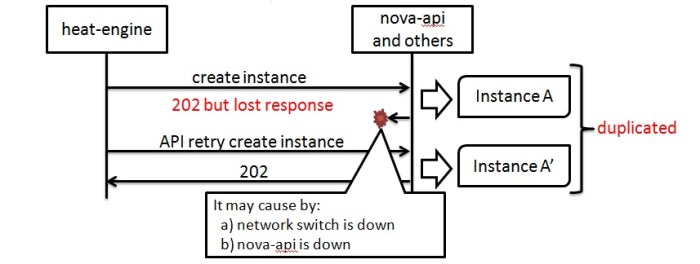
The “lift and shift” migration approach, while seemingly straightforward, often leads to unforeseen challenges and suboptimal outcomes. This comprehensive guide provides a roadmap for successfully navigating application migrations, avoiding the pitfalls of this common anti-pattern, and achieving a seamless transition to a more robust and scalable environment.
This document Artikels the critical factors to consider when migrating applications, emphasizing the importance of careful planning, meticulous execution, and a proactive approach to address potential risks and maximize the benefits of cloud-based solutions. By understanding the limitations of “lift and shift” and exploring alternative migration strategies, organizations can minimize operational costs and enhance the long-term value of their applications.
Identifying the Risks of “Lift and Shift”

The “lift and shift” approach to application migration, while seemingly straightforward, often conceals significant risks. This method, which involves simply moving applications from one environment to another with minimal modifications, can lead to unforeseen complications and operational challenges. Understanding these potential pitfalls is crucial for planning a successful and cost-effective migration strategy.The lack of careful planning and consideration for the nuances of the target environment can result in significant difficulties.
Compatibility issues, dependency management challenges, security concerns, and lost optimization opportunities are all common outcomes of a poorly executed lift and shift migration. Recognizing and mitigating these risks upfront is essential to avoid costly rework and prolonged downtime.
Potential Compatibility Issues
Applications are often tightly coupled with their underlying infrastructure. Differences in operating systems, databases, or other system components between the source and target environments can lead to unexpected errors or failures. For instance, an application built on a specific version of Linux might not function correctly on a different distribution or a different version. Compatibility issues can also arise with software libraries or APIs.
Carefully assessing the application’s dependencies and their compatibility with the target environment is essential. This often requires thorough testing and potential code adjustments.
Challenges in Maintaining Application Dependencies
Applications rely on various components, such as libraries, APIs, and other services, to function properly. Migrating these applications without careful consideration of these dependencies can lead to problems. For example, a web application that depends on a specific database might encounter difficulties if the database schema is not properly migrated or if the database version is incompatible with the target environment.
A lack of consideration for these dependencies can cause critical failures or performance issues, leading to substantial downtime and maintenance efforts.
Difficulty in Managing Security Vulnerabilities and Compliance
Lift and shift migrations often overlook security considerations. The same application code deployed in a new environment may inherit existing security vulnerabilities. Furthermore, regulatory compliance requirements might not be met if the migration process doesn’t address necessary security protocols or controls. A significant risk is the potential exposure of sensitive data due to misconfigurations or lack of proper security measures in the target environment.
Failing to address these vulnerabilities can result in data breaches and costly penalties.
Loss of Optimization Opportunities
Migrating applications without a comprehensive plan can prevent organizations from capitalizing on opportunities for optimization. The target environment might offer enhanced resources or capabilities that could significantly improve application performance. Failing to take advantage of these opportunities can result in slower application response times and a diminished user experience. Furthermore, a lack of planning might lead to inefficiencies in resource utilization.
Examples of Failed Lift and Shift Migrations and Their Consequences
Several documented cases highlight the pitfalls of lift and shift migrations. One example involves a company that migrated an application to a cloud environment but encountered significant performance issues due to insufficient resource allocation. Another instance illustrates how a lack of security hardening during the migration led to a data breach. These failures highlight the importance of thorough planning, testing, and security measures during the migration process.
Consequences of such failures can range from significant downtime and loss of revenue to costly remediation efforts.
