
Implementing Runtime Security for Containerized Applications
This article provides a comprehensive overview of runtime security for containers, emphasizing its critical role in protecting containerized applicati...
152 posts in this category

This article provides a comprehensive overview of runtime security for containers, emphasizing its critical role in protecting containerized applicati...

This comprehensive guide delves into the critical role of Cloud Workload Protection Platforms (CWPP) in modern cloud security, exploring its core conc...
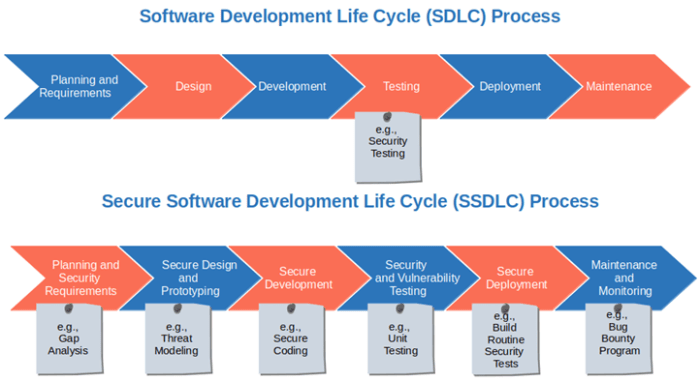
Protecting your software from vulnerabilities is paramount in today's digital world, and this guide provides a comprehensive approach to implementing...
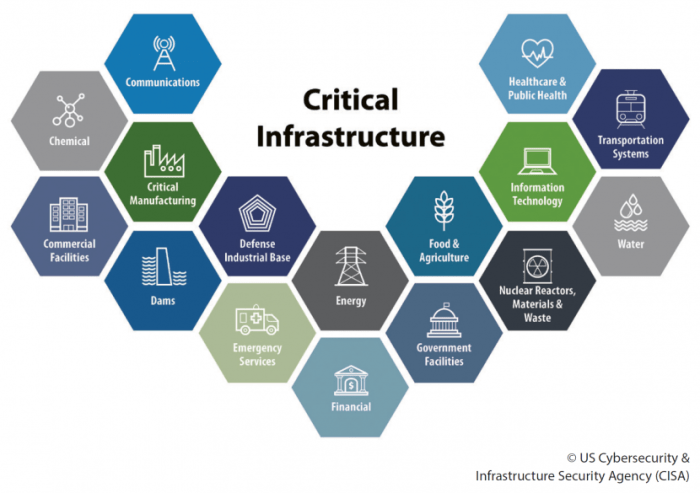
This article provides a comprehensive guide to implementing CIS Benchmarks for cloud hardening, covering crucial aspects from understanding the benchm...

This comprehensive guide explores Interactive Application Security Testing (IAST), detailing its fundamental principles, advantages, and practical imp...

This comprehensive guide explores the critical concepts of data anonymization and pseudonymization, essential practices for protecting sensitive infor...
This article provides a comprehensive guide to implementing a Zero Trust security model within cloud environments, covering key principles, asset iden...
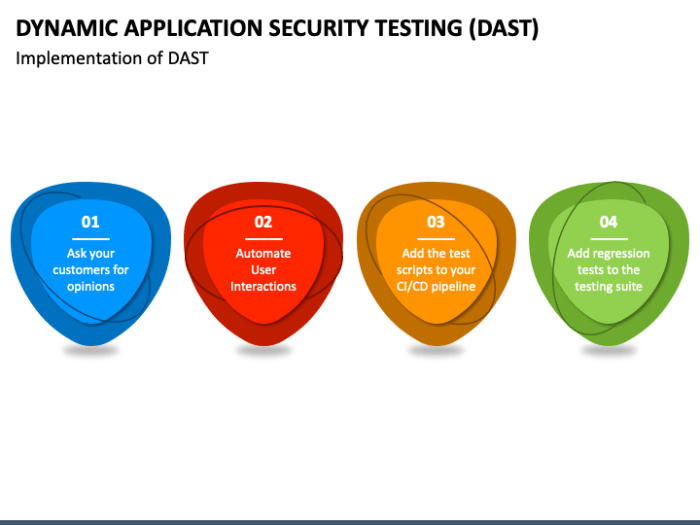
This comprehensive guide explores Dynamic Application Security Testing (DAST), providing a deep dive into its core concepts, functionality, and practi...

This article delves into the critical security challenges inherent in serverless computing, covering everything from authentication and authorization...
This article provides a comprehensive guide to preventing Cross-Site Scripting (XSS) attacks, detailing the fundamental concepts, various attack types...

This comprehensive guide explores the ISO 27001 standard, a globally recognized framework for information security management. From its core principl...

This guide provides a comprehensive roadmap for establishing robust threat hunting capabilities, essential for proactively identifying and mitigating...