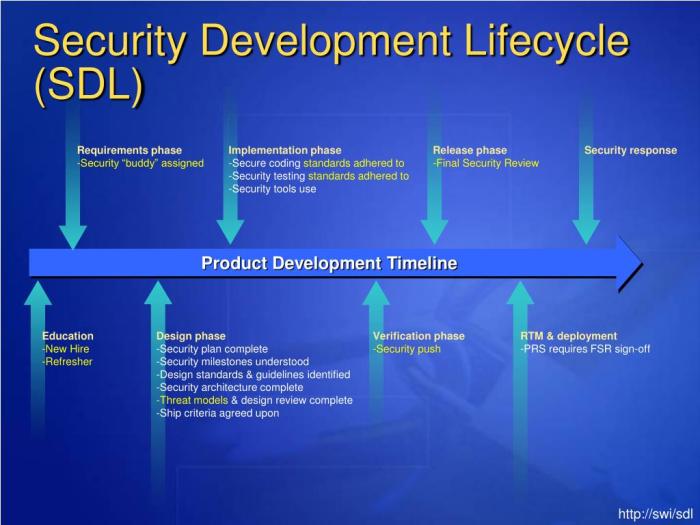
Shifting Security Left: Integrating Security into Your Development Workflow
"Shifting security left" is a critical strategy for modern software development, emphasizing the integration of security practices early in the develo...
152 posts in this category

"Shifting security left" is a critical strategy for modern software development, emphasizing the integration of security practices early in the develo...
This article provides a comprehensive overview of Secure Boot processes within virtual machines, detailing its critical role in securing a VM's boot p...

Discover how Open Policy Agent (OPA) is transforming policy enforcement in modern software development. This guide explores OPA's capabilities in mana...
The proliferation of Internet of Things (IoT) devices necessitates robust security measures to protect against increasingly sophisticated cyber threat...

In today's data-driven world, protecting sensitive information is critical, and Key Management Services (KMS) are essential for achieving this. This a...
This article provides a comprehensive overview of endpoint security specifically tailored for cloud workloads, outlining its core concepts, essential...

In the modern cloud-centric business environment, robust data and infrastructure security is critical. Security Information and Event Management (SIEM...
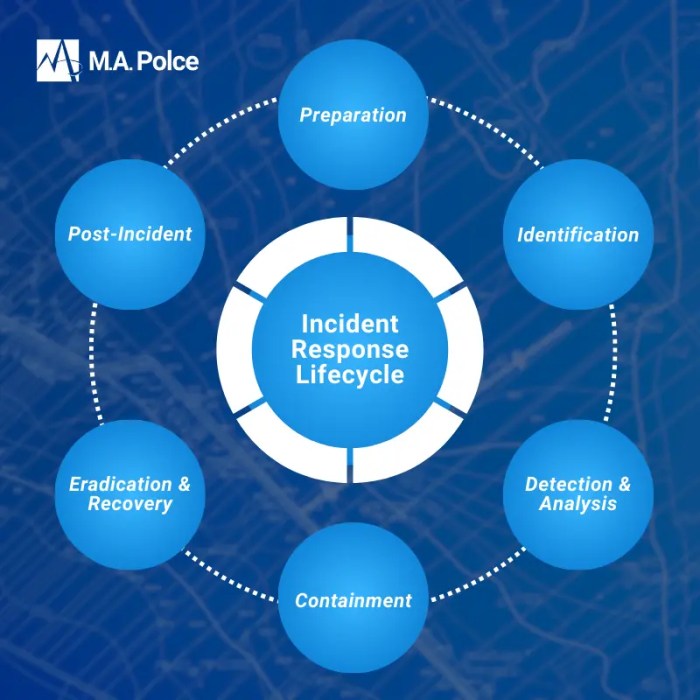
In the face of ever-evolving cyber threats, tabletop exercises are vital for strengthening an organization's incident response capabilities. These dyn...
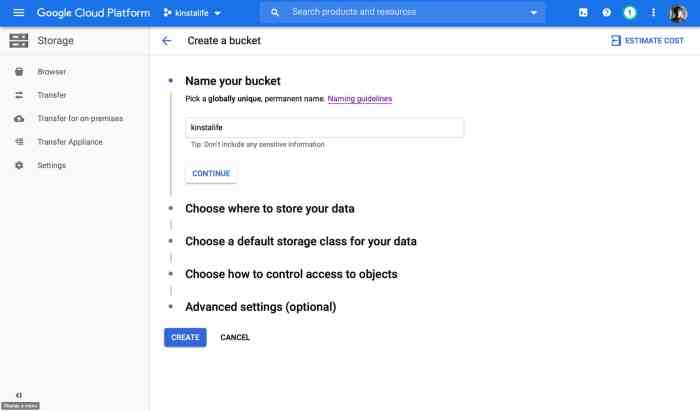
With the increasing reliance on cloud storage, securing your buckets from misconfiguration is crucial. This article delves into the unique security ch...

This article provides a comprehensive overview of the Common Vulnerabilities and Exposures (CVE) database, detailing its purpose, structure, and the r...

Safeguarding your cloud environment begins with a thorough vulnerability assessment. This guide provides a structured approach to identifying and miti...

This article provides a comprehensive guide to Tactics, Techniques, and Procedures (TTPs), crucial elements for understanding and combating cyber thre...