizations or vendors to use their facilities in case of a disruption. This could include shared office space, data centers, or manufacturing facilities. The availability and compatibility of the alternate site are crucial factors.
- Hot Sites: These are fully equipped and immediately available backup facilities with all the necessary infrastructure, data, and applications to support critical business functions. They are the most expensive but offer the fastest recovery time.
- Warm Sites: These sites have the necessary infrastructure and basic IT equipment but may require some time to restore data and applications. They offer a balance between cost and recovery time.
- Cold Sites: These are basic facilities with only the necessary infrastructure. They require significant time to set up and configure the IT environment and restore data. They are the least expensive option but offer the slowest recovery time.
- Data Backup and Recovery: This strategy focuses on backing up critical data and ensuring its availability for recovery. This can involve on-site backups, off-site backups, cloud-based backups, and other data replication methods. The choice of method depends on the RPO and the criticality of the data.
- Virtualization: This involves virtualizing servers and applications, allowing them to be easily moved to a backup environment in case of a disruption. This can significantly reduce recovery time.
Creating Communication Plans and Notification Procedures
Effective communication is essential during a business disruption. A well-defined communication plan ensures that all stakeholders are informed promptly and accurately, minimizing confusion and facilitating a coordinated response. Notification procedures Artikel the steps for alerting employees, customers, vendors, and other relevant parties about the disruption and the actions they need to take.Here’s how to create effective communication plans and notification procedures:
- Identify Key Stakeholders: Determine all the individuals and groups that need to be informed during a disruption, including employees, customers, vendors, partners, regulatory bodies, and the media.
- Develop Communication Templates: Create pre-written templates for different types of disruptions and audiences. These templates should include key information such as the nature of the disruption, the impact on operations, the actions being taken, and contact information.
- Establish Communication Channels: Identify the communication channels that will be used to disseminate information, such as email, phone, text messages, social media, and internal communication platforms. Redundancy is crucial.
- Define Notification Procedures: Artikel the steps for notifying stakeholders, including who is responsible for sending notifications, the timing of notifications, and the frequency of updates.
- Test and Practice: Regularly test the communication plan and notification procedures to ensure they are effective. This includes simulating disruptions and practicing the communication process.
- Update Contact Information: Maintain up-to-date contact information for all stakeholders.
- Use Multiple Communication Methods: Employ a combination of communication methods to ensure information reaches all stakeholders, even if some channels are unavailable. For example, a company could send out an email and also post updates on social media.
Incorporating Remote Work and Cloud Solutions
Integrating remote work and cloud solutions into the BCP significantly enhances an organization’s resilience. These technologies enable businesses to maintain operations even when physical locations are inaccessible, offering flexibility and scalability.Here’s how to incorporate remote work and cloud solutions into the BCP:
- Remote Work Policies and Infrastructure: Develop clear policies and procedures for remote work, including guidelines for data security, communication, and performance management. Provide employees with the necessary equipment and access to company resources, such as laptops, secure internet access, and VPNs.
- Cloud-Based Solutions: Leverage cloud-based applications and services for critical business functions, such as email, collaboration tools, data storage, and business applications. Cloud solutions offer scalability, redundancy, and disaster recovery capabilities.
- Data Security and Access Control: Implement robust security measures to protect data and ensure that remote workers have secure access to company resources. This includes multi-factor authentication, data encryption, and access controls.
- Communication and Collaboration Tools: Provide remote workers with access to communication and collaboration tools, such as video conferencing, instant messaging, and project management software, to facilitate teamwork and communication.
- Testing and Training: Regularly test the remote work infrastructure and train employees on how to use remote work tools and follow security protocols.
- Consider Hybrid Work Models: A hybrid work model, combining remote and in-office work, can offer increased flexibility and resilience.
Developing DR Strategies
After assessing risks, analyzing business impacts, and formulating BCP strategies, the next crucial step is to develop robust Disaster Recovery (DR) strategies. These strategies ensure business operations can be restored quickly and efficiently following a disruptive event. Effective DR planning minimizes downtime, data loss, and the overall impact on business continuity.
Selecting DR Strategies Based on RTO and RPO
The selection of appropriate DR strategies is directly driven by the Recovery Time Objective (RTO) and the Recovery Point Objective (RPO) established during the Business Impact Analysis (BIA). The RTO defines the maximum acceptable downtime, while the RPO specifies the maximum acceptable data loss. These objectives guide the choice of DR solutions that align with the organization’s tolerance for disruption.The relationship between RTO/RPO and DR strategy selection can be summarized as follows:
- High RTO and High RPO: Organizations with a high tolerance for downtime and data loss often opt for less expensive DR strategies, such as cold sites. These sites require a longer recovery time, but they are cost-effective.
- Medium RTO and Medium RPO: Organizations seeking moderate recovery times and data loss levels may choose warm sites or data replication strategies. These options offer a balance between cost and recovery speed.
- Low RTO and Low RPO: Businesses that require minimal downtime and data loss typically invest in hot sites or real-time data replication. These strategies provide the fastest recovery but are the most expensive.
Examples of DR Strategies
Several DR strategies exist, each offering different levels of protection and cost implications. Choosing the right strategy depends on the organization’s specific needs and risk tolerance.
- Cold Site: A cold site is a basic facility that provides only the physical space, power, and cooling required to house IT infrastructure. No hardware or software is pre-installed. Recovery involves acquiring and configuring the necessary equipment, which can take days or weeks. This strategy is suitable for organizations with a high RTO and RPO. For example, a small non-profit organization might choose a cold site to keep costs low, accepting a longer recovery time.
- Warm Site: A warm site provides a partially configured environment with some hardware and software already installed. Data backups are typically stored offsite and can be restored more quickly than with a cold site. Recovery time is reduced, usually to hours or a few days. A retail business with multiple locations might use a warm site, ensuring a faster recovery than a cold site.
- Hot Site: A hot site is a fully functional environment with a complete replica of the primary production environment, including hardware, software, and real-time data replication. Recovery is almost instantaneous, minimizing downtime. This strategy is ideal for organizations that cannot tolerate significant downtime or data loss. For instance, a financial institution might employ a hot site to maintain critical services and protect sensitive financial data.
