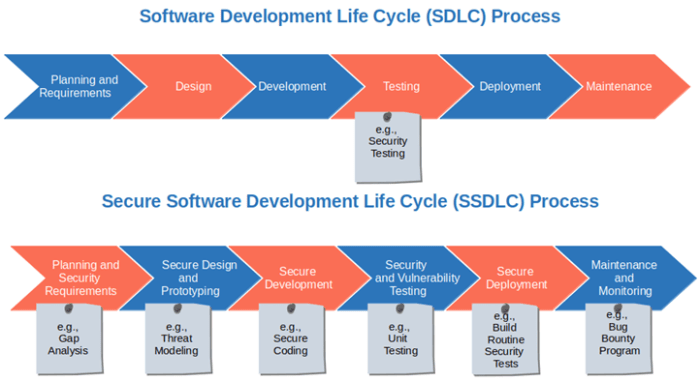
Embarking on the journey of how to implement a secure software development life cycle (SDLC) is crucial in today’s digital landscape. This isn’t just about writing code; it’s about building a fortress, a secure foundation for your software that protects against vulnerabilities and ensures trust. We’ll explore the key phases, from initial planning to ongoing maintenance, and equip you with the knowledge to create robust, secure applications.
The SDLC is a structured process, and integrating security at every stage is paramount. By understanding the principles of secure design, implementation, testing, and deployment, you can significantly reduce the risk of security breaches. This guide provides a roadmap, offering practical strategies, tools, and best practices to help you build secure software from the ground up, protecting your users and your business.
Introduction to Secure SDLC
Implementing a Secure Software Development Life Cycle (SDLC) is crucial for building robust and trustworthy software. It integrates security practices throughout the entire development process, minimizing vulnerabilities and protecting against threats. This approach ensures that security is not an afterthought but a fundamental aspect of software creation, leading to more reliable and secure applications.
Core Principles of a Secure SDLC
The core principles of a Secure SDLC revolve around proactive security measures embedded throughout the development lifecycle. These principles aim to address vulnerabilities early and continuously.
- Security by Design: Security considerations are integrated into the initial design phases. This includes threat modeling, security architecture design, and the selection of secure technologies and frameworks. By considering security from the outset, developers can proactively mitigate potential risks.
- Threat Modeling: This involves identifying potential threats, vulnerabilities, and attack vectors. It helps prioritize security efforts and guides the development of appropriate countermeasures. The STRIDE model (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege) is a common framework for threat modeling.
- Secure Coding Practices: Developers are trained in secure coding techniques to prevent common vulnerabilities such as SQL injection, cross-site scripting (XSS), and buffer overflows. This includes adhering to coding standards, using secure libraries, and performing code reviews.
- Security Testing: Comprehensive testing is performed throughout the SDLC to identify and address security flaws. This includes static analysis (SAST), dynamic analysis (DAST), penetration testing, and fuzzing.
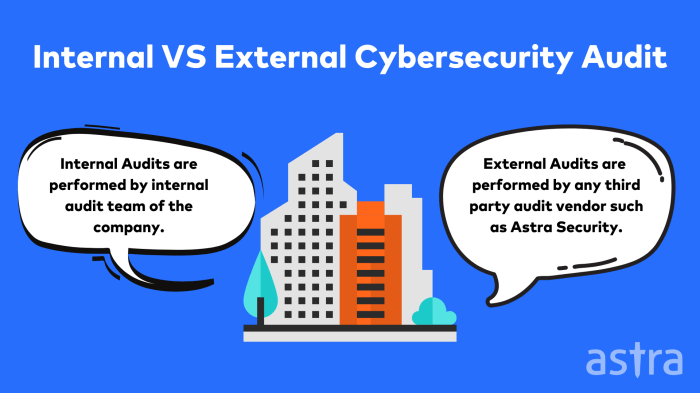
- Security Auditing: Regular security audits are conducted to assess the effectiveness of security controls and identify areas for improvement. These audits may be internal or performed by third-party security experts.
- Continuous Monitoring: Ongoing monitoring of the software in production is essential to detect and respond to security incidents. This includes logging, intrusion detection, and vulnerability scanning.
Definition and Importance of SDLC
The Software Development Life Cycle (SDLC) is a structured approach to planning, designing, developing, testing, and deploying software. Its importance lies in providing a framework for managing the entire software development process, ensuring consistency, quality, and efficiency.
The SDLC is a systematic process for creating and maintaining software applications. It defines the stages involved, the deliverables at each stage, and the roles and responsibilities of the development team.
The SDLC’s structured approach helps organizations to:
- Improve Quality: By following a defined process, organizations can ensure that software meets quality standards and user requirements.
- Reduce Costs: A well-defined SDLC can help to reduce development costs by minimizing errors, rework, and delays.
- Enhance Security: Integrating security practices throughout the SDLC helps to identify and address vulnerabilities early, leading to more secure software.
- Increase Efficiency: The SDLC promotes efficiency by streamlining the development process and facilitating communication and collaboration among team members.
- Ensure Maintainability: The SDLC ensures that software is designed and developed in a way that makes it easy to maintain and update.
Benefits of Implementing a Secure SDLC
Implementing a Secure SDLC offers numerous benefits that extend beyond just improved security. It impacts various aspects of software development and the overall business.
- Reduced Security Vulnerabilities: Integrating security practices early in the development process significantly reduces the number of security vulnerabilities in the final product.
- Lower Development Costs: Addressing security issues early is far less expensive than fixing them later. A Secure SDLC helps to prevent costly rework and emergency patches.
- Improved Compliance: Many industries and regulatory bodies require specific security measures. A Secure SDLC helps organizations meet these compliance requirements, such as GDPR, HIPAA, and PCI DSS.
- Enhanced Customer Trust: Building secure software increases customer trust and confidence in the organization. This is particularly important in industries where data security is paramount.
- Faster Time to Market: While it might seem counterintuitive, a well-implemented Secure SDLC can actually speed up the development process by preventing costly delays caused by security breaches or vulnerabilities found late in the cycle.
- Improved Team Collaboration: A Secure SDLC fosters better communication and collaboration between development, security, and operations teams.
- Protection of Intellectual Property: Secure SDLC practices help protect the organization’s intellectual property by preventing unauthorized access to code and sensitive information.
