
Securing Infrastructure as Code (IaC): A Comprehensive Guide
This comprehensive guide provides a crucial roadmap for securing Infrastructure as Code (IaC) templates, addressing the inherent security challenges o...
152 posts in this category

This comprehensive guide provides a crucial roadmap for securing Infrastructure as Code (IaC) templates, addressing the inherent security challenges o...

This article delves into the OWASP Top 10, the definitive guide to web application security risks. It provides a comprehensive overview of the most c...
Protecting sensitive data in the digital age demands robust security measures. This guide provides a detailed overview of enforcing strong authenticat...

Cloud environments present unique challenges for security forensics, but understanding the core principles is crucial for effective investigation. Thi...

This article delves into the intricacies of legal hold and eDiscovery, focusing on the significant advantages of leveraging cloud technology for these...
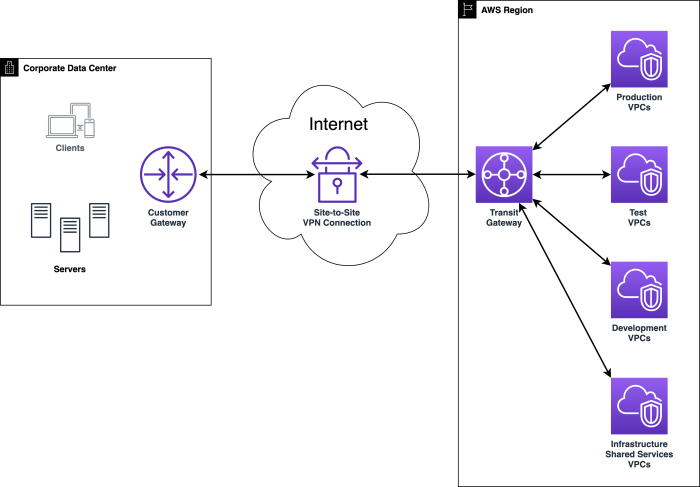
Understand the critical role of Virtual Private Networks (VPNs) in securing modern corporate communications. This article explores the core functional...

The cloud offers significant advantages, but it also presents new vulnerabilities to malware and ransomware attacks. This article outlines essential s...
In the world of interconnected microservices, secure service-to-service communication is critical. Mutual Transport Layer Security (mTLS) provides a p...