- Cloud-Based DR: Leveraging cloud services for DR offers flexibility and scalability. Cloud-based solutions can range from simple data backups to full-scale replication and failover. Organizations can select cloud-based DR based on their RTO/RPO requirements, often utilizing services such as Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), or Software-as-a-Service (SaaS).
Methods for Data Backup and Recovery Procedures
Effective data backup and recovery procedures are essential components of any DR strategy. The chosen method depends on the RTO and RPO.
- Full Backups: A full backup copies all data to a separate location. While providing the most complete data protection, full backups are time-consuming and require significant storage space. They are generally used as the base for incremental or differential backups.
- Incremental Backups: Incremental backups only copy data that has changed since the last backup, whether it was a full or incremental backup. This method is faster and uses less storage than full backups, but recovery requires the last full backup and all subsequent incremental backups.
- Differential Backups: Differential backups copy all data that has changed since the last full backup. This is faster than restoring from a full backup and all incremental backups, but slower and uses more storage than incremental backups.
- Data Replication: Data replication involves creating and maintaining an exact copy of data in a separate location, either synchronously or asynchronously. Synchronous replication provides the lowest RPO, while asynchronous replication is less expensive and suitable for higher RPOs.
- Backup Frequency: The frequency of backups should align with the RPO. More frequent backups are necessary for lower RPOs. For instance, a financial institution might require hourly or even more frequent backups to minimize potential data loss.
- Testing and Validation: Regular testing of backup and recovery procedures is crucial. This includes restoring data and verifying its integrity. Testing ensures that the DR plan functions as expected and identifies any issues before a real disaster occurs.
Integrating DR with Cloud-Based Services and Solutions
Cloud-based services offer various options for DR, providing flexibility, scalability, and cost-effectiveness. Integrating DR with cloud services often involves utilizing IaaS, PaaS, or SaaS solutions.
- Cloud-Based Backup and Recovery: Organizations can use cloud-based services for data backup and recovery. This can range from simple offsite backups to more sophisticated solutions that replicate data and applications to the cloud.
- Cloud-Based Replication: Cloud providers offer services for replicating data and applications to their infrastructure. This enables rapid failover to the cloud in the event of a disaster.
- Failover to the Cloud: In the event of a disaster, organizations can failover their IT infrastructure to the cloud. This can involve replicating the entire production environment or just critical applications.
- Cloud-Based DRaaS (Disaster Recovery as a Service): DRaaS providers offer comprehensive DR solutions, including backup, replication, and failover capabilities. They manage the entire DR process, reducing the burden on internal IT staff.
- Cost Considerations: When integrating DR with cloud services, organizations should consider the costs associated with data storage, bandwidth, and compute resources. Cloud providers offer various pricing models, and the optimal choice depends on the specific DR requirements and budget.
Integrating BCP and DR Plans
Integrating Business Continuity Planning (BCP) and Disaster Recovery (DR) plans is crucial for comprehensive organizational resilience. This integration ensures a coordinated response to disruptions, minimizing downtime and financial losses. Effective integration involves identifying overlaps, aligning strategies, maintaining consistent documentation, and incorporating incident response procedures.
Key Areas of Overlap Between BCP and DR Plans
BCP and DR plans share several critical areas that necessitate close coordination. These areas, when integrated, enhance the overall effectiveness of both plans.
- Risk Assessment and Business Impact Analysis (BIA): Both BCP and DR rely on the results of risk assessments and BIAs. The BIA identifies critical business functions and their recovery time objectives (RTOs) and recovery point objectives (RPOs), which inform both BCP and DR strategies. The risk assessment identifies potential threats and vulnerabilities, which are relevant to both planning efforts.
- Recovery Strategies: Both plans develop strategies to recover from disruptions. BCP focuses on maintaining business operations during an incident, while DR focuses on restoring IT infrastructure and data. These strategies must be aligned to ensure a seamless transition between business operations and IT recovery. For instance, a BCP strategy might involve manual workarounds, while the corresponding DR strategy might involve failover to a backup data center.
- Communication and Notification: Both plans include communication and notification procedures. A unified communication plan ensures that stakeholders are informed about the incident, the response actions, and the recovery progress. This consistency is vital for maintaining trust and minimizing confusion.
- Testing and Exercises: Regular testing and exercises are essential for validating both BCP and DR plans. Integrated testing, where both plans are tested simultaneously, provides a more comprehensive assessment of the organization’s resilience.
Procedure for Aligning BCP and DR Strategies
Aligning BCP and DR strategies requires a systematic approach to ensure that both plans complement each other. This process involves several key steps to guarantee a cohesive and effective response.
- Define Recovery Objectives: Clearly define the RTOs and RPOs for critical business functions and IT systems. This information, derived from the BIA, is fundamental to both BCP and DR planning.
- Identify Interdependencies: Map the dependencies between business functions and IT systems. Understand how business processes rely on IT infrastructure and data. For example, a manufacturing company might depend on its enterprise resource planning (ERP) system for production scheduling, inventory management, and supply chain operations.
- Develop Integrated Strategies: Develop strategies that address both business and IT recovery needs. BCP strategies might include manual workarounds, while DR strategies might include failover to backup systems or data replication. Ensure that these strategies are mutually supportive. For instance, a BCP strategy for order processing could involve manual order entry while the DR strategy focuses on restoring the order management system.
- Document and Communicate: Document the integrated strategies and communicate them to all relevant stakeholders. Ensure that all teams understand their roles and responsibilities during an incident.
- Test and Refine: Regularly test the integrated strategies and refine them based on the results of the tests. Conduct exercises that simulate different scenarios to validate the effectiveness of the plans.
Ensuring Consistency Between BCP and DR Documentation
Maintaining consistent documentation is critical for the successful integration of BCP and DR plans. Consistent documentation minimizes confusion and ensures that all stakeholders have access to the same information.
- Use a Common Template: Utilize a standardized template for both BCP and DR plans. This template should include common sections, such as incident response procedures, contact information, and recovery strategies.