Planning and Requirements Phase Security
The planning and requirements phase is the foundational stage for building secure software. Neglecting security considerations here can lead to significant vulnerabilities later in the SDLC, increasing costs and risks. Integrating security from the outset ensures that security is not an afterthought but an integral part of the software’s design and functionality. This proactive approach significantly reduces the likelihood of costly rework and security breaches.
Incorporating Security Considerations During the Planning Phase
During the planning phase, security should be a core component of project initiation. This involves several key activities.
- Defining Security Goals: Clearly articulate the security objectives of the software. This includes identifying the assets to be protected (data, systems, reputation), the threats it faces, and the desired security posture. For example, if the software handles sensitive financial data, the security goals would prioritize confidentiality, integrity, and availability.
- Identifying Security Requirements: Translate the security goals into specific, measurable, achievable, relevant, and time-bound (SMART) security requirements. These requirements should be documented and used to guide all subsequent development activities. Examples include: “All user passwords must be stored using strong hashing algorithms with salting” or “The system must be able to withstand a denial-of-service attack of up to 1000 requests per second.”
- Establishing Security Policies and Standards: Develop and adopt relevant security policies and standards. These provide a framework for secure development practices, covering areas such as coding standards, access control, data encryption, and incident response. These standards should align with industry best practices and regulatory requirements, such as those Artikeld by OWASP or NIST.
- Selecting Security Technologies and Tools: Identify the security technologies and tools that will be used throughout the SDLC. This may include static and dynamic analysis tools, penetration testing tools, and security libraries. The selection should be based on the project’s specific needs and the threats it faces.
- Defining Roles and Responsibilities: Clearly define the roles and responsibilities for security within the development team. This ensures accountability and facilitates effective collaboration. For example, a security architect might be responsible for designing the security architecture, while developers are responsible for implementing secure coding practices.
Role of Threat Modeling in Identifying Potential Vulnerabilities
Threat modeling is a proactive security technique used to identify, analyze, and mitigate potential threats to a system. It involves systematically evaluating a system’s design to understand how it might be attacked and what can be done to prevent or mitigate those attacks. This process helps identify vulnerabilities early in the SDLC, when they are easiest and least expensive to fix.
- Process Overview: The threat modeling process typically involves these steps:
- Define the Scope: Identify the system or component being analyzed.
- Gather Information: Collect details about the system’s architecture, data flows, and trust boundaries.
- Identify Threats: Use frameworks like STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege) or PASTA (Process for Attack Simulation and Threat Analysis) to identify potential threats.
- Analyze Threats: Assess the likelihood and impact of each threat.
- Develop Mitigations: Design and implement security controls to address the identified threats.
- Document and Track: Document the threat model and track the status of mitigations.
- Benefits of Threat Modeling: Threat modeling provides several benefits:
- Early Vulnerability Detection: Helps identify vulnerabilities before code is written, reducing the cost of remediation.
- Improved Security Design: Drives the development of more secure systems by considering security from the outset.
- Reduced Risk: Minimizes the likelihood of successful attacks by proactively addressing potential threats.
- Enhanced Communication: Facilitates communication about security risks among stakeholders.
- Compliance: Supports compliance with security regulations and standards.
- Example: Consider a web application that allows users to upload files. A threat model might identify the threat of malicious file uploads. The analysis would assess the likelihood of this threat (e.g., based on the application’s popularity and the attackers’ motivations) and the impact (e.g., data breaches, system compromise). The mitigation would involve implementing security controls such as file type validation, size limits, and malware scanning.
Security Requirements Gathering Techniques
Effective security requirements gathering is crucial for building secure software. Various techniques can be employed to elicit these requirements from stakeholders.
| Technique | Description | Benefits | Considerations |
|---|---|---|---|
| Stakeholder Interviews | Conducting structured interviews with stakeholders (users, developers, security experts, business owners) to gather their security needs and concerns. | Provides in-depth understanding of specific needs, allows for clarification and follow-up questions, and fosters collaboration. | Time-consuming; requires skilled interviewers; may be biased by individual perspectives. |
| Requirements Workshops | Organizing workshops with diverse stakeholders to collaboratively define security requirements through brainstorming, use case analysis, and threat modeling exercises. | Promotes consensus, facilitates shared understanding, and encourages diverse perspectives. | Requires careful planning and facilitation; can be challenging with large groups; may require multiple sessions. |
| Document Review | Analyzing existing documentation (system specifications, design documents, policy documents, regulatory requirements) to identify security-related information and requirements. | Provides a baseline understanding of the system; efficient for gathering existing requirements; helps identify gaps in documentation. | Requires access to comprehensive and up-to-date documentation; may not capture evolving security needs; can be time-consuming to analyze large volumes of documents. |
| Use Case Analysis | Analyzing system use cases to identify potential security threats and vulnerabilities associated with each use case, and defining security requirements to address those threats. | Focuses on specific user interactions and potential attack vectors; helps to define security requirements in the context of system functionality; easy to visualize and communicate. | Requires a well-defined set of use cases; may not cover all potential threats; requires a good understanding of security principles. |
Design Phase Security Practices
The design phase is a critical juncture in the Secure Software Development Life Cycle (SSDLC). This is where the architectural blueprint of the software is laid, determining its security posture from the outset. Decisions made during this phase have a profound impact on the application’s resilience against attacks. Careful consideration of security principles, threat modeling, and secure coding practices during design minimizes vulnerabilities and strengthens the software’s overall security.
Design Secure Architectural Patterns for Software Applications
Secure architectural patterns are pre-defined, proven designs that incorporate security considerations into the core structure of an application. These patterns provide a structured approach to building secure software, reducing the likelihood of common security flaws. Employing these patterns during the design phase promotes a proactive security stance.
- Microservices Architecture: Microservices break down an application into a collection of smaller, independent services. This pattern can enhance security by isolating failures and limiting the impact of security breaches. If one microservice is compromised, the attack’s reach is contained. Each service can also be secured independently, allowing for more granular security controls.
- Model-View-Controller (MVC) with Security Layers: The MVC pattern separates an application into three interconnected parts: the model (data), the view (user interface), and the controller (logic). When combined with security layers, this pattern can improve security. A security layer, for example, can be added to the controller to validate user input and authorize access. The separation of concerns makes it easier to implement and maintain security controls.
