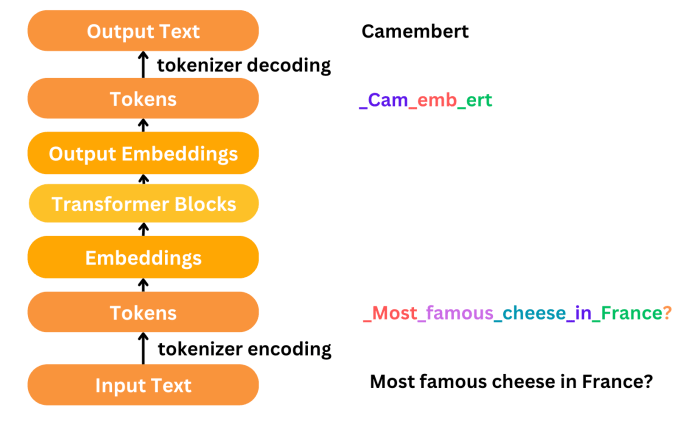
Data Tokenization: A Comprehensive Guide to Enhanced Security
This comprehensive article delves into the critical role of tokenization in modern data security, exploring its core concepts, operational mechanisms,...
152 posts in this category

This comprehensive article delves into the critical role of tokenization in modern data security, exploring its core concepts, operational mechanisms,...
This article explores the critical technical controls necessary for organizations to comply with GDPR regulations concerning data residency and sovere...

Navigating the complexities of cloud security requires a proactive approach, beginning with a comprehensive incident response plan. This guide highlig...
This comprehensive article explores the concept of honeypots in cybersecurity, detailing their purpose, diverse types (low, medium, and high-interacti...
This article offers a comprehensive guide to negotiating robust security provisions within your cloud service level agreement (SLA). It covers critica...
This comprehensive guide delves into the critical aspects of secure logging and monitoring within cloud environments, exploring its fundamental concep...

This article provides a comprehensive overview of the roles and responsibilities within a Security Operations Center (SOC), crucial for modern cyberse...

Privacy-preserving computation offers a groundbreaking approach to data security, enabling the processing of encrypted data without the need for decry...

This comprehensive article delves into Runtime Application Self-Protection (RASP), exploring its fundamental concepts, architecture, and operational m...
Establishing a formal cloud security governance framework is crucial for protecting valuable assets and maintaining compliance in the cloud. This fram...

This article provides a comprehensive overview of Software Bill of Materials (SBOMs), explaining their definition, purpose, and benefits for various s...
This comprehensive guide provides a detailed roadmap for implementing Single Sign-On (SSO) across your enterprise applications. From understanding the...