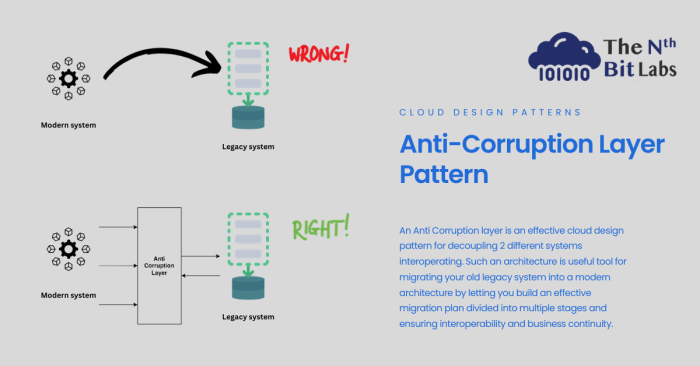
Anti-Corruption Layer: Shielding Your System from Legacy Dependencies
The anti-corruption layer pattern is a critical architectural approach for shielding core applications from the complexities of external systems. This...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

The anti-corruption layer pattern is a critical architectural approach for shielding core applications from the complexities of external systems. This...

A security baseline serves as the foundation for robust cybersecurity, providing a standardized configuration for systems and applications to ensure a...

Effectively managing cloud costs begins with establishing clear internal pricing models. This guide provides a comprehensive overview of how to set in...

This comprehensive guide explores the diverse training resources available for cloud migration, from vendor-specific programs offered by AWS, Azure, a...

This comprehensive guide explores the critical importance of securing your software dependencies, outlining potential risks from supply chain attacks...

This guide offers a strategic approach to optimizing data storage costs by focusing on migrating data to lower-cost storage tiers. It explores essenti...
Navigating a cloud cost review meeting effectively is essential for optimizing cloud spending. This guide offers a structured approach, breaking down...

This article explores the pivotal role of service meshes in securing modern, microservices-based application architectures. It highlights how service...
Serverless computing is undergoing a crucial transformation as it adapts to handle stateful workloads, a departure from its historical focus on statel...
Cybersecurity is a dynamic field, and bolstering your security posture requires a proactive, ongoing approach. This article outlines a strategic frame...
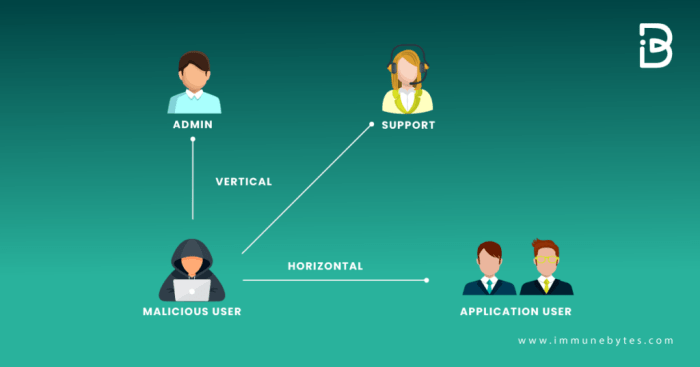
Function-Level Access Control (FLAC) is a critical security mechanism that provides granular control over application functionalities, moving beyond b...

Managing session state effectively is paramount for building scalable and reliable distributed applications. This involves tracking user data across m...