Impact on Operational Costs
The risks associated with lift and shift migrations can significantly impact operational costs. Unexpected downtime, the need for extensive debugging and maintenance, and security breaches can all result in substantial expenses. Furthermore, the loss of optimization opportunities can lead to increased operational costs in the long run. A well-planned migration strategy, including thorough testing and security hardening, can mitigate these risks and optimize operational costs.
Alternative Migration Strategies
Avoiding the “lift and shift” anti-pattern necessitates a strategic approach that considers the unique characteristics of the cloud environment. A successful migration requires careful planning, encompassing the selection of appropriate strategies and a thorough understanding of the target cloud platform. This involves more than simply moving existing applications to the cloud; it demands a comprehensive evaluation of application architecture and potential for optimization.Successful cloud migrations often involve a nuanced approach, going beyond simple replication.
This necessitates a paradigm shift in thinking, moving away from the traditional on-premises infrastructure mindset and embracing cloud-native principles. Understanding and leveraging these principles is crucial for realizing the full potential of cloud-based deployments.
Migration Strategies Avoiding the Lift-and-Shift Anti-pattern
Various strategies can be employed to avoid the pitfalls of “lift and shift.” These approaches emphasize adapting applications to the cloud environment rather than simply replicating their on-premises counterparts.
- Refactoring and Modernization: This strategy involves redesigning and restructuring applications to take advantage of cloud-native features and services. This often leads to improved performance, scalability, and maintainability. Refactoring, for example, can involve rewriting parts of the application using newer programming languages or frameworks, or optimizing database schemas for cloud environments. Modernization includes upgrading applications to leverage cloud services and features like serverless computing or containerization.
- Cloud-Native Application Design: Developing applications from the ground up with cloud-native principles in mind is a crucial strategy. This approach focuses on modularity, microservices architecture, and leveraging cloud-native services. This ensures that the application is designed for scalability, resilience, and rapid deployment from the outset.
- Containerization and Orchestration: Containerization technologies like Docker, coupled with orchestration platforms like Kubernetes, enable consistent and automated deployment, scaling, and management of applications across various cloud environments. This approach allows for rapid deployment and efficient resource utilization.
- Serverless Computing: This strategy leverages cloud providers’ serverless platforms, where applications run on demand and are automatically scaled. This eliminates the need for managing servers and allows for highly scalable and cost-effective solutions, particularly for applications with unpredictable workloads.
- Application Programming Interfaces (APIs): Leveraging APIs to connect existing applications to cloud services can enhance functionality and enable integration with other cloud resources, potentially unlocking further optimization opportunities.
Benefits of Refactoring and Modernization Techniques
Refactoring and modernization efforts during migration yield several key benefits. They enhance application agility, performance, and cost-effectiveness.
- Enhanced Scalability and Elasticity: Cloud-native applications are designed for automatic scaling based on demand. This ensures that resources are dynamically adjusted, avoiding performance bottlenecks or underutilization.
- Improved Performance: Modernization often involves optimizing code and leveraging cloud-native technologies, leading to faster response times and enhanced user experience.
- Reduced Operational Costs: Cloud-native architectures and serverless functions often result in lower operational costs by automating tasks and optimizing resource utilization.
- Increased Maintainability: Refactoring and modernization typically lead to more maintainable codebases, facilitating future updates and enhancements.
Importance of Cloud-Native Application Design Principles
Adhering to cloud-native design principles is paramount for building applications that are optimized for the cloud environment.
- Modularity and Microservices: Breaking down applications into smaller, independent services allows for independent scaling, deployment, and maintenance.
- Decentralized Data Management: Adopting cloud-native database services often offers better performance, scalability, and cost-effectiveness compared to traditional relational databases.
- Resilience and Fault Tolerance: Cloud-native architectures are built with redundancy and failover mechanisms in mind, enhancing application reliability.
Different Cloud-Native Deployment Models
Various cloud-native deployment models exist, each with its strengths and weaknesses.
- Container Orchestration (e.g., Kubernetes): This model provides automation for deploying, scaling, and managing containerized applications. It excels at managing complex deployments and ensuring consistency across environments.
- Serverless Functions: These functions are triggered by events and automatically scaled based on demand. This approach is ideal for applications with unpredictable workloads and a need for minimal infrastructure management.