- Centralized Repository: Store all BCP and DR documentation in a centralized, easily accessible repository. This ensures that all stakeholders have access to the latest versions of the plans. Cloud-based platforms or secure network drives are suitable options.
- Cross-Referencing: Cross-reference information between the BCP and DR plans. For example, if a BCP strategy refers to a specific IT system, the DR plan should include information about how that system will be recovered.
- Version Control: Implement version control to track changes to the plans. This ensures that stakeholders are using the correct version and can easily revert to previous versions if necessary.
- Regular Reviews: Conduct regular reviews of the documentation to ensure accuracy and relevance. Update the plans as needed to reflect changes in the business environment or IT infrastructure.
Integrating Incident Response Procedures into Both Plans
Integrating incident response procedures into both BCP and DR plans is essential for a coordinated and effective response to any disruption. This integration ensures that the organization can quickly and efficiently address incidents, regardless of their nature.
- Define Incident Types: Clearly define different types of incidents that could impact the organization. This includes natural disasters, cyberattacks, and equipment failures.
- Develop a Common Incident Response Team: Establish a common incident response team that is responsible for managing all types of incidents. This team should include representatives from both the business and IT departments.
- Establish Escalation Procedures: Define clear escalation procedures for reporting and escalating incidents. This ensures that incidents are addressed promptly and that the appropriate resources are mobilized.
- Create Communication Protocols: Develop communication protocols for notifying stakeholders about incidents. This includes internal communication, as well as communication with external parties, such as customers, vendors, and regulatory agencies.
- Integrate into Testing and Exercises: Integrate incident response procedures into testing and exercises. This provides an opportunity to validate the effectiveness of the procedures and identify areas for improvement. For instance, during a simulated cyberattack exercise, the incident response team could test their communication protocols, escalation procedures, and recovery strategies.
Documentation and Plan Development
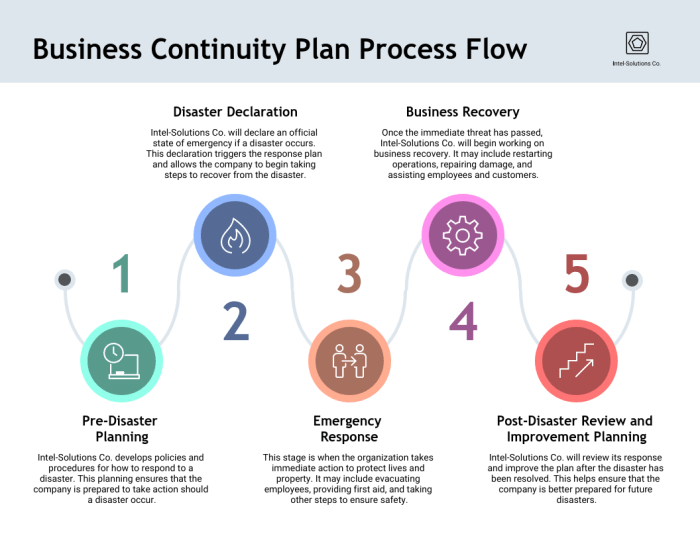
Effective documentation is the cornerstone of successful Business Continuity Planning (BCP) and Disaster Recovery (DR) efforts. Well-structured plans, readily accessible information, and clear communication protocols are crucial for ensuring a rapid and coordinated response during a disruptive event. This section focuses on creating a robust framework for documenting and developing both BCP and DR plans, facilitating efficient execution and minimizing downtime.
Designing a Comprehensive BCP and DR Plan Template
A standardized template provides a consistent framework for both BCP and DR plans, ensuring all essential elements are addressed. This promotes clarity, ease of use, and facilitates updates.The template should include the following key sections:
- Executive Summary: Provides a concise overview of the plan’s purpose, scope, and key strategies. It highlights the organization’s overall approach to business continuity and disaster recovery.
- Introduction: Artikels the plan’s objectives, scope, and the assumptions upon which it is based. It identifies the audience and provides context for the plan.
- Business Impact Analysis (BIA): Summarizes the BIA findings, including critical business functions, recovery time objectives (RTOs), and recovery point objectives (RPOs). This section informs the development of recovery strategies.
- Risk Assessment: Details the identified threats, vulnerabilities, and potential impacts. This section includes a risk register and mitigation strategies.
- BCP Strategies: Describes the proactive measures to prevent disruptions and the reactive steps to continue critical business functions during an event. This may include alternative work arrangements, data backup procedures, and communication protocols.
- DR Strategies: Artikels the procedures for restoring IT infrastructure, data, and applications following a disaster. This section includes details on failover procedures, data recovery processes, and system restoration timelines.
- Plan Activation and Escalation: Defines the triggers for activating the plan and the escalation procedures for notifying key personnel and stakeholders. It clarifies the roles and responsibilities during plan activation.
- Communication Plan: Specifies the communication channels, contact lists, and messaging templates for internal and external stakeholders. It ensures timely and accurate information dissemination.
- Training and Awareness: Details the training programs and awareness campaigns to educate employees about their roles and responsibilities. This promotes preparedness and reduces confusion during an event.
- Plan Maintenance and Testing: Describes the procedures for regularly reviewing, updating, and testing the plan to ensure its effectiveness. It includes schedules for plan reviews, drills, and simulations.
- Appendices: Contains supporting documentation such as contact lists, vendor agreements, data backup schedules, and site-specific information.
Organizing Key Sections in BCP and DR Plans
Organizing the key sections logically enhances the usability of both BCP and DR plans. A clear structure allows users to quickly locate the information they need during a crisis. The structure should follow a similar pattern for both plans, with variations based on their specific focus.The following structure is recommended:
- Plan Overview: Introduces the plan’s purpose, scope, objectives, and the audience.
- Business Impact Analysis (BIA) / IT Impact Analysis: Summarizes the impact of disruptions on business operations and IT infrastructure, respectively.
- Risk Assessment: Details identified risks, vulnerabilities, and mitigation strategies.
- Strategies and Procedures: Artikels the specific actions to be taken before, during, and after a disruption.
- Roles and Responsibilities: Defines the roles and responsibilities of individuals and teams involved in the plan.
- Communication Plan: Specifies the communication channels and protocols.