- Zero Trust Architecture: Zero Trust assumes no implicit trust. It requires continuous verification of every user and device trying to access resources. This model includes components like multi-factor authentication (MFA), least privilege access, and micro-segmentation to control access and prevent lateral movement within the network. This design helps to contain breaches and reduce the attack surface.
- API Gateway: An API gateway acts as a central point of entry for all API requests. It can provide security features such as authentication, authorization, rate limiting, and request validation. This central control point simplifies security management and helps to protect backend services from direct exposure.
Elaborate on the Importance of Secure Coding Standards During the Design Phase
Secure coding standards are a set of guidelines and best practices that developers follow to write secure code. Implementing these standards during the design phase is crucial because it establishes a foundation for security from the beginning. Early adoption helps prevent vulnerabilities that can be expensive and time-consuming to fix later in the SDLC.
- Input Validation and Sanitization: Input validation ensures that all user-supplied data conforms to the expected format and content. Sanitization removes or modifies potentially harmful data from user inputs. This is critical for preventing injection attacks, such as SQL injection and cross-site scripting (XSS).
- Authentication and Authorization: Authentication verifies the identity of a user or system, while authorization determines the level of access they are granted. Implementing strong authentication mechanisms, such as multi-factor authentication (MFA), and adhering to the principle of least privilege are essential.
- Secure Session Management: Secure session management involves protecting user sessions from hijacking and unauthorized access. This includes using secure session IDs, regularly rotating session tokens, and setting appropriate session timeout values.
- Error Handling and Logging: Proper error handling and logging practices are crucial for detecting and responding to security incidents. Error messages should not reveal sensitive information. Comprehensive logging enables security professionals to track events, identify anomalies, and investigate potential breaches.
- Cryptography: Cryptographic techniques, such as encryption and hashing, should be used to protect sensitive data. Securely storing passwords, encrypting data at rest and in transit, and using strong cryptographic algorithms are critical aspects of secure coding.
Provide Examples of Common Design Flaws and How to Mitigate Them
Common design flaws can lead to significant security vulnerabilities. Identifying and mitigating these flaws during the design phase is essential to building secure software. This involves understanding the potential weaknesses and implementing appropriate countermeasures.
- Insufficient Input Validation: This flaw occurs when user-supplied input is not properly validated.
- Example: A web application that doesn’t validate user input in a search field. An attacker could inject malicious code (e.g., JavaScript) to perform a cross-site scripting (XSS) attack.
- Mitigation: Implement robust input validation and sanitization techniques. Use parameterized queries to prevent SQL injection. Employ allowlists for input where possible.
- Broken Authentication and Session Management: This flaw involves vulnerabilities related to how users are authenticated and how their sessions are managed.
- Example: Weak password storage, such as storing passwords in plain text or using weak hashing algorithms.
- Mitigation: Use strong password hashing algorithms (e.g., bcrypt, Argon2). Implement multi-factor authentication (MFA). Securely store and manage session IDs.
- Cross-Site Scripting (XSS): XSS vulnerabilities allow attackers to inject malicious scripts into websites viewed by other users.
- Example: A web application that doesn’t sanitize user input before displaying it on a webpage. An attacker could inject malicious JavaScript code into a comment field.
- Mitigation: Implement output encoding to prevent the browser from interpreting user-supplied data as executable code. Use a Content Security Policy (CSP) to restrict the sources from which the browser can load resources.
- SQL Injection: SQL injection allows attackers to inject malicious SQL code into database queries.
- Example: A web application that constructs SQL queries by concatenating user-supplied input directly into the query string.
- Mitigation: Use parameterized queries or prepared statements. Validate and sanitize all user input. Employ the principle of least privilege for database users.
- Insecure Direct Object References (IDOR): IDOR vulnerabilities occur when an application provides direct access to objects based on user-supplied input without proper authorization checks.
- Example: An application that allows users to access files by providing a file ID in the URL. If the application doesn’t check whether the user is authorized to access the file, an attacker can access any file on the server by simply changing the file ID.
- Mitigation: Implement proper access controls and authorization checks for all object references. Use indirect object references.
Implementation Phase Security
The implementation phase is where the secure SDLC truly comes to life. This stage involves writing the code, integrating components, and building the software based on the design specifications. Ensuring security during this phase is crucial, as vulnerabilities introduced here can have significant consequences. Secure coding practices, rigorous code reviews, and the use of security tools are essential to mitigate risks and build a robust and secure application.
Secure Coding Practices to Prevent Common Vulnerabilities
Implementing secure coding practices is fundamental to preventing common vulnerabilities. These practices involve writing code that is resistant to attacks and minimizes the potential for security flaws. The following examples illustrate how to address some of the most prevalent threats.
- SQL Injection Prevention: SQL injection occurs when malicious SQL code is inserted into an application’s input, allowing attackers to manipulate database queries. To prevent this, always use parameterized queries or prepared statements. These techniques treat user input as data rather than executable code.
For example, instead of:
String sql = "SELECT
- FROM users WHERE username = '" + username + "' AND password = '" + password + "'";
Use a parameterized query:
String sql = "SELECT
- FROM users WHERE username = ? AND password = ?";
PreparedStatement ps = connection.prepareStatement(sql);
ps.setString(1, username);
ps.setString(2, password);
ResultSet rs = ps.executeQuery();
- Cross-Site Scripting (XSS) Prevention: XSS vulnerabilities allow attackers to inject malicious scripts into web pages viewed by other users. To mitigate XSS, always sanitize user input and encode output.
Input validation should be performed to ensure that the data conforms to the expected format and range.
Output encoding, also known as escaping, converts special characters into their HTML entities, preventing the browser from interpreting them as code. For example, the less-than sign (<) should be encoded as <.
- Cross-Site Request Forgery (CSRF) Prevention: CSRF attacks trick users into submitting unwanted requests to a web application they are authenticated in. Protect against CSRF by using anti-CSRF tokens.
These tokens are unique, secret values generated by the server and embedded in forms or requests. The server validates these tokens before processing the request.
- Authentication and Authorization: Implement robust authentication and authorization mechanisms to control user access. Use strong password policies, multi-factor authentication (MFA), and role-based access control (RBAC).
Regularly review and update authentication and authorization configurations. Implement mechanisms to handle password resets securely, such as sending a one-time password (OTP) or a link to reset the password, rather than directly sending the password.
