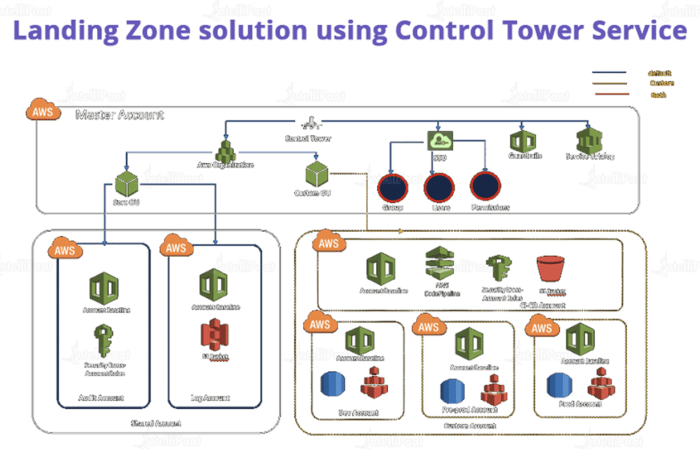
Designing a Secure and Compliant Landing Zone: A Comprehensive Guide
Building a secure and compliant cloud environment is crucial, and this article provides a comprehensive guide to designing a robust landing zone. Fro...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Building a secure and compliant cloud environment is crucial, and this article provides a comprehensive guide to designing a robust landing zone. Fro...
This article provides a comprehensive guide to integrating SonarQube, a powerful platform for static code analysis, into your software development wor...
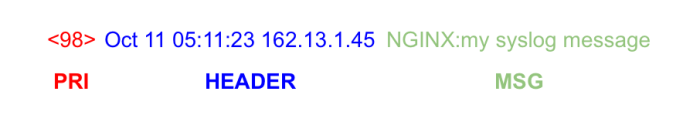
Centralized logging is essential for effectively managing the complexities of distributed systems, and this guide provides a practical roadmap for imp...
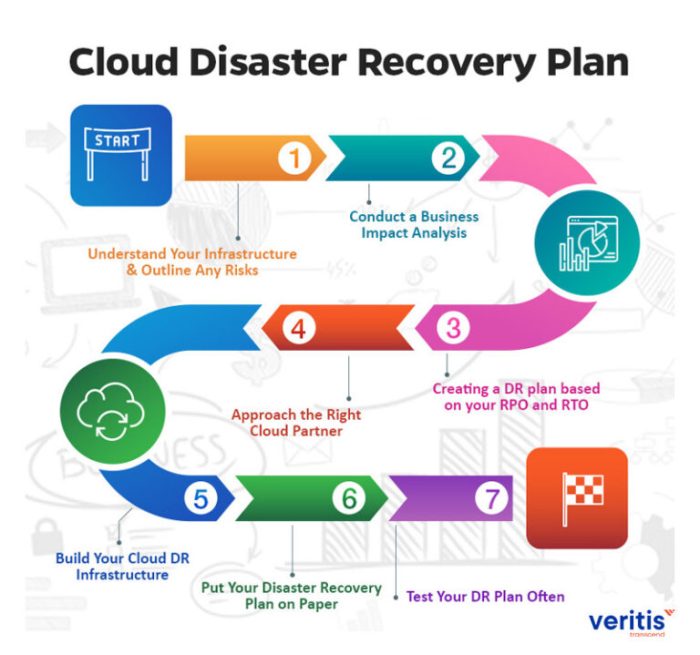
This comprehensive guide explores the critical elements of a cloud disaster recovery plan, covering everything from understanding core objectives and...
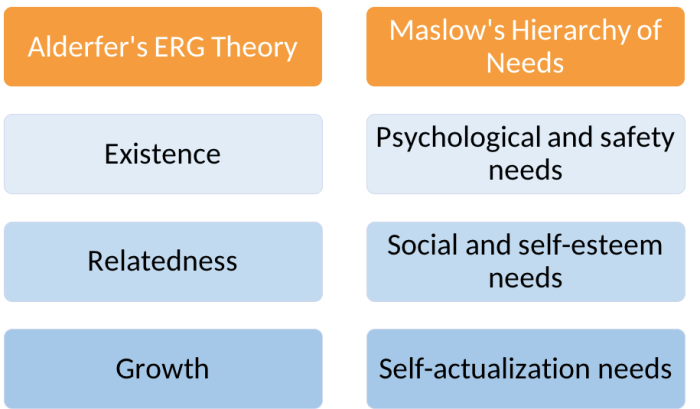
Handling cardholder data in the cloud necessitates adherence to Payment Card Industry Data Security Standard (PCI DSS) compliance. This guide provides...

To optimize financial performance, businesses must understand the distinct benefits of proactive versus reactive cost management. This article compare...

This article delves into the critical aspects of Software Asset Management (SAM) in the cloud, outlining core principles, key components, and the sign...
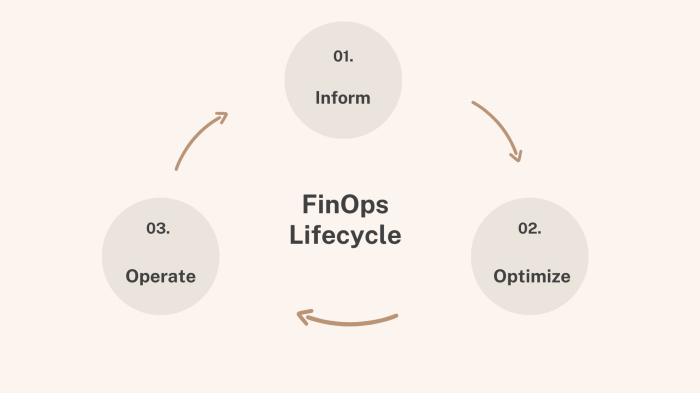
This article explores the innovative application of gamification within the FinOps framework to drive cloud cost savings. Learn how to design engagin...
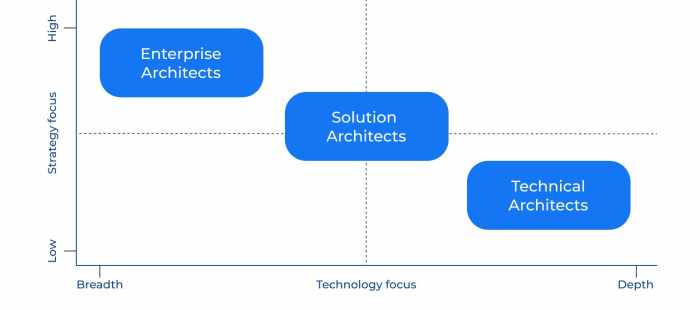
In the complex landscape of cloud migration, the Cloud Solution Architect plays a critical role in translating business needs into a secure and cost-e...

This comprehensive guide delves into the crucial process of establishing a CI/CD pipeline for microservices, a key strategy for boosting software deve...
Embarking on a cloud migration requires a thorough understanding of your organization's readiness. This comprehensive guide provides a step-by-step ap...

Cloud egress fees, the charges for transferring data out of a cloud provider's network, can significantly impact your bottom line. This guide provides...