- Resource Requirements: Lists the resources needed to implement the plan, including personnel, equipment, and facilities.
- Plan Activation and Escalation: Describes the triggers for plan activation and the escalation procedures.
- Testing and Maintenance: Artikels the procedures for regularly testing and updating the plan.
- Appendices: Includes supporting documents such as contact lists, checklists, and SOPs.
Creating a Structure for Documenting Roles, Responsibilities, and Contact Information
A well-defined structure for documenting roles, responsibilities, and contact information is critical for effective communication and coordination during a crisis. This ensures that everyone knows their role and how to reach the right people quickly.A sample table format is recommended:
| Role | Responsibilities | Primary Contact | Secondary Contact | Contact Information |
|---|---|---|---|---|
| BCP Coordinator | Overseeing BCP development, maintenance, and testing; coordinating response efforts. | [Name] | [Name] | [Phone, Email, Alternate Contact] |
| DR Manager | Managing DR plan, leading recovery efforts, and coordinating with IT staff. | [Name] | [Name] | [Phone, Email, Alternate Contact] |
| IT Manager | Overseeing IT infrastructure recovery, data restoration, and system testing. | [Name] | [Name] | [Phone, Email, Alternate Contact] |
| Department Heads | Ensuring departmental preparedness, coordinating departmental response, and reporting status. | [Name] | [Name] | [Phone, Email, Alternate Contact] |
| Communication Lead | Disseminating information to internal and external stakeholders, managing media inquiries. | [Name] | [Name] | [Phone, Email, Alternate Contact] |
This table should be easily accessible and updated regularly to reflect any changes in personnel or contact information.
Demonstrating the Use of Checklists and Standard Operating Procedures (SOPs)
Checklists and SOPs are essential tools for ensuring consistency, accuracy, and efficiency during a BCP or DR event. They provide step-by-step instructions and reduce the risk of errors or omissions. Checklists provide a concise list of actions to be taken. For example, a checklist for data backup could include:
- Verify backup media is properly labeled.
- Initiate backup process according to schedule.
- Monitor backup progress.
- Review backup logs for errors.
- Store backup media in a secure offsite location.
SOPs provide detailed instructions on how to perform specific tasks. For example, an SOP for restoring a critical application could include:
- Objective: To restore the [Application Name] application from the most recent backup.
- Scope: Applies to all IT staff responsible for application recovery.
- Procedure:
- Identify the last known good backup.
- Verify the integrity of the backup data.
- Restore the application to the designated server.
- Test the application functionality.
- Notify stakeholders of the restoration.
- Roles and Responsibilities: IT Administrator.
- Tools and Equipment: Backup software, server access.
- Documentation: Restoration log.
Checklists and SOPs should be regularly reviewed and updated to reflect changes in technology, procedures, or personnel.
Testing and Exercising the Integrated Plan
Regular testing and exercising of your integrated Business Continuity Plan (BCP) and Disaster Recovery (DR) plan is crucial for ensuring its effectiveness. These activities validate the plan’s components, identify weaknesses, and confirm that the organization can recover critical business functions within acceptable timeframes. Effective testing provides valuable insights for plan refinement and enhances the overall resilience of the organization.
Types of Testing for BCP and DR Plans
Several testing methodologies are employed to evaluate the effectiveness of BCP and DR plans. Each approach offers a different level of rigor and focuses on specific aspects of the plan.
- Tabletop Exercises: These are discussion-based simulations where participants walk through the plan in a non-threatening environment. They involve key personnel discussing their roles and responsibilities, reviewing procedures, and addressing hypothetical scenarios. Tabletop exercises are cost-effective and excellent for familiarizing staff with the plan and identifying potential gaps in communication or coordination.
- Walkthrough Tests: These tests involve a step-by-step review of the plan, often conducted in a controlled setting. Participants physically walk through the procedures, verifying the accuracy and clarity of the instructions. Walkthrough tests help to identify any procedural inconsistencies or missing steps.
- Functional Tests: These tests focus on verifying the functionality of specific systems or applications. For example, a functional test might involve simulating a data center outage and verifying that the backup systems can successfully restore critical data and applications.
- Simulation Exercises: Simulations replicate real-world disaster scenarios as closely as possible. These exercises may involve activating recovery sites, deploying recovery teams, and restoring critical business functions. Simulations are more complex and resource-intensive than tabletop exercises but provide a more realistic assessment of the plan’s effectiveness. For instance, a simulation could involve a mock cyberattack, forcing teams to execute their incident response, data recovery, and business continuity protocols simultaneously.
- Full-Scale Exercises: These are the most comprehensive type of testing, involving the complete activation of the BCP and DR plans. Full-scale exercises often involve multiple departments and external stakeholders, such as vendors and regulatory agencies. They provide a complete assessment of the organization’s ability to recover from a major disruption.
Exercise Scenarios to Validate the Integrated Plan
Effective exercise scenarios should challenge the plan’s various components and assess the organization’s ability to respond to different types of disruptions. The scenarios should be realistic, relevant to the organization’s risk profile, and designed to test specific objectives.
- Scenario: Cyberattack on Primary Systems: Simulate a ransomware attack that encrypts critical business data and systems. This scenario would test the organization’s incident response plan, data backup and recovery procedures, and business continuity strategies. Teams would need to isolate infected systems, restore data from backups, and maintain essential business operations using alternative methods.
- Scenario: Natural Disaster Affecting Primary Site: Simulate a flood or earthquake that renders the primary office or data center inaccessible. This scenario would test the organization’s DR plan, including the activation of the recovery site, relocation of staff, and restoration of critical applications and data. It also assesses the business continuity plan’s ability to maintain essential functions with a reduced workforce and limited resources.
- Scenario: Supply Chain Disruption: Simulate a disruption in the supply of critical materials or services. This scenario would test the organization’s business continuity plan, including alternative sourcing strategies, inventory management, and communication with suppliers and customers. For example, the scenario could involve a fire at a key supplier’s factory, forcing the organization to find alternative sources for essential components.
