Post-Migration Support: A Comprehensive Guide for User Success
System migrations can disrupt user workflows, making a comprehensive support strategy crucial for a smooth transition. This article explores essential...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

System migrations can disrupt user workflows, making a comprehensive support strategy crucial for a smooth transition. This article explores essential...
This article delves into the core concept of a FinOps iteration, providing a practical guide to navigating the dynamic world of cloud financial manage...

This comprehensive guide explores the evolving landscape of Master Data Management (MDM) in the cloud, examining its architecture, data integration st...

This article provides a practical guide to implementing robust data lifecycle management policies, essential for efficient data handling within any or...
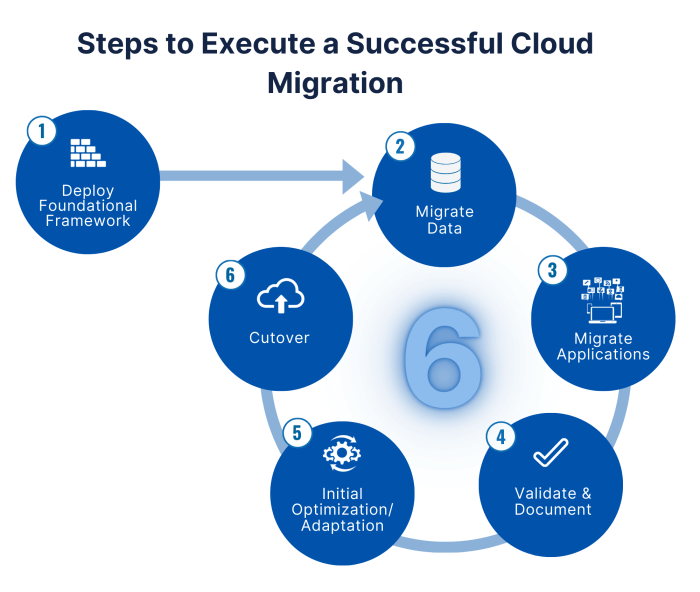
Migrating to the cloud offers significant benefits, but the real cost savings and efficiency gains are realized through ongoing optimization. This art...
Kubernetes excels at orchestrating container lifecycles, providing the foundation for efficient application deployment, management, and scaling. This...
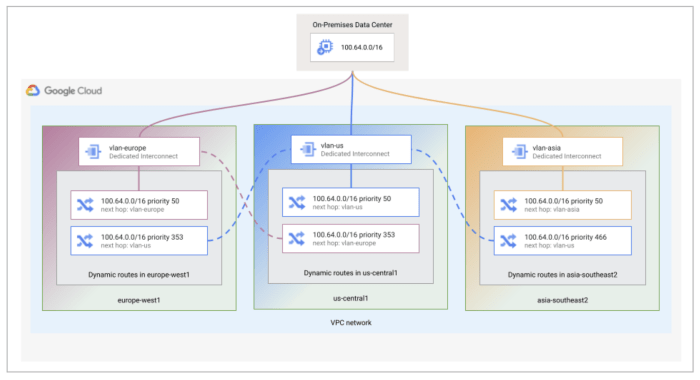
Cloud application performance hinges on efficient network paths, making optimization a critical priority for modern organizations. This article explor...

This article delves into the world of Enterprise-Grade FinOps Platforms, exploring their core features, benefits, and the critical role they play in o...

Understanding your cloud spending starts with the crucial Inform phase of the FinOps lifecycle. This stage is where you gather, analyze, and transform...

This comprehensive guide to Cloud Identity and Access Management (IAM) explores core concepts, best practices, and emerging trends to secure your clou...
This comprehensive guide explores the critical aspects of infrastructure monitoring and alerting, providing a roadmap for building robust and proactiv...
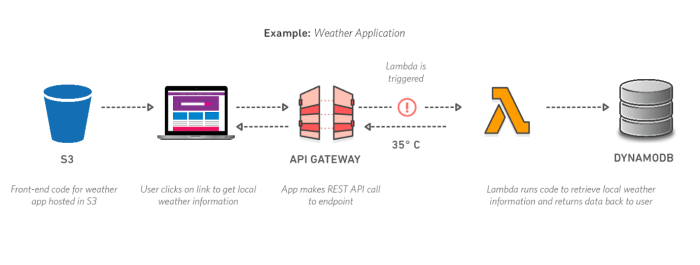
The Internet of Things explosion brings with it an unprecedented volume of data, posing significant challenges for traditional processing methods. Thi...