
Stateless vs. Stateful Microservices: A Comprehensive Guide
This comprehensive article provides a deep dive into the crucial distinctions between stateless and stateful microservices, exploring their unique cha...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This comprehensive article provides a deep dive into the crucial distinctions between stateless and stateful microservices, exploring their unique cha...
This comprehensive article meticulously examines the crucial differences between unit testing and integration testing, offering a clear understanding...
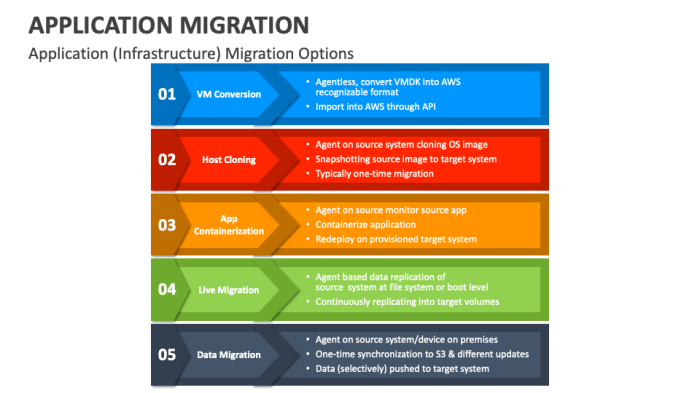
Organizations are increasingly migrating applications to optimize resources and drive operational efficiency. This process necessitates a thorough ass...
In an era defined by digital interconnectedness, cyber insurance has become a critical safeguard for businesses facing persistent online threats. This...

Cloud-based businesses are increasingly vulnerable to Distributed Denial of Service (DDoS) attacks, which can disrupt online services and lead to subs...
Serverless data analytics is revolutionizing data processing through scalable, cost-effective, and agile solutions. This paradigm shift requires strat...

This article provides a comprehensive guide to building custom Docker images from scratch, empowering developers to precisely tailor their containeriz...
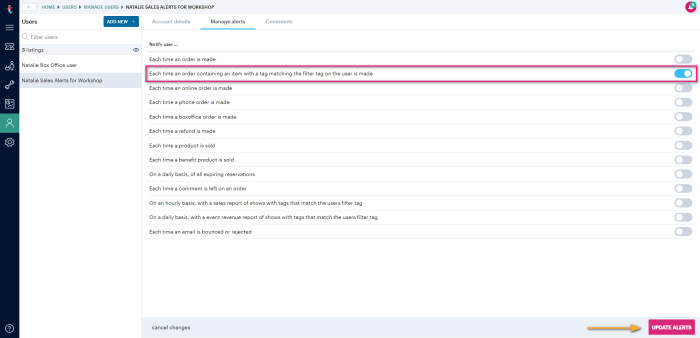
Effectively managing cloud spending is crucial, and this guide provides a clear roadmap for establishing automated cost alerts and notifications. Lear...
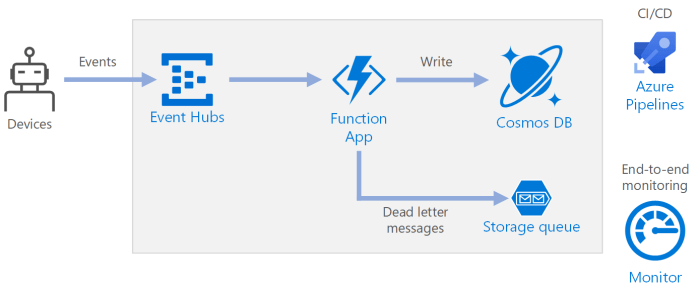
Ready to dive into serverless computing with Azure Functions? This guide provides a clear, step-by-step approach to writing your first Azure Function...
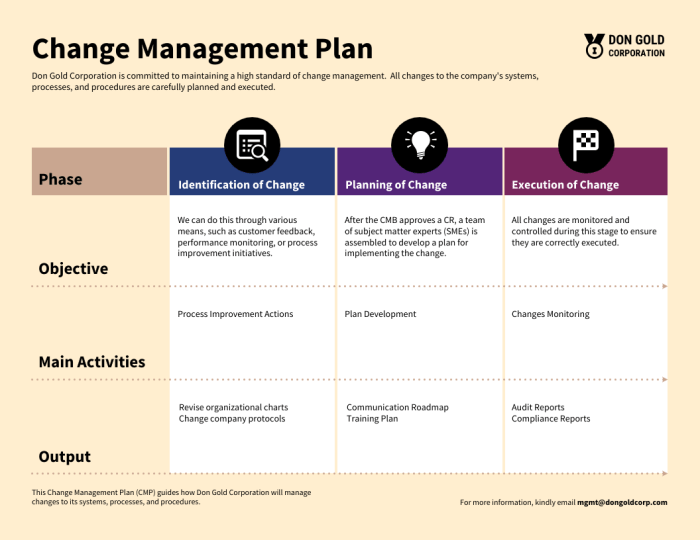
Navigating a cloud migration requires a robust change management plan to minimize disruption and ensure a seamless transition. This article provides a...

Serverless environments, while offering scalability and agility, introduce unique security challenges due to their ephemeral and distributed nature. T...

Managing third-party contractor access is a crucial element of robust cybersecurity. This guide outlines essential strategies for securely granting ac...