- Scenario: Pandemic or Outbreak: Simulate a pandemic or widespread illness that results in a significant reduction in the workforce. This scenario would test the organization’s business continuity plan, including remote work policies, workforce management strategies, and communication protocols. This is especially important, considering the COVID-19 pandemic’s impact on businesses globally.
- Scenario: Human Error Causing Data Loss: Simulate a situation where a critical database is accidentally deleted or corrupted due to human error. This scenario would test the organization’s data backup and recovery procedures, as well as its incident response plan.
Methods for Conducting Regular Plan Reviews and Updates
Regular plan reviews and updates are essential for ensuring that the BCP and DR plans remain relevant and effective. The frequency of these reviews should be determined by the organization’s risk profile, the rate of change in its business environment, and any regulatory requirements.
- Annual Reviews: Conduct a comprehensive review of the BCP and DR plans at least annually. This review should involve all key stakeholders and assess the plan’s effectiveness, accuracy, and completeness.
- Post-Incident Reviews: After any actual incident or exercise, conduct a post-incident review to identify lessons learned and update the plan accordingly. This is crucial for incorporating real-world experiences and improving the plan’s responsiveness.
- Change Management: Establish a change management process to ensure that the plan is updated whenever there are significant changes to the organization’s business operations, IT infrastructure, or risk profile. This includes changes in personnel, new applications, or new regulations.
- Regular Testing and Exercises: Incorporate regular testing and exercises into the plan review process. These activities provide valuable feedback on the plan’s effectiveness and identify areas for improvement.
- Benchmarking: Compare the BCP and DR plans with industry best practices and standards. This can help identify areas where the organization can improve its resilience.
Importance of Documenting Test Results and Lessons Learned
Thorough documentation of test results and lessons learned is crucial for improving the BCP and DR plans and ensuring their ongoing effectiveness. This documentation provides a valuable record of the plan’s strengths and weaknesses, as well as insights for future improvements.
- Test Reports: Create detailed test reports that document the objectives of the test, the participants involved, the scenarios used, the results achieved, and any issues encountered.
- After-Action Reviews (AARs): Conduct AARs after each test or exercise to identify lessons learned and areas for improvement. These reviews should involve all participants and focus on what went well, what could have been done better, and what actions are needed to improve the plan.
- Corrective Action Plans: Develop corrective action plans to address any weaknesses or deficiencies identified during testing or exercises. These plans should include specific actions, timelines, and responsible parties.
- Plan Updates: Update the BCP and DR plans based on the results of testing, exercises, and AARs. This ensures that the plans remain current and reflect the organization’s evolving needs.
- Communication: Communicate the test results and lessons learned to all relevant stakeholders, including management, employees, and external partners. This promotes awareness of the organization’s resilience and fosters a culture of preparedness.
Technology and Infrastructure Considerations
Integrating technology and infrastructure considerations into Business Continuity Planning (BCP) and Disaster Recovery (DR) is crucial for ensuring business resilience. A robust technology strategy enables organizations to recover quickly from disruptions, minimizing downtime and financial losses. This section explores key aspects of incorporating technology into your BCP and DR plans.
Incorporating Cloud Computing and Virtualization into BCP and DR
Cloud computing and virtualization offer significant advantages for BCP and DR. They provide flexibility, scalability, and cost-effectiveness, allowing organizations to protect critical data and applications more efficiently.
- Cloud-Based Backup and Recovery: Cloud platforms offer readily available backup and recovery solutions. This includes features such as automated backups, data replication, and rapid failover capabilities. This approach minimizes the need for on-premises hardware and reduces the time required for recovery. For instance, a retail company might use a cloud provider to back up its point-of-sale (POS) system data daily. In the event of a local server failure, the company can quickly restore its POS system from the cloud, minimizing disruption to customer service.
- Virtualization for Rapid Recovery: Virtualization allows organizations to create virtual machines (VMs) that can be easily replicated and restored. In a disaster scenario, VMs can be quickly deployed on alternative hardware or in the cloud, minimizing downtime. A healthcare provider could virtualize its patient record system. If a server in a primary data center fails, the provider can quickly activate a replica of the VM in a secondary data center or the cloud, ensuring continued access to patient data.
- Scalability and Flexibility: Cloud environments offer scalability, allowing organizations to adjust resources (computing power, storage) as needed. This is particularly useful during a disaster when increased capacity may be required to handle increased workloads or accommodate a surge in demand. A financial services firm could use cloud resources to handle a sudden increase in online trading activity during a market crisis.
- Cost-Effectiveness: Cloud services often offer a pay-as-you-go model, reducing the need for large upfront investments in hardware and infrastructure. This can significantly lower the overall cost of BCP and DR. A small business might opt for cloud-based services for email, file storage, and basic applications, reducing the need to maintain its own IT infrastructure and lowering operational costs.
Procedure for Securing Data and Systems During a Disaster
Securing data and systems during a disaster is paramount to maintaining confidentiality, integrity, and availability. A comprehensive security plan should address various threats and vulnerabilities.
- Data Encryption: Encrypt sensitive data both in transit and at rest. Encryption ensures that even if data is compromised, it remains unreadable without the proper decryption keys. A bank, for example, encrypts all customer financial data stored on servers and in transit across its network to protect against unauthorized access.
- Access Control and Authentication: Implement strong access controls, including multi-factor authentication (MFA), to restrict access to critical systems and data. Regularly review and update user access privileges. A government agency uses MFA for all employees accessing classified information. This requires users to provide a password and a second form of verification, such as a one-time code from a mobile device.
- Network Segmentation: Segment the network to isolate critical systems and data from less critical areas. This limits the impact of a security breach. A manufacturing company segments its network, separating its industrial control systems (ICS) from its corporate network. This helps prevent malware that infects the corporate network from spreading to the ICS, which could disrupt production.
- Regular Security Audits and Vulnerability Assessments: Conduct regular security audits and vulnerability assessments to identify and address weaknesses in the security posture. This includes penetration testing and vulnerability scanning. A retail chain performs quarterly penetration testing to identify vulnerabilities in its online payment systems. This helps to detect and remediate security flaws before they can be exploited by attackers.