- Input Validation and Sanitization: Validate all user inputs on both the client-side and the server-side. Client-side validation provides immediate feedback to the user, but it should not be relied upon as a sole security measure. Server-side validation is essential to ensure data integrity.
Sanitize all inputs to remove or neutralize potentially harmful code or characters.
For example, strip HTML tags from user-submitted comments to prevent XSS attacks.
- Error Handling and Logging: Implement secure error handling and logging practices. Avoid displaying sensitive information in error messages, which could reveal details about the system’s internal workings.
Log all security-related events, such as login attempts, failed access attempts, and any suspicious activity. Use a centralized logging system to facilitate monitoring and analysis.
- Secure Configuration: Securely configure all software components and systems. Disable unnecessary services and features. Regularly update software to patch known vulnerabilities.
Implement secure default configurations and adhere to the principle of least privilege, granting users only the minimum necessary access rights. Use security scanning tools to identify misconfigurations.
Code Review Best Practices
Code reviews are a crucial component of secure software development. They involve a systematic examination of source code to identify security vulnerabilities, coding errors, and adherence to coding standards. Effective code reviews help catch security flaws early in the development lifecycle, reducing the cost and effort of remediation.
- Establish a Code Review Process: Define a clear and documented code review process. Specify who performs reviews, the review criteria, and the tools used. This provides consistency and predictability.
- Use Checklists: Create checklists based on common vulnerability types (e.g., SQL injection, XSS, CSRF). These checklists help reviewers systematically examine code for specific issues.
- Automated Tools: Integrate static analysis tools into the code review process. These tools automatically scan code for potential vulnerabilities and coding errors, assisting reviewers in identifying potential problems.
- Review Code Changes: Review all code changes, regardless of their size or complexity. This includes new code, modifications to existing code, and any third-party libraries.
- Focus on Security: Ensure reviewers have a strong understanding of security principles and common vulnerabilities. Encourage reviewers to focus on security-related aspects of the code.
- Reviewers’ Selection: Select reviewers who are knowledgeable about the specific code and the security implications of the code’s functionality.
- Reviewer Training: Provide reviewers with regular training on secure coding practices and common vulnerabilities. Keep them informed about emerging threats and best practices.
- Documentation and Communication: Document all code review findings and recommendations. Communicate these findings to the developers promptly and clearly.
- Iterative Reviews: Conduct multiple rounds of code reviews, especially for complex or critical code. Address feedback and re-review the code after changes are made.
- Address Findings: Ensure that all identified security vulnerabilities and coding errors are addressed promptly. Track the status of all findings until they are resolved.
Image Description: Secure Coding Principles Illustration
The illustration depicts a stylized cityscape representing a software application. At the base of the city, strong foundations are laid, representing secure coding principles. These foundations are built with interlocking blocks, each labeled with a core security concept: “Input Validation,” “Output Encoding,” “Authentication,” “Authorization,” and “Error Handling.” These blocks are tightly integrated, symbolizing the interconnectedness of these principles.Above the foundations, several buildings are visible.
The tallest building, representing the core functionality of the application, has multiple layers of security features, such as a secure entryway with a guard checking credentials, and windows with reinforced glass, symbolizing the protection against attacks. The buildings are constructed with a focus on secure materials, like “secure code,” “parameterized queries,” and “anti-CSRF tokens.”Around the buildings, there are several lines of defense.
The first line is a fence labeled “Input Sanitization,” which filters out malicious data. Further out, a strong firewall is represented by a large wall, displaying the labels “Firewall Rules” and “Intrusion Detection.” The entire city is surrounded by a protective force field, symbolizing the use of encryption to protect data in transit and at rest.In the sky, a sun with the words “Code Review” shines brightly, illuminating the city and helping to identify any weaknesses or vulnerabilities.
This represents the constant monitoring and improvement of the code through reviews. The entire scene conveys a sense of security, resilience, and proactive defense against potential threats. The overall impression is one of a robust and secure software application built on solid security principles.
Testing Phase Security
The Testing Phase is a critical stage in the Secure Software Development Life Cycle (SDLC). Its primary objective is to identify vulnerabilities introduced during the previous phases and ensure the software functions as intended while adhering to security requirements. This phase validates the effectiveness of security controls implemented throughout the development process. Rigorous testing helps minimize the risk of security breaches and data compromises by uncovering weaknesses before the software is deployed to production.
Different Types of Security Testing
Various testing methodologies are employed to assess the security posture of software. Each method offers unique advantages in identifying different types of vulnerabilities. Understanding the characteristics of each type is essential for a comprehensive security assessment.
- Static Analysis (SAST): This testing method involves analyzing the source code without executing it. SAST tools scan the code for potential vulnerabilities, such as buffer overflows, SQL injection flaws, and insecure coding practices. SAST tools examine code for patterns that indicate security weaknesses, identifying potential problems early in the development cycle.
- Dynamic Analysis (DAST): DAST involves testing the software while it is running. This method analyzes the application’s behavior by providing input and observing its responses. DAST tools simulate real-world attacks to identify vulnerabilities that might not be apparent in the source code, such as cross-site scripting (XSS) and authentication issues.
- Penetration Testing (Pen Testing): Penetration testing, also known as ethical hacking, simulates a real-world attack on the software. Penetration testers attempt to exploit vulnerabilities to gain unauthorized access to the system. This process involves a combination of manual and automated techniques to assess the effectiveness of security controls and identify exploitable weaknesses.
- Fuzz Testing: Fuzz testing, also known as fuzzing, involves providing invalid, unexpected, or random data as input to the software. This testing method helps identify vulnerabilities that can cause the application to crash or behave unexpectedly, potentially leading to security flaws.
- Vulnerability Scanning: Vulnerability scanning uses automated tools to identify known vulnerabilities in software, operating systems, and network configurations. These tools compare the system’s components against a database of known vulnerabilities and provide reports detailing the identified weaknesses.
Comparison of Testing Methods
Each security testing method has its strengths and weaknesses. Choosing the right combination of testing methods is crucial for a comprehensive security assessment. The selection depends on factors like project budget, development stage, and the nature of the software.
- Static Analysis:
- Benefits: Early vulnerability detection, identifies coding errors, cost-effective, and integrates well into the development process.
- Drawbacks: May produce false positives, cannot detect runtime vulnerabilities, and requires access to source code.
- Dynamic Analysis:
- Benefits: Tests the application in a real-world environment, identifies runtime vulnerabilities, and requires no access to the source code.
