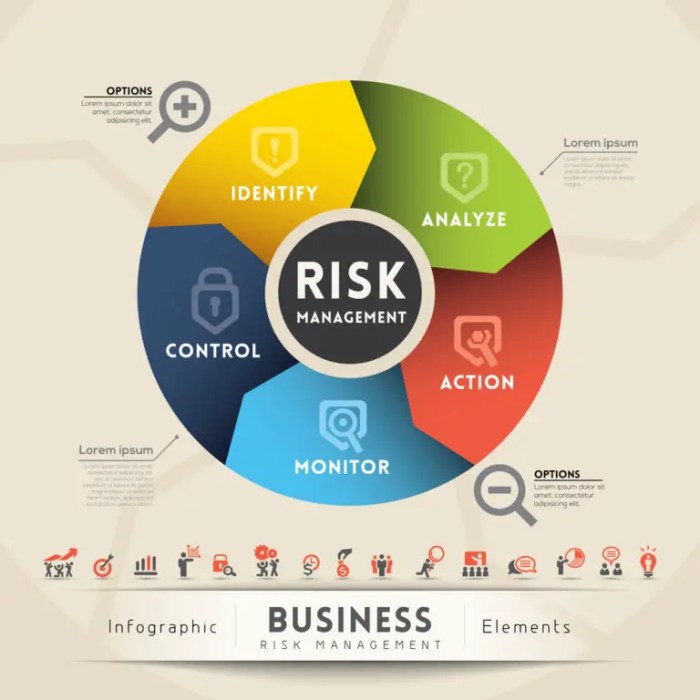
Key Risk Indicators (KRIs) for Cybersecurity: A Comprehensive Guide
Cybersecurity Key Risk Indicators (KRIs) serve as vital early warning signals, enabling organizations to proactively manage and mitigate evolving cybe...
152 posts in this category

Cybersecurity Key Risk Indicators (KRIs) serve as vital early warning signals, enabling organizations to proactively manage and mitigate evolving cybe...

This article provides a comprehensive overview of Static Application Security Testing (SAST), exploring its core principles, role within the Software...
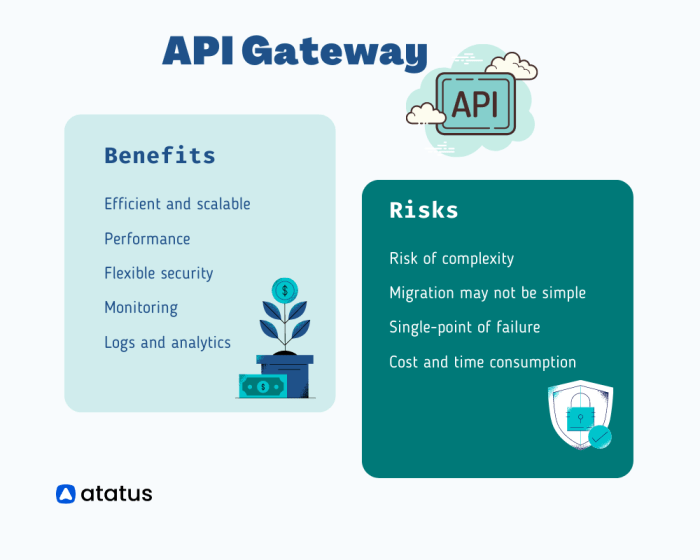
API gateways are vital components of modern application architectures, acting as the primary point of entry and security for all API traffic. Understa...

Effectively securing your cloud infrastructure requires a deep understanding of both Security Groups and Network ACLs. This comprehensive guide delves...
Cybersecurity is a dynamic field, and bolstering your security posture requires a proactive, ongoing approach. This article outlines a strategic frame...

This article comprehensively explores the "Right to Be Forgotten," a critical aspect of data privacy laws, detailing its origins, legal frameworks, an...
In the face of escalating cyber threats, protecting web applications is more critical than ever. This article delves into the essential function of We...

The NIST Cybersecurity Framework is a widely adopted, voluntary standard designed to help organizations proactively manage and reduce cybersecurity ri...
In today's evolving threat landscape, measuring the effectiveness of your security program is paramount. This guide provides a structured approach to...

Safeguarding a data lake environment requires a multi-faceted approach. This article provides a comprehensive guide to securing your data lake, coveri...
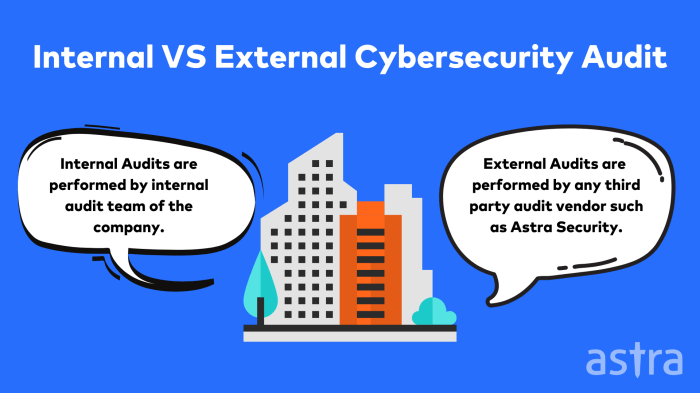
Navigating a cloud security audit can seem daunting, but this comprehensive guide provides a clear roadmap for preparation and success. The article me...

This article provides a comprehensive analysis of proactive versus reactive security strategies, detailing their core principles, advantages, and limi...