Strengths and Weaknesses of Migration Approaches
A comparative analysis of different migration approaches highlights their unique characteristics.
| Migration Approach | Strengths | Weaknesses |
|---|---|---|
| Lift and Shift | Relatively quick and simple | Limited scalability, performance issues, higher operational costs, and difficulty in leveraging cloud-native features. |
| Refactoring/Modernization | Improved scalability, performance, and maintainability; better cost optimization; enhanced cloud-native capabilities | Requires significant effort and time; may involve risk and complexity in the initial stages. |
| Cloud-Native Development | Best for new applications; maximum utilization of cloud services; high scalability and flexibility | Requires significant upfront investment and specialized skills. |
Planning for a Successful Migration
A successful application migration requires meticulous planning and execution. A well-defined strategy, encompassing thorough assessment, resource allocation, and project management, is paramount to avoiding the pitfalls of the “lift and shift” approach and ensuring a smooth transition to the new environment. This comprehensive approach will mitigate risks and maximize the chances of a positive outcome.Thorough planning is not just about avoiding the “lift and shift” anti-pattern; it is a crucial element in realizing the full potential of the migration.
By carefully considering all aspects, including potential challenges and opportunities, organizations can achieve a seamless transition and reap the benefits of modernization.
Application Assessment Prior to Migration
A comprehensive application assessment is critical for understanding the intricacies of the existing system and its suitability for migration. This involves a detailed analysis of the application’s architecture, dependencies, data structures, and functionality. Understanding the application’s current state allows for a realistic assessment of its compatibility with the target environment. Key elements of this assessment include identifying potential compatibility issues, evaluating performance characteristics, and determining data migration requirements.
This stage also involves understanding security implications and potential compliance requirements.
Migration Strategy and Roadmap
A robust migration strategy serves as a blueprint for the entire process. It Artikels the specific steps, timelines, and resources required for each phase of the migration. This roadmap should detail the migration approach, considering factors like incremental vs. complete migration, phased rollout, or parallel operation. Furthermore, the strategy should address potential risks and contingencies, ensuring a proactive approach to potential problems.
This includes defining clear success metrics, which will be essential in evaluating the effectiveness of the migration.
Resource Allocation and Project Management
Effective resource allocation is crucial for a successful migration. This involves not only assigning the right personnel with the necessary expertise but also allocating adequate time, budget, and tools. Proper project management techniques, such as Agile or Waterfall, can be employed to track progress, manage risks, and ensure adherence to timelines. The allocated resources should be carefully managed and monitored to maintain efficiency and control throughout the migration.
This includes identifying and addressing resource constraints proactively.
Checklist for a Smooth Transition
A detailed checklist ensures all critical tasks are addressed. This checklist should cover activities from data validation and migration to system testing and user training. Having a comprehensive checklist is essential to mitigate the risk of missing critical steps. This checklist should also include contingency plans for unexpected challenges and ensure a proactive approach to potential problems.
- Data Validation and Migration: This stage requires meticulous validation of data to ensure accuracy and integrity during migration. Proper data transformation processes are necessary to maintain data integrity and consistency.
- System Testing: Comprehensive testing in the target environment is essential to identify and resolve any potential compatibility issues. This includes functional testing, performance testing, and security testing.
- User Training and Support: Thorough user training programs are critical to ensure a smooth transition to the new system. This should be integrated into the migration plan and support must be readily available during and after the transition.
- Change Management: Implementing change management strategies is crucial for managing user adoption and minimizing resistance to the new system.
Crucial Factors for Successful Migration Execution
Successful migration execution hinges on several crucial factors. These factors include effective communication, collaboration among teams, adherence to timelines, and proactive risk management. Continuous monitoring and adaptation are also key to ensuring a smooth transition and addressing any unforeseen issues. It is important to maintain a flexible approach to handle evolving requirements and potential disruptions.
Examples of Successful Migration Projects
Numerous organizations have successfully migrated applications without adopting the “lift and shift” approach. These examples demonstrate the potential benefits of careful planning and strategic execution. For instance, Company X migrated their core application using a phased approach, minimizing downtime and ensuring a smooth transition for end-users. Another successful example involved Company Y, which used a cloud-based migration strategy, leveraging the scalability and flexibility of the cloud environment.