- Drawbacks: Can be time-consuming, may not identify all vulnerabilities, and requires a running application.
- Penetration Testing:
- Benefits: Simulates real-world attacks, identifies critical vulnerabilities, and assesses the effectiveness of security controls.
- Drawbacks: Can be expensive, time-consuming, and requires specialized expertise.
- Fuzz Testing:
- Benefits: Identifies vulnerabilities related to input handling, reveals unexpected application behavior, and is automated.
- Drawbacks: May not always provide specific vulnerability details, and can be time-consuming.
- Vulnerability Scanning:
- Benefits: Automated, identifies known vulnerabilities, and provides quick results.
- Drawbacks: May produce false positives, relies on vulnerability databases, and does not exploit vulnerabilities.
Penetration Testing Steps
Penetration testing involves a structured process to assess the security of a system. Each step contributes to a comprehensive evaluation of the software’s vulnerabilities. The following table Artikels the key steps involved in penetration testing.
| Phase | Description | Activities |
|---|---|---|
| Planning and Scoping | This phase defines the objectives, scope, and rules of engagement for the penetration test. | Defining the target systems, identifying the scope of the test, establishing communication channels, and obtaining necessary approvals. |
| Information Gathering | This phase involves collecting information about the target system. | Gathering information through open-source intelligence (OSINT), network scanning, and vulnerability scanning. |
| Vulnerability Analysis | This phase identifies potential vulnerabilities based on the information gathered. | Analyzing the gathered information to identify potential weaknesses, such as outdated software, misconfigurations, and coding flaws. |
| Exploitation | This phase involves attempting to exploit identified vulnerabilities to gain unauthorized access. | Exploiting vulnerabilities using various tools and techniques, such as social engineering, password cracking, and privilege escalation. |
| Post-Exploitation | This phase involves maintaining access and gathering further information after successfully exploiting a vulnerability. | Maintaining access to the compromised system, gathering sensitive information, and pivoting to other systems. |
| Reporting | This phase involves documenting the findings and providing recommendations. | Preparing a detailed report that includes the identified vulnerabilities, the steps taken to exploit them, and recommendations for remediation. |
Deployment Phase Security
The deployment phase is a critical juncture in the SDLC, where the developed software transitions into a live production environment. This phase introduces new attack vectors and vulnerabilities, making it a prime target for malicious actors. Therefore, robust security measures are paramount to protect the software, data, and infrastructure from potential threats. Neglecting security during deployment can lead to significant breaches, data loss, and reputational damage.
Importance of Secure Deployment Strategies
Secure deployment strategies are essential to minimize risks and ensure the integrity, confidentiality, and availability of the software. A well-defined and implemented strategy encompasses various security practices, including secure configuration management, access controls, and monitoring. The primary goal is to prevent unauthorized access, protect sensitive data, and mitigate potential vulnerabilities introduced during the deployment process. Implementing secure deployment strategies also helps to maintain compliance with relevant regulations and industry standards, such as GDPR, HIPAA, and PCI DSS, which often mandate specific security controls.
Methods for Securing the Deployment Environment
Securing the deployment environment involves a multi-layered approach that encompasses various aspects, from infrastructure to application configuration. Several methods are crucial for achieving a secure deployment.
- Infrastructure Hardening: This involves securing the underlying infrastructure, including servers, networks, and databases. It is essential to configure the infrastructure securely to minimize potential attack surfaces.
- Regularly apply security patches and updates to operating systems, firmware, and software.
- Implement firewalls to control network traffic and restrict access to sensitive resources.
- Use intrusion detection and prevention systems (IDS/IPS) to monitor network activity and detect malicious behavior.
- Harden servers by disabling unnecessary services, removing default accounts, and configuring strong authentication mechanisms.
- Configuration Management: Establish a robust configuration management process to ensure consistent and secure configurations across all environments.
- Use configuration management tools (e.g., Ansible, Chef, Puppet) to automate configuration tasks and enforce security policies.
- Version control configuration files to track changes and facilitate rollbacks.
- Implement least privilege access control, granting users only the necessary permissions.
- Regularly audit configurations to identify and remediate any security vulnerabilities.
- Secure Automation: Automate deployment processes to reduce the risk of human error and ensure consistency.
- Use CI/CD pipelines to automate build, test, and deployment processes.
- Implement security checks within the CI/CD pipeline, such as static code analysis, vulnerability scanning, and penetration testing.
- Use infrastructure as code (IaC) to manage and provision infrastructure resources in a secure and repeatable manner.
- Automate security testing to identify and address vulnerabilities early in the deployment process.
- Monitoring and Logging: Implement comprehensive monitoring and logging to detect and respond to security incidents promptly.
- Collect and analyze security logs from various sources, including servers, applications, and network devices.
- Use security information and event management (SIEM) systems to aggregate and correlate security events.
- Establish alerting mechanisms to notify security teams of suspicious activities.
- Regularly review logs to identify potential security threats and anomalies.
Process of Configuring a Secure Server
Configuring a secure server involves a series of steps to minimize vulnerabilities and protect against potential attacks. This process should be consistently applied to all servers within the deployment environment.
- Operating System Hardening: Start by securing the operating system.
- Keep the OS updated with the latest security patches.
- Disable unnecessary services to reduce the attack surface.
- Remove default accounts and create strong passwords for all user accounts.
- Configure a firewall to restrict network access based on the principle of least privilege.
- Implement security auditing to monitor system activities.
- Application Server Configuration: Secure the application server based on the software being used.
- Follow the vendor’s security recommendations.
- Configure the server to use HTTPS with a valid SSL/TLS certificate.
- Restrict access to sensitive configuration files.
- Regularly review and update the server configuration.
- Database Security: Implement security measures for the database server.
- Use strong passwords for database accounts.
- Limit access to the database based on the principle of least privilege.
- Encrypt sensitive data at rest and in transit.
- Regularly back up the database to prevent data loss.
- Monitor database activity for suspicious behavior.
- Network Security: Secure the network environment.
- Implement firewalls to control network traffic.
- Use intrusion detection and prevention systems (IDS/IPS) to monitor network activity.
- Segment the network to isolate sensitive resources.
- Regularly scan the network for vulnerabilities.
- Access Control: Implement access controls to manage user access to server resources.