- Incident Response Plan: Develop and regularly test an incident response plan that Artikels the steps to be taken in the event of a security breach or disaster. This plan should include procedures for containment, eradication, and recovery. A hospital has an incident response plan that specifies how to respond to a ransomware attack. The plan includes steps for isolating infected systems, notifying relevant authorities, and restoring data from backups.
Role of Network Infrastructure and Connectivity in Business Continuity
Network infrastructure and reliable connectivity are the backbone of business continuity. A robust network ensures that critical applications and data remain accessible, even during a disruption.
- Redundant Network Infrastructure: Implement redundant network components, such as routers, switches, and internet connections, to provide failover capabilities. This ensures that if one component fails, another can take over seamlessly. A telecommunications company uses redundant fiber optic cables and multiple internet service providers (ISPs) to ensure continuous network availability.
- Network Monitoring and Management: Implement robust network monitoring and management tools to proactively identify and address network issues. This includes monitoring bandwidth usage, latency, and other performance metrics. A logistics company uses network monitoring tools to track the performance of its network during peak shipping seasons.
- Wide Area Network (WAN) Optimization: Optimize WAN performance to ensure efficient data transfer between different locations, especially during a disaster when network congestion may occur. A multinational corporation uses WAN optimization techniques to improve the performance of its applications and data transfer between its offices worldwide.
- Secure Remote Access: Provide secure remote access solutions, such as virtual private networks (VPNs), to allow employees to access critical systems and data from remote locations. This is crucial for maintaining business operations during a disaster. A financial institution uses VPNs to enable employees to work from home during a severe weather event, allowing them to continue providing customer service.
- Wireless Connectivity: Ensure reliable wireless connectivity throughout the organization, including backup wireless options. This enables employees to maintain access to critical resources even if wired connections are unavailable. A university campus provides Wi-Fi coverage throughout its buildings and outdoor areas.
Considerations for Selecting and Implementing Backup and Recovery Solutions
Selecting and implementing the right backup and recovery solutions is critical for data protection and rapid recovery. Careful consideration of various factors is essential.
- Recovery Time Objective (RTO) and Recovery Point Objective (RPO): Define RTO and RPO based on business requirements. RTO is the maximum acceptable downtime, and RPO is the maximum acceptable data loss. For example, a critical financial system might have an RTO of minutes and an RPO of seconds, requiring real-time replication.
- Backup Types: Choose appropriate backup types, such as full, incremental, and differential backups, based on RTO and RPO requirements. Full backups are time-consuming but provide the most complete recovery. Incremental backups are faster but require restoring the last full backup and all subsequent incremental backups. A company that needs to restore its data within an hour might use a combination of full and incremental backups.
- Backup Media and Storage: Select appropriate backup media and storage solutions, such as tape, disk, and cloud storage. Consider the cost, capacity, and durability of each option. An archive library might use tape for long-term, cost-effective storage of infrequently accessed data.
- Offsite Data Storage: Store backup data offsite to protect against physical disasters that could affect the primary data center. This could involve using a remote data center or a cloud-based backup service. A hospital stores its backups in a geographically separate data center to protect against natural disasters.
- Regular Testing and Validation: Regularly test and validate backup and recovery processes to ensure they function correctly. This includes simulating disaster scenarios and restoring data. A manufacturing plant regularly tests its disaster recovery plan by restoring critical data from backups to ensure its ability to resume operations quickly.
Legal and Regulatory Compliance
Integrating Business Continuity Planning (BCP) and Disaster Recovery (DR) requires a thorough understanding of legal and regulatory obligations. Organizations must ensure their plans align with industry-specific requirements to avoid penalties, maintain customer trust, and protect their operations. This section details the legal and regulatory considerations essential for robust BCP and DR strategies.
Legal and Regulatory Requirements Across Industries
Organizations must navigate a complex landscape of legal and regulatory requirements. These requirements dictate how businesses handle data, protect sensitive information, and maintain operational resilience. Failure to comply can result in severe consequences, including financial penalties, legal action, and reputational damage.
- Financial Services: The financial sector faces stringent regulations such as the Gramm-Leach-Bliley Act (GLBA) in the United States and the Payment Card Industry Data Security Standard (PCI DSS). These regulations mandate robust data security, incident response plans, and business continuity measures to protect customer financial information. For example, a bank must have a comprehensive BCP to ensure it can continue processing transactions and providing services even during a major disruption, such as a natural disaster or cyberattack.
- Healthcare: The Health Insurance Portability and Accountability Act (HIPAA) in the United States establishes regulations for protecting patient health information (PHI). Healthcare providers and business associates must implement BCP and DR plans that ensure the confidentiality, integrity, and availability of PHI. A hospital, for instance, must have backup systems and procedures to maintain access to patient records and critical medical devices during a power outage.
- Government: Government agencies are subject to various regulations, including the Federal Information Security Management Act (FISMA) in the United States. FISMA requires federal agencies to develop and implement information security programs, including BCP and DR plans, to protect government data and systems.
- Manufacturing: Manufacturing companies must adhere to industry-specific standards, such as those set by the International Organization for Standardization (ISO), and often face regulations related to environmental protection and worker safety. A manufacturing plant must have a BCP to ensure the continuity of production and protect critical infrastructure.
- Retail: Retail businesses must comply with PCI DSS to protect customer payment card information. They also must have plans for inventory management, supply chain disruptions, and data breaches. A retail chain, for example, must ensure its point-of-sale systems are secure and that customer data is protected during a disaster.
- Telecommunications: Telecommunications companies are subject to regulations regarding network reliability and customer service. They must implement BCP and DR plans to maintain service availability during outages and other disruptions. A telecommunications provider must have redundant systems and backup power to ensure its network remains operational during a major event.
- Data Privacy: Organizations that handle the personal data of individuals within the European Union must comply with the General Data Protection Regulation (GDPR). GDPR mandates strict requirements for data security, breach notification, and data subject rights. A company operating in the EU must have a BCP and DR plan that incorporates GDPR requirements to ensure data privacy and security during a disaster.
Industry-Specific Compliance Standards: Examples
Various industry-specific standards are essential for organizations to meet legal and regulatory requirements. These standards provide a framework for implementing BCP and DR plans, ensuring compliance, and mitigating risks.