These examples illustrate the importance of selecting the appropriate migration strategy based on the specific needs of the application and the organization.
Addressing Application Dependencies and Integrations
Effective migration strategies require a thorough understanding and management of application dependencies and integrations. Neglecting these crucial aspects can lead to significant challenges and delays, potentially impacting the overall success of the migration project. Careful planning and execution are paramount to ensuring a smooth transition.A comprehensive approach to dependency management involves identifying, documenting, and mitigating potential risks associated with interconnected systems.
This includes understanding the intricate relationships between applications and external services, as well as the data flows and communication protocols involved. A thorough analysis of these dependencies allows for informed decisions about migration strategies and resource allocation.
Analyzing and Managing Application Dependencies
Thorough analysis of application dependencies is critical to avoid unforeseen issues during the migration. This process entails identifying all applications and services that interact with the target application. Documentation should include details on the nature of the interaction (e.g., data exchange, API calls, message queues), the frequency of interaction, and the potential impact of changes on other systems.
This detailed documentation is crucial for accurately assessing the complexity and scope of the migration.
Identifying and Addressing Integration Points
Understanding and managing integration points with other systems is vital for a successful migration. Integration points encompass all interactions with external systems, including APIs, databases, message queues, and other services. Identifying and documenting these points is the first step in assessing the impact of the migration on these external systems.
Utilizing API Management Tools and Strategies
API management tools play a critical role in facilitating smooth integrations during migration. These tools provide a centralized platform for managing APIs, including documentation, security, monitoring, and governance. Properly implemented API management can significantly streamline the integration process, enabling a more controlled and predictable migration. This includes features like API gateways, rate limiting, and authentication mechanisms to ensure smooth communication and security during and after migration.
Maintaining Data Consistency Throughout the Migration
Maintaining data consistency is paramount during the migration process. Any discrepancies or inconsistencies can lead to data loss or corruption, impacting the success of the migration. Strategies to maintain data consistency should be planned and implemented from the initial stages. This includes defining clear data mapping strategies, establishing validation rules, and implementing robust data transformation processes.
Database Migration Steps
A structured approach to database migration is crucial. A step-by-step guide for database migration should include:
- Assessment and Planning: Thoroughly assess the current database structure, data volume, and dependencies. Develop a detailed migration plan outlining the steps, timelines, and resources required. This stage includes identifying potential risks and devising mitigation strategies.
- Data Backup and Validation: Create complete backups of the source database. Develop a robust validation strategy to ensure data integrity during the migration process. Data validation procedures should cover various data points, such as data types, formats, and constraints.
- Data Transformation: Define the data transformation rules and processes necessary to adapt the data to the target database schema. Consider potential data loss or corruption and implement appropriate safeguards.
- Database Migration: Migrate the database schema and data to the target environment. Implement proper monitoring and logging mechanisms to track progress and identify potential issues.
- Testing and Validation: Rigorously test the migrated database and applications to ensure functionality and data consistency. Use appropriate testing methodologies and validation tools to identify and resolve any issues.
- Post-Migration Activities: Perform post-migration checks and fine-tuning. Review performance metrics and make necessary adjustments. Ensure all applications and services are functioning correctly with the migrated database.
Security and Compliance Considerations

Maintaining the security and compliance posture of applications during and after a migration is critical. A robust security strategy must be implemented from the initial planning stages to ensure a smooth and secure transition. This includes understanding and mitigating potential risks throughout the entire migration lifecycle, from assessing existing security controls to implementing new ones in the target environment.The migration process can introduce vulnerabilities if not carefully managed.
Addressing security and compliance from the outset prevents costly issues later on and ensures a secure and compliant application in the new environment. Proper planning, thorough testing, and adherence to regulatory requirements are paramount.
Ensuring Application Security During Migration
A comprehensive security strategy must be implemented throughout the migration process. This involves carefully assessing existing security controls, understanding potential risks associated with the migration, and proactively mitigating those risks. Implementing robust access controls and secure configurations from the outset is essential to safeguard sensitive data and maintain a high level of protection.