- Use role-based access control (RBAC) to assign permissions based on user roles.
- Implement multi-factor authentication (MFA) to enhance security.
- Regularly review user access to ensure it aligns with the principle of least privilege.
Maintenance Phase Security
The Maintenance Phase is a critical stage in the Secure SDLC, as it ensures the continued security and integrity of the software after deployment. This phase involves ongoing activities to address vulnerabilities, monitor for threats, and maintain the software’s security posture. Neglecting this phase can lead to significant security breaches and compromise the confidentiality, integrity, and availability of the system.
Continuous Monitoring and Vulnerability Management
Continuous monitoring and vulnerability management are fundamental components of the Maintenance Phase. They provide the visibility and control necessary to identify and mitigate security risks proactively.Continuous monitoring involves the ongoing assessment of the software and its environment to detect security threats, anomalies, and potential vulnerabilities. This includes:* Security Information and Event Management (SIEM) Systems: These systems collect and analyze security-related logs from various sources, such as servers, applications, and network devices, to identify suspicious activities and potential security incidents.
They can generate alerts and reports to notify security teams of potential threats. For instance, a SIEM system might detect unusual login attempts or suspicious network traffic patterns.
Intrusion Detection and Prevention Systems (IDPS)
IDPS monitor network traffic and system activity for malicious behavior. They can detect and block attacks in real-time. An IDPS might identify and block attempts to exploit known vulnerabilities.
Vulnerability Scanning
Regularly scanning the software and its environment for known vulnerabilities using automated tools. Vulnerability scanners identify weaknesses in the software, its dependencies, and the underlying infrastructure. They provide reports on identified vulnerabilities, along with recommendations for remediation.
Penetration Testing
Periodic penetration testing (ethical hacking) to simulate real-world attacks and assess the effectiveness of security controls. Penetration testers attempt to exploit vulnerabilities to identify weaknesses and assess the potential impact of a successful attack.Vulnerability management is the process of identifying, assessing, prioritizing, and remediating vulnerabilities. It involves:* Vulnerability Identification: Identifying vulnerabilities through various means, including vulnerability scanning, penetration testing, and security audits.
Vulnerability Assessment
Assessing the severity and potential impact of identified vulnerabilities. This includes evaluating the likelihood of exploitation and the potential consequences of a successful attack.
Vulnerability Prioritization
Prioritizing vulnerabilities based on their severity, exploitability, and potential impact. This allows security teams to focus their efforts on addressing the most critical risks first. Common prioritization frameworks include the Common Vulnerability Scoring System (CVSS).
Vulnerability Remediation
Addressing vulnerabilities through patching, configuration changes, or other mitigation strategies. This involves applying security updates, implementing security controls, and updating system configurations.
Vulnerability Verification
Verifying that vulnerabilities have been successfully remediated. This involves re-scanning the system and confirming that the vulnerabilities are no longer present.
Best Practices for Patching and Updating Software
Regular patching and updating of software are crucial for maintaining a strong security posture. They address known vulnerabilities and protect against emerging threats. Following best practices ensures that patches are applied effectively and without disrupting the software’s functionality.* Establish a Patch Management Policy: Develop a formal policy that defines the processes and procedures for patching and updating software. This policy should specify the frequency of patching, the testing and validation process, and the roles and responsibilities for patch management.
Prioritize Patching Based on Risk
Prioritize patching based on the severity of the vulnerability, the availability of exploits, and the potential impact of a successful attack. Critical vulnerabilities that are actively being exploited should be addressed immediately.
Test Patches Before Deployment
Before deploying patches to production systems, test them in a non-production environment to ensure they do not cause compatibility issues or disrupt the software’s functionality. Testing should include functional testing, security testing, and performance testing.
Automate Patch Deployment
Automate the patch deployment process to reduce the time and effort required to apply patches. Automation tools can streamline the patch deployment process and ensure that patches are applied consistently across all systems.
Maintain an Inventory of Software and Versions
Maintain a comprehensive inventory of all software and versions installed on systems. This inventory is essential for identifying vulnerable software and tracking the patching status.
Monitor Patching Status
Continuously monitor the patching status of all systems to ensure that patches are applied promptly and effectively. Use automated tools to track the patching status and generate reports.
Rollback Plan
Create a rollback plan to revert to a previous state if a patch causes unexpected issues. This plan should Artikel the steps required to remove the patch and restore the system to its previous configuration.
Keep Dependencies Updated
Keep software dependencies, such as libraries and frameworks, up-to-date. These dependencies often contain vulnerabilities that can be exploited by attackers.
Apply Patches Promptly
Apply security patches promptly, ideally within a timeframe defined by the organization’s risk tolerance. Delaying patch application increases the window of opportunity for attackers to exploit known vulnerabilities.
Process for Incident Response and Security Updates
A well-defined incident response process is essential for responding effectively to security incidents and mitigating their impact. This process should be integrated with the process for security updates to ensure that vulnerabilities are addressed promptly and that the software remains secure.* Incident Detection and Reporting: Implement mechanisms for detecting and reporting security incidents. This includes monitoring security logs, reviewing security alerts, and providing a clear process for users to report suspected security incidents.
Incident Analysis and Validation
Upon receiving a security incident report, analyze the incident to determine its nature, scope, and impact. Validate the incident to ensure it is a genuine security event.
Containment
Contain the incident to prevent further damage. This may involve isolating affected systems, disabling compromised accounts, or blocking malicious traffic.
Eradication
Eradicate the root cause of the incident. This may involve removing malware, patching vulnerabilities, or removing compromised accounts.
Recovery
Recover affected systems and data. This may involve restoring from backups, rebuilding systems, or re-establishing services.
Post-Incident Activities
Conduct a post-incident review to identify lessons learned and improve the incident response process. This may include updating security policies, improving security controls, or enhancing incident response training.
Security Update Integration
Integrate the incident response process with the process for security updates. When a vulnerability is discovered during an incident, the security update process should be initiated immediately. This includes:
Vulnerability Assessment
Assess the severity and potential impact of the vulnerability.
Patch Development
Develop a patch to address the vulnerability.
Testing
Test the patch in a non-production environment.
Deployment
Deploy the patch to production systems.
