
Enforcing Mandatory Tagging: A Comprehensive Guide for Resource Management
This comprehensive guide outlines the critical steps for enforcing mandatory tagging across all resources, ensuring improved organization, compliance,...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This comprehensive guide outlines the critical steps for enforcing mandatory tagging across all resources, ensuring improved organization, compliance,...

Faced with ever-growing data volumes, businesses are constantly seeking ways to optimize storage costs. Storage tiering provides a powerful solution b...

This article provides a comprehensive comparison of Continuous Delivery and Continuous Deployment, two crucial methodologies for modern software devel...
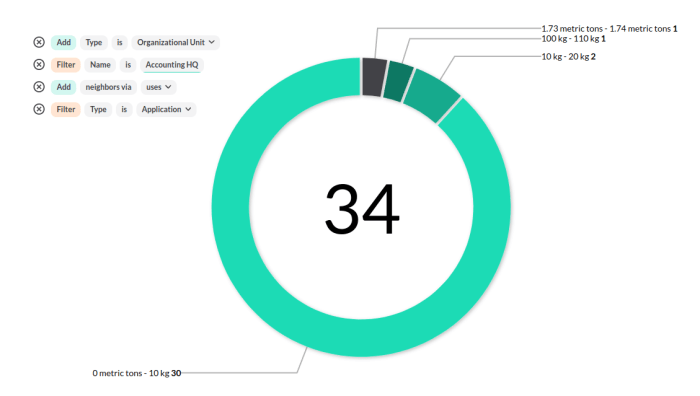
In today's environment, understanding the carbon footprint of your cloud architecture is paramount. This article provides a comprehensive guide to mea...
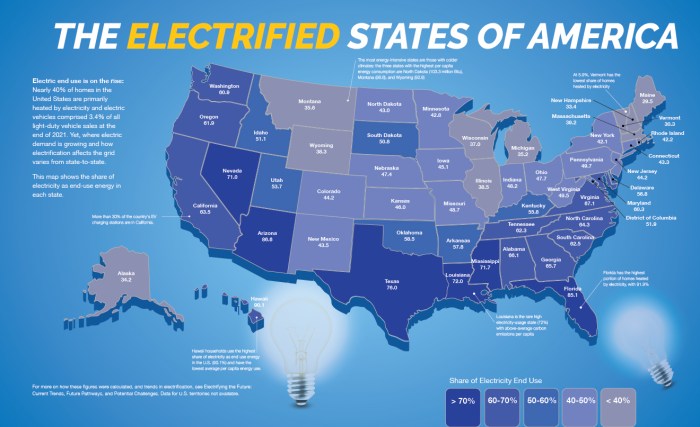
Protecting your business from unforeseen disasters requires a robust recovery plan. This article clarifies the distinctions between cold sites and hot...

This article provides a comprehensive analysis of proactive versus reactive security strategies, detailing their core principles, advantages, and limi...
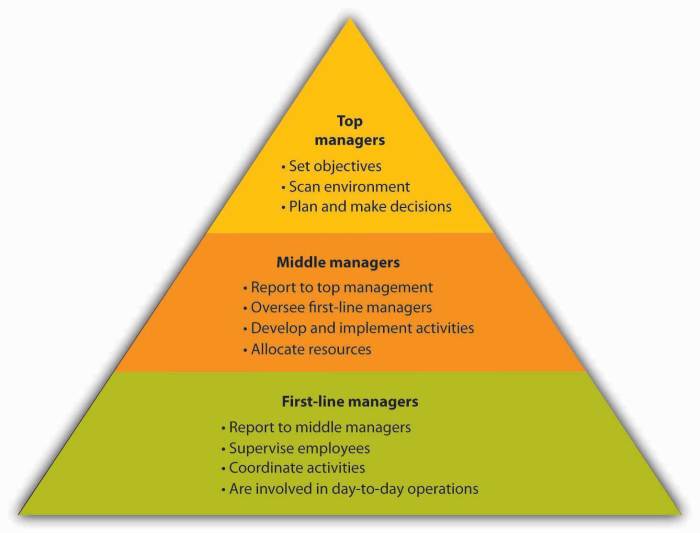
Securing cloud resources is critical, and implementing Least Privilege Access (LPA) is a foundational security practice. LPA limits user and applicati...
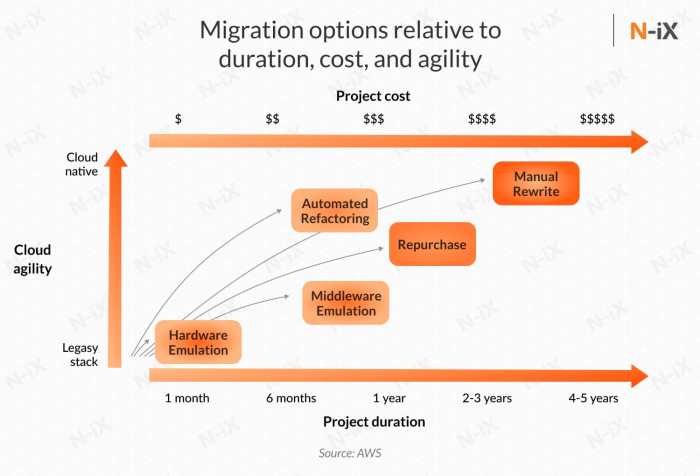
Cloud migration offers substantial benefits, but migrating all applications at once is rarely feasible. This necessitates a strategic approach to prio...

This comprehensive guide provides a deep dive into securing container images and registries, covering essential topics from image scanning and vulnera...

This comprehensive guide delves into the intricacies of designing a robust cloud data warehouse architecture, covering critical aspects from initial p...

This guide provides a comprehensive framework for calculating and managing error budgets, essential for ensuring the reliability of complex systems. I...

This article delves into the critical process of de-provisioning user accounts, explaining its definition, triggers, and the vital role it plays in bo...