- HIPAA (Health Insurance Portability and Accountability Act): HIPAA sets standards for protecting the privacy and security of Protected Health Information (PHI). Covered entities (healthcare providers, health plans, and healthcare clearinghouses) and their business associates must implement administrative, physical, and technical safeguards to ensure the confidentiality, integrity, and availability of PHI. A healthcare provider must have a BCP that includes data backup and recovery, offsite storage, and procedures for handling data breaches.
- GDPR (General Data Protection Regulation): GDPR regulates the processing of personal data of individuals within the EU. Organizations must implement measures to protect data privacy, including data encryption, access controls, and breach notification procedures. A company must have a BCP that incorporates GDPR requirements, such as data backup and recovery, to ensure data privacy and security during a disaster.
- PCI DSS (Payment Card Industry Data Security Standard): PCI DSS sets standards for protecting cardholder data. Organizations that process, store, or transmit cardholder data must comply with PCI DSS requirements, including implementing security measures, conducting vulnerability assessments, and maintaining a robust BCP. A retail business must have a BCP that addresses the security of payment card data during a disaster.
- GLBA (Gramm-Leach-Bliley Act): GLBA requires financial institutions to protect customer financial information. Financial institutions must implement security measures to protect customer data, including developing a BCP and DR plan. A bank must have a BCP to ensure it can continue to provide financial services and protect customer data during a disruption.
- ISO 27001 (Information Security Management System): ISO 27001 is an international standard for information security management. It provides a framework for establishing, implementing, maintaining, and continually improving an information security management system (ISMS). Organizations can use ISO 27001 to develop their BCP and DR plans.
Methods for Ensuring Data Privacy and Security During a Disaster
Maintaining data privacy and security during a disaster is critical for regulatory compliance and protecting customer trust. Implementing specific methods can help organizations safeguard their data and mitigate the impact of disruptions.
- Data Encryption: Encrypting data both at rest and in transit protects sensitive information from unauthorized access. This ensures that even if data is compromised, it remains unreadable.
- Data Backup and Recovery: Regularly backing up data to offsite locations is essential for ensuring data availability during a disaster. Organizations should have a comprehensive data recovery plan that includes procedures for restoring data quickly and efficiently.
- Access Controls: Implementing strong access controls limits who can access sensitive data. This includes using strong passwords, multi-factor authentication, and role-based access control.
- Data Loss Prevention (DLP): DLP tools help prevent sensitive data from leaving the organization’s control. These tools monitor data in use, in motion, and at rest and can block or alert on unauthorized data transfers.
- Incident Response Plan: A well-defined incident response plan Artikels the steps to be taken in the event of a data breach or security incident. This includes procedures for containment, eradication, recovery, and notification.
- Regular Security Audits and Assessments: Conducting regular security audits and assessments helps identify vulnerabilities and ensure that security measures are effective. This includes penetration testing, vulnerability scanning, and compliance audits.
- Employee Training: Training employees on data privacy and security best practices is essential for creating a security-conscious culture. Employees should be trained on topics such as phishing awareness, password security, and data handling procedures.
The Importance of Legal Counsel in BCP and DR Planning
Involving legal counsel in the BCP and DR planning process is essential for ensuring compliance, mitigating legal risks, and protecting the organization. Legal counsel can provide valuable expertise and guidance throughout the planning process.
- Compliance Review: Legal counsel can review the BCP and DR plans to ensure they comply with all relevant laws and regulations. They can identify potential legal risks and recommend measures to mitigate them.
- Contractual Obligations: Legal counsel can review contracts with vendors and third-party providers to ensure that BCP and DR requirements are met. They can also help negotiate contracts that include appropriate disaster recovery provisions.
- Data Privacy and Security: Legal counsel can advise on data privacy and security requirements, including GDPR, HIPAA, and PCI DSS. They can help develop data breach response plans and ensure compliance with data protection laws.
- Incident Response: Legal counsel can provide guidance during a disaster or security incident, including advising on legal obligations, notification requirements, and communications strategies.
- Risk Management: Legal counsel can help identify and assess legal risks associated with BCP and DR. They can provide recommendations for mitigating these risks and protecting the organization.
- Insurance Coverage: Legal counsel can review insurance policies to ensure adequate coverage for business interruption, data loss, and other disaster-related events.
Budgeting and Resource Allocation
Effective budgeting and resource allocation are crucial for successful Business Continuity Planning (BCP) and Disaster Recovery (DR) implementation. Without adequate financial and human resources, even the most meticulously crafted plans can fail. This section Artikels a structured approach to estimating costs, securing budget approval, allocating resources, and justifying the investment in BCP and DR initiatives.
Framework for Estimating BCP and DR Costs
Establishing a robust framework is essential for accurately estimating the financial implications of BCP and DR. This involves a detailed analysis of all associated costs, categorized for clarity and efficient tracking.
- Initial Investment Costs: These are one-time expenses incurred during the initial setup phase. They include:
- Technology Infrastructure: This encompasses hardware, software, and cloud services necessary for data backup, replication, and failover. For example, consider the cost of purchasing new servers, storage devices, and implementing virtualization software.
- Consulting Fees: Costs associated with engaging external consultants for BCP and DR plan development, risk assessment, and training. These fees can vary significantly based on the consultant’s expertise and the complexity of the project.
- Software Licenses: The price of acquiring and maintaining software licenses required for data backup, recovery, and business continuity operations. Consider the cost of acquiring data replication tools or specialized recovery software.
- Office Space/Alternate Sites: Expenses related to securing alternate office locations or data centers for business operations during a disaster. Consider the cost of leasing space or establishing agreements with co-location facilities.
- Training and Awareness Programs: Costs associated with providing training to employees on BCP and DR procedures, including workshops, seminars, and online courses.
- Ongoing Operational Costs: These are recurring expenses necessary to maintain and update BCP and DR plans.
- Maintenance and Support Contracts: Costs associated with maintaining hardware, software, and infrastructure, including vendor support agreements.
- Data Backup and Storage Costs: Expenses related to backing up data, including storage media, cloud storage fees, and offsite storage solutions.
