
Serverless Application Model (SAM): Definition, Benefits, and Use Cases
Discover insights and practical tips in this comprehensive guide about What Is The Serverless Application Model (Sam).
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Discover insights and practical tips in this comprehensive guide about What Is The Serverless Application Model (Sam).

This article delves into the OWASP Top 10, the definitive guide to web application security risks. It provides a comprehensive overview of the most c...

This article explores the essential role finance teams play in the burgeoning field of FinOps, a discipline dedicated to optimizing cloud spending and...

This comprehensive guide explores the essential best practices for creating effective API documentation, crucial for developer adoption and success. F...

Handling Data Subject Access Requests (DSARs) is a critical component of GDPR compliance. This comprehensive guide offers a clear and detailed roadmap...
The increasing convergence of Internet of Things (IoT) devices and cloud services necessitates a thorough examination of the associated security risks...

Unveiling the true financial implications of cloud computing requires a deeper look beyond initial pricing models. This article explores the often-ove...

Microservices architecture presents a significant challenge: effective inter-service communication. This article delves into the crucial aspects of ma...
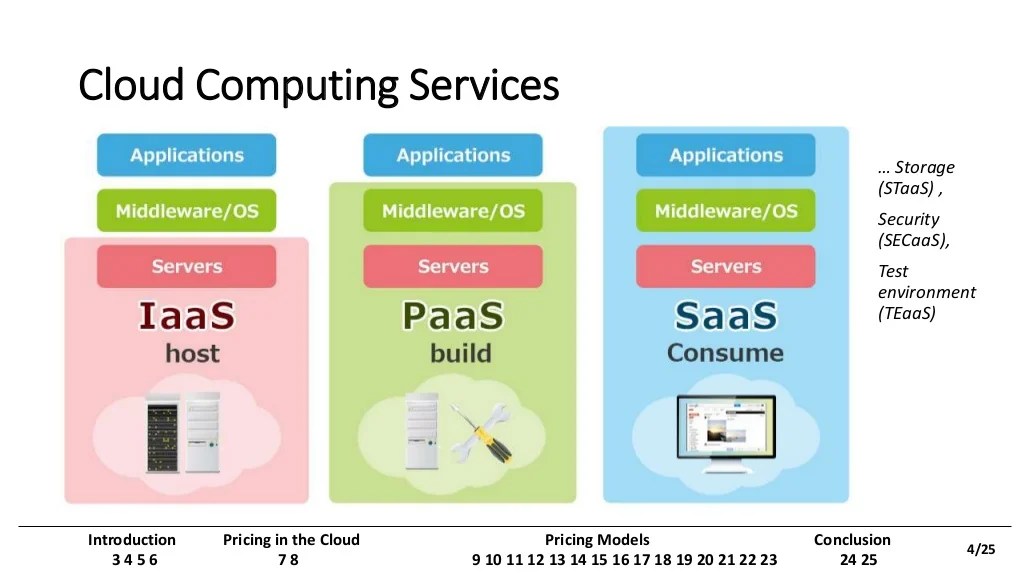
Understanding internal cloud service costs is crucial for efficient resource management. A rate card functions as a price list for your internal cloud...
Discover insights and practical tips in this comprehensive guide about How To Align Migration With Long-Term Business Goals.

Understanding the Principle of Least Privilege (PoLP) is crucial for securing your AWS Lambda functions. This principle emphasizes granting only the m...
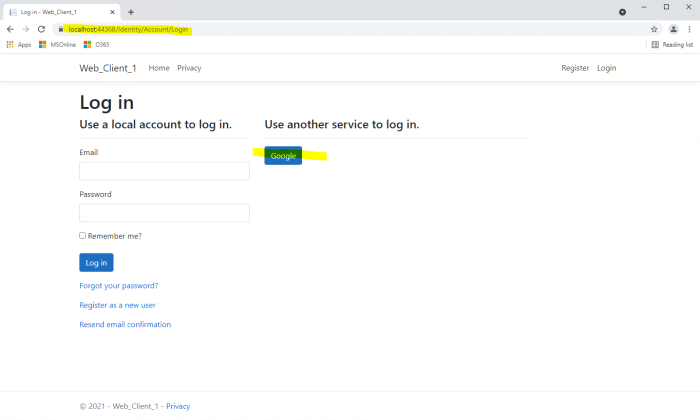
This comprehensive guide delves into the intricacies of OAuth 2.0 and OpenID Connect, explaining their roles in modern authentication and authorizatio...