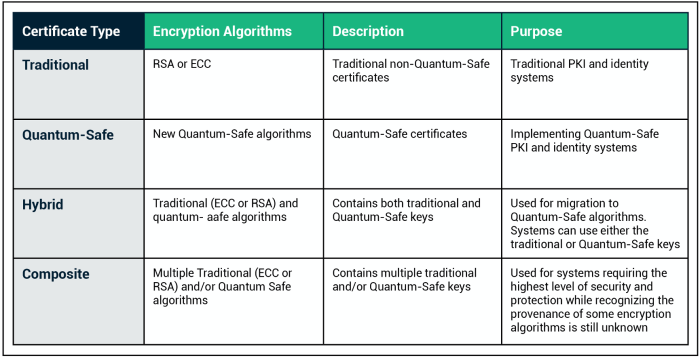
Quantum Cryptography: How It's Revolutionizing Security
Explore the groundbreaking field of quantum cryptography and its revolutionary impact on cybersecurity in this comprehensive article. From fundamental...
152 posts in this category

Explore the groundbreaking field of quantum cryptography and its revolutionary impact on cybersecurity in this comprehensive article. From fundamental...

This article provides a comprehensive overview of User and Entity Behavior Analytics (UEBA), exploring its core concepts, components, and practical ap...
User Lifecycle Management (ULM) and provisioning are crucial for security, operational efficiency, and compliance within any organization. This guide...

This article provides an introduction to threat modeling using the STRIDE methodology, a critical practice for enhancing software security. Learn how...

Navigate the complex legal landscape of cloud computing with this comprehensive guide. This article delves into critical areas like data privacy regul...
Artificial intelligence is rapidly transforming the cybersecurity landscape, offering powerful new tools for threat detection, incident response, and...
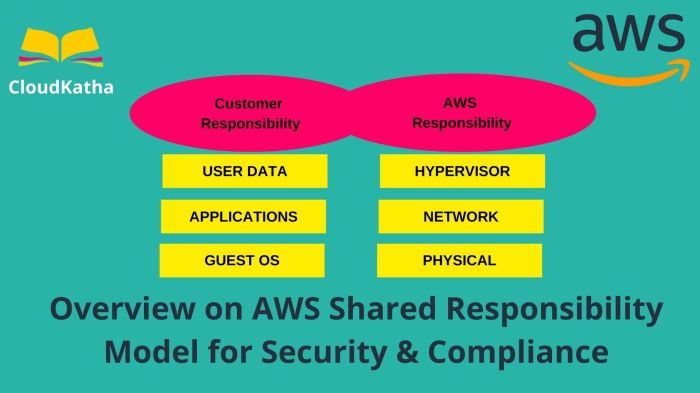
The shared responsibility model is a critical framework in cloud security, outlining the security obligations of both the cloud provider and the custo...
This comprehensive guide outlines the crucial steps for conducting regular cloud security risk assessments, ensuring the protection of your valuable a...

This article delves into the critical practice of Continuous Compliance Monitoring (CCM) in cloud environments, explaining its core concepts and showc...
In an era defined by digital interconnectedness, cyber insurance has become a critical safeguard for businesses facing persistent online threats. This...
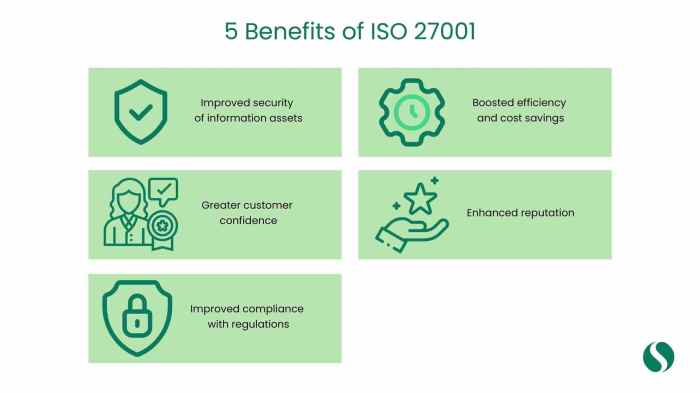
This comprehensive guide provides a detailed roadmap for achieving ISO 27001 certification, covering everything from understanding the core principles...

Navigating HIPAA compliance in the cloud requires a strategic approach that addresses data security, access controls, and disaster recovery. This comp...