Importance of Compliance with Industry Regulations
Compliance with industry regulations, such as HIPAA, GDPR, or PCI DSS, is crucial. These regulations dictate specific security measures and data handling protocols. Migrating applications while adhering to these regulations requires careful planning and execution to avoid penalties and maintain business continuity. A thorough review of the applicable regulations and the implementation of corresponding controls is essential.
Managing Security Risks and Vulnerabilities
Identifying and mitigating security risks and vulnerabilities is paramount. This includes conducting thorough security assessments of the source and target environments, identifying potential vulnerabilities in the migration process itself, and developing strategies to address them. A proactive approach to risk management is vital for minimizing the impact of potential breaches. Implementing security testing tools and procedures can help uncover potential vulnerabilities.
Thorough Security Testing
Thorough security testing is critical to validate the security of applications both before and after the migration. This involves penetration testing, vulnerability assessments, and security audits to identify weaknesses and implement necessary security measures. Penetration testing simulates real-world attacks to assess the application’s resilience against various threats. Vulnerability assessments automate the detection of known vulnerabilities, enabling timely remediation.
Checklist for Validating Security Measures
This checklist Artikels key security measures to validate during and after the migration process. The validation process should encompass both technical and procedural aspects.
- Review of existing security controls: Verify the effectiveness of existing security measures in the source environment, and plan for their implementation in the target environment.
- Security assessments of the source and target environments: Identify and document security vulnerabilities and weaknesses in both the current and new environments. This should include a thorough inventory of applications, data, and infrastructure components.
- Security testing procedures: Implement penetration testing, vulnerability assessments, and security audits to validate the effectiveness of security measures.
- Compliance with industry regulations: Ensure compliance with applicable industry regulations, including data privacy and security standards. Document the implementation of these controls.
- Data encryption: Implement data encryption throughout the migration process and in the target environment. This includes data at rest and in transit.
- Access controls: Establish and enforce strict access controls to restrict access to sensitive data and resources.
- Incident response plan: Develop a comprehensive incident response plan to address security incidents and breaches.
Performance and Scalability Optimization
Migrating applications to the cloud often presents opportunities for significant performance and scalability improvements. However, a “lift and shift” approach, while simple, often fails to leverage these opportunities, leading to suboptimal results. This section details strategies for optimizing application performance and scalability during and after migration, emphasizing cloud-native design principles and the benefits of containerization and orchestration.
Optimizing Application Performance During and After Migration
Careful planning and execution during the migration process are crucial for achieving optimal performance. This involves a thorough analysis of application bottlenecks and resource usage patterns. Identifying and addressing these issues before migrating ensures a smoother transition and prevents performance degradation. After migration, ongoing monitoring and tuning are essential to maintain peak performance and respond to evolving demands.
Continuous optimization is a key element in maximizing the benefits of cloud migration.
Importance of Cloud-Native Design Principles for Scalability
Cloud-native design principles, such as microservices architecture, containerization, and serverless functions, are essential for building scalable applications in the cloud. These architectures enable applications to dynamically adjust resources based on demand, ensuring high availability and responsiveness. The flexibility and elasticity of the cloud are best harnessed when applications are designed to accommodate varying workloads without compromising performance.
Benefits of Containerization and Orchestration Tools
Containerization technologies like Docker and orchestration platforms like Kubernetes enable the creation of portable, scalable, and manageable application environments. These tools facilitate consistent deployment across various cloud environments, leading to increased efficiency and reduced operational overhead. The standardization and automation inherent in containerization and orchestration significantly enhance application scalability and resilience.
Examples of Applications Optimized During Migration
Several organizations have successfully optimized their applications during migration to the cloud. For instance, a retail company migrated its e-commerce platform to a cloud-based infrastructure, leveraging containerization to achieve improved responsiveness during peak shopping seasons. This resulted in a significant reduction in latency and a noticeable improvement in customer experience. Similarly, a financial institution migrated its core banking application, utilizing cloud-native design principles, to enhance scalability and handle increased transaction volumes during peak periods.