- Testing and Exercising Costs: Costs incurred during regular testing and exercising of the BCP and DR plans, including personnel time, facility usage, and travel expenses.
- Insurance Premiums: Costs associated with business interruption insurance and other relevant insurance policies.
- Personnel Costs: Salaries and benefits for employees dedicated to BCP and DR activities, including plan development, testing, and execution.
- Contingency Planning: Setting aside a contingency fund to cover unexpected expenses. This fund should be a percentage of the total estimated costs, typically ranging from 10% to 20%, depending on the organization’s risk profile.
Organizing Budget Approval for BCP and DR Initiatives
Securing budget approval requires a well-structured approach, including a clear justification for the investment and a persuasive presentation to stakeholders.
- Develop a Comprehensive Business Case: This document should clearly articulate the need for BCP and DR, outlining potential risks, the impact of downtime, and the benefits of investing in resilience.
- Quantify Potential Losses: Estimate the financial impact of various disaster scenarios, including revenue loss, operational expenses, and reputational damage.
- Present Return on Investment (ROI) Analysis: Demonstrate the financial benefits of BCP and DR, such as reduced downtime, minimized losses, and improved customer satisfaction.
- Include a Detailed Budget Proposal: Provide a breakdown of all estimated costs, including initial investment and ongoing operational expenses.
- Identify Key Stakeholders: Determine who needs to approve the budget, typically including senior management, the Chief Financial Officer (CFO), and relevant department heads.
- Tailor the Presentation: Adapt the business case and presentation to the specific concerns and priorities of each stakeholder. Highlight the benefits most relevant to their area of responsibility. For example, the CFO will be interested in financial impact, while the CEO will be focused on overall business strategy and risk mitigation.
- Seek Early Support: Engage with key stakeholders early in the process to gather feedback and address any concerns before the formal budget presentation.
- Present Clear Metrics: Define key performance indicators (KPIs) to measure the effectiveness of the BCP and DR plan, such as recovery time objective (RTO), recovery point objective (RPO), and downtime reduction.
Structure for Allocating Resources to Support BCP and DR Activities
Effective resource allocation is critical for ensuring that the BCP and DR plan is implemented, maintained, and tested properly. This includes both financial and human resources.
- Establish a Dedicated BCP/DR Team: Designate a team or individuals responsible for BCP and DR activities. This team should have clear roles, responsibilities, and reporting lines.
- Team Composition: The team should include representatives from various departments, such as IT, operations, finance, and legal.
- Roles and Responsibilities: Clearly define each team member’s responsibilities, including plan development, testing, training, and incident response.
- Allocate Budget for Training and Education: Invest in training programs to equip the BCP/DR team and other employees with the necessary skills and knowledge.
- Invest in Technology and Infrastructure: Allocate budget for technology and infrastructure that supports BCP and DR, such as data backup and recovery systems, redundant servers, and offsite storage.
- Implement Regular Testing and Exercises: Allocate resources for regular testing and exercising of the BCP and DR plan. This includes personnel time, facility usage, and travel expenses.
- Testing Frequency: Establish a schedule for testing the BCP and DR plan, including tabletop exercises, functional tests, and full-scale simulations.
- Monitor and Review Resource Allocation: Regularly monitor the allocation of resources to ensure they are adequate and effective. Adjust the allocation as needed based on changing business needs and risk profiles.
Demonstrating Justification for Investment in Business Continuity and Disaster Recovery
Justifying the investment in BCP and DR requires demonstrating its value to stakeholders. This involves quantifying the benefits and presenting a compelling case for the investment.
- Quantify Potential Losses: Estimate the financial impact of potential disasters, including revenue loss, operational expenses, and reputational damage.
For example, according to the Disaster Recovery Preparedness Benchmark Report by Databarracks, the average cost of downtime for businesses is $10,000 per hour. This demonstrates the significant financial impact of IT failures and the importance of investing in DR.
- Present Return on Investment (ROI) Analysis: Demonstrate the financial benefits of BCP and DR, such as reduced downtime, minimized losses, and improved customer satisfaction.
The ROI can be calculated by comparing the cost of implementing and maintaining the BCP/DR plan to the potential losses avoided due to reduced downtime and improved resilience.
- Highlight Regulatory Compliance: Emphasize the importance of BCP and DR for meeting regulatory requirements, such as those Artikeld by the Sarbanes-Oxley Act (SOX) or the Health Insurance Portability and Accountability Act (HIPAA). Non-compliance can result in significant fines and penalties.
- Improve Customer Satisfaction and Retention: BCP and DR can improve customer satisfaction by ensuring continued service availability during disruptions. This can lead to increased customer loyalty and retention.
- Protect Brand Reputation: A well-executed BCP and DR plan can help protect the organization’s brand reputation by minimizing the impact of disruptions and demonstrating a commitment to customer service.
- Enhance Business Resilience: BCP and DR improve the overall resilience of the business, enabling it to recover quickly from disruptions and maintain operations.
Final Review
Integrating BCP and DR is a journey, not a destination. By understanding the key areas of overlap, aligning your strategies, and consistently testing your plans, you can create a truly resilient organization. This guide equips you with the knowledge and tools to build a comprehensive, adaptable framework that protects your business from disruptions, ensuring its continued success. Remember, preparedness is the cornerstone of survival and prosperity in an uncertain world.
Question & Answer Hub
What is the primary difference between BCP and DR?
BCP focuses on keeping a business running during a disruption, while DR focuses on restoring IT systems and data after a disaster.
How often should we test our integrated BCP and DR plan?
Regular testing, at least annually, is crucial. More frequent testing, especially after significant changes, is recommended to ensure plan effectiveness.
What are the key components of a good communication plan?
A communication plan should include contact information for key personnel, notification procedures, and methods for keeping stakeholders informed during a crisis.
How can cloud solutions enhance BCP and DR?
Cloud solutions offer data backup, offsite storage, and the ability to quickly restore operations in the event of a disaster, providing flexibility and scalability.
What is the role of legal counsel in BCP and DR planning?
Legal counsel ensures compliance with regulations, helps address liability issues, and provides guidance on data privacy and security.