
Cloud Access Security Broker (CASB): Definition, Benefits, and How It Works
This article provides a comprehensive overview of Cloud Access Security Brokers (CASBs), outlining their core functions, architecture, and key feature...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This article provides a comprehensive overview of Cloud Access Security Brokers (CASBs), outlining their core functions, architecture, and key feature...

This article provides a comprehensive guide to designing cloud architectures with a focus on cost optimization. It explores essential strategies for e...
This comprehensive guide provides a step-by-step approach to designing a robust cloud storage backup strategy, covering crucial aspects from defining...

This comprehensive guide delves into the core principles of Cloud Native architecture, providing a detailed exploration of microservices, containeriza...
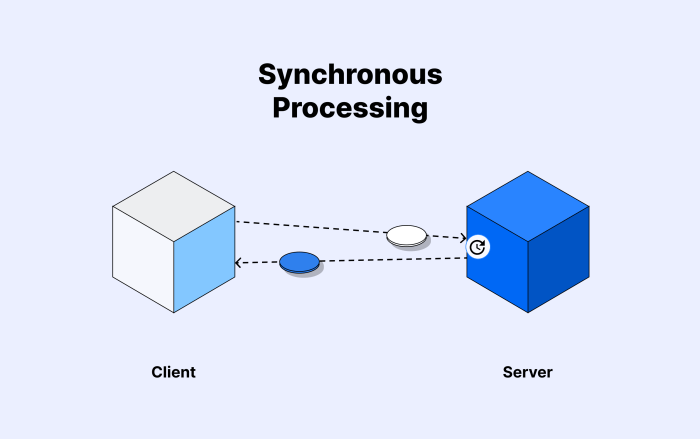
Serverless computing is revolutionizing machine learning inference by offering significant cost savings and unparalleled scalability for predictive mo...

Navigating the complexities of data in a cloud environment demands robust data governance. This article provides a comprehensive guide to implementing...
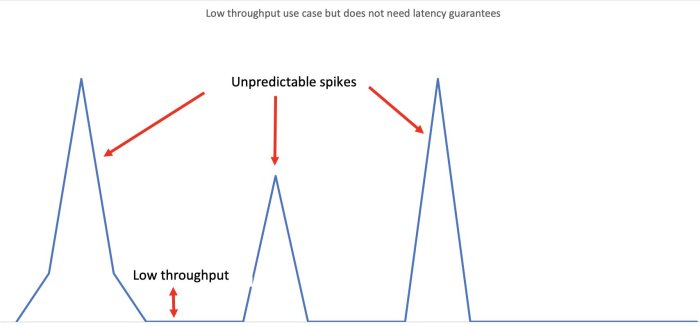
Explore the core principles and historical significance of message queues in this insightful guide to asynchronous communication. Discover how these p...
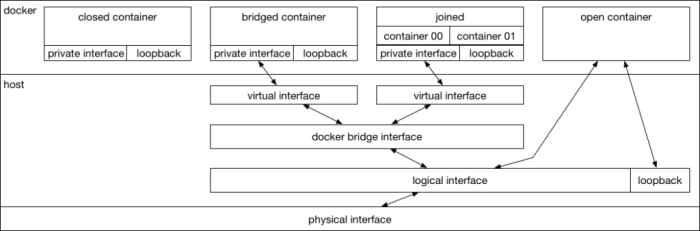
This comprehensive guide demystifies Docker networking, providing a deep dive into its fundamental concepts, network drivers, and advanced configurati...

