Automated Security Remediation: Definition, Benefits, and Best Practices
In the face of ever-evolving digital threats, organizations need efficient and proactive security solutions. Automated security remediation offers a p...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

In the face of ever-evolving digital threats, organizations need efficient and proactive security solutions. Automated security remediation offers a p...
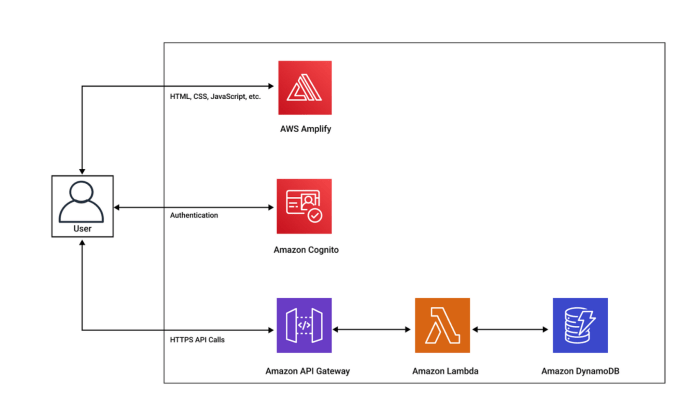
Serverless applications thrive on scalability, but managing state within their ephemeral nature presents a unique hurdle. This article explores how Dy...

A pilot migration offers a strategic, phased approach to transitioning software or data, enabling thorough testing and refinement before a full-scale...

This comprehensive guide provides a deep dive into implementing the Competing Consumers Pattern, a powerful architectural pattern for handling concurr...

In today's demanding digital environment, guaranteeing continuous operation is crucial. This comprehensive guide explores the essential strategies for...
This comprehensive guide provides a step-by-step approach to migrating your web application to the cloud, covering crucial aspects from understanding...

This comprehensive guide delves into the critical role of Cloud Workload Protection Platforms (CWPP) in modern cloud security, exploring its core conc...
This comprehensive guide provides a step-by-step approach to designing a robust cloud storage backup strategy, covering crucial aspects from defining...
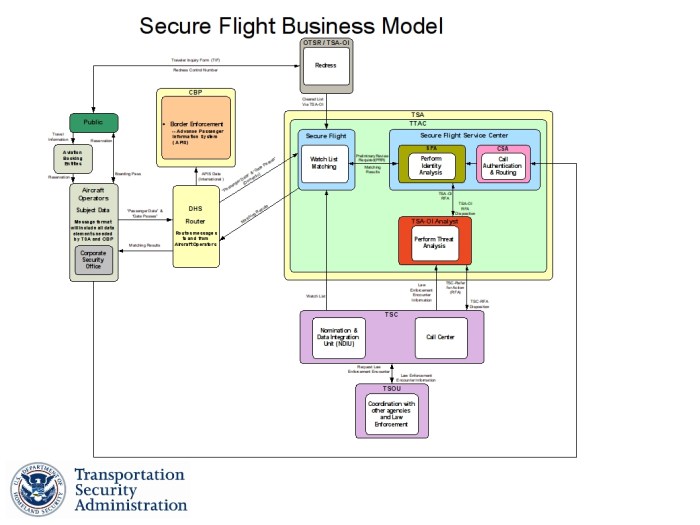
This article provides a comprehensive overview of Secure Boot processes within virtual machines, detailing its critical role in securing a VM's boot p...

Protecting sensitive data within Kubernetes is crucial for the security of your deployments. This article provides a comprehensive guide to managing s...

Discover the Saga pattern, a vital strategy for ensuring data consistency within distributed transactions in microservices architectures. This article...

This comprehensive guide provides a step-by-step approach to threat modeling for cloud applications, outlining critical steps from identifying assets...