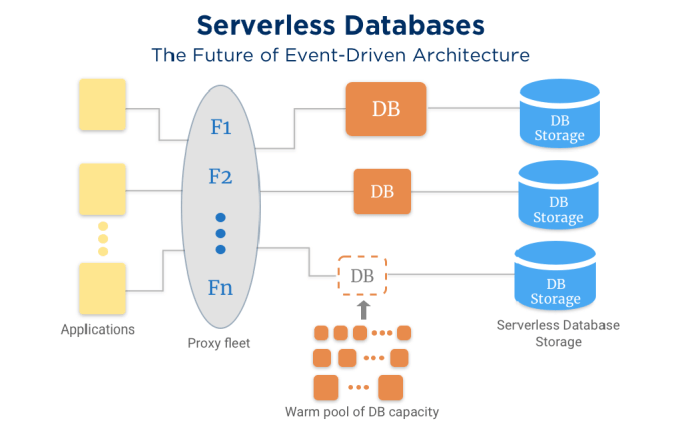
Serverless Pay-As-You-Go Pricing: A Comprehensive Guide
This article provides a comprehensive guide to the serverless pay-as-you-go pricing model, delving into its core principles, cost components, and opti...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This article provides a comprehensive guide to the serverless pay-as-you-go pricing model, delving into its core principles, cost components, and opti...

Cloud computing's transformative impact necessitates a proactive approach to security. This article outlines the core principles of "secure by design"...
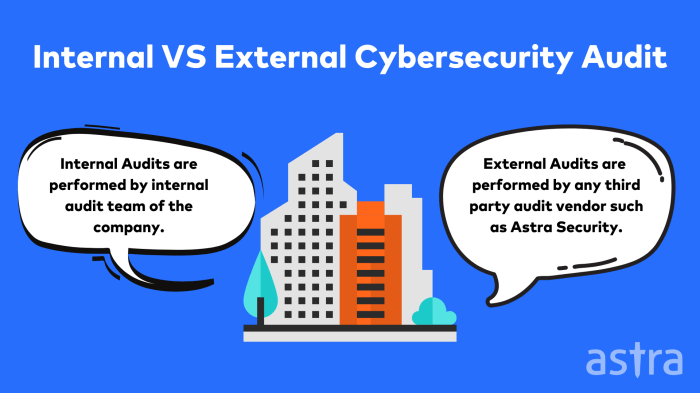
Navigating a cloud security audit can seem daunting, but this comprehensive guide provides a clear roadmap for preparation and success. The article me...

Navigating a migration project without exceeding budget is a significant challenge. This comprehensive guide explores the critical steps to avoid unex...

Measuring the impact of your FinOps practice is crucial for demonstrating its value and driving continuous improvement in cloud spending. This guide p...

Securing APIs within a cloud environment is paramount for the modern development landscape. This guide offers a comprehensive overview of best practic...
Choosing between SQL and NoSQL databases is a critical decision for any application. This comprehensive guide provides a thorough comparison, analyzin...

This article provides a comprehensive overview of Software Bill of Materials (SBOMs), explaining their definition, purpose, and benefits for various s...
Site Reliability Engineering (SRE) is a discipline that integrates software engineering principles with operational practices to build reliable and sc...

This article delves into the transformative impact of Artificial Intelligence (AI) and Machine Learning (ML) on cloud architecture, exploring their in...

Serverless computing offers significant benefits, but it also introduces the critical challenge of vendor lock-in, which can severely impact portabili...
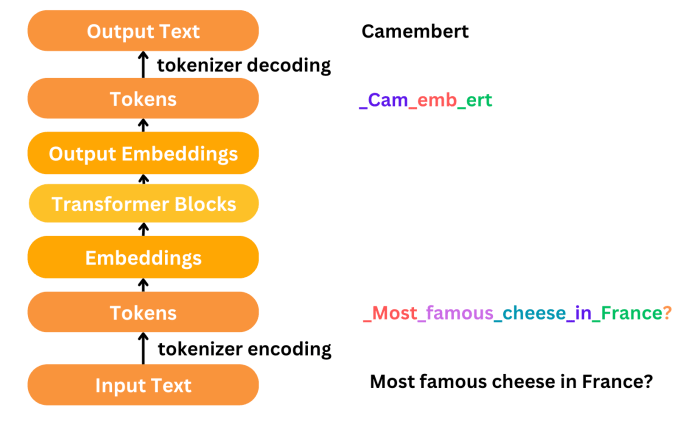
This comprehensive article delves into the critical role of tokenization in modern data security, exploring its core concepts, operational mechanisms,...