Preparing for a cloud migration requires a thorough pre-migration security and compliance assessment. This crucial step involves a comprehensive evalu...
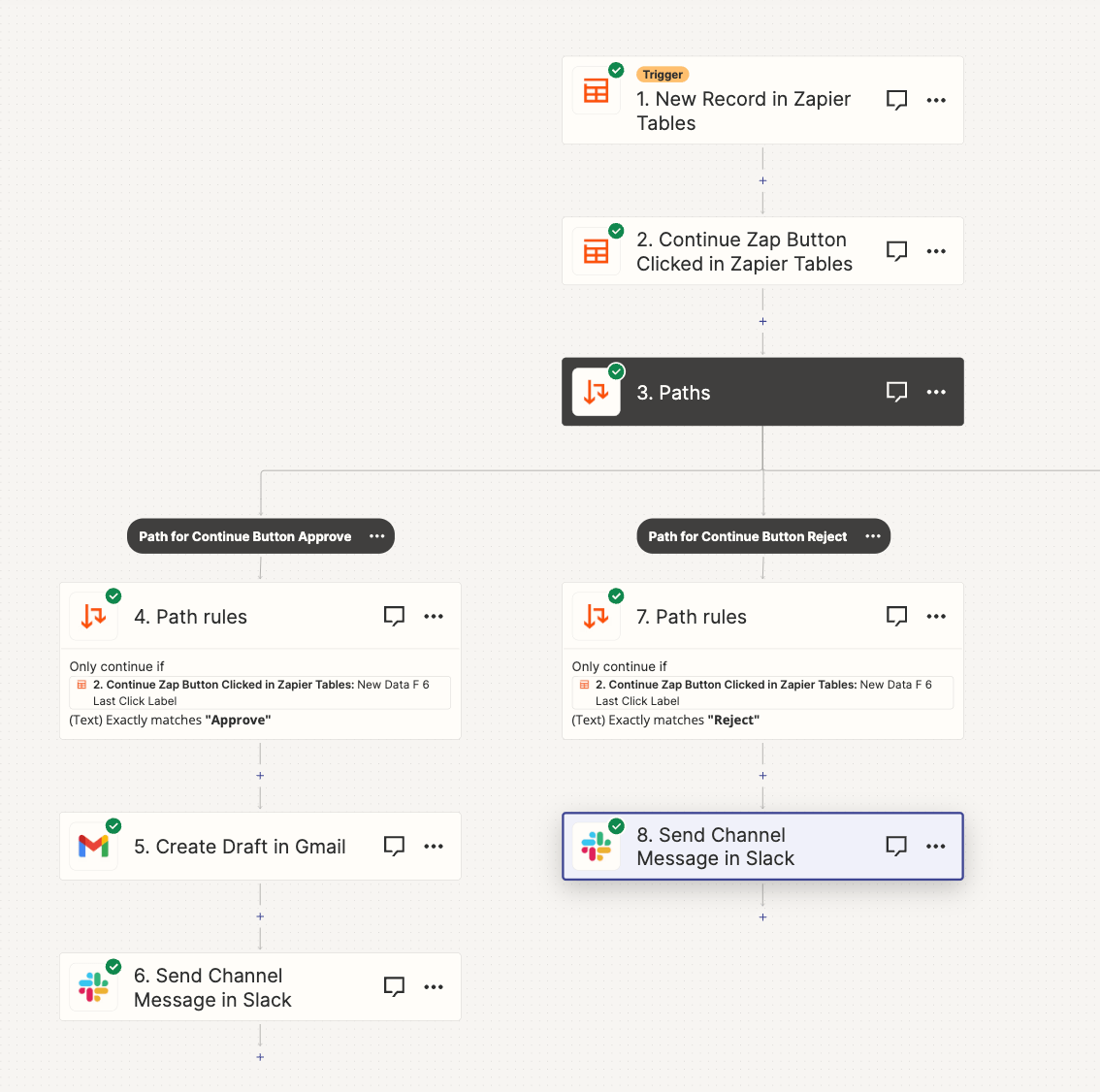
Serverless computing simplifies software development by removing the need for server management, allowing developers to concentrate on code. This arti...

Scaling applications doesn't have to be complex. This article provides a comprehensive guide to scaling applications using Kubernetes deployments, det...
In the face of escalating cyber threats, protecting web applications is more critical than ever. This article delves into the essential function of We...