Performance Gains from Cloud-Native Technologies
The table below illustrates potential performance gains achievable through the adoption of cloud-native technologies. These figures are illustrative and can vary based on specific application characteristics and cloud provider choices.
| Technology | Performance Metric (e.g., Latency Reduction) | Estimated Improvement (%) |
|---|---|---|
| Containerization (Docker) | Application Startup Time | 40-60% |
| Orchestration (Kubernetes) | Resource Utilization | 25-40% |
| Serverless Functions | Cost Optimization | 20-30% |
Note: Performance gains are not guaranteed and can vary based on factors such as application complexity, specific cloud configurations, and workload patterns.
Post-Migration Maintenance and Support

Post-migration, the focus shifts from the initial transition to ensuring ongoing operational excellence. Effective maintenance and support are critical for realizing the full benefits of the migration and maintaining the stability and performance of the new environment. This phase demands proactive monitoring, efficient troubleshooting, and a streamlined process for managing updates and patches. Failure to adequately address these post-migration needs can lead to unexpected downtime, security vulnerabilities, and performance degradation.Post-migration support encompasses a range of activities, from continuous monitoring of system health to handling user requests and resolving technical issues.
It requires a dedicated team or individuals with expertise in the new environment and a clear understanding of the application’s functionalities and dependencies. Proactive maintenance minimizes the risk of potential problems, ensuring the new system remains reliable and accessible to end-users.
Importance of Post-Migration Support and Maintenance
Proactive maintenance and support are essential to maintain application performance and user satisfaction after a migration. Effective support reduces downtime, mitigates security risks, and facilitates efficient problem resolution. A well-structured support process can minimize the impact of unexpected incidents and ensure the system remains a reliable and secure platform for critical business operations.
Monitoring and Troubleshooting Mechanisms
Robust monitoring and troubleshooting mechanisms are crucial for detecting and resolving issues promptly. These mechanisms should provide real-time insights into system performance, identify potential problems before they escalate, and facilitate rapid issue resolution. Implementing monitoring tools that track key metrics such as CPU utilization, memory consumption, and network traffic can be invaluable in proactive problem identification.
- Real-time monitoring dashboards are essential to track system health and performance. These dashboards should be configurable to provide customized views of key metrics relevant to specific applications and business needs.
- Establish a well-defined incident response plan, including procedures for escalation, communication, and issue resolution.
- Implement logging and auditing capabilities to track events, identify trends, and facilitate root cause analysis.
Automated Deployment and Scaling
Automation plays a critical role in streamlining the deployment and scaling of applications in the new environment. Automated deployment processes minimize manual intervention, reduce errors, and shorten deployment cycles. This also improves the efficiency of scaling resources up or down based on demand, which is crucial for maintaining optimal performance and cost-effectiveness.
- Utilize automation tools for application deployments and configuration management.
- Implement automated scaling solutions to adjust resources based on fluctuating demands.
- Establish a robust change management process for deployments, incorporating thorough testing and validation.
Managing Updates and Patches
A structured approach to managing updates and patches is critical to maintaining system security and stability. A well-defined process should include rigorous testing of updates in a staging environment prior to deploying them to production. This ensures compatibility and minimizes the risk of unforeseen issues.
- Establish a schedule for applying security patches and updates.
- Implement a rollback strategy in case of issues arising from an update.
- Conduct thorough testing of updates and patches in a controlled environment before deploying them to production.
Ongoing Monitoring and Support Checklist
This checklist Artikels key tasks for ongoing monitoring and support. Consistent adherence to these tasks ensures the smooth operation and performance of the migrated systems.
| Task | Frequency | Responsible Party |
|---|---|---|
| System Performance Monitoring | Hourly/Daily | Operations Team |
| Security Vulnerability Scanning | Weekly/Monthly | Security Team |
| Application Logging Review | Daily | Development Team |
| User Support Ticket Resolution | As needed | Support Team |
Cost Optimization Strategies
Accurate cost estimation is crucial for successful cloud migrations. Understanding the potential financial implications throughout the entire lifecycle, from initial planning to ongoing operations, is vital for informed decision-making. Failing to account for hidden costs, such as ongoing maintenance or scaling requirements, can lead to significant budget overruns. This section details strategies for precisely estimating migration costs and controlling operational expenditures post-migration.Precise cost estimation is paramount to a successful cloud migration.
