Selecting the Best Runtime for Your AWS Lambda Function
Selecting the right runtime for your AWS Lambda function is a crucial, yet often overlooked, step in optimizing your serverless applications. This dec...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Selecting the right runtime for your AWS Lambda function is a crucial, yet often overlooked, step in optimizing your serverless applications. This dec...

This article delves into the world of serverless stream processing, exploring its core components, benefits, and real-world applications. Readers wil...

This guide provides a comprehensive overview of designing systems that adhere to data sovereignty and residency principles, crucial in today's landsca...

In a microservices architecture, service discovery is essential for dynamic communication and efficient scaling. This guide offers a comprehensive roa...

Optimizing cloud resource utilization is essential for cost-effectiveness in today's digital environment. This guide, "Strategies for Minimizing Idle...
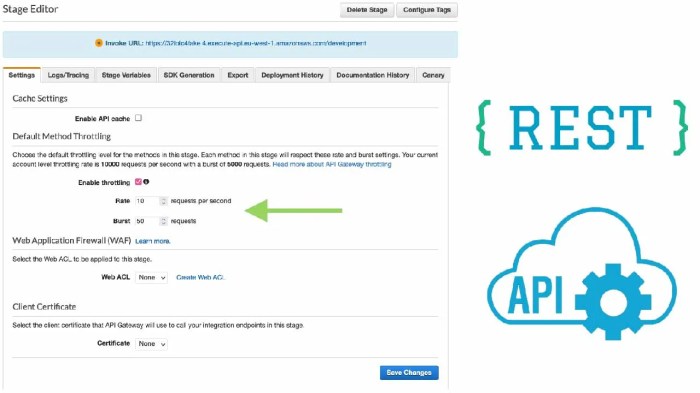
This article provides a comprehensive overview of throttling in serverless APIs, exploring its fundamental concepts, various implementation mechanisms...

Chaos Monkey, while sounding disruptive, is a valuable tool for proactively testing and strengthening system resilience. By intentionally introducing...
This article provides a comprehensive guide to building a serverless recommendation engine, covering everything from data collection and algorithm sel...

This article dissects the "Replace Architecture" anti-pattern, outlining its characteristics, motivations, and detrimental consequences for software d...
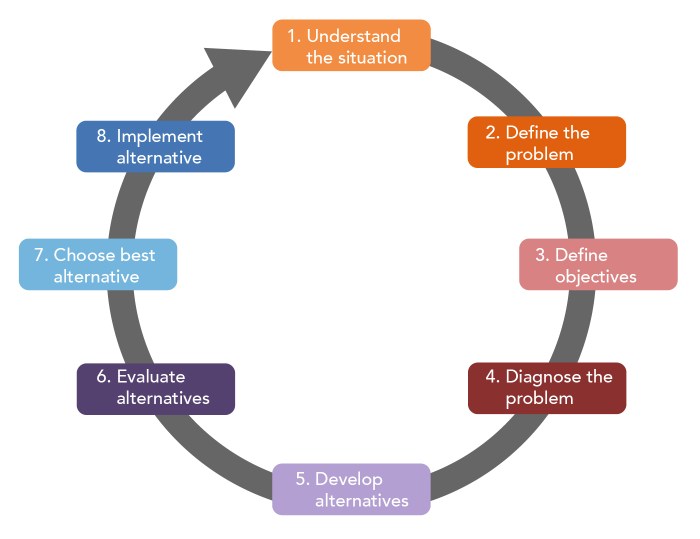
This comprehensive guide provides a deep dive into Behavior-Driven Development (BDD), outlining its core principles, workflow, and benefits for softwa...

Navigating the benefits of a multi-cloud architecture requires careful consideration of significant challenges, including complexities in management,...

This comprehensive guide explores the multifaceted landscape of container security, outlining critical best practices to protect your deployments from...