Automate Security Policy Enforcement: A Practical Guide
In today's dynamic digital environment, automating security policy enforcement is paramount. This guide provides a comprehensive overview, covering es...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

In today's dynamic digital environment, automating security policy enforcement is paramount. This guide provides a comprehensive overview, covering es...

Data migration, while crucial for business modernization, inherently carries risks that can disrupt operations. This article explores essential strate...

Building a real-time data processing architecture is essential for applications requiring immediate insights. This guide explores the critical aspects...

Vendor lock-in poses significant risks during migration projects, potentially hindering flexibility and increasing costs. This article delves into the...

FinOps fundamentally reshapes business agility by integrating financial accountability directly into technology decisions. This proactive approach to...

Sticky sessions are a fundamental technique in web application architecture that directs a user's requests to the same server within a cluster, mirror...
Application migration presents two key strategies: replatforming and refactoring. Understanding the distinctions between these approaches is critical...
Embark on a journey into the world of serverless computing with our comprehensive guide to the best online courses. This article explores the core con...
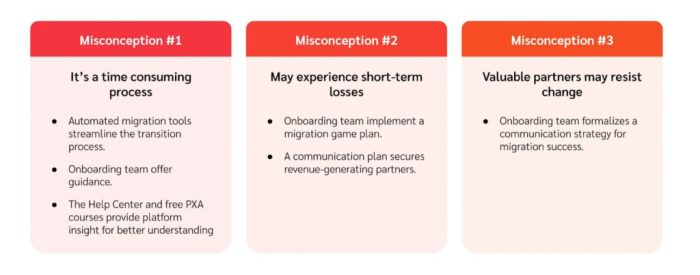
Developing a communication plan for migration stakeholders is vital for building trust and fostering effective collaboration across diverse communitie...

This comprehensive guide explores the critical concepts of data anonymization and pseudonymization, essential practices for protecting sensitive infor...
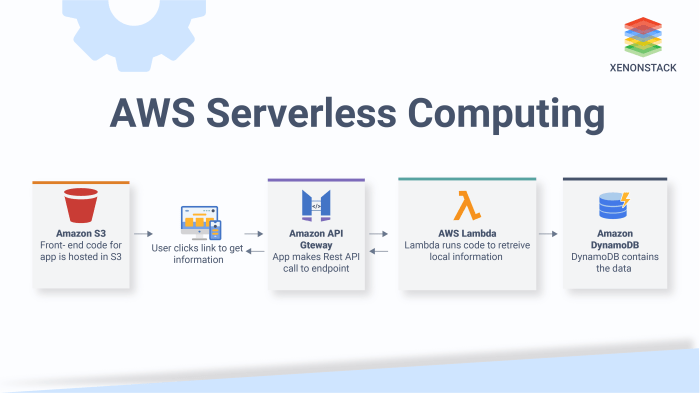
This comprehensive guide prepares you for a serverless developer interview by covering fundamental concepts, core technologies, architectural patterns...

This article provides a comprehensive overview of the Event Sourcing pattern, delving into its core principles, architecture, and benefits compared to...