By thoroughly analyzing the current infrastructure costs, future projected needs, and potential cloud service consumption patterns, organizations can accurately predict the financial implications of migrating to the cloud. This section details strategies to optimize costs, highlighting the value of cloud-native practices and cost-optimization tools.
Methods for Accurate Migration Cost Estimation
Precise cost estimation involves a multi-faceted approach. Start by meticulously analyzing existing infrastructure costs, including hardware, software licenses, and personnel expenses. Quantify anticipated future resource needs, including storage, compute, and networking requirements. Leverage cloud pricing calculators and detailed service descriptions to forecast cloud service consumption. Finally, factor in migration-related expenses, such as consulting fees, migration tools, and potential downtime costs.
This comprehensive approach will lead to a more accurate and realistic cost projection.
Importance of Cost Optimization Strategies During Migration
Cost optimization strategies are integral to a successful cloud migration. By proactively identifying and mitigating potential cost overruns, organizations can maximize the return on investment (ROI) from their cloud infrastructure. Minimizing operational expenses is not just about initial migration costs but also about maintaining a sustainable and cost-effective cloud environment over the long term. These strategies directly impact the overall budget and financial performance of the organization.
Use of Cloud Cost Optimization Tools
Cloud providers offer various tools designed to monitor and optimize cloud spending. These tools allow for granular control over resource usage and consumption patterns. By leveraging these tools, organizations can identify areas for cost savings and implement adjustments to optimize resource allocation. Examples include detailed billing reports, cost alerts, and automated scaling solutions. Using these tools can yield significant savings over time.
Potential Cost Savings from Adopting Cloud-Native Practices
Adopting cloud-native practices can result in significant cost savings. Employing microservices architecture, containerization technologies (e.g., Docker), and serverless functions reduces infrastructure overhead and enables dynamic resource allocation. These practices lead to more efficient resource utilization and minimize wasted capacity. The result is a more agile and cost-effective cloud infrastructure.
Strategies to Control Operational Costs After Migration
Controlling operational costs after migration is essential for long-term success. Implementing a robust monitoring and management strategy is crucial to track cloud resource utilization and identify areas for improvement. Implementing automated scaling solutions based on real-time demand allows for efficient resource allocation, avoiding unnecessary costs. Utilizing cloud cost optimization tools and establishing a clear cost management policy ensures consistent cost awareness and control.
Continuously evaluating and refining the cloud infrastructure design, based on real-world usage data, is also crucial for minimizing operational expenses.
Summary
In conclusion, avoiding the “lift and shift” anti-pattern requires a strategic approach that encompasses thorough assessment, meticulous planning, and a commitment to cloud-native principles. By prioritizing a comprehensive migration strategy, organizations can mitigate risks, optimize performance, and ensure a successful transition that delivers long-term value and cost savings. Remember, a well-executed migration is a significant investment in the future of your applications.
Expert Answers
What are some common pitfalls of the “lift and shift” approach?
Common pitfalls include compatibility issues between source and target environments, difficulties in managing dependencies and integrations, and challenges in maintaining security and compliance. Often, performance and scalability are also negatively impacted due to a lack of optimization.
How can I ensure compatibility during the migration process?
Thorough testing and validation of the application’s compatibility with the target environment are crucial. Careful consideration of operating system, libraries, and dependencies is essential. Employing automated testing tools can greatly aid in identifying and resolving compatibility issues early in the process.
What are the key differences between “lift and shift” and cloud-native strategies?
“Lift and shift” involves minimal changes to the existing application, while cloud-native approaches embrace the flexibility and scalability offered by cloud platforms. Cloud-native strategies involve refactoring applications to take full advantage of cloud resources, leading to improved performance, scalability, and resilience.
What is a comprehensive migration strategy?
A comprehensive migration strategy encompasses a detailed plan for the entire migration process, from initial assessment and planning to post-migration maintenance. It includes detailed steps for application dependencies, security, and compliance, along with performance and cost optimization strategies. This plan serves as a roadmap for the entire process, ensuring a smooth transition.