
Knative: Run Serverless Applications Directly on Kubernetes
This article provides a comprehensive overview of Knative, a powerful open-source platform designed for building and deploying serverless applications...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This article provides a comprehensive overview of Knative, a powerful open-source platform designed for building and deploying serverless applications...
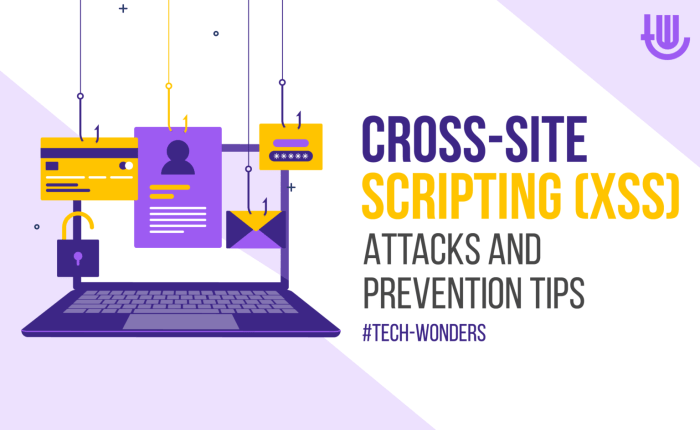
This article provides a comprehensive guide to preventing Cross-Site Scripting (XSS) attacks, detailing the fundamental concepts, various attack types...

This article provides a comprehensive guide to Service Level Objectives (SLOs) and Service Level Indicators (SLIs), explaining their crucial roles in...
Managing resources across multiple cloud providers like AWS, Azure, and GCP introduces complex challenges for consistent security and access control d...
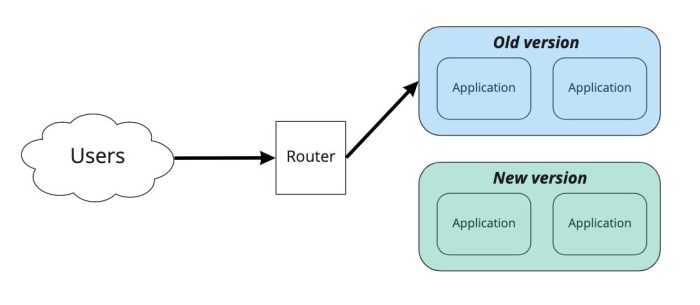
This article provides a comprehensive guide to implementing blue-green deployments, a powerful strategy for achieving zero-downtime releases. It cover...
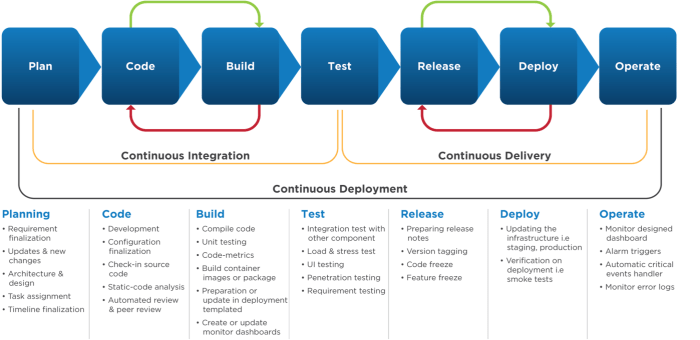
This comprehensive guide delves into the world of CI/CD pipelines, explaining their core concepts and outlining the significant advantages they offer...
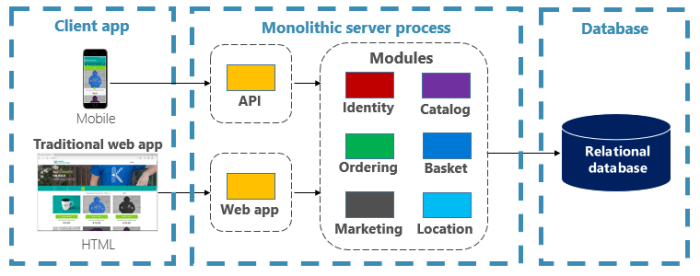
This comprehensive article delves into the core principles of cloud native architecture, offering a practical guide to building modern, scalable, and...

Ensuring data consistency is paramount when designing and deploying microservices architectures. This comprehensive guide explores the challenges of m...
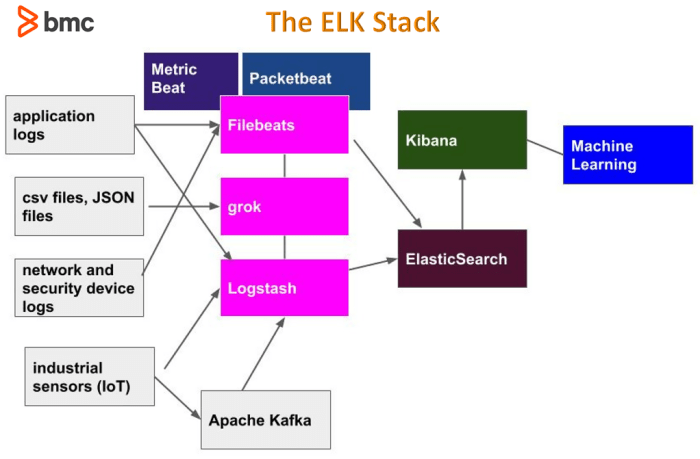
This comprehensive guide explores the ELK Stack (Elasticsearch, Logstash, and Kibana) as a powerful log management solution, covering its core compone...
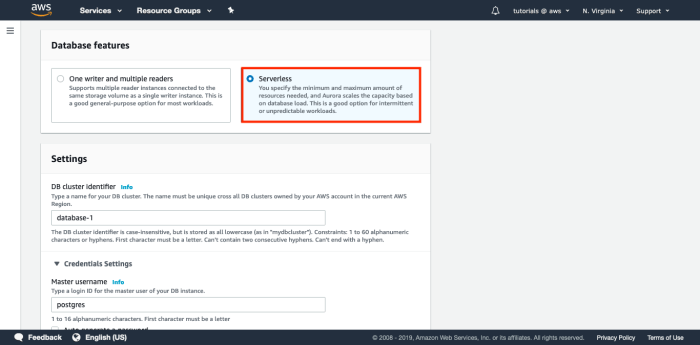
Choosing between Aurora Serverless and DynamoDB is crucial for building efficient and scalable applications on AWS. This article explores the key diff...

In the realm of serverless computing with AWS Lambda, choosing the right programming language is crucial for optimal performance and resource efficien...

Effectively managing cloud costs is crucial for maximizing the value of your cloud investments. This comprehensive guide explores cloud cost managemen...