Communication
Communicate the vulnerability and the patch to users and stakeholders.An example of a security update process integrated with incident response is the handling of a zero-day vulnerability. A zero-day vulnerability is a security flaw that is unknown to the vendor and for which no patch exists. If a zero-day vulnerability is discovered during an incident, the incident response team would:
- Contain the incident by implementing temporary mitigations, such as blocking malicious traffic.
- Work with the vendor to develop a patch.
- Test the patch thoroughly.
- Deploy the patch to production systems as soon as possible.
- Communicate the vulnerability and the patch to users and stakeholders.
Tools and Technologies for Secure SDLC
Implementing a secure Software Development Life Cycle (SDLC) necessitates the utilization of various tools and technologies. These resources aid in automating security checks, identifying vulnerabilities, and ensuring the overall integrity of the software throughout its lifecycle. The selection of appropriate tools depends on the specific needs of the project, the programming languages used, and the development methodologies employed. This section will explore different categories of tools and provide a practical example of their application.
Tools for Static Code Analysis
Static code analysis tools examine source code without executing it. They analyze the code for potential vulnerabilities, coding standard violations, and other security flaws. These tools are typically integrated into the development environment, allowing developers to identify and fix issues early in the development process.
- SAST (Static Application Security Testing) Tools: These tools perform a comprehensive analysis of the source code.
- Examples of SAST Tools:
- SonarQube: An open-source platform for continuous inspection of code quality. It supports numerous languages and provides detailed reports on vulnerabilities, code smells, and other issues.
- Veracode Static Analysis: A commercial SAST tool offering a wide range of features, including vulnerability detection and compliance reporting.
- Checkmarx: Another commercial SAST tool known for its accuracy and integration capabilities.
- Coverity: A static analysis tool focused on identifying critical defects early in the development process.
- Benefits of Static Code Analysis:
- Early vulnerability detection, which reduces the cost of remediation.
- Enforcement of coding standards, which improves code quality and maintainability.
- Increased developer awareness of security best practices.
Tools for Dynamic Analysis
Dynamic analysis tools, unlike static analysis tools, execute the software to identify vulnerabilities. These tools simulate user interactions and analyze the application’s behavior to detect security flaws, such as SQL injection, cross-site scripting (XSS), and other runtime issues.
- DAST (Dynamic Application Security Testing) Tools: These tools are designed to detect vulnerabilities in running applications.
- Examples of DAST Tools:
- OWASP ZAP (Zed Attack Proxy): A free and open-source web application security scanner that can identify a wide range of vulnerabilities.
- Burp Suite: A popular commercial tool that combines various features, including a web application scanner, a proxy server, and manual testing tools.
- Acunetix: A commercial web vulnerability scanner that automates security testing.
- Netsparker: A fully automated web application security scanner that identifies vulnerabilities in web applications.
- Benefits of Dynamic Code Analysis:
- Identification of runtime vulnerabilities.
- Assessment of the application’s behavior under various conditions.
- Validation of the effectiveness of security controls.
Demonstration of a Specific Security Tool: OWASP ZAP
OWASP ZAP (Zed Attack Proxy) is a free and open-source web application security scanner. It is a powerful tool that can be used to identify vulnerabilities in web applications during the implementation and testing phases of the SDLC. Here is a step-by-step guide to using OWASP ZAP for a basic web application scan.
- Installation and Setup:
- Download and install OWASP ZAP from the official website. The installation process is straightforward, following the instructions for your operating system.
- Once installed, launch ZAP. You will be presented with the ZAP user interface.
- Setting Up the Target Application:
- The target application can be a local web application running on your machine or a remote web application. For this example, let’s assume a local web application running on `http://localhost:8080`.
- Using the Automated Scan:
- Choose an automated scan: From the ZAP interface, select “Automated Scan” from the “Quick Start” tab.
- Enter the URL: Enter the URL of your target web application (e.g., `http://localhost:8080`) in the “URL to attack” field.
- Start the scan: Click the “Attack” button to start the automated scan. ZAP will crawl the application and identify potential vulnerabilities.
- Analyzing the Results:
- Review the Alerts tab: ZAP will display the identified vulnerabilities in the “Alerts” tab. The alerts are categorized by severity (High, Medium, Low, Informational).
- Examine the details: Click on each alert to view detailed information about the vulnerability, including the affected URL, the risk, the confidence level, and the recommended remediation steps.
- Use the “Sites” tab: The “Sites” tab provides a hierarchical view of the web application, allowing you to explore the different pages and resources.
- Interpreting the Findings:
- High-severity vulnerabilities: These vulnerabilities require immediate attention. They often represent critical security flaws, such as SQL injection or cross-site scripting.
- Medium-severity vulnerabilities: These vulnerabilities also pose a risk and should be addressed.
- Low-severity vulnerabilities: These vulnerabilities may not be critical but should still be reviewed and addressed if possible.
- Remediation:
- Based on the scan results, implement the recommended remediation steps provided by ZAP. This may involve fixing code, configuring security settings, or applying patches.
- Reporting:
- ZAP allows generating reports in various formats (HTML, XML, etc.). These reports can be shared with the development team and other stakeholders.
This step-by-step guide provides a basic overview of using OWASP ZAP. ZAP offers advanced features, such as manual testing tools and API support, for more in-depth security assessments. The results of a ZAP scan should be used to inform and guide the development team in fixing vulnerabilities and improving the security posture of the web application.
Measuring and Improving Security Posture
Implementing a secure Software Development Life Cycle (SDLC) is an ongoing process, not a one-time event. To ensure the effectiveness of your secure SDLC and to continuously improve your security posture, it is crucial to establish mechanisms for measuring performance and identifying areas for enhancement. This involves defining relevant metrics, regularly monitoring performance, and adapting processes based on the insights gained.
Metrics for Measuring Secure SDLC Effectiveness
Measuring the effectiveness of a secure SDLC requires a multifaceted approach. It involves tracking various aspects of the development process to identify vulnerabilities, assess the impact of security measures, and gauge overall improvement. The following metrics are crucial for a comprehensive evaluation.
- Vulnerability Detection Rate: This metric measures the effectiveness of vulnerability detection efforts. It is typically calculated as the percentage of vulnerabilities found during testing phases, such as static and dynamic analysis, penetration testing, and code reviews, compared to the total number of vulnerabilities identified. A higher detection rate indicates a more robust vulnerability identification process. For instance, if a project team identifies 80 vulnerabilities out of a total of 100 during testing, the vulnerability detection rate is 80%.
