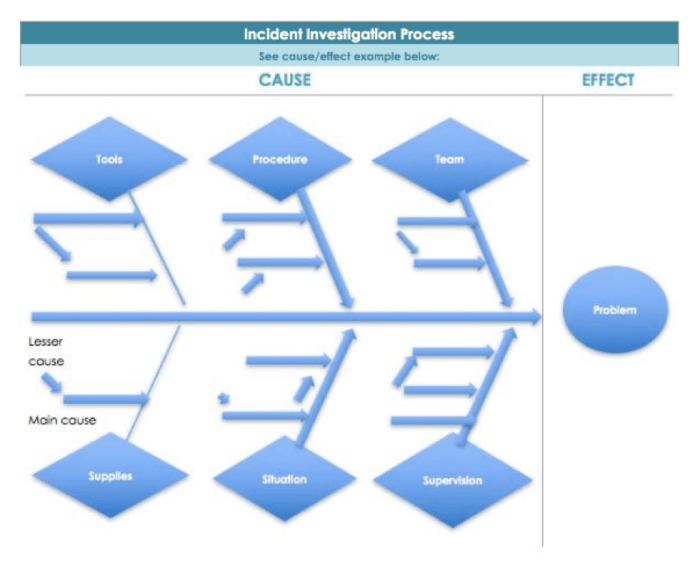
Root Cause Analysis for Security Incidents: A Step-by-Step Guide
This article provides a comprehensive guide to performing a Root Cause Analysis (RCA) following a security incident, a crucial skill in today's digita...
152 posts in this category

This article provides a comprehensive guide to performing a Root Cause Analysis (RCA) following a security incident, a crucial skill in today's digita...

The digital world is constantly evolving, and staying informed about the latest security threats and vulnerabilities is crucial for both individuals a...
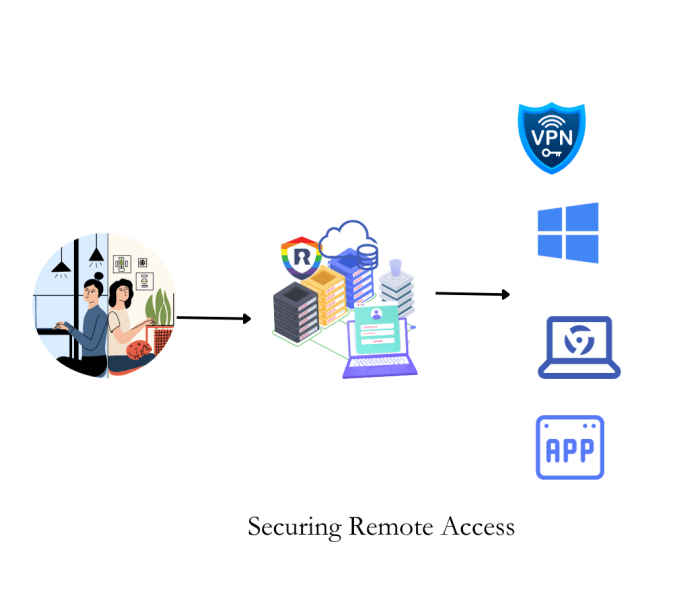
Securing remote access to cloud environments is paramount in today's interconnected landscape, yet presents significant security challenges. This guid...

This comprehensive guide explores the critical importance of securing your software dependencies, outlining potential risks from supply chain attacks...

This article provides a comprehensive overview of security maturity models, essential frameworks for enhancing an organization's cybersecurity posture...
Securing cloud resources is critical, and implementing Least Privilege Access (LPA) is a foundational security practice. LPA limits user and applicati...
This comprehensive guide delves into the intricacies of OAuth 2.0 and OpenID Connect, explaining their roles in modern authentication and authorizatio...

In the digital age, the integrity and admissibility of digital evidence are paramount for successful investigations. This article delves into the cruc...

Enhance your cybersecurity strategy by learning how to set up a honeypot, a valuable tool designed to attract and analyze potential attackers. This gu...

Managing third-party contractor access is a crucial element of robust cybersecurity. This guide outlines essential strategies for securely granting ac...

This article provides a comprehensive overview of Cloud Access Security Brokers (CASBs), outlining their core functions, architecture, and key feature...
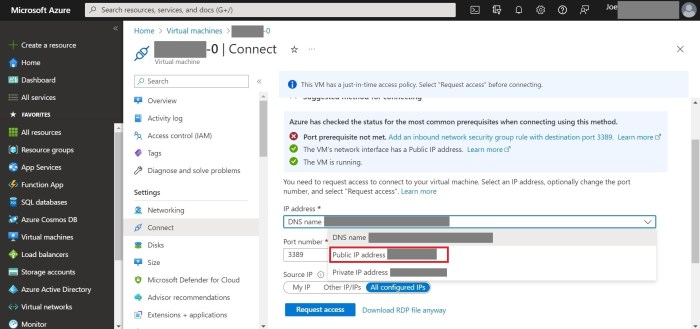
This article delves into the critical concept of Just-in-Time (JIT) access for cloud resources, exploring its core principles and the significant secu...