- Time to Remediate Vulnerabilities: This metric tracks the average time taken to fix identified vulnerabilities. It highlights the efficiency of the remediation process and the speed at which security issues are addressed. A shorter time to remediate indicates a more responsive and effective security team. The time is measured from vulnerability discovery to the point where a fix is implemented and verified.
- Number of Security Incidents: This metric monitors the occurrence of security incidents, such as data breaches, unauthorized access, and malware infections, after the software is deployed. A decrease in the number of security incidents over time signifies an improvement in the overall security posture. The incident rate is often normalized by the number of users or transactions to provide a more accurate comparison.
- Code Coverage for Security Tests: Code coverage measures the percentage of the codebase that is exercised by security tests. A higher code coverage ensures that a larger portion of the code is tested for vulnerabilities, increasing the likelihood of detecting security flaws. This includes tests like unit tests, integration tests, and system tests, and it helps to understand how well the testing process is covering the application’s code.
- Security Training Completion Rate: This metric assesses the level of security awareness within the development team. It measures the percentage of developers who have completed relevant security training programs. A higher completion rate indicates a more security-conscious team, which can lead to fewer security vulnerabilities.
- Compliance with Security Policies: This metric evaluates adherence to established security policies and standards. It assesses the extent to which the development team follows security best practices and guidelines throughout the SDLC. Compliance can be measured through audits, code reviews, and other assessments.
Strategies for Continuous Security Posture Improvement
Continuous improvement is essential for maintaining a strong security posture. This involves a proactive approach that includes regular assessments, ongoing training, and iterative refinement of security practices. Implementing the following strategies can significantly enhance the effectiveness of a secure SDLC.
- Regular Security Audits and Assessments: Conduct periodic security audits and assessments, including penetration testing, vulnerability scanning, and code reviews. These assessments help identify weaknesses and vulnerabilities in the software and the development processes. The frequency of these assessments should be determined based on the risk profile of the software.
- Implement Automated Security Testing: Automate security testing throughout the SDLC to catch vulnerabilities early and often. This includes static code analysis, dynamic analysis, and automated penetration testing. Automation reduces the manual effort required for security testing and allows for more frequent testing.
- Provide Ongoing Security Training: Ensure that all development team members receive regular security training. This training should cover the latest security threats, vulnerabilities, and best practices. Training should be tailored to the roles and responsibilities of the team members.
- Foster a Security-Conscious Culture: Promote a culture of security awareness within the organization. This involves encouraging developers to prioritize security, report vulnerabilities, and share security knowledge. Regular communication and awareness campaigns can help foster a security-conscious culture.
- Monitor and Analyze Security Incidents: Implement robust monitoring and incident response processes. This includes monitoring security logs, analyzing security incidents, and learning from past mistakes. Incident analysis should identify the root causes of security incidents and inform improvements to the SDLC.
- Update Security Tools and Technologies: Keep security tools and technologies up-to-date. This includes regularly updating vulnerability scanners, intrusion detection systems, and other security tools. Keeping tools updated ensures that the latest security threats are addressed.
- Refine Security Policies and Procedures: Continuously review and refine security policies and procedures based on the findings of security assessments, incident analysis, and changes in the threat landscape. This ensures that the policies and procedures remain effective.
Key Performance Indicators (KPIs) for Secure SDLC Implementation
The following table Artikels key performance indicators (KPIs) that can be used to measure the effectiveness of a secure SDLC implementation. These KPIs provide a framework for tracking progress and identifying areas for improvement.
| KPI | Measurement Method | Target | Benefits |
|---|---|---|---|
| Vulnerability Detection Rate | Percentage of vulnerabilities detected during testing phases. | Increase year over year (e.g., from 70% to 80%). | Improved software security, reduced risk of exploitation. |
| Time to Remediate Vulnerabilities | Average time taken to fix identified vulnerabilities. | Reduce the average remediation time (e.g., from 30 days to 15 days). | Faster response to security threats, reduced attack surface. |
| Number of Security Incidents | Number of security incidents reported. | Decrease in the number of incidents over time. | Improved overall security posture, reduced business impact. |
| Code Coverage for Security Tests | Percentage of code covered by security tests. | Increase code coverage (e.g., from 60% to 80%). | More comprehensive security testing, reduced risk of undiscovered vulnerabilities. |
| Security Training Completion Rate | Percentage of developers completing security training. | Increase the completion rate (e.g., from 80% to 95%). | Increased security awareness, reduced human error. |
| Compliance with Security Policies | Results of audits and code reviews. | Maintain high compliance rates (e.g., 95% or higher). | Ensures adherence to security standards, reduces compliance risks. |
Closing Summary
In conclusion, implementing a secure software development life cycle is not merely a best practice; it’s a necessity. We’ve traversed the landscape of secure SDLC, from planning and design to testing and maintenance. By embracing continuous learning, utilizing the right tools, and fostering a culture of security awareness, you can create software that is not only functional and efficient but also resilient against evolving threats.
Remember, security is a journey, not a destination, so stay vigilant and keep building securely.
Query Resolution
What is the biggest challenge in implementing a secure SDLC?
The biggest challenge is often integrating security into the existing development workflow and fostering a security-conscious culture across the entire team. This requires buy-in from all stakeholders and a commitment to continuous training and improvement.
How often should security audits be conducted?
Security audits should be conducted regularly, ideally at least annually, and more frequently if there are significant changes to the software, infrastructure, or threat landscape. Penetration testing should be performed regularly, ideally as part of a continuous integration and continuous deployment (CI/CD) pipeline.
What are the most common types of security vulnerabilities?
Some of the most common vulnerabilities include SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), insecure authentication and authorization, and security misconfiguration. These vulnerabilities often arise from coding errors, poor design choices, or inadequate security practices.
How can I measure the effectiveness of my secure SDLC?
Measure the effectiveness of your SDLC through metrics such as the number of security vulnerabilities discovered during testing, the time it takes to remediate vulnerabilities, the number of security incidents, and the results of security audits and penetration tests. Tracking these KPIs over time can help you identify areas for improvement.
Is a secure SDLC expensive to implement?
While implementing a secure SDLC requires an initial investment in training, tools, and processes, it can ultimately save money by reducing the risk of costly security breaches and data loss. Furthermore, building security in from the start is often less expensive than fixing vulnerabilities later in the development lifecycle.